Configuring sandboxing
The Security Fabric supports the following types of FortiSandbox deployments:
|
Type |
Description |
Requirements |
Next steps |
|---|---|---|---|
|
FortiGate Cloud Sandbox (FortiSandbox SaaS) |
Files are sent to Fortinet’s Cloud Sandbox cluster for post‑processing. |
|
|
|
FortiGuard Inline Malware Prevention System |
Files are sent to Fortinet’s Cloud Sandbox cluster for real-time processing. |
|
|
|
FortiSandbox Cloud (FortiSandbox PaaS) |
Files are sent to a dedicated FortiCloud hosted instance of FortiSandbox for processing. |
|
|
|
FortiSandbox Appliance |
Files are sent to a physical or VM appliance, typically residing on premise, for processing. |
|
|
To apply sandboxing in a Security Fabric, connect one of the FortiSandbox deployments, then configure an antivirus profile to submit files for dynamic analysis. The submission results supplement the AV signatures on the FortiGate. FortiSandbox inspection can also be used in web filter profiles.
In a Security Fabric environment, sandbox settings are configured on the root FortiGate. Once configured, the root FortiGate pushes the settings to other FortiGates in the Security Fabric.
FortiGate Cloud Sandbox (FortiSandbox SaaS)
FortiGate Cloud Sandbox allows users to take advantage of FortiSandbox features without having to purchase, operate, and maintain a physical appliance. It also allows you to control the region where your traffic is sent to for analysis. This allows you to meet your country's compliance needs regarding data storage locations.
Users are not required to have a FortiCloud account to use FortiGate Sandbox Cloud.
The submission to the cloud with a valid FortiGuard Antivirus (AVDB) license is rate limited per FortiGate model. Refer to the Service Description for details. For those without any AVDB license, the submission is limited to only 100 per day.
To configure FortiGate Cloud Sandbox, you must first activate the connection from the CLI. Note that FortiGate Cloud Sandbox is decoupled from FortiGate Cloud logging, so you do not need to have a FortiCloud account or have cloud logging enabled.
To activate the FortiGate Cloud Sandbox connection:
|
|
To ensure proper connectivity to FortiGate Cloud Sandbox, on the FortiGate in Security Profiles > AntiVirus, create a profile with Send files to FortiSandbox Cloud for inspection configured, and create a firewall policy with logging enabled that uses the Sandbox-enabled AV profile. |
# execute forticloud-sandbox region 0 Europe 1 Global 2 Japan 3 US Please select cloud sandbox region[0-3]:3
After a region is selected, the following configuration is added:
config system fortiguard
set sandbox-region {0 | 1 | 2 | 3}
end
|
|
Alternatively, using the |
To obtain or renew a FortiGuard antivirus license:
-
See the How to Purchase or Renew FortiGuard Services video for FortiGuard antivirus license purchase instructions.
-
Once a FortiGuard license is purchased and activated, users are provided with a paid FortiSandbox Cloud license.
-
Go to Dashboard > Status to view the FortiSandbox Cloud license indicator.

-
Alternatively, go to System > FortiGuard to view the FortiSandbox Cloud license indicator.
-
To enable FortiGate Cloud Sandbox in the GUI:
-
Go to Security Fabric > Fabric Connectors and double-click the Sandbox card.
-
Set the Status to Enabled.
-
Set the Type to FortiGate Cloud.
-
Select a Region from the dropdown.

-
Click OK.
FortiSandbox Cloud (FortiSandbox PaaS)
FortiSandbox Cloud offers more features and better detection capability. Connecting to FortiSandbox Cloud will automatically use the cloud user ID of the FortiGate to connect to the dedicated FortiSandbox Cloud instance. The FortiGate automatically detects if there is a valid entitlement.
The following items are required to initialize FortiSandbox Cloud:
- A FortiCloud premium account.
- A valid FortiSandbox Cloud contract on the FortiGate. To view contract information in the CLI, enter
diagnose test update info. TheUser IDat the end of the output shows FortiCloud which FortiSandbox Cloud account the FortiGate is connected to. - A provisioned FortiSandbox Cloud. See Deploying FortiSandbox Cloud for information.
To configure FortiSandbox Cloud in the GUI:
-
Go to Security Fabric > Fabric Connectors and double-click the Sandbox card.
-
Set the Status to Enabled.
-
Set the Type to FortiSandbox Cloud.

If the FortiSandbox Cloud option is grayed out or not visible, enter the following in the CLI:
config system global set gui-fortigate-cloud-sandbox enable end -
Click OK.
To configure FortiSandbox Cloud in the CLI:
config system fortisandbox
set status enable
set forticloud enable
set server fortisandboxcloud.com
end
If the FortiGate does not detect the proper entitlement, a warning is displayed and the CLI configuration will not save.
If the FortiSandbox Cloud is running version 4.0.0 and later, the FortiGate will automatically connect to fortisandboxcloud.com, and then discover the specific region and server to connect to based on which region the customer selected to deploy their FortiSandbox Cloud instance. The FortiGate must have a FortiCloud premium account license and a FortiSandbox Cloud VM license for this functionality.
FortiSandbox appliance
FortiSandbox appliance is the on-premise option for a full featured FortiSandbox. Connecting to a FortiSandbox appliance requires that Cloud Sandbox is disabled.
To enable FortiSandbox appliance in the GUI:
-
Go to Security Fabric > Fabric Connectors and double-click the Sandbox card.
-
Set the Status to Enabled.
-
In the Server field, enter the FortiSandbox device's IP address.

-
Optionally, enter a Notifier email.
-
Click OK.
To enable FortiSandbox appliance in the CLI:
config system fortisandbox
set status enable
set forticloud disable
set server <address>
end
Authorizing the FortiGate from FortiSandbox Cloud and a FortiSandbox appliance
Once the FortiGate makes a connection to the FortiSandbox Cloud or appliance, the FortiGate must be authorized. See FortiGate devices in the FortiSandbox Administration guide for information.
Antivirus profiles
An antivirus profile must be configured to send files to the sandbox. Once submitted, sandbox inspection is performed on the file to detect malicious activities. The FortiGate can use the dynamic malware detection database from the sandbox to supplement the AV signature database. See Using FortiSandbox post-transfer scanning with antivirus for more information.
FortiSandbox inline scanning is supported on FortiSandbox appliances in proxy inspection mode. When inline scanning is enabled, the client's file is held while it is sent to FortiSandbox for inspection. Once a verdict is returned, the appropriate action is performed on the held file. If there is an error or timeout on the FortiSandbox, the FortiGate's configuration determines what to do with the held file. See Using FortiSandbox inline scanning with antivirus for more information.
|
|
Inline scanning requires FortiSandbox version 4.2 or later. |
Web filter profiles
Sandbox inspection can be used in web filter profiles. The FortiGate uses URL threat detection database from the sandbox to block malicious URLs. See Block malicious URLs discovered by FortiSandbox for more information.
FortiSandbox Files FortiView monitor
In the FortiSandbox Files FortiView monitor, users can select a submitted file and drill down to view its static and dynamic file analysis. The full FortiSandbox report can be downloaded in PDF format. This feature works with FortiGate Cloud Sandbox, FortiSandbox Cloud, and FortiSandbox appliance. FortiSandbox must be running version 3.2.1 and later.
PDF reports are downloaded on-demand. By default, only 10 are kept in memory. PDFs are deleted from memory after 24 hours.
Prerequisites:
-
Add FortiSandbox to the Security Fabric.
-
Configure an AV profile with Send files to FortiSandbox for inspection enabled (see Using FortiSandbox post-transfer scanning with antivirus).
-
Configure a firewall policy with the AV profile that allows traffic to the internet.
-
Add the Top FortiSandbox Files FortiView monitor (see Adding FortiView monitors).
-
On a client PC, attempt to download a suspicious file.
To view the FortiSandbox analysis and download the PDF:
-
Go to Dashboard > FortiSandbox Files. The entry appears in the table, but the analysis is not available yet because the Status is Pending. The default view is Files.

-
After about five to ten minutes, refresh the table. The analysis is now available.
-
Select the entry, then right-click and select Drill Down to Details.

The Sandbox File Analysis Drill Down pane opens.
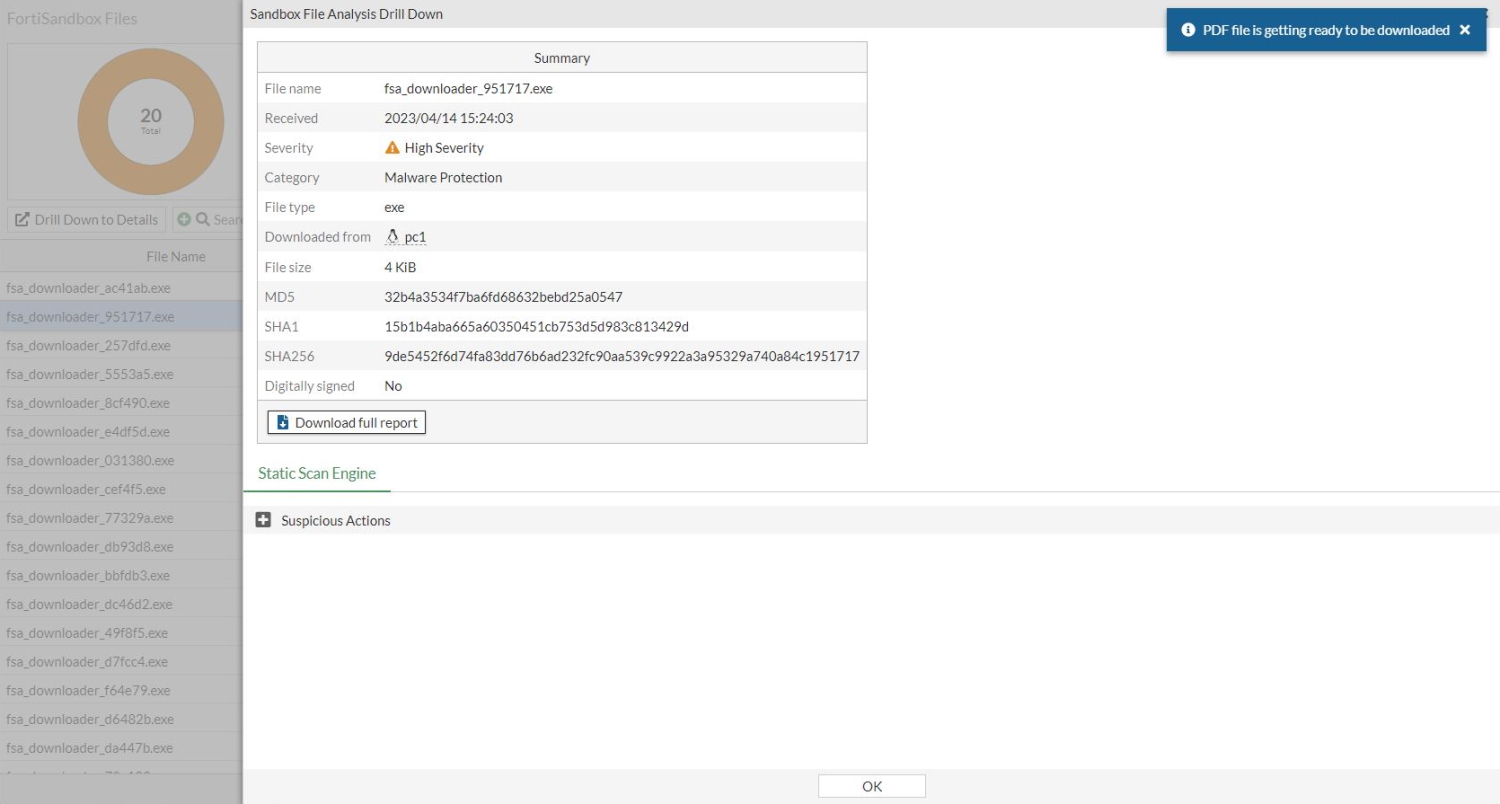
-
Click Download full report to download the detailed PDF report.
-
Change the view to Reports to verify that the file was downloaded successfully. The reports contains FortiSandbox job information and detailed file information.

When the file type is not supported, a warning message appears that the file was not scanned when the Sandbox File Analysis Drill Down pane opens.

To change the maximum number of PDFs kept in memory:
# diagnose test analytics-pdf-report max <integer>
The range is 1 - 10, and the default is 10. After the FortiGate is restarted, this value will revert to the default.

