What's new
The following sections describe new features, enhancements, and changes in FortiProxy 7.2.10:
-
Configure port of data session to connect FTP client in active mode
-
Log client IP from headers without using the IP for policy matching
- TLS 1.3 support for LDAP connections
Manually upload license in air-gapped environments
You can now manually upload a FortiProxy license in air-gapped environments. Refer to Licensing in air-gap environments in the FortiProxy 7.2.10 Administration Guide for detailed instructions.
New shaper-related fields in traffic logs
FortiProxy 7.2.10 adds the following shaper-related fields to traffic logs:
-
shaperdroprcvdbyte
-
shaperdropsentbyte
-
shaperperipdropbyte
-
shaperperipname
-
shaperrcvdname
-
shapersentname
-
shapingpolicyid
-
shapingpolicyname
Refer to the FortiProxy Log Message Reference Guide for more details.
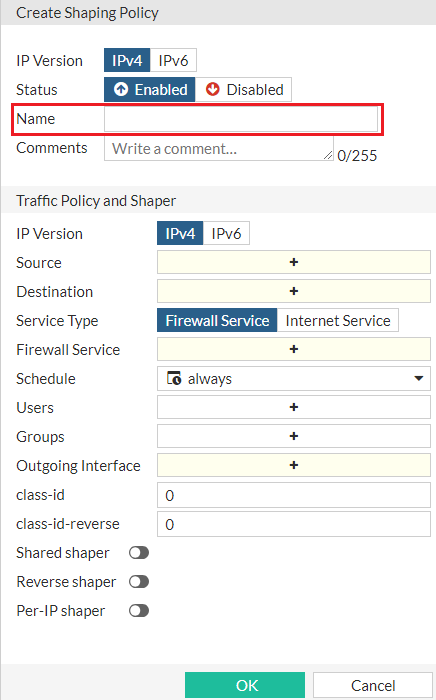
Specify the name for a traffic shaping policy
In FortiProxy 7.2.10, you can specify the policy name when you Create or edit a traffic shaping policy:
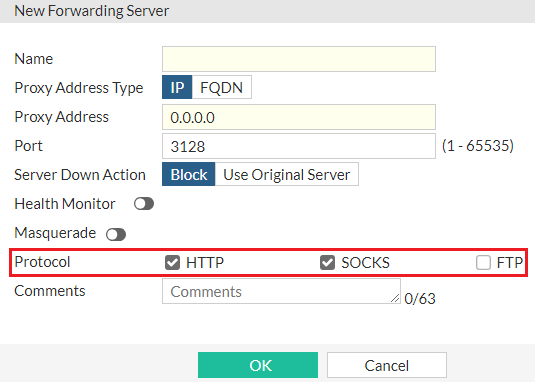
Configure the protocol for forwarding servers in GUI
In FortiProxy 7.2.10, you can configure the protocol when you create or edit a forwarding server in the GUI:
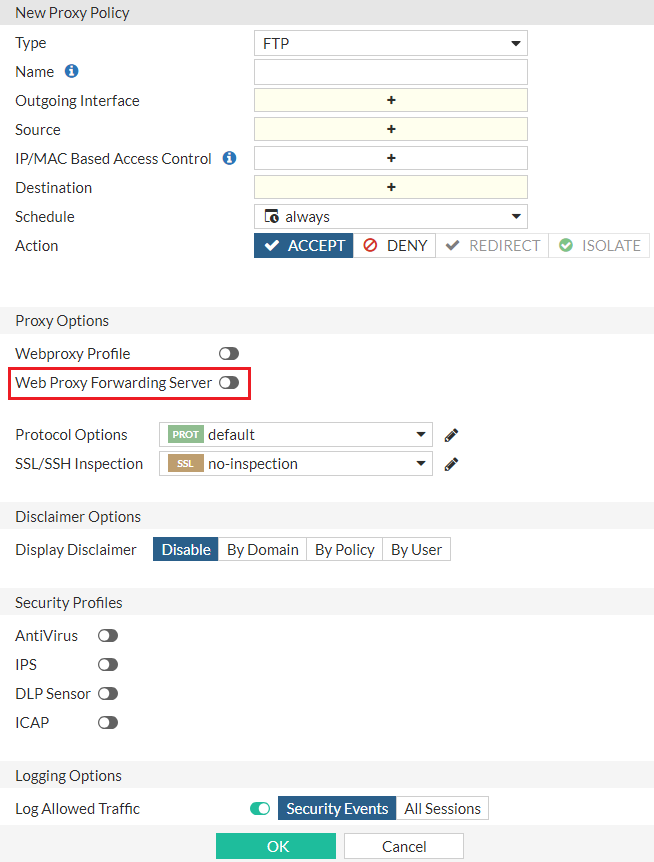
Configure the forwarding server for FTP policies in GUI
In FortiProxy 7.2.10, you can configure the forwarding server when you create or edit an FTP policy in the GUI:
Configure port of data session to connect FTP client in active mode
You can now configure the port of data session to connect FTP client in active mode using the new set active-src-port subcommand under config ftp-proxy explicit. It can be the incoming port (default) or the same port as FTP server source port. The configuration helps enable compatibility with network devices that must perform deep inspection of FTP proxy data (such as load balancers) where active mode client connections are required.
Log client IP from headers without using the IP for policy matching
In FortiProxy 7.2.10, you can configure the web proxy to log the client's IP address from headers without using the IP for policy matching. To do so, use the new log-only option of the learn-client-ip subcommand under config web-proxy global.
TLS 1.3 support for LDAP connections
FortiProxy 7.2.10 adds support for TLS 1.3 for LDAP connections. Under config user ldap, use the new ssl-max-proto-version subcommand to configure the maximum supported protocol version for SSL/TLS connections. Use the new TLSv1-3 option of the ssl-min-proto-version subcommand to configure TLS v1.3 as the minimum supported protocol version for SSL/TLS connections.
ZSTD HTTP encoding support for AV scan
FortiProxy 7.2.10 adds support for ZSTD HTTP encoding for AV scan.
Change to default status of fg-fm port
In FortiProxy 7.2.10, the fg-fm port (TCP 541) is disabled on all interfaces by default. To add a FortiProxy to FortiManager for management, you must open the port on the FortiProxy first.
Monitoring the status of the PSUs for FPX-400G
FortiProxy 7.2.10 adds support for PSU monitoring for FPX-400G. A log message is generated if a FPX-400G power supply unit (PSU) loses or regains power.
No support for SSL VPN
FortiProxy 7.2.10 no longer supports SSL VPN.
CLI changes
FortiProxy 7.2.10 includes the following CLI changes:
-
config user ldap—Use the newssl-max-proto-versionsubcommand to configure the maximum supported protocol version for SSL/TLS connections. Thessl-min-proto-versionsubcommand adds theTLSv1-3option which you can use to configure TLS v1.3 as the minimum supported protocol version for SSL/TLS connections. -
config web-proxy global—Thelearn-client-ipsubcommand adds thelog-onlyoption, which allows the web proxy to learn the client's IP address from headers and use it only for logging without using it for policy matching. Meanwhile, the optionenableis renamedtraffic-process, which allows the web proxy to learn the client's IP address from headers and use it for both policy-matching and logging. -
config ftp-proxy explicit—Use the newset active-src-portsubcommand to configure the port of data session to connect FTP client in active mode. It can be the incoming port (default) or the same port as FTP server source port. -
diag wad stats—This command can now show UNIX stream statistics of different WAD daemons.Example output:
dut6 (Interim)# diag wad stats worker.proc_common
worker.proc_common.unix_sock.config.in_buf_len 0
worker.proc_common.unix_sock.config.out_buf_len 0
worker.proc_common.unix_sock.config.n_output 64
worker.proc_common.unix_sock.config.n_input 192
worker.proc_common.unix_sock.config.n_reconnect 2
worker.proc_common.unix_sock.config.n_connect_fails 0
worker.proc_common.unix_sock.config.n_write_block 0
worker.proc_common.unix_sock.config.n_fd 0
worker.proc_common.unix_sock.fast_match.in_buf_len 0
worker.proc_common.unix_sock.fast_match.out_buf_len 0
worker.proc_common.unix_sock.fast_match.n_output 1
worker.proc_common.unix_sock.fast_match.n_input 3
worker.proc_common.unix_sock.fast_match.n_reconnect 1
worker.proc_common.unix_sock.fast_match.n_connect_fails 0
worker.proc_common.unix_sock.fast_match.n_write_block 0
worker.proc_common.unix_sock.fast_match.n_fd 0

