ZTNA HTTPS access proxy example
In this example, an HTTPS access proxy is configured to demonstrate its function as a reverse proxy on behalf of the web server it is protecting. It verifies user identity, device identity, and trust context, before granting access to the protected source.
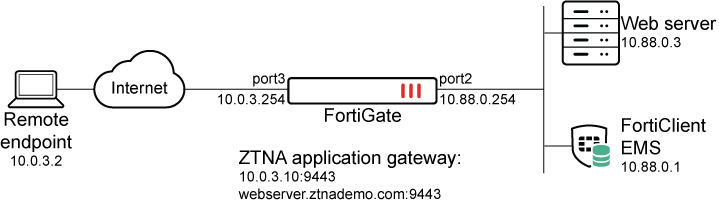
This example shows access control that allows or denies traffic based on security posture tags. Traffic is allowed when the FortiClient endpoint is tagged as Low Importance using Classification tags, and denied when the endpoint is tagged with Malicious-File-Detected.
This example assumes that the FortiGate EMS fabric connector is already successfully connected.
|
|
To configure ZTNA in the GUI, go to System > Feature Visibility and enable Zero Trust Network Access. |
To configure a Zero Trust tagging rule on the FortiClient EMS:
-
Log in to the FortiClient EMS.
-
Go to Zero Trust Tags > Zero Trust Tagging Rules, and click Add.
-
In the Name field, enter Malicious-File-Detected.
-
In the Tag Endpoint As dropdown list, select Malicious-File-Detected.
EMS uses this tag to dynamically group together endpoints that satisfy the rule, as well as any other rules that are configured to use this tag.
-
Click Add Rule then configure the rule:
-
For OS, select Windows.
-
From the Rule Type dropdown list, select File and click the + button.
-
Enter a file name, such as C:\virus.txt.
-
Click Save.
-
-
Click Save.
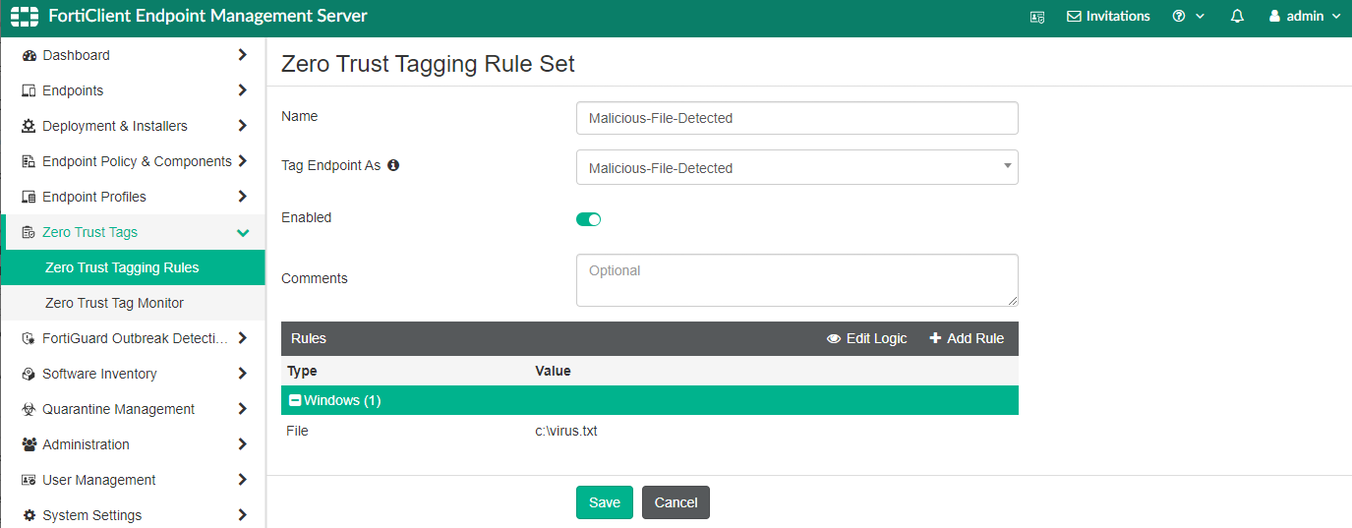
To configure FortiClient EMS to share classification tags:
-
Go to Administration > Fabric Devices.
-
Select the FortiGate device.
-
Click Edit.
-
Under Tag Types Being Shared, add Classification Tags.
-
Click Save.
To configure a ZTNA server for HTTPS access proxy in the GUI:
-
Go to Policy & Objects > ZTNA and select the ZTNA Server tab.
-
Click Create New.
-
Set Name to ZTNA-webserver.
-
Set Interface to port3. The IP address and Port fields are automatically set to the IP of the selected interface and the default port of 443.
- Set External IP to 10.0.3.10.
- Set External port to 9443.

Verify that the IP address and port do not conflict with management access to the interface. Otherwise, change the IP address to another address on that subnet.
-
Select the Default certificate. Clients will be presented with this certificate when they connect to the access proxy VIP.
-
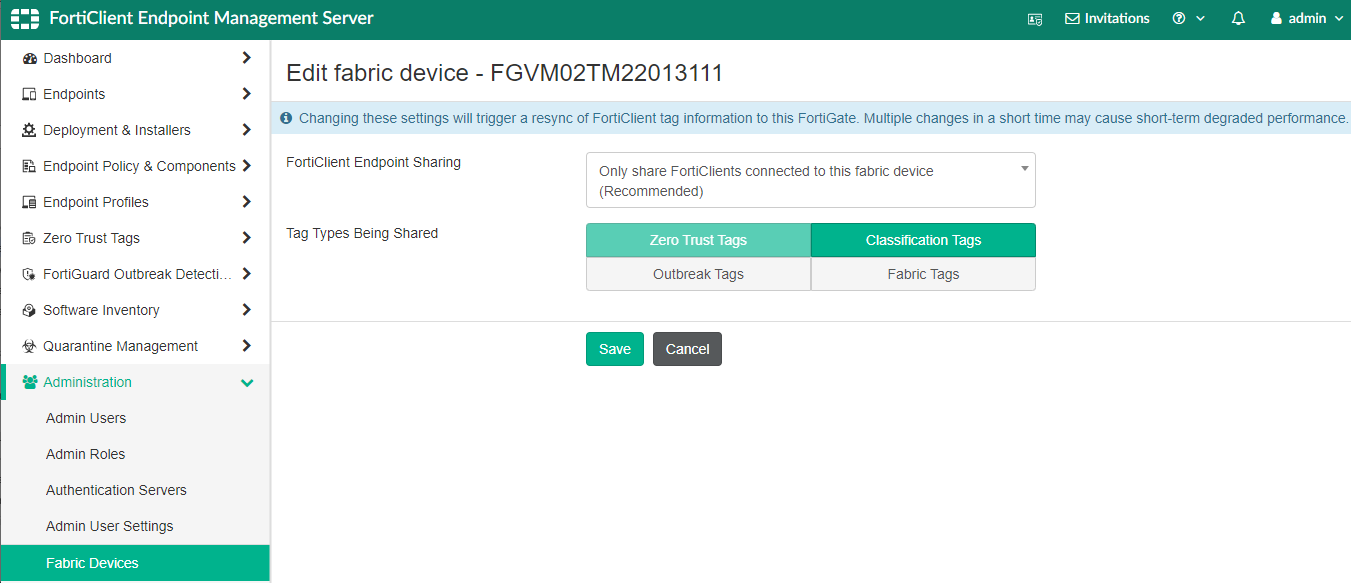
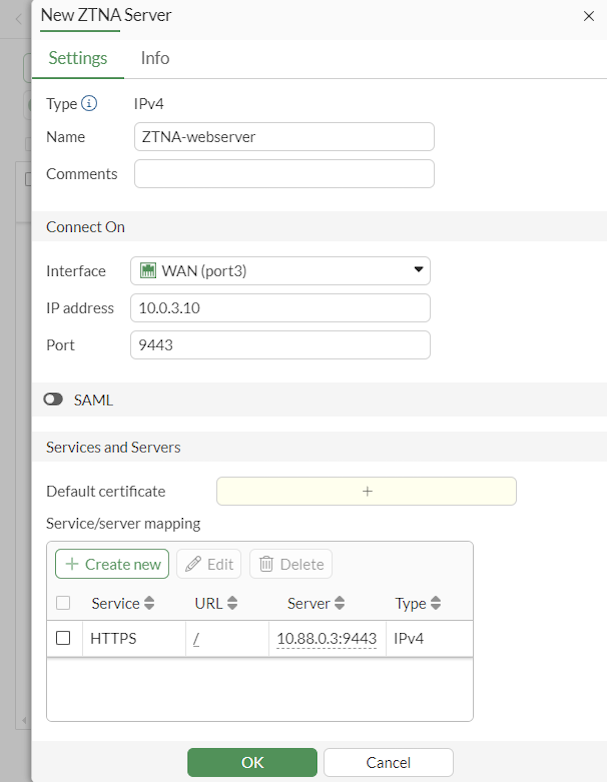
Add server mapping:
-
In the Service/server mapping table, click Create New.
-
Set Service to HTTPS.
-
Set Virtual Host to Any Host.
-
Configure the path as needed. For example, to map to webserver.ztnademo.com/fortigate, enter /fortigate.
-
In the Server section, set Address type to IP.
-
Set IP address to 10.88.0.3.
-
Set Port to 9443.
-
Click OK. The server mapping is displayed.
-
-
Click OK.
To configure simple ZTNA policies to allow and deny traffic based on security posture tags in the GUI:
-
Go to Policy & Objects > Firewall Policy.
-
Create a rule to deny traffic:
-
Click Create New.
-
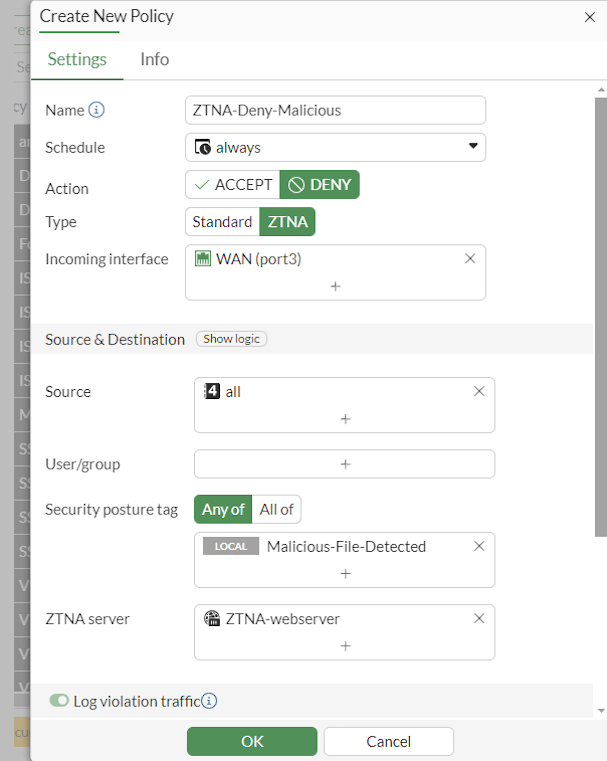
Set Name to ZTNA-Deny-malicious.
-
Set Action to DENY.
-
Set Type to ZTNA.
-
Set Incoming Interface to port3.
-
Set Source to all.
-
Add the security posture tag Malicious-File-Detected.
This tag is dynamically retrieved from EMS when you first created the Zero Trust Tagging Rule.
-
Select the ZTNA server ZTNA-webserver.
-
Enable Log Violation Traffic.
-
Click OK.
-
-
Create a rule to allow traffic:
-
Click Create New.
-
Set Name to ZTNA-Allow-Simple.
-
Set Type to ZTNA.
-
Set Incoming Interface to port3.
-
Set Source to all. This can also be set to specific IP addresses to only allow those addresses to connect to this HTTPS access proxy.
-
Add the Class tag Low.
-
Select the ZTNA server ZTNA-webserver.
-
Configure the remaining options as needed.
-
Click OK.
-
-
On the firewall policy list, make sure that the deny rule (ZTNA-Deny-malicious) is above the allow rule (ZTNA-Allow-Simple).
To configure HTTPS access in the CLI:
-
Configure the access proxy VIP:
config firewall vip edit "ZTNA-webserver" set type access-proxy set extip 10.0.3.10 set extintf "port3" set server-type https set extport 9443 set ssl-certificate "ztna-wildcard" next end -
Configure the server and path mapping:
config firewall access-proxy edit "ZTNA-webserver" set vip "ZTNA-webserver" set log-blocked-traffic enable config api-gateway edit 1 config realservers edit 1 set ip 10.88.0.3 set port 9443 next end next end next end -
Configure ZTNA policies:
config firewall policy edit 9 set name "ZTNA-Deny-Malicious" set srcintf "port3" set dstintf "any" set srcaddr "all" set dstaddr "ZTNA-webserver" set ztna-ems-tag "EMS1_ZTNA_Malicious-File-Detected" set schedule "always" set logtraffic all next edit 10 set name "ZTNA-Allow-Simple" set srcintf "port3" set dstintf "any" set action accept set srcaddr "all" set dstaddr "ZTNA-webserver" set ztna-ems-tag "EMS1_CLASS_Low" set schedule "always" set logtraffic all set nat enable next end
For configuration examples using full ZTNA policy, see Configure a ZTNA policy.
Testing the remote access to the HTTPS access proxy
After FortiClient EMS and FortiGate are configured, the HTTPS access proxy remote connection can be tested.
Access allowed:
-
On the remote Windows PC, open FortiClient.
-
On the Zero Trust Telemetry tab, make sure that you are connected to the EMS server.

It is not necessary to configure a ZTNA Destination on FortiClient for the HTTPS access proxy use case. In fact, configuring a ZTNA Destination rule for the website may interfere with its operation.
-
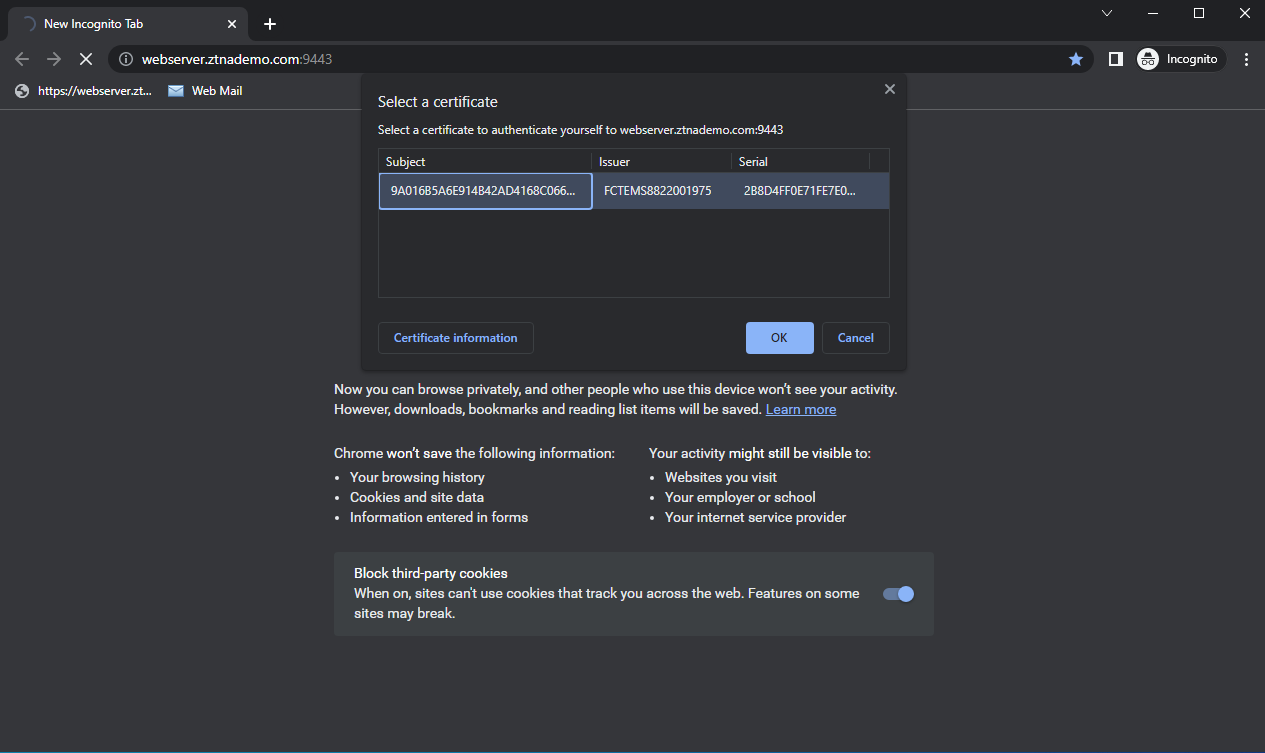
Open a browser and enter the address of the server and the access port. When entering the FQDN, make sure that the DNS can resolve the address to the IP address of the FortiGate. In this example, webserver.ztnademo.com resolves to 10.0.3.10.
-
The browser prompts for the client certificate to use. Select the EMS signed certificate, then click OK.
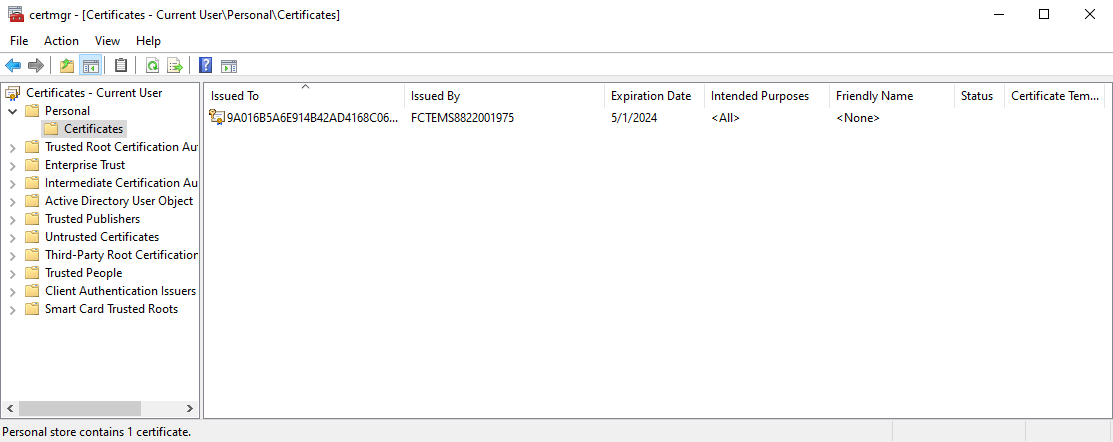
The certificate is in the User Configuration store, under Personal > Certificates. The details show the SN of the certificate, which matches the record on the FortiClient EMS and the FortiGate.
-
The client is verified by the FortiGate to authenticate your identity.
-
The FortiGate matches your security posture by verifying your security posture tag and matching the corresponding ZTNA rule, and you are allowed access to the web server.
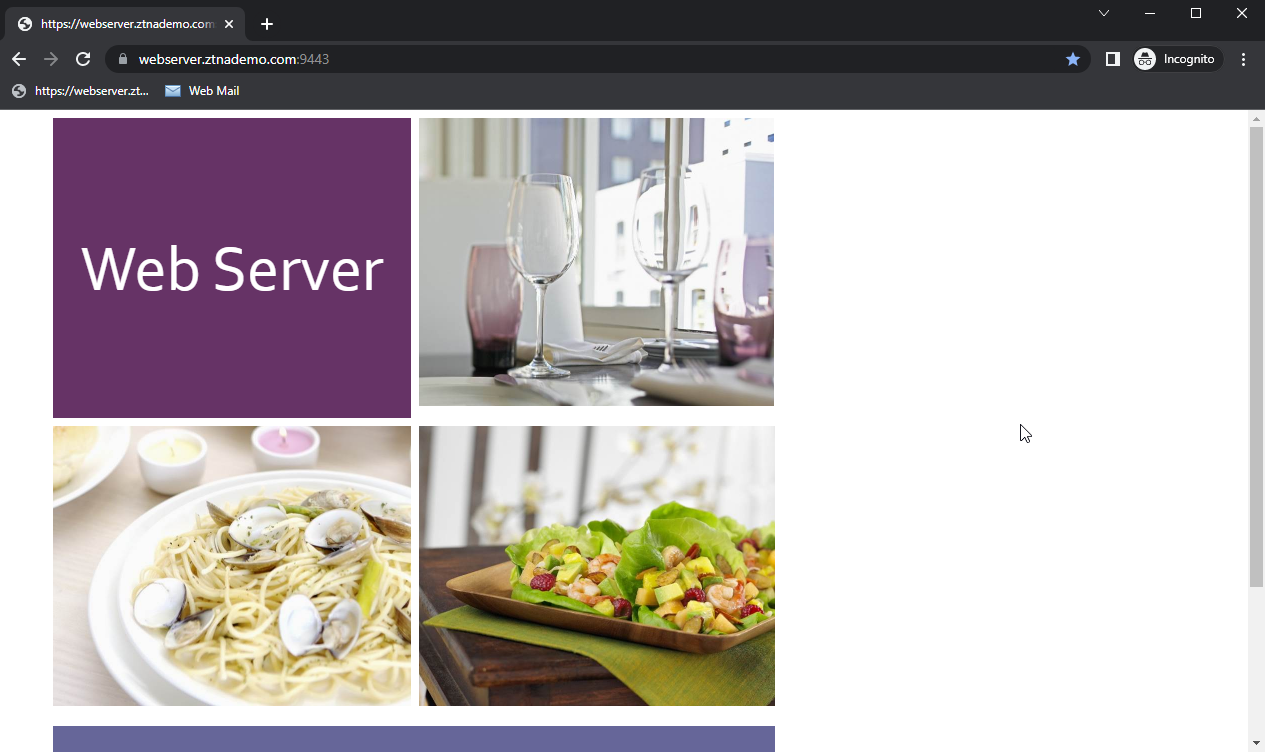
Access denied:
-
On the remote Windows PC, trigger the Zero Trust Tagging Rule by creating the file in C:\virus.txt.
-
Open a browser and enter the address http://webserver.ztnademo.com:9443.
-
The client is verified by the FortiGate to authenticate your identity.
-
FortiGate checks your security posture. Because EMS has tagged the PC with the Malicious-File-Detected tag, it matches the ZTNA-Deny-malicious rule.
-
You are denied access to the web server.
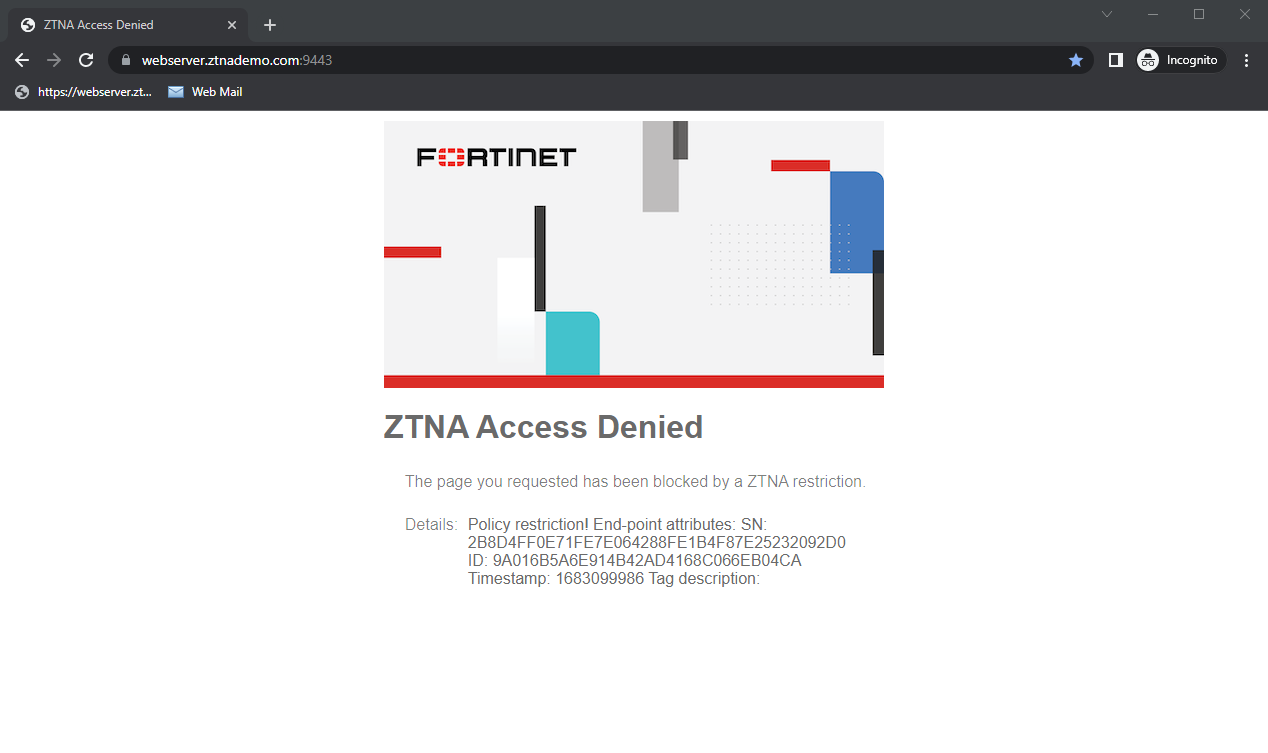
Logs and debugs
Access allowed:
# diagnose endpoint ec-shm list
Record 0:
IP Address = 10.0.3.2
MAC Address = 02:09:0f:00:03:03
MAC list =
VDOM = (-1)
EMS serial number: FCTEMS8822001975
EMS tenant id: 00000000000000000000000000000000
Client cert SN: 2B8D4FF0E71FE7E064288FE1B4F87E25232092D0
Public IP address: 34.23.223.220
Quarantined: no
Online status: online
Registration status: registered
On-net status: on-net
Gateway Interface:
FortiClient version: 7.2.0
AVDB version: 1.0
FortiClient app signature version: 23.544
FortiClient vulnerability scan engine version: 2.34
FortiClient UID: 9A016B5A6E914B42AD4168C066EB04CA
Host Name: WIN10-01
OS Type: WIN64
…
Number of Routes: (0)
online records: 1; offline records: 0; quarantined records: 0; out-of-sync records: 0
# diagnose test application fcnacd 7 Entry #1: - UID: 9A016B5A6E914B42AD4168C066EB04CA - EMS Fabric ID: FCTEMS8822001975:00000000000000000000000000000000 - Sys upd time: 2023-05-03 07:32:24.0367058 - Tag upd time: 2023-05-03 07:32:24.0367058 lls_idx_mask = 0x00000001 #ID:0 UID: 9A016B5A6E914B42AD4168C066EB04CA State: sysinfo:1, tag:1, tagsz:1, out-of-sync:0 Owner: Cert SN: 2B8D4FF0E71FE7E064288FE1B4F87E25232092D0 online: Yes Route IP:0.0.0.0 vfid: 0 has more:No Tags: idx:0, ttdl:1 name:Domain-Users idx:1, ttdl:1 name:Remote-Allowed idx:2, ttdl:1 name:Group-Membership-Domain-Users idx:3, ttdl:2 name:Low idx:4, ttdl:2 name:Remote idx:5, ttdl:1 name:all_registered_clients
# diagnose wad dev query-by uid 9A016B5A6E914B42AD4168C066EB04CA FCTEMS8822001975 00000000000000000000000000000000 Attr of type=0, length=83, value(ascii)=9A016B5A6E914B42AD4168C066EB04CA Attr of type=4, length=0, value(ascii)= Attr of type=6, length=1, value(ascii)=true Attr of type=5, length=40, value(ascii)=2B8D4FF0E71FE7E064288FE1B4F87E25232092D0 Attr of type=3, length=66, value(ascii)=ZTNA_Domain-Users_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=68, value(ascii)=ZTNA_Remote-Allowed_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=83, value(ascii)=ZTNA_Group-Membership-Domain-Users_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=58, value(ascii)=CLASS_Low_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=61, value(ascii)=CLASS_Remote_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=76, value(ascii)=ZTNA_all_registered_clients_FCTEMS882200197500000000000000000000000000000000 Response termination due to no more data
# execute log filter category 0 # execute log filter field subtype ztna # execute log display 1: date=2023-05-03 time=00:42:22 eventtime=1683099742638807678 tz="-0700" logid="0005000024" type="traffic" subtype="ztna" level="notice" vd="root" srcip=10.0.3.2 srcport=35553 srcintf="port3" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.88.0.3 dstport=9443 dstintf="port2" dstintfrole="dmz" sessionid=7258 srcuuid="b458a65a-f759-51ea-d7df-ef2e750026d1" service="tcp/9443" proxyapptype="http" proto=6 action="accept" policyid=10 policytype="policy" poluuid="92d54e0e-e949-51ed-5dba-7b4724d33d52" policyname="ZTNA-Allow-Simple" duration=599 gatewayid=1 realserverid=1 vip="ZTNA-webserver" accessproxy="ZTNA-webserver" clientdeviceid="9A016B5A6E914B42AD4168C066EB04CA" clientdevicemanageable="manageable" clientdevicetags="EMS1_ZTNA_all_registered_clients/EMS1_CLASS_Remote" emsconnection="online" wanin=301677 rcvdbyte=301677 wanout=3177 lanin=2716 sentbyte=2716 lanout=302368 fctuid="9A016B5A6E914B42AD4168C066EB04CA" appcat="unscanned"
Access denied:
# diagnose test application fcnacd 7 Entry #1: - UID: 9A016B5A6E914B42AD4168C066EB04CA - EMS Fabric ID: FCTEMS8822001975:00000000000000000000000000000000 - Sys upd time: 2023-05-03 07:32:24.0367058 - Tag upd time: 2023-05-03 07:45:20.0034279 lls_idx_mask = 0x00000001 #ID:0 UID: 9A016B5A6E914B42AD4168C066EB04CA State: sysinfo:1, tag:1, tagsz:1, out-of-sync:0 Owner: Cert SN: 2B8D4FF0E71FE7E064288FE1B4F87E25232092D0 online: Yes Route IP:0.0.0.0 vfid: 0 has more:No Tags: idx:0, ttdl:1 name:Domain-Users idx:1, ttdl:1 name:Remote-Allowed idx:2, ttdl:1 name:Group-Membership-Domain-Users idx:3, ttdl:2 name:Low idx:4, ttdl:1 name:Malicious-File-Detected idx:5, ttdl:2 name:Remote idx:6, ttdl:1 name:all_registered_clients
# diagnose wad dev query-by uid 9A016B5A6E914B42AD4168C066EB04CA FCTEMS8822001975 00000000000000000000000000000000 Attr of type=0, length=83, value(ascii)=9A016B5A6E914B42AD4168C066EB04CA Attr of type=4, length=0, value(ascii)= Attr of type=6, length=1, value(ascii)=true Attr of type=5, length=40, value(ascii)=2B8D4FF0E71FE7E064288FE1B4F87E25232092D0 Attr of type=3, length=66, value(ascii)=ZTNA_Domain-Users_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=68, value(ascii)=ZTNA_Remote-Allowed_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=83, value(ascii)=ZTNA_Group-Membership-Domain-Users_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=58, value(ascii)=CLASS_Low_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=77, value(ascii)=ZTNA_Malicious-File-Detected_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=61, value(ascii)=CLASS_Remote_FCTEMS882200197500000000000000000000000000000000 Attr of type=3, length=76, value(ascii)=ZTNA_all_registered_clients_FCTEMS882200197500000000000000000000000000000000 Response termination due to no more data
# execute log display 1: date=2023-05-03 time=00:46:26 eventtime=1683099986322746507 tz="-0700" logid="0005000024" type="traffic" subtype="ztna" level="notice" vd="root" srcip=10.0.3.2 srcport=35731 srcintf="port3" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.0.3.10 dstport=9443 dstintf="root" dstintfrole="undefined" sessionid=7574 srcuuid="b458a65a-f759-51ea-d7df-ef2e750026d1" dstuuid="96e98cb0-e937-51ed-3e8b-9ee64af51512" service="tcp/9443" proxyapptype="http" proto=6 action="deny" policyid=9 policytype="proxy-policy" poluuid="3aa15b1a-e949-51ed-6b93-77ca8d2c4d6e" policyname="ZTNA-Deny-Malicious" duration=0 vip="ZTNA-webserver" accessproxy="ZTNA-webserver" clientdeviceid="9A016B5A6E914B42AD4168C066EB04CA" clientdevicemanageable="manageable" clientdevicetags="EMS1_ZTNA_all_registered_clients/EMS1_CLASS_Remote" emsconnection="online" msg="Traffic denied because of proxy-policy action is deny. Matched tag: EMS1_ZTNA_Malicious-File-Detected" wanin=0 rcvdbyte=0 wanout=0 lanin=2375 sentbyte=2375 lanout=2506 fctuid="9A016B5A6E914B42AD4168C066EB04CA" appcat="unscanned" crscore=30 craction=131072 crlevel="high"

