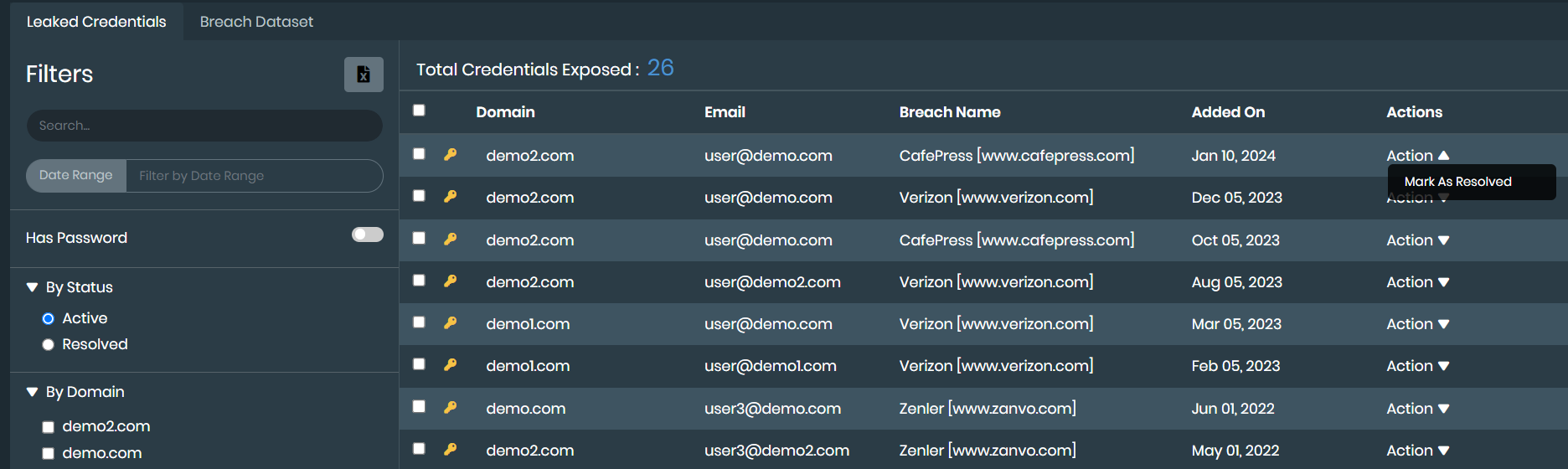
Viewing leaked credential details
On the EASM > Leaked Credentials page, click the Leaked Credentials tab to view the results.
You can filter the list of leaked credentials by date and domain, and you can search for keywords.
To view leaked credential details:
- Go to EASM > Leaked Credentials, and click Leaked Credentials.
- Apply the filters that you want.
- Click a domain name to display more details.
- Change the status of a report by selecting Mark as Resolved or Mark as Active in the Actions dropdown.
To filter leaked credentials details:
- Go to EASM > Leaked Credentials.
- On Leaked Credentials tab, filter reports by a date range:
- Click Filter Report by Date Range. Two calendars are displayed.
- In the left calendar, select a month, year, and day to specify the start date of the range.
- In the right calendar, select a month, year, and day to specify the end date of the range.
Only reports from the date range are displayed.
- Click the Filter Report by Date Range box, and click X to remove the date range filter.
-
Search for keywords:
-
In the Type and hit Enter to Search box, type a keyword, and press Enter.
-
The threats are filtered to display only threats with the keyword.
-
Click the X beside the keyword to remove the filter.
-
- Toggle Has Password option to filter reports that contain passwords.
- Filter by status in the By Status section:
- Select Active or Resolved to filter threats by their assigned status.
- Filter by domain in the By Domains section.