Protocol Port Enforcement
Protocol enforcement is added to the Application Control Profile, allowing the admin to configure network services (e.g., FTP, HTTP, HTTPS) on known ports (e.g., 21, 80, 443), while blocking those services on other ports.
The feature takes action in the following scenarios:
- When one protocol dissector confirms the service of network traffic, protocol enforcement can check whether the confirmed service is whitelisted under the server port. If it is not, then the traffic is considered a violation and IPS can take action (e.g., block) specified in the configuration.
- There is no confirmed service for the network traffic. It would be considered a service violation if IPS dissectors rule out all the services enforced under its server port.
In Security Profiles > Application Control, a new Network Protocol Enforcement pane lets you create and configure network services on specific ports and set violation action.

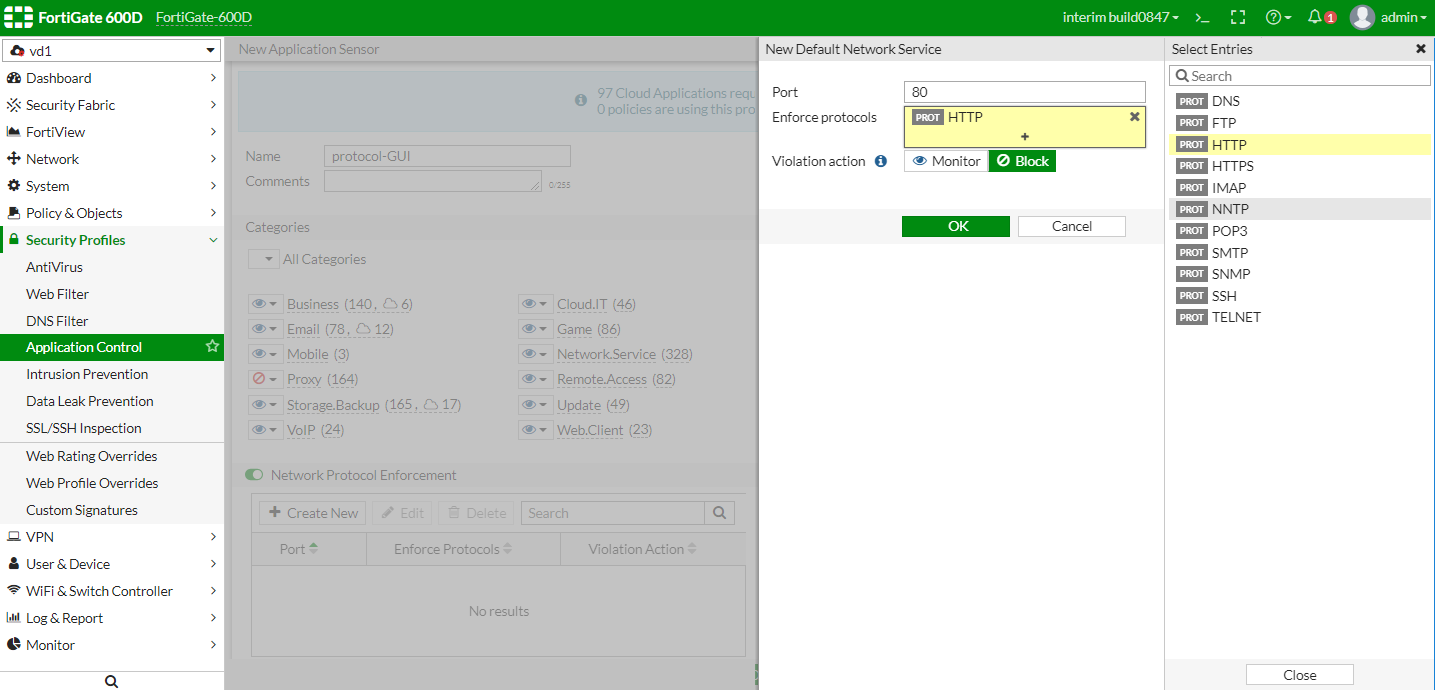
To configure the application profile default network service list using CLI:
config application list
edit "protocol-GUI"
set other-application-log enable
set control-default-network-services enable # Enable enforcement of protocols over select ports.
config default-network-services # Default network service entries
edit 1
set port 80 # Port number, port Enter an integer value from <0> to <65535>
set services http # Network protocols: http, ssh, telnet, ftp, dns, smtp, pop3, imap, snmp, nntp and https
next
edit 2
set port 53
set services dns
set violation-action monitor # Set action for protocols not whitelisted under select port: block/pass/monitor
next
end
next
end

