Packet distribution for aggregate dial-up IPsec tunnels
To support per-packet load balancing on aggregate dial-up IPsec tunnels between sites, each spoke must be configured with a location ID. On the hub, per-packet load balancing is performed on the tunnels in the IPsec aggregate that have the same location ID.
Multiple dial-up VPN tunnels from the same location can be aggregated on the VPN hub and load balanced based on the configured load balance algorithm.
IPsec traffic cannot be offloaded to the NPU.
Example
In this example, an IPsec aggregate tunnel is formed between two dial-up IPsec tunnels in order to support per-packet load balancing.
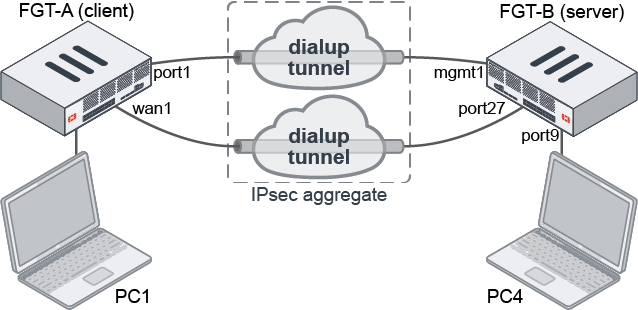
To configure the client FortiGate (FGT-A):
-
Configure the IPsec tunnels:
config vpn ipsec phase1-interface edit "client1" set interface "port1" set peertype any set net-device disable set aggregate-member enable set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1 set remote-gw 172.16.200.4 set psksecret ********** next edit "client2" set interface "wan1" set peertype any set net-device disable set aggregate-member enable set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1 set remote-gw 173.1.1.1 set psksecret ********** next end -
Configure an aggregate of the IPsec tunnels:
config system ipsec-aggregate edit "agg1" set member "client1" "client2" next end -
Configure the location ID:
config system settings set location-id 1.1.1.1 end
To configure the server FortiGate (FGT-B):
-
Configure the IPsec tunnels:
config vpn ipsec phase1-interface edit "server1" set type dynamic set interface "mgmt1" set peertype any set net-device disable set aggregate-member enable set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1 set dpd on-idle set psksecret *********** set dpd-retryinterval 60 next edit "server2" set type dynamic set interface "port27" set peertype any set net-device disable set aggregate-member enable set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1 set dpd on-idle set psksecret ********** set dpd-retryinterval 60 next end config vpn ipsec phase2-interface edit "server1" set phase1name "server1" set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256 aes128gcm aes256gcm chacha20poly1305 next edit "server2" set phase1name "server2" set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256 aes128gcm aes256gcm chacha20poly1305 next end -
Configure an aggregate of the IPsec tunnels:
config system ipsec-aggregate edit "server" set member "server1" "server2" next end -
Configure a firewall policy:
config firewall policy edit 1 set srcintf "server" set dstintf "port9" set srcaddr "all" set dstaddr "all" set action accept set schedule "always" set service "ALL" next end
To check the IPsec tunnel and aggregate state:
-
List all of the VPN tunnels:
FGDocs # diagnose vpn tunnel list list all ipsec tunnel in vd 0 ------------------------------------------------------ name=server1 ver=1 serial=1 172.16.200.4:500->0.0.0.0:500 tun_id=1.0.0.0 dst_mtu=0 dpd-link=on remote_location=0.0.0.0 weight=1 bound_if=4 lgwy=static/1 tun=tunnel/15 mode=dialup/2 encap=none/4616 options[1208]=npu frag-rfc accept_traffic=1 overlay_id=0 proxyid_num=0 child_num=2 refcnt=4 ilast=14210 olast=14210 ad=/0 stat: rxp=798921 txp=819074 rxb=121435992 txb=68802216 dpd: mode=on-idle on=0 idle=60000ms retry=3 count=0 seqno=0 natt: mode=none draft=0 interval=0 remote_port=0 run_tally=0 ------------------------------------------------------ name=server2 ver=1 serial=2 173.1.1.1:500->0.0.0.0:500 tun_id=2.0.0.0 dst_mtu=0 dpd-link=on remote_location=0.0.0.0 weight=1 bound_if=17 lgwy=static/1 tun=tunnel/15 mode=dialup/2 encap=none/4616 options[1208]=npu frag-rfc accept_traffic=1 overlay_id=0 proxyid_num=0 child_num=1 refcnt=3 ilast=14177 olast=14177 ad=/0 stat: rxp=836484 txp=819111 rxb=137429352 txb=80046050 dpd: mode=on-idle on=0 idle=60000ms retry=3 count=0 seqno=0 natt: mode=none draft=0 interval=0 remote_port=0 run_tally=0 ------------------------------------------------------ name=server1_0 ver=1 serial=8 172.16.200.4:500->172.16.200.1:500 tun_id=172.16.200.1 dst_mtu=1500 dpd-link=on remote_location=1.1.1.1 weight=1 bound_if=4 lgwy=static/1 tun=tunnel/15 mode=dial_inst/3 encap=none/4744 options[1288]=npu rgwy-chg frag-rfc run_state=0 accept_traffic=1 overlay_id=0 parent=server1 index=0 proxyid_num=1 child_num=0 refcnt=5 ilast=45 olast=45 ad=/0 stat: rxp=17176 txp=17176 rxb=2610752 txb=1442784 dpd: mode=on-idle on=1 idle=60000ms retry=3 count=0 seqno=12 natt: mode=none draft=0 interval=0 remote_port=0 proxyid=server1 proto=0 sa=1 ref=2 serial=1 add-route src: 0:0.0.0.0-255.255.255.255:0 dst: 0:10.1.100.0-10.1.100.255:0 SA: ref=3 options=2a6 type=00 soft=0 mtu=1438 expire=42342/0B replaywin=2048 seqno=4319 esn=0 replaywin_lastseq=00004319 itn=0 qat=0 hash_search_len=1 life: type=01 bytes=0/0 timeout=43186/43200 dec: spi=0aef2a07 esp=aes key=16 12738c8a1db02c23bfed73eb3615a5a1 ah=sha1 key=20 0f3edd28e3165d184292b4cd397a6edeef9d20dc enc: spi=2cb75665 esp=aes key=16 982b418e40f0bb18b89916d8c92270c0 ah=sha1 key=20 08cbf9bf78a968af5cd7647dfa2a0db066389929 dec:pkts/bytes=17176/1442784, enc:pkts/bytes=17176/2610752 npu_flag=00 npu_rgwy=172.16.200.1 npu_lgwy=172.16.200.4 npu_selid=6 dec_npuid=0 enc_npuid=0 ------------------------------------------------------ name=server1_1 ver=1 serial=a 172.16.200.4:500->172.16.200.3:500 tun_id=172.16.200.3 dst_mtu=0 dpd-link=on remote_location=2.2.2.2 weight=1 bound_if=4 lgwy=static/1 tun=tunnel/15 mode=dial_inst/3 encap=none/4744 options[1288]=npu rgwy-chg frag-rfc run_state=0 accept_traffic=1 overlay_id=0 parent=server1 index=1 proxyid_num=1 child_num=0 refcnt=5 ilast=27 olast=27 ad=/0 stat: rxp=0 txp=0 rxb=0 txb=0 dpd: mode=on-idle on=1 idle=60000ms retry=3 count=0 seqno=0 natt: mode=none draft=0 interval=0 remote_port=0 proxyid=server1 proto=0 sa=1 ref=2 serial=1 add-route src: 0:0.0.0.0-255.255.255.255:0 dst: 0:0.0.0.0-255.255.255.255:0 SA: ref=3 options=2a6 type=00 soft=0 mtu=1280 expire=43167/0B replaywin=2048 seqno=1 esn=0 replaywin_lastseq=00000000 itn=0 qat=0 hash_search_len=1 life: type=01 bytes=0/0 timeout=43187/43200 dec: spi=0aef2a0a esp=aes key=16 4b7a17ba9d239e4ae5fe95ec100fca8b ah=sha1 key=20 7d3e058088f21e0c4f1c13c297293f06c8b592e7 enc: spi=7e961809 esp=aes key=16 ecd1aa8657c5a509662aed45002d3990 ah=sha1 key=20 d159e06c1cf0ded18a4e4ac86cbe5aa0315c21c9 dec:pkts/bytes=0/0, enc:pkts/bytes=0/0 npu_flag=00 npu_rgwy=172.16.200.3 npu_lgwy=172.16.200.4 npu_selid=9 dec_npuid=0 enc_npuid=0 ------------------------------------------------------ name=server2_0 ver=1 serial=7 173.1.1.1:500->11.101.1.1:500 tun_id=11.101.1.1 dst_mtu=1500 dpd-link=on remote_location=1.1.1.1 weight=1 bound_if=17 lgwy=static/1 tun=tunnel/15 mode=dial_inst/3 encap=none/4744 options[1288]=npu rgwy-chg frag-rfc run_state=0 accept_traffic=1 overlay_id=0 parent=server2 index=0 proxyid_num=1 child_num=0 refcnt=5 ilast=45 olast=45 ad=/0 stat: rxp=16001 txp=17179 rxb=2113664 txb=1594824 dpd: mode=on-idle on=1 idle=60000ms retry=3 count=0 seqno=12 natt: mode=none draft=0 interval=0 remote_port=0 proxyid=server2 proto=0 sa=1 ref=2 serial=1 add-route src: 0:0.0.0.0-255.255.255.255:0 dst: 0:10.1.100.0-10.1.100.255:0 SA: ref=6 options=2a6 type=00 soft=0 mtu=1438 expire=42342/0B replaywin=2048 seqno=431a esn=0 replaywin_lastseq=00003e80 itn=0 qat=0 hash_search_len=1 life: type=01 bytes=0/0 timeout=43185/43200 dec: spi=0aef2a08 esp=aes key=16 394d4e444e90ccb5184e744d49aabe3c ah=sha1 key=20 faabea35c2b9b847461cbd263c4856cfb679f342 enc: spi=2cb75666 esp=aes key=16 0b3a2fbac4d5610670843fa1925d1207 ah=sha1 key=20 97e99beff3d8f61a8638f6ef887006a9c323acd4 dec:pkts/bytes=16001/2113596, enc:pkts/bytes=17179/2762792 npu_flag=03 npu_rgwy=11.101.1.1 npu_lgwy=173.1.1.1 npu_selid=7 dec_npuid=1 enc_npuid=1 -
List the IPsec aggregate members:
# diagnose sys ipsec-aggregate list server members(3): server1_1 server1_0 server2_0 -
In the GUI, go to Dashboard > Network and expand the IPsec widget to review the traffic distributed over the aggregate members:


