Testing an antivirus profile
Antivirus (AV) profiles can be tested using various file samples to confirm whether AV is correctly configured. In this topic, an AV profile is configured, applied to a firewall policy, and a user attempts to download sample virus test files hosted on eicar.org and fortiguard.com.
Different sample files are used to verify different features on the AV profile. The expectation is these files must be blocked by the AV profile, and the user should be presented with a block page.
|
File |
Test case |
|---|---|
|
A plain text EICAR test file (hosted on eicar.org over a HTTPS connection) to test basic AV scanning on the FortiGate using deep inspection. |
|
|
A machine learning sample file to test AI-based malware detection on the FortiGate. |
|
|
A zero-day sample virus file to test the outbreak prevention feature of the AV profile. |
|
|
Files that are detected by a sandbox. This requires FortiSandbox integration with the FortiGate. |
Basic configuration
For the following AV test cases, the test PC has an IP of 192.168.1.110/24 and is connected to the internal1 interface. It accesses the internet through the wan1 interface.

Configuring the AV profile
The default AV profile is used, and the Use FortiGuard outbreak prevention database setting is enabled with the action set to block.
To configure the AV profile:
-
Go to Security Profiles > AntiVirus and edit the default profile.
-
In the Virus Outbreak Prevention section, enable Use FortiGuard outbreak prevention database and select Block. See FortiGuard outbreak prevention for more information about this setting.
-
Configure the other settings as needed (see Configuring an antivirus profile).
-
Click OK.
By default, the FortiOS AV Engine has AI-based malware detection enabled (set machine-learning-detection enable) . The AV Engine AI malware detection model integrates into regular AV scanning to help detect potentially malicious Windows Portable Executables (PEs) in order to mitigate zero-day attacks. See AI-based malware detection for more information.
To verify the status of the AV Engine AI contract:
# diagnose autoupdate versions | grep AI -A6 AI/Machine Learning Malware Detection Model --------- Version: 2.12588 signed Contract Expiry Date: Tue Jul 9 2024 Last Updated using scheduled update on Tue Sep 5 08:23:15 2023 Last Update Attempt: Tue Sep 5 09:23:00 2023 Result: No Updates
Configuring the SSL SSH profile and firewall policy
The PC will be accessing and downloading the test files using HTTPS from the EICAR and the FortiGuard websites. Since HTTPS traffic is encrypted traffic, in order for the FortiGate to scan the encrypted traffic and inspect it for viruses and malware, it should act as the machine-in-the-middle to decrypt this communication and then re-encrypt it to send it to the website. Deep inspection must be enabled in the SSL SSH profile that will be applied to the firewall policy (see Deep inspection). The custom-deep-inspection profile is modified to remove the fortinet FQDN address from the exemption list.
To configure the SSL SSH profile:
-
Go to Security Profiles > SSL/SSH Inspection and edit the custom-deep-inspection profile.
-
In the Exempt from SSL Inspection section, locate the fortinet FQDN entry in the Addresses field, and click the X to delete it.
-
Click OK.
To configure the firewall policy:
-
Go to Policy & Objects > Firewall Policy and click Create New.
-
Configure the following settings:
Name
To Internet
Incoming Interface
internal1
Outgoing Interface
wan1
AntiVirus
Enable and select default.
SSL Inspection
Select custom-deep-inspection.
-
Configure the other settings as needed (see Firewall policy).

The feature set setting (proxy or flow) in the antivirus profile must match the inspection mode setting (proxy or flow) in the associated firewall policy. For example, a flow-based antivirus profile must be used with a flow-based firewall policy.
-
Click OK.
Example 1: EICAR test file
EICAR hosts anti-malware test files, which are available to download from https://www.eicar.org/download-anti-malware-testfile.
To test the AV profile with the EICAR test file:
-
On the PC, go to the EICAR website and download the eicar.com file.
-
The download attempt is blocked by the FortiGate’s default AV profile, and a block page appears in the PC's browser.

-
Verify the AV log.
-
In the GUI, go to Log & Report > Security Events and select the AntiVirus card. Select the log entry and click Details.
-
In the CLI, enter the following:
# execute log filter category 2 # execute log display date=2023-08-30 time=14:51:26 eventtime=1693432286598227820 tz="-0700" logid="0211008192" type="utm" subtype="virus" eventtype="infected" level="warning" vd="root" policyid=1 poluuid="c65fa590-4758-51ee-4d28-f2cc75f14979" policytype="policy" msg="File is infected." action="blocked" service="HTTPS" sessionid=15797 srcip=192.168.1.110 dstip=89.238.73.97 srcport=64641 dstport=443 srccountry="Reserved" dstcountry="Germany" srcintf="internal1" srcintfrole="undefined" dstintf="wan1" dstintfrole="wan" srcuuid="ab8d1c24-30b1-51ee-138a-f7be846c205d" dstuuid="ab8d1c24-30b1-51ee-138a-f7be846c205d" proto=6 direction="incoming" filename="eicar.com" quarskip="Quarantine-disabled" virus="EICAR_TEST_FILE" viruscat="Virus" dtype="av-engine" ref="http://www.fortinet.com/ve?vn=EICAR_TEST_FILE" virusid=2172 url="https://secure.eicar.org/eicar.com" profile="default" agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0" httpmethod="GET" referralurl="https://www.eicar.org/" analyticscksum="275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f" analyticssubmit="false" crscore=50 craction=2 crlevel="critical"
-
Example 2: AI sample file
FortiGuard provides several sample files to test the AV configuration on the FortiGate, which are available to download from https://www.fortiguard.com/sample-files.
To test the AV profile with the AI sample file:
-
On the PC, go to the FortiGuard website and download the AI Sample file.
-
The download attempt is blocked by the FortiGate’s default AV profile, and a block page appears in the PC's browser.

The file is blocked due to AI-based malware detection and will be logged. Files detected by the AV Engine AI are identified with the W32/AI.Pallas.Suspicious virus signature in the AV logs.
-
Verify the AV log.
-
In the GUI, go to Log & Report > Security Events and select the AntiVirus card. Select the log entry and click Details.
-
In the CLI, enter the following:
# execute log filter category 2 # execute log display date=2023-08-30 time=17:28:57 eventtime=1693441737721077640 tz="-0700" logid="0211008192" type="utm" subtype="virus" eventtype="infected" level="warning" vd="root" policyid=1 poluuid="c65fa590-4758-51ee-4d28-f2cc75f14979" policytype="policy" msg="File is infected." action="blocked" service="HTTPS" sessionid=1179 srcip=192.168.1.110 dstip=209.52.38.129 srcport=63117 dstport=443 srccountry="Reserved" dstcountry="Canada" srcintf="internal1" srcintfrole="undefined" dstintf="wan1" dstintfrole="wan" srcuuid="6c43f8d6-478a-51ee-95d8-31177232e869" dstuuid="6c43f8d6-478a-51ee-95d8-31177232e869" proto=6 direction="incoming" filename="ai_sample1" quarskip="Quarantine-disabled" virus="W32/AI.Pallas.Suspicious" viruscat="Virus" dtype="av-engine" ref="http://www.fortinet.com/ve?vn=W32%2FAI.Pallas.Suspicious" virusid=8187637 url="https://filestore.fortinet.com/fortiguard/test-files/ml/ai_sample1" profile="default" agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/117.0" httpmethod="GET" referralurl="https://www.fortiguard.com/" analyticscksum="7057e364dbf09b6de7a6cc152b8967e50ed86a0edf97cfd2e88b142ac41873f0" analyticssubmit="false" crscore=50 craction=2 crlevel="critical"
-
-
Verify the AV (scanunit daemon) real-time debug:
# diagnose sys scanunit debug all # diagnose sys scanunit debug level verbose su 4655 req vfid 0 id 2 ep 0 new request from ipsengine pid 4998, size 4096, fwd-pol 1, oversize 0, url-exempt 0x0, ff-done 0, partial-data 0, dir srv->clt, http-block 0 su 4655 job 157 req vfid 0 id 2 ep 0 received; ack 157, data type: 2 su 4655 job 157 request info: su 4655 job 157 client N/A server N/A su 4655 job 157 object_name 'ai_sample1' su 4655 job 157 heuristic scan enabled su 4655 job 157 enable databases 0f (core avai mmdb extended) su 4655 job 157 scan file 'ai_sample1' bytes 4096 su 4655 job 157 file-hash query, level 0, filename 'ai_sample1' size 4096 su 4655 job 157 sha1 'e027a991fd3f03961d05d25cd27617d2945be10b' su 4655 job 157 scan return status 2 su 4655 job 157 scan status 2 infection 2 virus 8187637 'W32/AI.Pallas.Suspicious' s_type 4 cate 0 fsize 4096 hr 100 checksum 1619585399 su 4655 job 157 add quarantine file 'ai_sample1' virus 'W32/AI.Pallas.Suspicious' infection_type 2 su 4655 job 157 settings are such that file won't be quarantined su 4655 job 157 not wanted for analytics: post-transfer scan submission is disabled at protocol level (m 2 r 2) su 4655 job 157 report HEURISTIC infection priority 1 su 4655 job 157 insert infection HEURISTIC SUCCEEDED loc (nil) off 0 sz 0 at index 0 total infections 1 error 0 su 4655 job 157 send result su 4655 job 157 close su 4654 open
Example 3: VO sample file
To test the AV profile with the VO sample file:
-
On the PC, go to the FortiGuard website and download the VO Sample file.
-
The download attempt is blocked by the FortiGate’s default AV profile, and a block page appears in the PC's browser.

The file is blocked due to the virus outbreak protection service and database that is enabled in the default AV profile.
-
Verify the AV log.
-
In the GUI, go to Log & Report > Security Events and select the AntiVirus card. Select the log entry and click Details.
-
In the CLI, enter the following:
# execute log filter category 2 # execute log display date=2023-08-30 time=17:50:33 eventtime=1693443033509250120 tz="-0700" logid="0204008202" type="utm" subtype="virus" eventtype="outbreak-prevention" level="warning" vd="root" policyid=1 poluuid="c65fa590-4758-51ee-4d28-f2cc75f14979" policytype="policy" msg="Blocked by Virus Outbreak Prevention service." action="blocked" service="HTTPS" sessionid=2501 srcip=192.168.1.110 dstip=209.52.38.129 srcport=63450 dstport=443 srccountry="Reserved" dstcountry="Canada" srcintf="internal1" srcintfrole="undefined" dstintf="wan1" dstintfrole="wan" srcuuid="6c43f8d6-478a-51ee-95d8-31177232e869" dstuuid="6c43f8d6-478a-51ee-95d8-31177232e869" proto=6 direction="incoming" filename="zhvo_test.com" quarskip="Quarantine-disabled" virus="503e99fe40ee120c45bc9a30835e7256fff3e46a" viruscat="File Hash" dtype="outbreak-prevention" filehash="503e99fe40ee120c45bc9a30835e7256fff3e46a" filehashsrc="fortiguard" url="https://filestore.fortinet.com/fortiguard/test-files/outbreak-prevention/zhvo_test.com" profile="default" agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/117.0" httpmethod="GET" referralurl="https://www.fortiguard.com/" analyticssubmit="false" crscore=50 craction=2 crlevel="critical"
-
Example 4: behavioral-based samples detected by a sandbox
The FortiGate can be integrated with FortiSandbox appliance (used in this example), FortiSandbox Cloud, or FortiGate Cloud Sandbox. See Configuring sandboxing for more information about configuring the different FortiSandbox sandbox solutions.
There are two types of scan strategies that can be used in an AV profile.
-
Inline: files are sent to the FortiSandbox, and the FortiGate waits for a verdict before completing the file transfer to the client (see Using FortiSandbox inline scanning with antivirus).
-
Post-transfer: files are sent to the FortiSandbox, but the FortiGate does not wait for a verdict and completes the file transfer to the client (see Using FortiSandbox post-transfer scanning with antivirus).
-
After the FortiSandbox scans and presents a verdict, it updates its malware signature database and the FortiGate retrieves the malware signature database from FortiSandbox if the FortiSandbox database is enabled.
-
If a user attempts to download the file again, the FortiGate will either block or allow the download depending on the FortiSandbox verdict.
-
This example uses the inline AV scan strategy with a Windows executable sample file, and assumes that the scan profile has already been configured in FortiSandbox. See Verify the FortiSandbox Analysis in the FortiSandbox Administration Guide for more information.

To test the AV profile with a Windows executable sample file:
-
Integrate the FortiGate with the FortiSandbox appliance using the Security Fabric (see Configuring sandboxing).
-
Update the AV profile to use inline scanning (see FortiSandbox appliance inline scanning).
-
On the PC, go to the FortiGuard website, hover over the Windows Executable link, right-click, and select the browser’s option to copy the link.
-
Open another browser tab, paste the URL, and append the URL with
&s=<string>, such ashttps://filegen.fortinet.com/v1/sandbox-file?file_name=windows.exe&s=ftnt.Every file download attempt from the FortiGuard website downloads a new file. Downloading a file with same
<string>ensures that the downloaded file is the same, and not a new file. A file named windows.exe starts to download.Since inline AV scanning is in use, the client's file is held while it is sent to FortiSandbox for inspection. During this time, the FortiGate may apply client comforting (see Protocol options) by leaking a certain amount of bytes at a certain time interval to the client.
Once a verdict is returned from FortiSandbox, the appropriate action (allow or block) is performed on the held file. If there is an error connecting to the FortiSandbox or a timeout on the FortiSandbox scanning the file within the default 50 seconds, the file can be passed, logged, or blocked based on FortiGate's configuration. In this example, the action is set to the default (
log-only), which allows the file to be downloaded if FortiSandbox takes more than 50 seconds to present a verdict.In the first attempt, the windows.exe file is downloaded on the client’s PC if FortiSandbox takes more than 50 seconds for scanning the file, after which the FortiGate encounters a scan timeout.
-
To change the FortiSandbox error and timeout settings in the AV profile, enter the following in the CLI:
config antivirus profile edit <name> set fortisandbox-error-action {ignore | log-only | block} set fortisandbox-timeout-action {ignore | log-only | block} next endfortisandbox-error-action {ignore | log-only | block}
Set the action to take if FortiSandbox inline scanning encounters an error reaching the FortiSandbox:
ignore: take no actionlog-only: log the FortiSandbox inline scan error, but allow the file (default)block: block the file upon FortiSandbox inline scan error
fortisandbox-timeout-action {ignore | log-only | block}
Set the action to take if FortiSandbox inline scanning encounters a scan timeout:
ignore: take no actionlog-only: log the FortiSandbox inline scan timeout, but allow the file (default)block: block the file upon FortiSandbox inline scan timeout
-
-
Verify the AV log:
# execute log filter category 2 # execute log display date=2023-11-01 time=11:30:45 eventtime=1698863444363194189 tz="-0700" logid="0209008225" type="utm" subtype="virus" eventtype="inline-block" level="notice" vd="root" policyid=1 poluuid="6f2b2dee-478a-51ee-e9c3-b7218be554fe" policytype="policy" msg="Inline Block scan timeout." action="monitored" service="HTTPS" sessionid=946497 srcip=192.168.1.110 dstip=149.5.234.147 srcport=57497 dstport=443 srccountry="Reserved" dstcountry="France" srcintf="internal1" srcintfrole="undefined" dstintf="wan1" dstintfrole="wan" srcuuid="a051eeb2-5284-51ee-99d0-d8b19cb7439d" dstuuid="6c43f8d6-478a-51ee-95d8-31177232e869" proto=6 direction="incoming" filename="windows.exe" quarskip="No-quarantine-for-inline-block-error" url="https://filegen.fortinet.com/v1/sandbox-file?file_name=windows.exe&s=ftnt profile="default" agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36" httpmethod="GET" analyticssubmit="false" icbaction="timeout" crscore=50 craction=2 crlevel="critical"
-
After FortiSandbox finishes scanning the file (typically between one to three minutes), attempt to re-download the file using the same URL and separator (
https://filegen.fortinet.com/v1/sandbox-file?file_name=windows.exe&s=ftnt). -
The file is now blocked by the FortiGate, and a High Security Alert block page appears in the PC's browser.
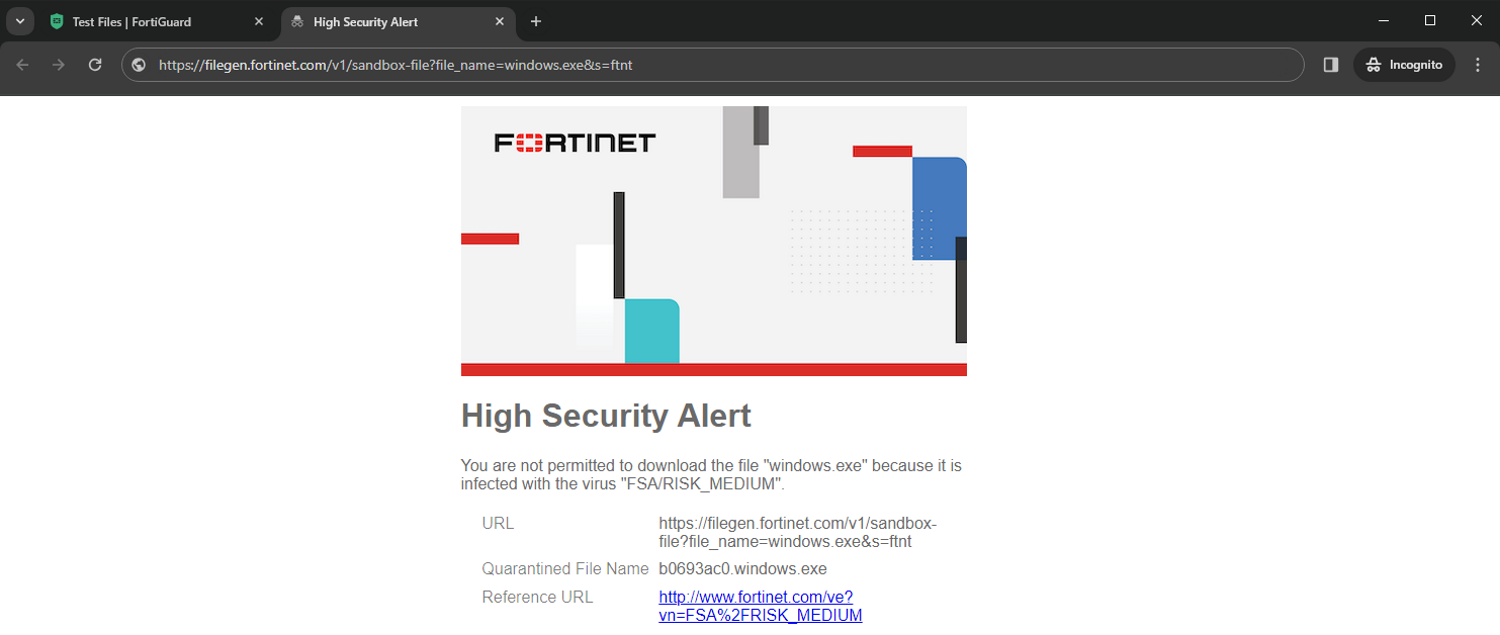
-
Verify the AV log again.
-
In the GUI, go to Log & Report > Security Events and select the AntiVirus card. Select the log entry and click Details.
-
In the CLI, enter the following:
# execute log filter category 2 # execute log display date=2023-11-01 time=11:46:34 eventtime=1698864393856143209 tz="-0700" logid="0211009234" type="utm" subtype="virus" eventtype="infected" level="warning" vd="root" policyid=1 poluuid="6f2b2dee-478a-51ee-e9c3-b7218be554fe" policytype="policy" msg="File reported infected by Sandbox." action="blocked" service="HTTPS" sessionid=946497 srcip=192.168.1.110 dstip=149.5.234.147 srcport=57497 dstport=443 srccountry="Reserved" dstcountry="France" srcintf="internal1" srcintfrole="undefined" dstintf="wan1" dstintfrole="wan" srcuuid="a051eeb2-5284-51ee-99d0-d8b19cb7439d" dstuuid="6c43f8d6-478a-51ee-95d8-31177232e869" proto=6 direction="incoming" filename="windows.exe" checksum="b0693ac0" quarskip="No-skip" virus="FSA/RISK_MEDIUM" viruscat="Virus" dtype="fortisandbox" ref="http://www.fortinet.com/ve?vn=FSA%2FRISK_MEDIUM" virusid=9 url="https://filegen.fortinet.com/v1/sandbox-file?file_name=windows.exe&s=ftnt" profile="default" agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36" httpmethod="GET" analyticscksum="44c43fc7e1af2071d035bc50871c12bf03f207427ad7094090eb038490ccaa68" analyticssubmit="false" crscore=10 craction=2 crlevel="medium"
-





