SD-WAN support for ADVPN 6.2.1
With this feature, SD-WAN service rules can utilize the shortcut VPN to forward traffic between spokes. Previously, spoke to spoke traffic could only be forwarded by the hub, and could not take advantage of the ADVPN feature.
This user ADVPN with SD-WAN scenario uses two hubs, and each spoke connects to two ISPs and establishes VPN tunnels with each hub.
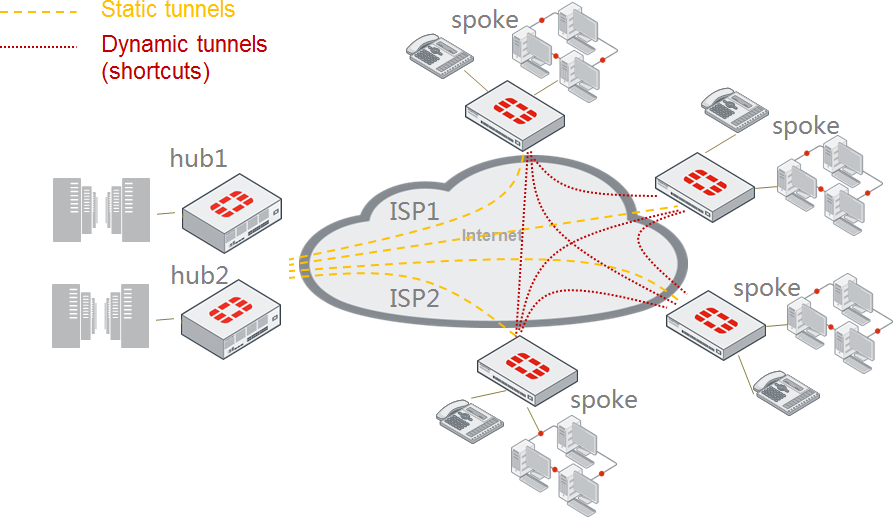
SD-WAN is configured on the spokes, and uses two VPN interfaces as members with rules to control traffic to other spokes via the ADVPN shortcut VPN interfaces.
To configure a hub:
- Configure the IPsec phase1 and phase2 interfaces:
config vpn ipsec phase1-interface edit "advpn-hub" set type dynamic set interface "port9" set peertype any set net-device disable set proposal aes128-sha256 aes256-sha256 3des-sha256 aes128-sha1 aes256-sha1 3des-sha1 set add-route disable set dpd on-idle set auto-discovery-sender enable set tunnel-search nexthop set psksecret sample set dpd-retryinterval 5 next end config vpn ipsec phase2-interface edit "advpn-hub" set phase1name "advpn-hub" set proposal aes128-sha1 aes256-sha1 3des-sha1 aes128-sha256 aes256-sha256 3des-sha256 next end - Configure firewall policies:
config firewall policy edit 1 set name "spoke2hub" set srcintf "advpn-hub" set dstintf "port10" set srcaddr "all" set dstaddr "11.11.11.0" set action accept set schedule "always" set service "ALL" next edit 2 set name "spoke2spoke" set srcintf "advpn-hub" set dstintf "advpn-hub" set srcaddr "all" set dstaddr "all" set action accept set schedule "always" set service "ALL" next end - Configure the VPN interface:
config system interface edit "advpn-hub" set ip 10.10.100.254 255.255.255.255 set remote-ip 10.10.100.253 255.255.255.0 next end - Configure BGP:
config router bgp set as 65412 config neighbor-group edit "advpn" set link-down-failover enable set remote-as 65412 set route-reflector-client enable next end config neighbor-range edit 1 set prefix 10.10.100.0 255.255.255.0 set neighbor-group "advpn" next end config network edit 1 set prefix 172.16.101.0 255.255.255.0 next end end
To configure a spoke:
- Configure the IPsec phase1 and phase2 interfaces:
config vpn ipsec phase1-interface edit "spoke1" set interface "wan1" set peertype any set net-device enable set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1 set add-route disable set dpd on-idle set auto-discovery-receiver enable set remote-gw 11.1.1.11 set psksecret sample set dpd-retryinterval 5 next edit "spoke1-2" set interface "wan2" set peertype any set net-device enable set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1 set add-route disable set dpd on-idle set auto-discovery-receiver enable set remote-gw 11.1.2.11 set monitor "spoke1" set psksecret sample set dpd-retryinterval 5 next end config vpn ipsec phase2-interface edit "spoke1" set phase1name "spoke1" set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256 aes128gcm aes256gcm chacha20poly1305 set auto-negotiate enable next edit "spoke1-2" set phase1name "spoke1_backup" set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256 aes128gcm aes256gcm chacha20poly1305 set auto-negotiate enable next end - Configure firewall policies:
config firewall policy edit 1 set name "outbound_advpn" set srcintf "internal" set dstintf "spoke1" "spoke1-2" set srcaddr "all" set dstaddr "all" set action accept set schedule "always" set service "ALL" next edit 2 set name "inbound_advpn" set srcintf "spoke1" "spoke1-2" set dstintf "internal" set srcaddr "all" set dstaddr "all" set action accept set schedule "always" set service "ALL" next end - Configure the VPN interface:
config system interface edit "spoke1" set ip 10.10.10.1 255.255.255.255 set remote-ip 10.10.10.254 255.255.255.0 next edit "spoke1-2" set ip 10.10.10.2 255.255.255.255 set remote-ip 10.10.10.254 255.255.255.0 next end - Configure BGP:
config router bgp set as 65412 config neighbor edit "10.10.100.254" set advertisement-interval 1 set link-down-failover enable set remote-as 65412 next edit "10.10.200.254" set advertisement-interval 1 set link-down-failover enable set remote-as 65412 next end config network edit 1 set prefix 10.1.100.0 255.255.255.0 next end end - Configure SD-WAN:
config system virtual-wan-link set status enable config members edit 1 set interface "vd2-1" next edit 2 set interface "vd2-2" next end config health-check edit "ping" set server "11.11.11.11" set members 1 2 end next end config service edit 1 set member 1 set dst "001-100" next edit 2 set member 2 set dst "100-200" next end end

