Basic BGP example
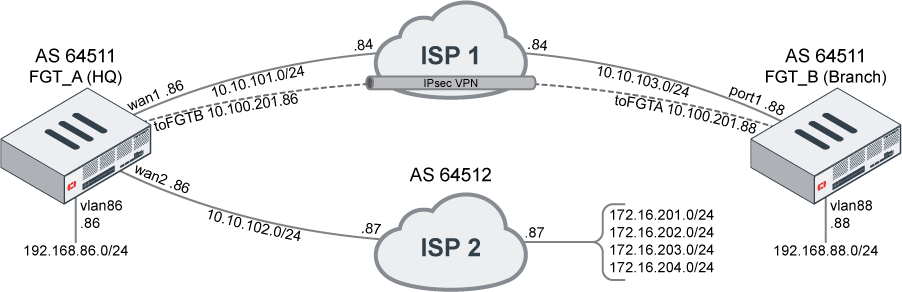
In this example, BGP is configured on two FortiGate devices. The FortiGates are geographically separated, and form iBGP peering over a VPN connection. FGT_A also forms eBGP peering with ISP2.
FGT_A learns routes from ISP2 and redistributes them to FGT_B while preventing any iBGP routes from being advertised.
The internal networks behind the FortiGates can communicate with each other, and the internal networks behind FGT_B can traverse FGT_A to reach networks that are advertised by ISP2.
-
FGT_A and FGT_B have static routes to each other through ISP1. ISP1 does not participate in BGP.
-
The IPsec VPN tunnel between FGT_A and FGT_B is configured with wildcard 0.0.0.0/0 networks for phase2 local and remote selectors. The VPN interfaces have IP addresses already configured and are used for peering between FGT_A and FGT_B.
-
FGT_A is configure to peer with ISP2 on 10.10.108.86.
-
The firewall policies between FGT_A and FGT_B are not NATed. The firewall policies egressing on wan2 are NATed.
Configuring iBGP peering
To configure FGT_A to establish iBGP peering with FGT_B in the GUI:
-
Go to Network > BGP.
-
Set Local AS to 64511
-
Set Router ID to 1.1.1.1.
-
In the Neighbors table, click Create New and set the following:
IP
10.100.201.88
Remote AS
64511
-
Click OK.
-
Under Networks, set IP/Netmask to 192.168.86.0/24.
-
Click Apply.
-
In the CLI, set the interface used as the source IP address of the TCP connection (where the BGP session, TCP/179, is connecting from) for the neighbor (
update-source) totoFGTB.
To configure FGT_A to establish iBGP peering with FGT_B in the CLI:
config router bgp
set as 64511
set router-id 1.1.1.1
config neighbor
edit "10.100.201.88"
set remote-as 64511
set update-source "toFGTB"
next
end
config network
edit 1
set prefix 192.168.86.0 255.255.255.0
next
end
end
To configure FGT_B to establish iBGP peering with FGT_A in the GUI:
-
Go to Network > BGP.
-
Set Local AS to 64511
-
Set Router ID to 2.2.2.2.
-
In the Neighbors table, click Create New and set the following:
IP
10.100.201.86
Remote AS
64511
-
Click OK.
-
Under Networks, set IP/Netmask to 192.168.88.0/24.
-
Click Apply.
-
In the CLI, set the interface used as the source IP address of the TCP connection (where the BGP session, TCP/179, is connecting from) for the neighbor (
update-source) totoFGTA.
To configure FGT_B to establish iBGP peering with FGT_A in the CLI:
config router bgp
set as 64511
set router-id 2.2.2.2
config neighbor
edit "10.100.201.86"
set remote-as 64511
set update-source "toFGTA"
next
end
config network
edit 1
set prefix 192.168.88.0 255.255.255.0
next
end
end
To check the FGT_A and FGT_B peering:
-
Check the BGP neighbors:
# get router info bgp neighbors
-
Check the networks learned from neighbors:
# get router info bgp network
-
Check that the routes are added to the routing table:
# get router info routing-table all
To see the neighborship status, network, and routing table command outputs for the completed example, see Troubleshooting and debugging.
Configuring eBGP peering
By establishing eBGP peering with ISP2, learned routes will have a distance of 20 and will automatically be propagated to iBGP peers.
iBGP peers do not change the next hop when they advertise a route. To make FGT_B receive a route with FGT_A as the next hop, and not ISP 2's network, Next hop self (next-hop-self) is enabled for routes advertised to FGT_B.
Additionally, to peer with another router that is multiple hops away, enable ebg-enforce-multihop in the neighbor configuration.
In this example, the iBGP routes are automatically advertised to the eBGP neighbor, so a route map is created to deny iBGP routes from being advertised to ISP 2. Prefixes from ISP 2 are advertised to FGT_A and FGT_B, but no prefixes are advertised from FGT_A to ISP 2.
To configure FGT_A to establish eBGP peering with ISP 2 in the GUI:
-
Configure a route map to prevent advertisement of iBGP routes to ISP 2:
-
Go to Network > Routing Objects and click Create New > Route Map.
-
Set Name to exclude1.
-
In the Rules table, click Create New.
-
Set Action to Deny.
-
Under Other Rule Variables, enable Match origin and set it to IGP.
-
Click OK.
-
Click OK.
-
-
Update the BGP configuration:
-
Go to Network > BGP.
-
In the Neighbors table, click Create New and set the following:
IP
10.10.102.87
Remote AS
64512
Route map out
exclude1
-
Click OK.
-
In the Neighbors table, edit the previously created entry, 10.100.201.88.
-
Under IPv4 Filtering, select Next hop self.
-
Click OK.
-
Click Apply.
-
To configure FGT_A to establish eBGP peering with ISP 2 in the CLI:
-
Configure a route map to prevent advertisement of iBGP routes to ISP 2:
config router route-map edit "exclude1" config rule edit 1 set action deny set match-origin igp next end next end -
Update the BGP configuration:
config router bgp config neighbor edit "10.10.102.87" set remote-as 64512 set route-map-out "exclude1" next edit "10.100.201.88" set next-hop-self enable next end end
To see the neighborship status, network, and routing table command outputs for the completed example, see Troubleshooting and debugging.
Firewall policies
On FGT_A configure the following policies:
-
Allow the internal subnet to the VPN interface. Do not enable NAT. Enable security profiles as required.
-
Allow the VPN interface to the internal subnet. Do not enable NAT. Enable security profiles as required.
-
Allow the internal subnet to wan2. Enable NAT and security profiles as required.
-
Allow VPN traffic from toFGTA to wan2. Enable NAT and security profiles as required.
On FGT_B configure the following policies:
-
Allow the internal subnet to the VPN interface. Do not enable NAT. Enable security profiles as required.
-
Allow the VPN interface to the internal subnet. Do not enable NAT. Enable security profiles as required.
To verify that pinging from FGT_B to FGT_A is successful:
FGT_B # execute ping-options source 192.168.88.88 FGT_B # execute ping 192.168.86.86 PING 192.168.86.86 (192.168.86.86): 56 data bytes 64 bytes from 192.168.86.86: icmp_seq=0 ttl=255 time=0.5 ms ... --- 192.168.86.86 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max = 0.3/0.3/0.5 ms
To verify that pinging from FGT_B to a subnet in ISP 2 is successful:
FGT_B # execute ping-options source 192.168.88.88 FGT_B # execute ping 172.16.201.87 PING 172.16.201.87 (172.16.201.87): 56 data bytes 64 bytes from 172.16.201.87: icmp_seq=0 ttl=254 time=0.6 ms ... --- 172.16.201.87 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max = 0.4/0.4/0.6 ms FGT_B # execute traceroute-options source 192.168.88.88 FGT_B # execute traceroute 172.16.201.87 traceroute to 172.16.201.87 (172.16.201.87), 32 hops max, 3 probe packets per hop, 84 byte packets 1 10.100.201.86 0.315 ms 0.143 ms 0.110 ms 2 172.16.201.87 0.258 ms 0.144 ms 0.222 ms
Troubleshooting and debugging
When troubleshooting issues, logically step through the debugs. For example, if peering cannot be established between FGT_A and FGT_B:
-
Verify the basic connectivity between the FGT_A wan1 interface and the FGT_B port1 interface.
-
Verify that the VPN between FGT_A and FGT_B is established.
-
Verify the connectivity between the VPN interfaces.
-
Check the neighborship status on each peer. Use the BGP state to help determine the possible issue, for example:
Idle state
The local FortiGate has not started the BGP process with the neighbor. This could be because the eBGP peer is multiple hops away, but multihop is not enabled.
Connect
The local FortiGate has started the BGP process, but has not initiated a TCP connection, possibly due to improper routing.
Active
The local FortiGate has initiated a TCP connection, but there is no response. This might indicate issues with the delivery or the response from the remote peer.
-
If there are issues establishing the TCP connection, use the command
diagnose sniffer packet any 'tcp and port 179'to identify the problem at the packet level.
The following outputs show instances where all of the configurations are completed, peering has formed, and routes have been exchanged. The debug output during each configuration step might differ from these outputs. These debug outputs can be used to help identify what might be missing or misconfigured on your device.
To verify the status of the neighbors:
FGT_A # get router info bgp neighbors
VRF 0 neighbor table:
BGP neighbor is 10.10.102.87, remote AS 64512, local AS 64511, external link
BGP version 4, remote router ID 192.168.2.87
BGP state = Established, up for 01:54:37
Last read 00:00:29, hold time is 180, keepalive interval is 60 seconds
Configured hold time is 180, keepalive interval is 60 seconds
Neighbor capabilities:
Route refresh: advertised and received (old and new)
Address family IPv4 Unicast: advertised and received
Address family IPv6 Unicast: advertised and received
Received 513 messages, 1 notifications, 0 in queue
Sent 517 messages, 2 notifications, 0 in queue
Route refresh request: received 0, sent 0
Minimum time between advertisement runs is 30 seconds
For address family: IPv4 Unicast
BGP table version 5, neighbor version 0
Index 3, Offset 0, Mask 0x8
Community attribute sent to this neighbor (both)
Outbound path policy configured
Route map for outgoing advertisements is *exclude1root
4 accepted prefixes, 4 prefixes in rib
0 announced prefixes
For address family: IPv6 Unicast
BGP table version 1, neighbor version 0
Index 3, Offset 0, Mask 0x8
Community attribute sent to this neighbor (both)
0 accepted prefixes, 0 prefixes in rib
0 announced prefixes
Connections established 4; dropped 3
Local host: 10.10.102.86, Local port: 20364
Foreign host: 10.10.102.87, Foreign port: 179
Nexthop: 10.10.102.86
Nexthop interface: wan2
Nexthop global: ::
Nexthop local: ::
BGP connection: non shared network
Last Reset: 01:54:42, due to BGP Notification sent
Notification Error Message: (CeaseUnspecified Error Subcode)
BGP neighbor is 10.100.201.88, remote AS 64511, local AS 64511, internal link
BGP version 4, remote router ID 2.2.2.2
BGP state = Established, up for 01:54:07
Last read 00:00:11, hold time is 180, keepalive interval is 60 seconds
Configured hold time is 180, keepalive interval is 60 seconds
Neighbor capabilities:
Route refresh: advertised and received (old and new)
Address family IPv4 Unicast: advertised and received
Address family IPv6 Unicast: advertised and received
Received 527 messages, 3 notifications, 0 in queue
Sent 543 messages, 8 notifications, 0 in queue
Route refresh request: received 0, sent 0
Minimum time between advertisement runs is 30 seconds
Update source is toFGTB
For address family: IPv4 Unicast
BGP table version 5, neighbor version 4
Index 1, Offset 0, Mask 0x2
NEXT_HOP is always this router
Community attribute sent to this neighbor (both)
1 accepted prefixes, 1 prefixes in rib
5 announced prefixes
For address family: IPv6 Unicast
BGP table version 1, neighbor version 1
Index 1, Offset 0, Mask 0x2
Community attribute sent to this neighbor (both)
0 accepted prefixes, 0 prefixes in rib
0 announced prefixes
Connections established 7; dropped 6
Local host: 10.100.201.86, Local port: 179
Foreign host: 10.100.201.88, Foreign port: 6245
Nexthop: 10.100.201.86
Nexthop interface: toFGTB
Nexthop global: ::
Nexthop local: ::
BGP connection: non shared network
Last Reset: 01:54:12, due to BGP Notification received
Notification Error Message: (CeaseUnspecified Error Subcode)
FGT_B # get router info bgp neighbors
VRF 0 neighbor table:
BGP neighbor is 10.100.201.86, remote AS 64511, local AS 64511, internal link
BGP version 4, remote router ID 1.1.1.1
BGP state = Established, up for 01:56:04
Last read 00:00:48, hold time is 180, keepalive interval is 60 seconds
Configured hold time is 180, keepalive interval is 60 seconds
Neighbor capabilities:
Route refresh: advertised and received (old and new)
Address family IPv4 Unicast: advertised and received
Address family IPv6 Unicast: advertised and received
Received 532 messages, 3 notifications, 0 in queue
Sent 526 messages, 3 notifications, 0 in queue
Route refresh request: received 0, sent 0
Minimum time between advertisement runs is 30 seconds
Update source is toFGTA
For address family: IPv4 Unicast
BGP table version 4, neighbor version 3
Index 1, Offset 0, Mask 0x2
Community attribute sent to this neighbor (both)
5 accepted prefixes, 5 prefixes in rib
1 announced prefixes
For address family: IPv6 Unicast
BGP table version 1, neighbor version 1
Index 1, Offset 0, Mask 0x2
Community attribute sent to this neighbor (both)
0 accepted prefixes, 0 prefixes in rib
0 announced prefixes
Connections established 7; dropped 6
Local host: 10.100.201.88, Local port: 6245
Foreign host: 10.100.201.86, Foreign port: 179
Nexthop: 10.100.201.88
Nexthop interface: toFGTA
Nexthop global: ::
Nexthop local: ::
BGP connection: non shared network
Last Reset: 01:56:09, due to BGP Notification sent
Notification Error Message: (CeaseUnspecified Error Subcode)
# get router info bgp neighbors <neighbor's IP> can also be used to verify the status of a specific neighbor.
To verify the networks learned from neighbors or a specific network:
FGT_A # get router info bgp network
VRF 0 BGP table version is 5, local router ID is 1.1.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight RouteTag Path
*> 172.16.201.0/24 10.10.102.87 0 0 0 64512 i <-/1>
*> 172.16.202.0/24 10.10.102.87 0 0 0 64512 i <-/1>
*> 172.16.203.0/24 10.10.102.87 0 0 0 64512 i <-/1>
*> 172.16.204.0/24 10.10.102.87 0 0 0 64512 i <-/1>
*> 192.168.86.0 0.0.0.0 100 32768 0 i <-/1>
*>i192.168.88.0 10.100.201.88 0 100 0 0 i <-/1>
Total number of prefixes 6
FGT_A # get router info bgp network 172.16.201.0
VRF 0 BGP routing table entry for 172.16.201.0/24
Paths: (1 available, best #1, table Default-IP-Routing-Table)
Advertised to non peer-group peers:
10.100.201.88
Original VRF 0
64512
10.10.102.87 from 10.10.102.87 (192.168.2.87)
Origin IGP metric 0, localpref 100, valid, external, best
Last update: Tue Dec 15 22:52:08 2020
FGT_A # get router info bgp network 192.168.88.0
VRF 0 BGP routing table entry for 192.168.88.0/24
Paths: (1 available, best #1, table Default-IP-Routing-Table)
Not advertised to any peer
Original VRF 0
Local
10.100.201.88 from 10.100.201.88 (2.2.2.2)
Origin IGP metric 0, localpref 100, valid, internal, best
Last update: Tue Dec 15 22:52:39 2020
FGT_B # get router info bgp network
VRF 0 BGP table version is 4, local router ID is 2.2.2.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight RouteTag Path
*>i172.16.201.0/24 10.100.201.86 0 100 0 0 64512 i <-/1>
*>i172.16.202.0/24 10.100.201.86 0 100 0 0 64512 i <-/1>
*>i172.16.203.0/24 10.100.201.86 0 100 0 0 64512 i <-/1>
*>i172.16.204.0/24 10.100.201.86 0 100 0 0 64512 i <-/1>
*>i192.168.86.0 10.100.201.86 0 100 0 0 i <-/1>
*> 192.168.88.0 0.0.0.0 100 32768 0 i <-/1>
Total number of prefixes 6
To verify the routing tables on FGT_A and FGT_B:
FGT_A # get router info routing-table all
Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
Routing table for VRF=0
S* 0.0.0.0/0 [10/0] via 172.16.151.1, port1, [5/0]
[10/0] via 192.168.2.1, port2, [10/0]
C 10.10.101.0/24 is directly connected, wan1
C 10.10.102.0/24 is directly connected, wan2
S 10.10.103.0/24 [10/0] via 10.10.101.84, wan1
C 10.100.201.0/24 is directly connected, toFGTB
C 10.100.201.86/32 is directly connected, toFGTB
C 172.16.151.0/24 is directly connected, port1
B 172.16.201.0/24 [20/0] via 10.10.102.87, wan2, 02:09:50
B 172.16.202.0/24 [20/0] via 10.10.102.87, wan2, 02:09:50
B 172.16.203.0/24 [20/0] via 10.10.102.87, wan2, 02:09:50
B 172.16.204.0/24 [20/0] via 10.10.102.87, wan2, 02:09:50
C 192.168.2.0/24 is directly connected, port2
C 192.168.86.0/24 is directly connected, vlan86
B 192.168.88.0/24 [200/0] via 10.100.201.88, toFGTB, 02:09:19
FGT_B # get router info routing-table all
Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
Routing table for VRF=0
S* 0.0.0.0/0 [10/0] via 10.10.103.84, port1
C 10.10.103.0/24 is directly connected, port1
C 10.100.201.0/24 is directly connected, toFGTA
C 10.100.201.88/32 is directly connected, toFGTA
B 172.16.201.0/24 [200/0] via 10.100.201.86, toFGTA, 02:11:36
B 172.16.202.0/24 [200/0] via 10.100.201.86, toFGTA, 02:11:36
B 172.16.203.0/24 [200/0] via 10.100.201.86, toFGTA, 02:11:36
B 172.16.204.0/24 [200/0] via 10.100.201.86, toFGTA, 02:11:36
B 192.168.86.0/24 [200/0] via 10.100.201.86, toFGTA, 02:11:36
C 192.168.88.0/24 is directly connected, vlan88

