Implicit rule
SD-WAN supports five types of implicit rules (load-balance mode):
- Source IP (CLI command:
source-ip-based): SD-WAN will load balance the traffic equally among its members according to a hash algorithm based on the source IP addresses. - Session (
weight-based): SD-WAN will load balance the traffic according to the session numbers ratio among its members. - Spillover (
usage-based): SD-WAN will use the first member until the bandwidth reaches its limit, then use the second, and so on. - Source-Destination IP (
source-dest-ip-based): SD-WAN will load balance the traffic equally among its members according to a hash algorithm based on both the source and destination IP addresses. - Volume (
measured-volume-based): SD-WAN will load balance the traffic according to the bandwidth ratio among its members.
Examples
The following four examples demonstrate how to use the implicit rules (load-balance mode).
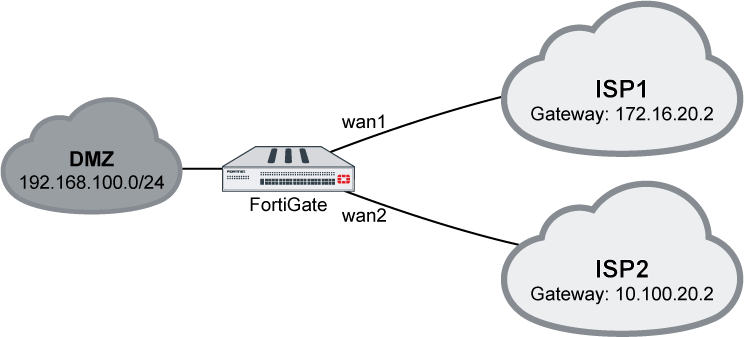
Example 1
Outgoing traffic is equally balanced between wan1 and wan2, using source-ip-based or source-dest-ip-based mode.
Using the GUI:
- On the FortiGate, enable SD-WAN and add wan1 and wan2 as SD-WAN members, then add a policy and static route. See Creating the SD-WAN interface for details.
- Go to Network > SD-WAN Rules.
- Edit the sd-wan rule (the last default rule).
- For the Load Balancing Algorithm, select either Source IP or Source-Destination IP.

- Click OK.
Using the CLI:
- Enable SD-WAN and add wan1 and wan2 as SD-WAN members, then add a policy and static route. See Creating the SD-WAN interface for details.
- Set the load balancing algorithm:
Source IP based:
config system virtual-wan-link set load-balance-mode source-ip-based endSource-Destination IP based:
config system virtual-wan-link set load-balance-mode source-dest-ip-based end
Example 2
Outgoing traffic is balanced between wan1 and wan2 with a customized ratio, using weight-based mode: wan1 runs 80% of the sessions, and wan2 runs 20% of the sessions.
Using the GUI:
- Go to Network > SD-WAN Rules.
- Edit the sd-wan rule (the last default rule).
- For the Load Balancing Algorithm, select Sessions.
- Enter 80 in the wan1 field, and 20 in the wan2 field.

- Click OK.
Using the CLI:
config system virtual-wan-link
set load-balance-mode weight-based
config members
edit 1
set interface "wan1"
set weight 80
next
edit 2
set interface "wan2"
set weight 20
next
end
end
Example 3
Outgoing traffic is balanced between wan1 and wan2 with a customized ratio, using measured-volume-based mode: wan1 runs 80% of the volume, and wan2 runs 20% of the volume.
Using the GUI:
- Go to Network > SD-WAN Rules.
- Edit the sd-wan rule (the last default rule).
- For the Load Balancing Algorithm, select Volume.
- Enter 80 in the wan1 field, and 20 in the wan2 field.
- Click OK.
Using the CLI:
config system virtual-wan-link
set load-balance-mode measured-volume-based
config members
edit 1
set interface "wan1"
set volume-ratio 80
next
edit 2
set interface "wan2"
set volume-ratio 20
next
end
end
Example 4
Load balancing can be used to reduce costs when internet connections are charged at different rates. For example, if wan2 charges based on volume usage and wan1 charges a fixed monthly fee, we can use wan1 at its maximum bandwidth, and use wan2 for overflow.
In this example, wan1's bandwidth is 10Mbps down and 2Mbps up. Traffic will use wan1 until it reaches its spillover limit, then it will start to use wan2. Note that auto‑asic‑offload must be disabled in the firewall policy.
Using the GUI:
- On the FortiGate, enable SD-WAN and add wan1 and wan2 as SD-WAN members, then add a policy and static route. See Creating the SD-WAN interface for details.
- Go to Network > SD-WAN Rules.
- Edit the sd-wan rule (the last default rule).
- For the Load Balancing Algorithm, select Spillover.
- Enter 10000 in the wan1 Ingress Spillover Threshold field, and 2000 in the wan1 Egress Spillover Threshold field.

- Click OK.
Using the CLI:
config system virtual-wan-link
set load-balance-mode usage-based
config members
edit 1
set interface "wan1"
set spillover-threshold 2000
set ingress-spillover-threshold 10000
next
end
end

