Single firewall vs. multiple virtual domains
A typical FortiGate setup, with a small to mid-range appliance, enables you to include a number of subnets on your network using the available ports and switch interfaces. This can potentially provide a means of having three or more mini networks for the various groups in a company. Within this infrastructure, multiple network administrators have access to the FortiGate to maintain security policies.
However, the FortiGate unit may not have enough interfaces to match the number of departments in the organization. If the FortiGate unit it running in transparent mode however, there is only one interface, and multiple network branches through the FortiGate are not possible.
A FortiGate unit with Virtual Domains (VDOMs) enabled, provides a means to provide the same functionality in transparent mode as a FortiGate in NAT mode. VDOMs are a method of dividing a FortiGate unit into two or more virtual units that function as multiple independent units. VDOMs can provide separate security policies and, in NAT mode, completely separate configurations for routing and VPN services for each connected network. For administration, an administrator can be assigned to each VDOM, minimizing the possibility of error or fouling network communications.
By default, most FortiGate units support 10 VDOMs. Many FortiGate models support purchasing a license key to increase the maximum number.
Single firewall vs. vdoms
When VDOMs are not enabled, and the FortiGate unit is in transparent mode, all the interfaces on your unit become broadcast interfaces. The problem is there are no interfaces free for additional network segments.
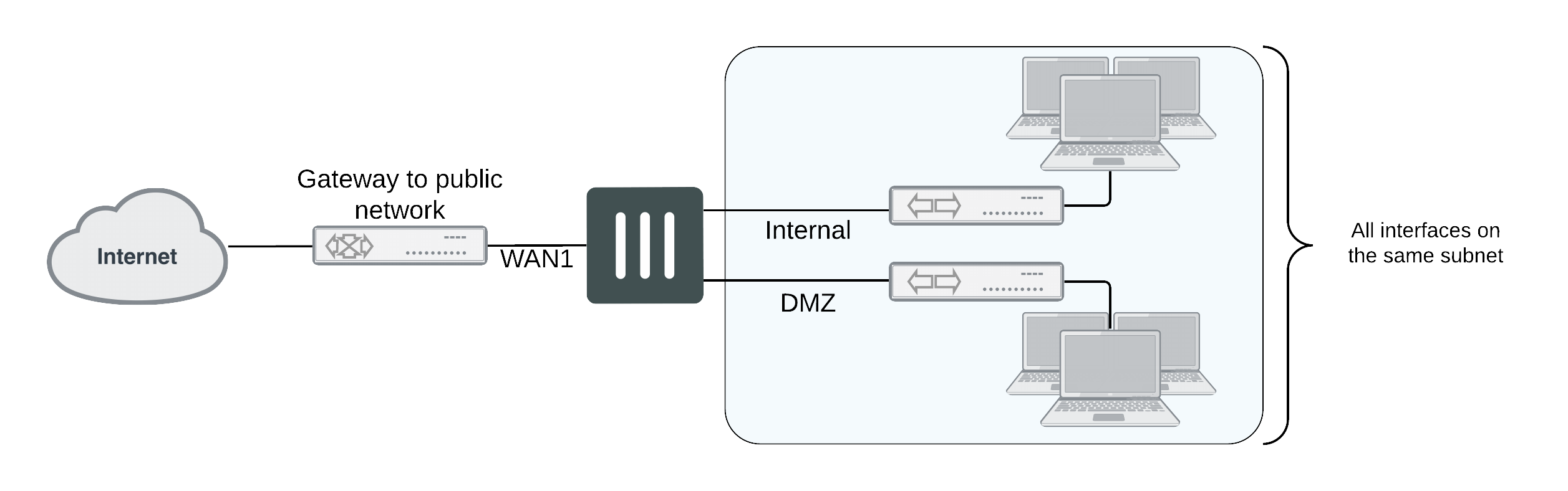
A FortiGate with three interfaces means only limited network segments are possible without purchasing more FortiGate devices.
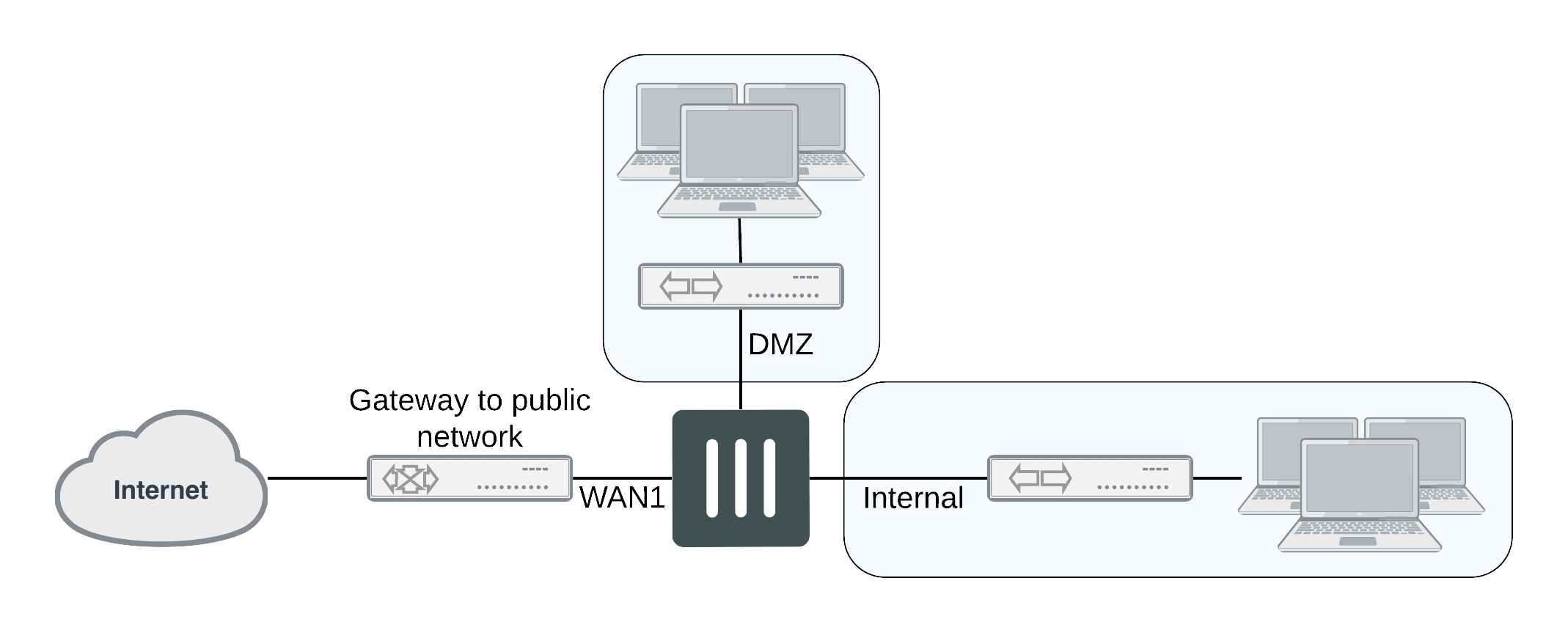
With multiple VDOMs you can have one of them configured in transparent mode, and the rest in NAT mode. In this configuration, you have an available transparent mode FortiGate unit you can drop into your network for troubleshooting, and you also have the standard.
This example shows how to enable VDOMs on the FortiGate unit and the basic and create a VDOM accounting on the DMZ2 port and assign an administrator to maintain the VDOM. First enable Virtual Domains on the FortiGate unit.
To enable VDOMs - GUI
- Go to System > Dashboard > Status.
- In the System Information widget, select Enable for Virtual Domain.
Note that on FortiGate-60 series and lower models, you need to enable VDOMs in the CLI only.
The FortiGate unit logs you out. Once you log back in, you will notice that the menu structure has changed. This reflects the global settings for all Virtual Domains.
To enable VDOMs - CLI
config system global
set vdom-admin enable
end
Next, add the VDOM called accounting.
To add a VDOM - GUI
- Go to Global > VDOM > VDOM, and select Create New.
- Enter the VDOM name
accounting. - Select OK.
To add a VDOM - CLI
config vdom
edit <new_vdom_name>
end
With the Virtual Domain created, you can assign a physical interface to it, and assign it an IP address.
To assign physical interface to the accounting Virtual Domain - GUI
- Go to Global > Network > Interface.
- Select the DMZ2 port row and select Edit.
- For the Virtual Domain drop-down list, select accounting.
- Select the Addressing Mode of Manual.
- Enter the IP address for the port of 10.13.101.100/24.
- Set the Administrative Access to HTTPS and SSH.
- Select OK.
To assign physical interface to the accounting Virtual Domain - CLI
config global
config system interface
edit dmz2
set vdom accounting
set ip 10.13.101.100/24
set allowaccess https ssh
next
end

