Tests for FortiSwitch added to Security Rating 6.4.2
Six new scenarios have been added in the Security Rating to test the FortiSwitch network and make recommendations to optimize the setup.
The following tests can be accessed by going to Security Fabric > Security Rating and clicking the Optimization scorecard.
Managed Switch Capacity Exceeded on FortiGate:
This test checks for the number of FortiSwitches managed by the downstream FortiGates that have exceeded 80% of the limit. The score is calculated individually and then averaged out. If the number of connected FortiSwitches is equal or greater than the maximum limit, then the result is a fail.
Users can upgrade to higher capacity FortiGates or add more FortiGates to the Security Fabric so the FortiSwitches can be split between multiple FortiGates.
In this example, the downstream FortiGates passed.

Redundant FortiLinks:
This test checks for redundant FortiLinks between the FortiGate and the FortiSwitch. There are multiple ports dedicated to FortiLink on FortiSwitches directly connected to FortiGates. FortiSwitches that are not directly connected to the FortiGate are exempt from this test. If there are no redundant FortiLinks, then the result is a fail.
In this example, the FortiGate failed. The Recommendations section lists which FortiSwitches require redundant FortiLinks.

Redundant ISL:
For FortiSwitches with inter-switch links (ISL), this test checks for two redundant links. If there is only one link, then the result is a fail. The Recommendations section lists which devices require an additional link. FortiSwitches with inter-chassis links (ICL) are exempt from the test.
In this example, the devices passed.

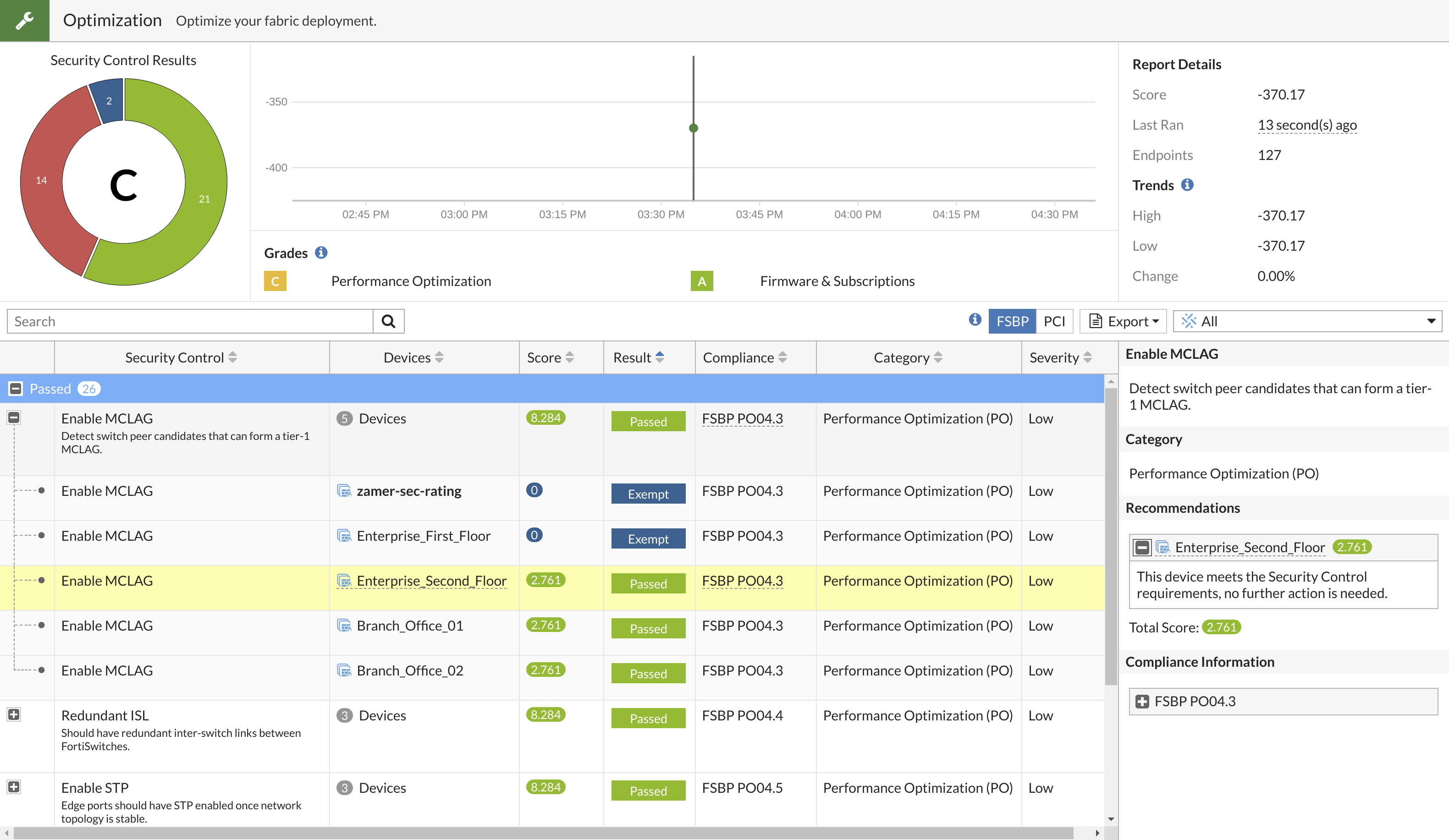
Enable MCLAG:
This test checks for candidate FortiSwitches that can form a tier-1 MCLAG. To do this, the FortiSwitches must be connected to each other and directly connected to the FortiGate. The FortiSwitch must support MCLAG. If an MCLAG already exists, this check is skipped.
In this example, three devices passed the test and two devices were exempt.
Lockdown LLDP Profile:
This test ensures that there are no accidental changes to the topology. For edge ports (not FortiLink or ISL), FortiOS suggests using the default LLDP profile. The test verifies the following:
- Looks for an edge port that has an auto-ISL LLDP profile
- Checks if the edge port BPDU guard is disabled
- Check if the FortiGate DHCP server and switches do not have a DHCP key
In this example, the devices failed. The EZ (Easy Apply) symbol appears, and port configurations to optimize the Security Fabric can be applied in the Recommendations section.

Enable STP:
This test checks if STP is enabled on edge ports. Once the network topology is stable, edge ports should have STP enabled to optimize the Security Fabric. In this example, the devices passed.


