Blocking HTTPS upload traffic with credit card info example
This configuration will block HTTPS upload traffic that includes credit card information. The pre-defined data type for credit card is used in the dictionary.
To configure blocking HTTPS upload traffic that includes credit card information:
- Go to Configuration > Security.
- For Profile Group, create a new profile group using + in the Profile Group dropdown list.
- In the Create Profile Group slide-in configure these settings:
- In the Name field, enter Custom-DLP-1.
- For Initial Configuration, select Basic.
- Click OK.
- When prompted to select the new entry, click OK.
- In the Create Profile Group slide-in configure these settings:
- Disable all enabled security features (AntiVirus, Web Filter with Inline-CASB, Intrusion Prevention, DNS Filter, Application Control With Inline-CASB) using these steps for each security feature:
- Click the toggle button next to the security feature widget to disable the feature.
- Click OK to confirm disabling the security feature.
- In the SSL Inspection widget ensure deep inspection is enabled:
- For SSL inspection, click Customize:
- Select Deep Inspection.
- Click OK.
- Enable Data Loss Prevention (DLP).
- Create a DLP rule:
- In the Data Loss Prevention (DLP) widget, click Customize.
- In the DLP slide-in, click Create to create a new DLP rule.
- In the New Rule slide-in, configure these settings:
Field
Value
Name
dlp-case-1 Sensors
Select DLP sensors. You must create a new DLP sensor and then select it. Severity
Medium Action
Block Type
File File type
builtin-patterns Protocol
HTTP-GET, HTTP-POST - Create a new sensor:
- Create a new sensor by clicking + next to Sensor.
- In the Select Entries slide-in, click + Create to the right to create a new sensor.
- In the New Sensor slide-in, configure these settings:
Field
Value
Name
sensor-case-1
Entry matches needed to trigger sensor
Any
Table of entries
Create a new entry.
- Create a sensor entry:
- Create a new sensor entry by clicking +Create.
- In the New Entry slide-in, configure these settings:
Field
Value
ID
1
Dictionary
Select the dictionary for this sensor entry. You must create a new dictionary and then select it.
Dictionary matches needed to consider traffic DLP risk
1
Status
Enabled
- Create a dictionary:
- Click the Dictionary field and click +Create to create a new DLP dictionary.
- In the New DLP Dictionary slide-in, configure these settings:
Field
Value
Name
dl-case-1
Entry matches needed to trigger sensor
Any
Table of Dictionary Entries
Create one or more dictionary entries.
- Create a dictionary entry:
- Create a new dictionary entry by clicking +Create.
- In the New Entry slide-in, configure these settings:
Field
Value
Type
credit-card
Repeat
Disable
Status
Enabled
- Click OK several times to complete the customization:
- Click OK to create the new dictionary entry.
- Click OK to create the DLP dictionary. Click OK when prompted to select the newly created dictionary.
- Click OK to create the new sensor entry.
- Click OK to create the new sensor. Click OK when prompted to select the newly created sensor. Click Close.
- Click OK to create the new DLP rule.
- Click OK to complete DLP configuration customization.
- Configure the updated profile group in a policy:
- Go to Configuration > Policies.
- Configure a new policy with these settings:
Field
Value
Name
Test-DLP-1
Source Scope
VPN Users
Source
All Traffic
User
All VPN Users
Destination
All Internet Traffic
Service
ALL
Action
Accept
Profile Group
Specify
Select Custom-DLP-1
Status
Enable
Log Allowed Traffic
Enable
Select All Sessions
- Click OK.
-
Drag the Test-DLP-1 to the top of the policy list. Ensure it is placed above Allow-All.
To verify blocking HTTPS upload traffic that includes credit card information is working:
- Ensure that your endpoint with FortiClient installed is registered with FortiSASE Endpoint Management Service and that you have established a secure connection to FortiSASE.
- On the connected endpoint, open the Chrome web browser in incognito mode.
- In the web browser, go to https://dlptest.com/sample-data/. Copy one of the credit card numbers from the page and paste it into a Word document. Save the document in .DOC format to your endpoint local drive as cc-test.doc.
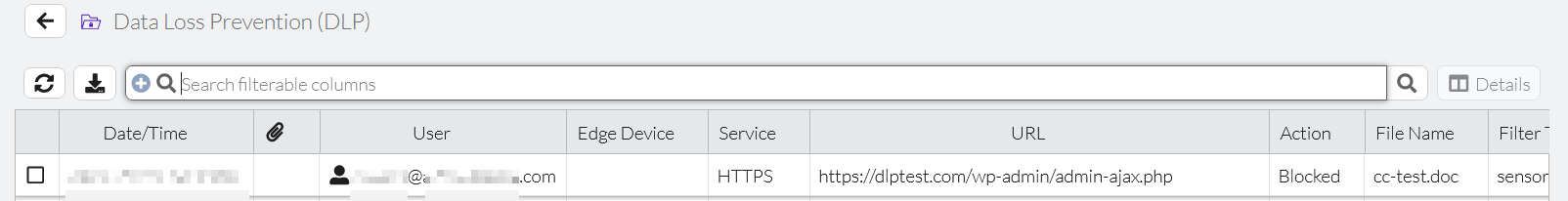
- Go to https://dlptest.com/https-post/. Under File Upload, select the .DOC file created and click Submit. Since HTTP POST traffic for the PDF file upload includes a credit card number, FortiSASE blocks the file and generates a DLP log.
- In FortiSASE, go to Analytics > Security > Data Loss Prevention (DLP) and confirm that FortiSASE generated a DLP block log entry that corresponds to your VPN user and cc-test.doc filename.