Consolidated IPv4 and IPv6 policy configuration
IPv4 and IPv6 policy configuration are consolidated in both NGFW profile-based and NGFW policy-based modes. When creating a policy, both IPv4 and IPv6 addresses can be added as sources and destinations.
The IP version of the sources and destinations in a policy must match. For example, a policy cannot have only an IPv4 source and an IPv6 destination.
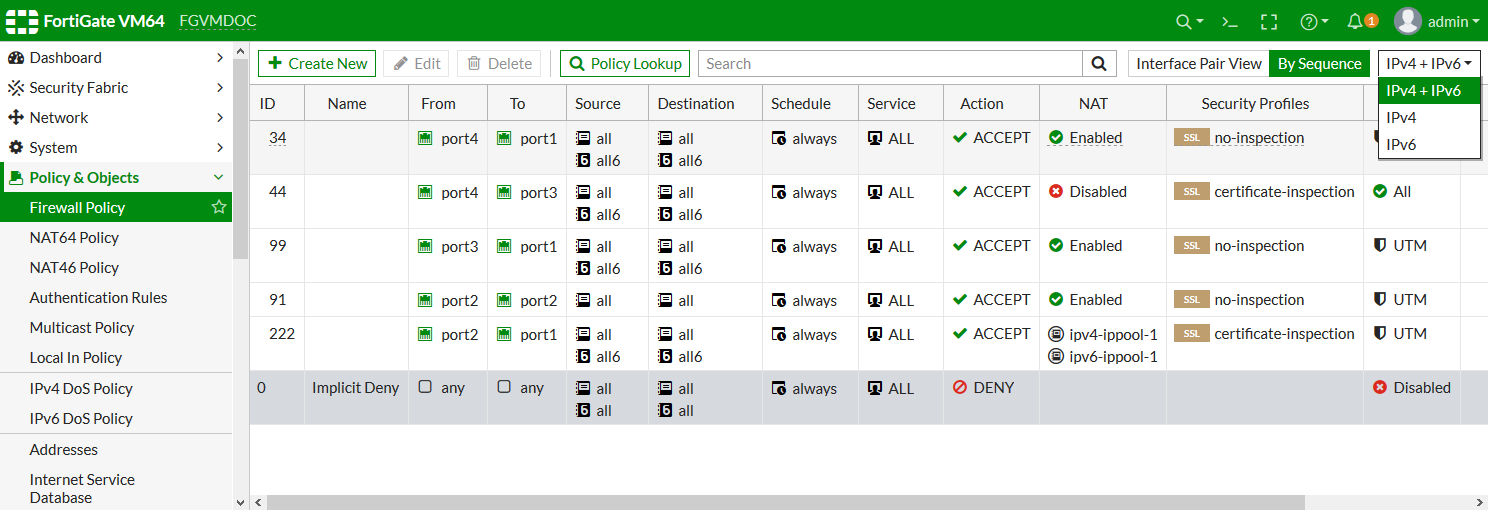
The policy list can be filtered to show policies with IPv4, IPv6, or IPv4 and IPv6 sources and destinations.
When upgrading from FortiOS 6.2.3 and later to 6.4.0 and later:
- In NGFW profile-based mode, IPv4 and IPv6 policies will all be added to the Firewall Policy list, with IPv6 policies listed after IPv4 policies. If consolidated policy mode is enabled, consolidated policies will be changed to firewall policies.
- In NGFW policy-based mode, policies will be changed from consolidated policies to firewall policies in the CLI.
- The
config firewall policy6andconfig firewall consolidated policycommands, and theconsolidated-firewall-modevariable in theconfig system settingscommand, are all removed.
|
|
By default, IPv6 options are not visible. See Feature visibility for instructions on making them visible. |
NGFW Profile-based mode
To configure an IPv4 and IPv6 firewall policy in the CLI:
config firewall policy
edit 99
set srcintf "port3"
set dstintf "port1"
set srcaddr "all"
set dstaddr "all"
set srcaddr6 "all6"
set dstaddr6 "all6"
set action accept
set schedule "always"
set service "ALL"
set nat enable
set ippool enable
set poolname "ipv4-ippool-1"
set poolname6 "ipv6-ippool-1"
next
end
To check the iprope lists for the policy:
# diagnose firewall iprope list 100004
policy index=99 uuid_idx=56 action=accept
flag (8050108): redir nat master use_src pol_stats
flag2 (4000): resolve_sso
flag3 (20): link-local
schedule(always)
cos_fwd=255 cos_rev=255
group=00100004 av=00004e20 au=00000000 split=00000000
host=1 chk_client_info=0x0 app_list=0 ips_view=0
misc=0
zone(1): 11 -> zone(1): 9
source(1): 0.0.0.0-255.255.255.255, uuid_idx=21,
dest(1): 0.0.0.0-255.255.255.255, uuid_idx=21,
service(1):
[0:0x0:0/(0,65535)->(0,65535)] helper:auto
nat(1): flag=1 base=0.0.0.0:0 2.2.2.30-2.2.2.40(0:0)# diagnose firewall iprope6 list 100004
policy id: 99, group: 00100004, uuid_idx=56
action: accept, schedule: always
cos_fwd=255 cos_rev=255
flag (08050108): redir nat master use_src pol_stats
flag2(00004000): resolve_sso
shapers: / per_ip=
sub_groups: av 00004e20 auth 00000000 split 00000000 misc 00000000
app_list: 0 ips_view: 0
vdom_id: 1
zone_from(1): 11
zone_to(1): 9
address_src(1):
all uuid_idx=40
address_dst(1):
all uuid_idx=40
service(1):
[0:0x0:0/(0,65535)->(0,65535)] helper:auto
nat(1):
flag=1 base=::(:0)
2003::2003 - 2003::2004(0:0)
NGFW Policy-based mode
To configure an IPv4 and IPv6 SSL Inspection & Authentication policy in the CLI:
config firewall policy
edit 2
set srcintf "port24"
set dstintf "port17"
set srcaddr "all"
set dstaddr "all"
set srcaddr6 "all"
set dstaddr6 "all"
set service "ALL"
set auto-asic-offload disable
next
end
To configure an IPv4 and IPv6 security policy in the CLI:
config firewall security-policy
edit 1
set comments "test"
set srcintf "port24"
set dstintf "port17"
set srcaddr "all"
set dstaddr "all"
set srcaddr6 "all"
set dstaddr6 "all"
set enforce-default-app-port disable
set service "ALL"
set action accept
set schedule "always"
set logtraffic all
next
end

