Blocking ChatGPT using keywords and FQDN example
Large language models (LLMs), such as GPT, which are a type of Generative AI (GenAI), are widely used in applications like chatbots.
This configuration blocks HTTPS upload traffic to the OpenAI ChatGPT application that includes a sensitive keyword. The predefined data type, keyword, is used in the DLP dictionary.
|
|
This example enables Application Control With Inline-CASB and configures it to block QUIC so that the OpenAI server uses TLS 1.3 instead of QUIC. FortiSASE can inspect TLS 1.3 traffic using SSL deep inspection. |
|
|
You must enable Intrusion Prevention for internet access traffic because Application Control With Inline-CASB features require it to be enabled. |
To configure blocking HTTPS upload traffic that includes sensitive keywords:
- Go to Configuration > Security.
- For Profile Group, create a new profile group using + in the Profile Group dropdown list.
- In the Create Profile Group slide-in configure these settings:
- In the Name field, enter ChatGPT.
- For Initial Configuration, select Basic.
- Click OK.
- When prompted to select the new entry, click OK.
- In the Create Profile Group slide-in configure these settings:
- Disable AntiVirus, Web Filter with Inline-CASB, and DNS Filter using these steps for each security feature:
- Click the toggle button next to the security feature widget to disable the feature.
- Click OK to confirm disabling the security feature.
- In the SSL Inspection widget, ensure deep inspection is enabled:
- For SSL inspection, click Customize:
- Select Deep Inspection.
- Click OK.
- Configure Intrusion Prevention:
- Enable Intrusion Prevention.
- In the Intrusion Prevention widget, click Customize.
- Select an IPS profile to apply to traffic. See Intrusion prevention.
- Configure Application Control With Inline-CASB:
- Enable Application Control With Inline-CASB.
- In the Application Control With Inline-CASB widget, click Customize. Do the following:
- In the Application Control With Inline-CASB slide-in, in the Application Overrides section, click +Create.
- In the Application Overrides slide-in, in the search box, enter QUIC and press
Enter. - Select the QUIC entry and click +Add Selected. You should see a green checkmark next to the QUIC entry.
- Click OK.
- Click OK to save the Application Control settings.
- Enable Data Loss Prevention (DLP).
- Create a DLP rule:
- In the Data Loss Prevention (DLP) widget, click Customize.
- In the DLP slide-in, click Create to create a new DLP rule.
- In the New Rule slide-in, configure these settings:
Field
Value
Name
chatgpt Sensors
Select DLP sensors. You must create a new DLP sensor and then select it. Severity
Critical Action
Block Type
Message Protocol
HTTP-POST - Create a new sensor:
- Create a new sensor by clicking + next to Sensor.
- In the Select Entries slide-in, click + Create to the right to create a new sensor.
- In the New Sensor slide-in, configure these settings:
Field
Value
Name
chatgpt
Entry matches needed to trigger sensor
Any
Table of entries
Create a new entry.
- Create a sensor entry:
- Create a new sensor entry by clicking +Create.
- In the New Entry slide-in, configure these settings:
Field
Value
ID
1
Dictionary
Select the dictionary for this sensor entry. You must create a new dictionary and then select it.
Dictionary matches needed to consider traffic DLP risk
1
Status
Enabled
- Create a dictionary:
- Click the Dictionary field and click +Create to create a new DLP dictionary.
- In the New DLP Dictionary slide-in, configure these settings:
Field
Value
Name
chatgpt
Entry matches needed to trigger sensor
All
Table of Dictionary Entries
Create two dictionary entries as follows.
- Create a dictionary entry with the fortinet keyword by doing the following:
- Create a new dictionary entry by clicking +Create.
- In the New Entry slide-in, configure these settings:
Field
Value
Type
keyword
Pattern
fortinet
Case sensitive
Enable
Repeat
Disable
Status
Enabled
The configuration enables Case sensitive to enable ignoring letter case when pattern matching.
- Create a dictionary entry with the source code keyword by doing the following:
- Create a new dictionary entry by clicking +Create.
- In the New Entry slide-in, configure these settings:
Field
Value
Type
keyword
Pattern
source code
Case sensitive
Enable
Repeat
Disable
Status
Enabled
The configuration enables Case sensitive to enable ignoring letter case when pattern matching.
- Click OK several times to complete the customization:
- Click OK to create the new dictionary entry.
- Click OK to create the DLP dictionary. Click OK when prompted to select the newly created dictionary.
- Click OK to create the new sensor entry.
- Click OK to create the new sensor. Click OK when prompted to select the newly created sensor. Click Close.
- Click OK to create the new DLP rule.
- Click OK to complete DLP configuration customization.
- Configure the updated profile group in a policy:
- Go to Configuration > Policies.
- Configure a new policy with these settings:
Field
Value
Name
ChatGPT
Source Scope
All
Destination
Specify:
- Click +.
- In the Select Entries slide-in, click + and create new + IPv4 Host.
- In the New Host slide-in, configure these settings:
- Location: Unspecified
- Name: OpenAI
- Type: FQDN
- FQDN: chat.openai.com
- Click OK to create the new host.
- Click OK when prompted to select the newly created host.
- Click Close.
Service
ALL
Action
Accept
Profile Group
Specify
Select ChatGPT
Status
Enable
Log Allowed Traffic
Enable
Select All Sessions
- Click OK.
-
Drag the ChatGPT policy to the top of the policy list. Ensure it is placed above Allow-All.
To verify blocking HTTPS upload traffic that includes sensitive keywords is working:
- Ensure that your endpoint with FortiClient installed is registered with FortiSASE Endpoint Management Service and that you have established a secure connection to FortiSASE.
- On the connected endpoint, open the Chrome web browser in incognito mode.
- In the web browser, go to https://chat.openai.com.
- Search for any phrase that includes the keywords set up in the DLP dictionary. Since the phrase in HTTP POST traffic includes both sensitive keywords, FortiSASE blocks this traffic to OpenAI and generates a DLP log. Verify the request fails in ChatGPT and an error is generated.

- In FortiSASE, go to Analytics > Security > Data Loss Prevention (DLP) and confirm that FortiSASE generated a DLP block log entry that corresponds to your VPN user and visiting https://chat.openai.com.
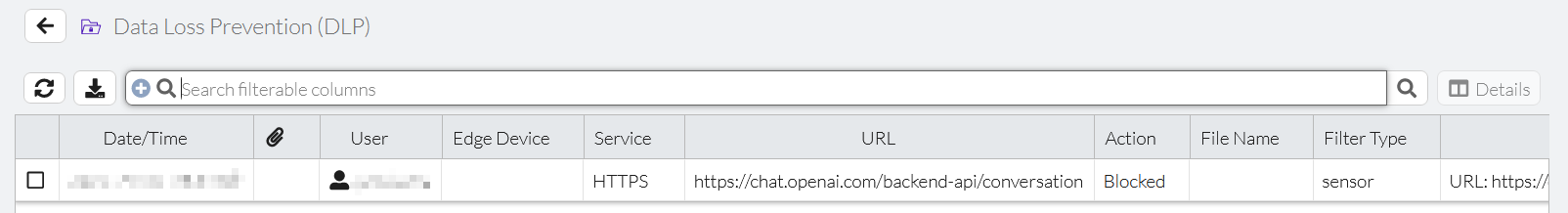
- Go to Analytics > Security > Traffic > Internet Access Traffic and confirm that FortiSASE generated a DLP block log entry that corresponds to your VPN user and visiting https://chat.openai.com.


