Configuring a profile to allow or block endpoint from VPN tunnel connection based on the applied security posture tag
You can configure a profile to allow or block an endpoint from connecting to a VPN tunnel based on its applied security posture tag. This feature is only available for Windows endpoints. This example describes configuring an endpoint profile to prohibit Windows endpoints with critical vulnerabilities from connecting to VPN.
To configure an endpoint profile to prohibit endpoints with critical vulnerabilities from connecting to VPN:
- Create a security posture tagging rule set that tags endpoints with critical vulnerabilities with the "Vulnerable Devices" tag:
- Go to Security Posture Tags > Security Posture Tagging Rules.
- Click Add.
- In the Tag Endpoint As field, create a new "Vulnerable Devices" tag.
- Toggle Enabled to on.
- Click Add Rule.
- For Windows devices, from the Rule Type dropdown list, select Vulnerable Devices.
- From the Severity Level dropdown list, select Critical.
- Click Save.
- Click Save again.

- Configure the options on the endpoint profile:
- Go to Endpoint Profiles > Remote Access.
- Edit the desired profile, or create a new one.
- Under General, enable Enable Secure Remote Access.
- Select an existing VPN tunnel, or create a new one by clicking Add Tunnel, then Manual.
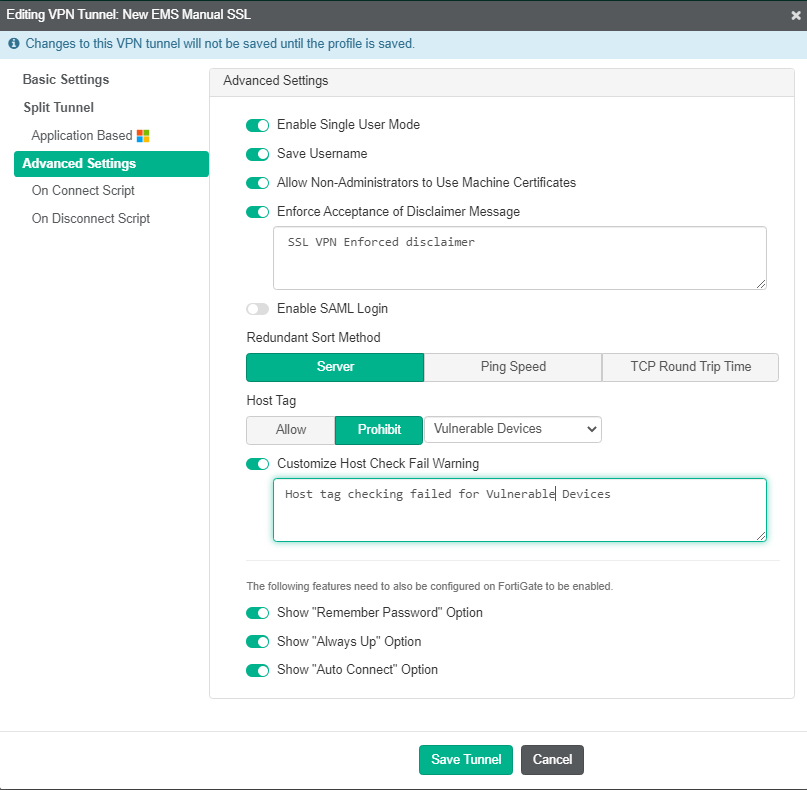
- In Advanced Settings, for Tags, select Prohibit.
- From the Select a Tag dropdown list, select Vulnerable Devices.
- Enable Customize Host Check Fail Warning.
- Enter a message to display to users when their connection to the VPN tunnel is prohibited due to critical vulnerabilities on their device.
- Configure other fields as desired.
- Save the configuration.
After the next communication between EMS and FortiClient, endpoints with this profile applied are unable to connect to this VPN tunnel if they have critical vulnerabilities. The following shows the notification that the end user sees when their connection to the VPN tunnel is prohibited due to critical vulnerabilities on their device. After the end user fixes the vulnerabilities, FortiClient allows them to establish the VPN connection.