Administration for schools
For a system administrator in a school system, it is difficult to maintain a network and access to the Internet. There are potential legal liabilities if content is not properly filtered and students gain access to pornography and other non-productive and potentially dangerous content. This section describes some basic practices administrators can employ.
Security policies
The default security policies in FortiOS allow all traffic on all ports and all IP addresses. While applying security profiles can help to block viruses, detect attacks and prevent spam, this doesn’t provide a solid overall security option. The best approach is a layered approach; the first layer being the security policy.
When creating outbound security policies, you need to identify what the students are allowed to do. Generally, they surf the web, connect to FTP sites, send and receive email, and so on.
Once you know what the students need to do, you can research the software used and determine the ports the applications use. For example, if the students only require web surfing, then there are only two ports (80 - HTTP and 443 - HTTPS) needed to complete their tasks. Setting the security policies to only allow traffic through two ports (rather than all 65,000), this will significantly lower any possible exploits. By restricting the ports to known services, means stopping the use of proxy servers, as many of them operate on a non-standard port to hide their traffic from URL filtering or HTTP inspection.
DNS
You should restrict the students use of DNS. We recommend that you point to an internal DNS server and only allow those devices out on port 53.
If there is no internal DNS server, then you should establish a restrictive list of allowed DNS servers students can use. One possible exploit would be for them to set up their own DNS server at home that serves different IPs for known hosts, such as having Google.com sent back the IP for playboy.com.
Encrypted traffic (HTTPS)
Generally speaking, students should not be allowed to access encrypted web sites. Encrypted traffic can't be sniffed, and therefore, can't be monitored. HTTPS traffic should only be allowed when necessary. Most web sites a student needs to access are HTTP, not HTTPS. Due to the nature of HTTPS protocol, and the fact that encryption is an inherent security risk to your network, its use should be restricted.
To ensure that students only visit HTTPS sites required for schoolwork, we recommend that you add a security policy that designates a list of allowed secure sites.
FTP
For the most part, students should not be using FTP. FTP is not HTTP or HTTPS so you can't use URL filtering to restrict where they go. This can be controlled with destination IPs in the security policy. With a policy that specifically outlines which FTP addresses are allowed, all other will be blocked.
Example security policies
Given these recommended practices, a set of security policies could look like the following illustration. In a large setup, all the IPs for the students are treated by one of these four policies.
Simple security policy setup
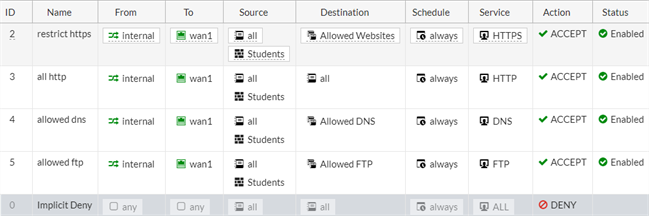
The last policy in the list is the deny policy that is configured by default. The deny policy ensures that any traffic making it to this point is stopped. It can also help in further troubleshooting by viewing the logs for denied traffic.
With these policies in place, even before packet inspection occurs, the FortiGate, and the network are fairly secure. Should any of the UTM profiles fail, there is still a basic level of security.
Security profiles
AntiVirus profiles
You should enable antivirus screening for any service that is enabled in the security policies. In the case above, HTTP, FTP, as well as POP3 and SMTP (assuming there is email access for students). There is not a virus scan option for HTTPS, because the content is encrypted. Generally speaking, most of the network traffic will be students surfing the web.
To configure antivirus profiles in the GUI, go to Security Profiles > AntiVirus.
Web filtering
We recommend that you configure your FortiGate to filter URLs, sites and content, using FortiGuard web filtering service. Web sites are constantly being monitored, and new ones reviewed and added to the FortiGuard databases every day. The FortiGuard categories provide an extensive list of offensive and non-productive sites.
There are additional settings to include in a web filtering profile to best contain a student’s web browsing. You can enable safe search, restrict YouTube access, block invalid URLs, and block malicious URLs discovered by FortiSandbox.
To configure web filtering options, go to Security Profiles > Web Filter.
Categories and classifications
The selection of what FortiGuard categories and classifications that should be blocked is based on the school system and its Internet information policy.
Email filtering
Other than specific teacher-led email inboxes, there is no reason why a student should be able to access, read or send personal email. Ports for POP3, SMTP and IMAP should not be opened in a security policy.
IPS
The intrusion prevention profiles are used to ensure the student PCs are not vulnerable to attacks and are not in a position to make attacks. As well, IPS can do more than simple vulnerability scans. With a FortiGuard subscription, IPS signatures are pushed to the FortiGate unit. New signatures are released regularly for intrusions as they are discovered.
FortiOS includes a number of predefined IPS sensors that you can enable by default. To configure IPS sensors, go to Security Profiles > Intrusion Prevention.
Application control
Application control uses IPS signatures to limit the use of instant messaging and peer-to-peer applications which can lead to possible infections on a student’s PC. FortiOS includes a number of pre-defined application categories. To configure and maintain application control profiles, go to Security Profiles > Application Control.
Some applications to consider include proxies, botnets, toolbars and P2P applications.
Logging
Turn on all logging. Every option in this section should be enabled. This is not where you decide what you are going to log. You are identifying what the profiles can log.
Logging everything is a way to monitor traffic on the network, see what student’s are utilizing the most, and locate any potential holes in your security plan. Keeping this information may help to prove negligence later if necessary.

