IAM Authentication
This feature adds the ability to use IAM credentials for Oracle Cloud Infrastructure (OCI) SDN connector functionality, including HA and dynamic address updating.
Prior to enabling IAM credentials for an SDN connector, a dynamic group and policy must configured on OCI. The SDN connector can then be configured using the FortiGate CLI or GUI.
To configure OCI:
- Create a Dynamic Group that includes rules to allow an instance that matches the FortiGate HA device's instance ID. For example:
ALL {instance.id = 'ocid1.instance.oc1.iad.abuwcljtkqllbq6yxgxtowybgc4ht6sxqpfccckjj23p6pbfmvbl52uttbiq'}
ALL {instance.id = 'ocid1.instance.oc1.iad.abuwcljttcylhekauqy42jzpsnu2dkalbhnlulqxfe2az24fktcuhtj65vnq'}
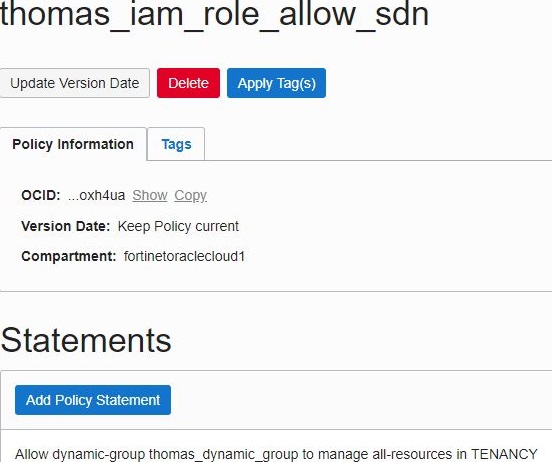
- Create a policy that allows that group to manage all resources:
Allow dynamic-group API to manage all-resources in TENANCY
To Configure the FortiGate using the CLI:
- Configure the SDN connector:
config system sdn-connector
edit "oci-sdn"
set status enable
set type oci
set ha-status enable
set tenant-id "ocid1.tenancy.oc1..aaaaaaaambr3uzztoyhweohbzqqdo775h7d3t54zpmzkp4b2cf35vs55ck3a"
set user-id "ocid1.user.oc1..aaaaaaaaq2lfspeo3uetzbzpiv2pqvzzevozccnys347stwssvizqlatfv7q"
set compartment-id "ocid1.tenancy.oc1..aaaaaaaambr3uzztoyhweohbzqqdo775h7d3t54zpmzkp4b2cf35vs55ck3a"
set oci-region ashburn
set oci-cert ''
set use-metadata-iam enable
set update-interval 60
next
end
- Confirm that the HA failover succeeds on the secondary HA device:
# diagnose debug application awsd -1 # diagnose debug enable
To Configure the FortiGate using the GUI:
- Go to Security Fabric > Fabric Connectors.
- Click Create New, then select Oracle Cloud Infrastructure (OCI) from the SDN category.
- Fill in the Name, User ID, OCI tenant ID, and OCI compartment ID.
- Enable Use metadata IAM.
- Configure the Update Interval and Status, then click OK.
- Go to Policy and Objects > Addresses to check that the dynamic address can update.