Whatʼs new
The following sections describe the new features and enhancements:
- Proxy settings
- Policy and objects
- Security profiles
- Content analyses
- WAN optimization
- User and authentication
- System
- Security Fabric
- Log and report
Proxy settings
This section includes new features related to proxy settings:
- LDAP user cache
- New masquerade command for the isolator server
- Web proxy header expanded
- Increased size of the cache object
- Disabling IP-based URL rating
- HTTP domain fronting blocking
- Use the body of the HTTP POST method to control web access
LDAP user cache
You can now use the following CLI commands to control the LDAP user cache for explicit proxy and transparent proxy users:
config web-proxy global
set ldap-user-cache {enable | disable}
end
New masquerade command for the isolator server
You can now use the CLI to control whether the web proxy uses the device address to connect to the proxy server for the isolator server. By default, this feature is enabled.
config web-proxy isolator-server
edit <server_name>
set masquerade {enable | disable}
next
end
Web proxy header expanded
The set content command (under the config web-proxy profile command) was previously limited to 256 characters. The header content can now be as long as 512 characters.
Increased size of the cache object
Use the following CLI commands to set the maximum size of the cacheable object:
config webcache settings
set max-object-size <1-2147483>
end
Disabling IP-based URL rating
You can now disable IP-based URL rating for SSL-exemption and proxy-address objects. By default, IP-based URL rating is enabled. Use the following CLI commands:
config firewall ssl-ssh-profile
edit <name>
set ssl-exemption-ip-rating {enable | disable}
next
end
config web-proxy global
set address-ip-rating {enable | disable}
end
HTTP domain fronting blocking
You can now block HTTP domain fronting with the following commands:
config firewall profile-protocol-options
edit <name>
config http
set domain-fronting disable
end
next
end
Use the body of the HTTP POST method to control web access
You can now control access to web services based on login information. Use the new set post-arg command:
config firewall proxy-address
edit <name>
set post-arg {enable | disable}
next
end
For example:
config firewall proxy-address
edit "xaddr-url-user"
set host "all"
set path "/t"
set query "username=.*&"
set post-arg enable
next
end
Policy and objects
This section includes new features related to policies and objects:
New pass-through policy
There is a new option to define a policy as a pass-through policy. When traffic matches a pass-through policy, the firewall continues to the next policy. After FortiProxy tries to match all policies, it will set the last matched pass-through policy as the matched policy. By default, the pass-through option is disabled.
To enable a pass-through policy in the GUI:
- Go to Policy & Objects > Policy.
- Create a new policy or edit an existing policy.
- Enable Enable Policy Matching Pass Through.
- Configure the remaining settings as needed.
- Click OK.
To control a pass-through policy in the CLI:
config firewall policy
edit <policy_ID>
set pass-through {enable | disable}
next
end
Export policy list to CSV and JSON formats
In the Policy list page, users can export the current view to CSV and JSON formats.
To export the policy list to a CSV or JSON file:
- Go to Policy & Objects > Policy.
- In the toolbar above the list, click Export.
- Select CSV or JSON.
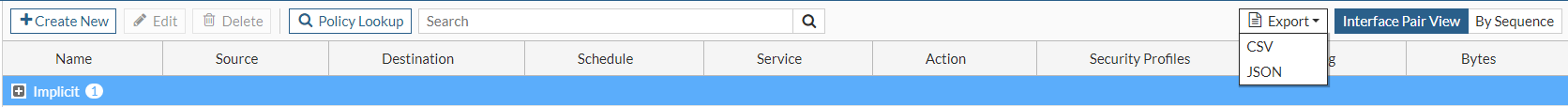
The file is automatically downloaded.
Security profiles
This section includes new features related to security profiles:
Client authentication with client certificate for Original Content Server
Clients can now use a client certificate for authentication on behalf of the Original Content Server. Use the following CLI commands:
config firewall ssl-ssh-profile
edit <profile_name>
config ssl-client-certificate
set status <*do-not-offer | keyring-list | ca-sign>
set keyring-list <keyring_list_used_to_find_client_certificate>
set caname <CA_certficate_used_to_sign_client_certificate>
end
next
end
config firewall ssl keyring-list
edit <keyring_list_used_to_find_client_certificate>
set uuid <UUID>
next
end
Content analyses
This section includes new features related to content analyses:
- X-Scan-Progress-Interval header supported in the FortiProxy ICAP client
- Timeout configuration available for the FortiProxy ICAP client
- ICAP load balancing available in the GUI
- ICAP scanning supported for FTP
X-Scan-Progress-Interval header supported in the FortiProxy ICAP client
You can now use the CLI to specify that the X-Scan-Progress-Interval header is used in the FortiProxy ICAP client and specify the scan progress interval value:
config icap profile
edit <profile_name>
set response {enable | disable}
set response-server <name_of_ICAP_server>
set response-path <HTTP_response_processing_service>
set extension-feature scan-progress
set scan-progress-interval <5-30 seconds (default is 10)>
next
end
Timeout configuration available for the FortiProxy ICAP client
You can now use the CLI to configure the number of seconds that the ICAP client waits for a response from the ICAP server:
config icap profile
edit <profile_name>
set timeout <30-3600 seconds (default is 30)>
next
end
ICAP load balancing available in the GUI
You can now configure ICAP load balancing in the GUI:
- Go to Content Analyses > ICAP Load Balancing.
- Click Create New.
- Enter a name for the ICAP load-balancing configuration.
- Select the load-balancing method:
- Weighted—Balance the traffic load to ICAP servers based on the assigned weights.
- Least Session—Send new sessions to the ICAP server with the lowest session count.
- Active Passive—Send new sessions to the active ICAP server with the highest weight.
- To create a server list for load balancing, click Create New.
- Select or create a remote server.
- Enter a weight for the remote server.
- Click OK to save the remote server entry.
- Click OK save your ICAP load-balancing configuration.
ICAP scanning supported for FTP
NOTE: The ICAP profile must be configured in the CLI before it is used in the GUI.
To forward transferred files with FTP to the ICAP server for further processing using the GUI:
-
Configure the ICAP remote server:
-
Go to Content Analyses > ICAP Remote Server.
-
Create a new configuration for an ICAP server or edit an existing configuration.
-
Click OK.
-
-
Create an ICAP profile that references the ICAP remote server:
-
Go to Content Analyses > ICAP Profile.
-
Click Create New.
-
In the FTP section, click FTP.
-
From the Server dropdown, select the ICAP server to use for the file transfer.
-
Click Error or Bypass for the action to take if the ICAP server cannot be contacted when processing a file transfer.
-
In the Path field, enter the path of the file transfer processing service.
-
Configure the remaining settings as needed.
-
Click OK to save the ICAP profile.
-
-
Create an explicit FTP proxy policy that uses the ICAP policy:
-
Go to Policy & Objects > Policy.
-
Click Create New.
-
Select FTP in the Type dropdown.
-
Enable ICAP and select the ICAP profile that references the ICAP remote server.
-
Enable Enable this policy.
-
Configure the remaining settings as needed.
-
Click OK.
-
To forward transferred files with FTP to the ICAP server for further processing using the CLI:
- Configure the ICAP remote server:
config icap server
edit <name_of_ICAP_server>
set ip-version {4 | 6}
set ip-address <IPv4_address_of_ICAP_server>
set ip6-address <IPv6_address_of_ICAP_server>
set port <ICAP_server_port>
set max-connections <1-65535>
set secure {enable | disable}
next
end
For example:
config icap remote-server
edit "icap1"
set ip-address 172.18.20.43
next
end
- Create an ICAP profile that references the ICAP remote server:
config icap profile
edit {<ICAP_profile_name>new | default}
set replacemsg-group <replacement_message_group>
set request {disable | enable}
set response {disable | enable}
set file-transfer ftp
set file-transfer-server <remote_server_name>
set file-transfer-failure {error | bypass}
set file-transfer-path <string>
set streaming-content-bypass {disable | enable}
set allow-204-response {disable | enable}
set preview {disable | enable}
set methods {delete | get | head | options | post | put | trace | other}
set icap-block-log {disable | enable}
set chunk-encap {disable | enable}
set extension-feature scan-progress
set timeout {30-3600}
set preview-data-length <0-4096>
set request-server <ICAP_server>
set response-server <ICAP_server>]
set request-failure {error | bypass}
set response-failure {error | bypass}
set request-path <string>
set response-path <string>
set response-req-hdr {disable | enable}
set respmod-default-action {forward | bypass}
next
end
For example:
config icap profile
edit "new1"
set request enable
set response enable
set file-transfer ftp
set request-server "icap1"
set response-server "icap1"
set file-transfer-server "icap1"
set request-path "test"
set response-path "test"
set file-transfer-path "test"
next
end
- Create an explicit FTP proxy policy that uses the ICAP policy:
config firewall policy
edit <policy_ID>
set type explicit-ftp
set status enable
set name <policy_name>
set uuid <UUID>
set dstintf <interface_name>
set srcaddr <address_name>
set dstaddr <address_name>
set srcaddr6 <address_name>
set dstaddr6 <address_name>
set action {accept | deny}
set schedule {<schedule_name} | always | none}
set ztna-ems-tag <address_name>
set ztna-tags-match-logic {or | and}
set internet-service {enable | disable}
set pass-through {enable | disable}
set internet-service-name <Internet_service_name>
set logtraffic {all | utm | disable}
set logtraffic-start {enable | disable}
set groups <group_name>
set users <user_name>
set comments <string>
set replacemsg-override-group <string>
set srcaddr-negate {enable | disable}
set dstaddr-negate {enable | disable}
set max-session-per-user <0-4294967295>
set profile-group <profile_group_name>
set profile-protocol-options <profile_name>
set ssl-ssh-profile <profile_name>
next
end
For example:
config firewall policy
edit 3
set type explicit-ftp
set uuid 9b932658-3214-51ec-f906-09ea9dd7e6dd
set dstintf "port1"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set utm-status enable
set logtraffic all
set ssl-ssh-profile "certificate-inspection"
set av-profile "fai"
set icap-profile "new1"
next
end
WAN optimization
This section includes new features related to WAN optimization:
TLS 1.3 supported for WAN optimization
WAN optimization now supports TLS 1.3.
Tracking WAD memory
Use the following command to check how much memory has been allocated for the WAN-optimization daemon (WAD):
diagnose wad memory track [<mem-id>]
User and authentication
This section includes new features related to users and authentication:
SAML features improved
The following SAML features have been improved:
- You can now use external browser SAML authentication.
- Clock-skew tolerance is now supported.
- Error messages have been improved.
System
This section includes new features related to system:
Disable weak ciphers in the HTTPS protocol
Administrators can select what ciphers to use for TLS 1.3 in administrative HTTPS connections and what ciphers to ban for TLS 1.2 and below.
To select the ciphers to use for TLS 1.3 and ban for TLS 1.2 and lower:
config system global
set admin-https-ssl-ciphersuites {TLS-AES-128-GCM-SHA256 TLS-AES-256-GCM-SHA384 TLS-CHACHA20-POLY1305-SHA256 TLS-AES-128-CCM-SHA256 TLS-AES-128-CCM-8-SHA256}
set admin-https-ssl-banned-ciphers {RSA DHE ECDHE DSS ECDSA AES AESGCM CAMELLIA 3DES SHA1 SHA256 SHA384 STATIC CHACHA20 ARIA AESCCM}
end
|
admin-https-ssl-ciphersuites {TLS-AES-128-GCM-SHA256 TLS-AES-256-GCM-SHA384 TLS-CHACHA20-POLY1305-SHA256 TLS-AES-128-CCM-SHA256 TLS-AES-128-CCM-8-SHA256} |
Select one or more TLS 1.3 cipher suites to enable. Ciphers in TLS 1.2 and below are not affected. At least one must be enabled. To disable all, remove TLS1.3 from TLS-AES-128-CCM-SHA256 and TLS-AES-128-CCM-8-SHA256 are only available when strong-crypto is disabled. |
|
admin-https-ssl-banned-ciphers {RSA DHE ECDHE DSS ECDSA AES AESGCM CAMELLIA 3DES SHA1 SHA256 SHA384 STATIC CHACHA20 ARIA AESCCM} |
Select one or more cipher technologies that cannot be used in GUI HTTPS negotiations. Only applies to TLS 1.2 and below. |
To test connecting from a PC using one of the cipher suites:
-
Disable strong-crypto and select all five cipher suites:
config system global set admin-https-redirect disable set admin-https-ssl-ciphersuites TLS-AES-128-GCM-SHA256 TLS-AES-256-GCM-SHA384 TLS-CHACHA20-POLY1305-SHA256 TLS-AES-128-CCM-SHA256 TLS-AES-128-CCM-8-SHA256 set strong-crypto disable end -
Connect from a PC using TLS_AES_128_CCM_SHA256:
~$ openssl s_client -connect 172.16.200.101:443 -tls1_3 -ciphersuites TLS_AES_128_CCM_SHA256 CONNECTED(00000005) Can't use SSL_get_servername depth=0 O = Fortinet Ltd., CN = FortiGate ... --- New, TLSv1.3, Cipher is TLS_AES_128_CCM_SHA256 Server public key is 2048 bit ....
-
Enable strong-crypto:
config system global set strong-crypto enable end TLS cipher suite 'TLS-AES-128-CCM-SHA256' can not be supported so removed. TLS cipher suite 'TLS-AES-128-CCM-8-SHA256' can not be supported so removed. -
Try to connect from the PC again using TLS_AES_128_CCM_SHA256:
~$ openssl s_client -connect 172.16.200.101:443 -tls1_3 -ciphersuites TLS_AES_128_CCM_SHA256 CONNECTED(00000005) 139694547268800:error:14094410:SSL routines:ssl3_read_bytes:sslv3 alert handshake failure:../ssl/record/rec_layer_s3.c:1528:SSL alert number 40 --- no peer certificate available --- No client certificate CA names sent --- SSL handshake has read 7 bytes and written 211 bytes Verification: OK --- New, (NONE), Cipher is (NONE) Secure Renegotiation IS NOT supported ....
The connection fails because TLS_AES_128_CCM_SHA256 is not supported when strong-ctrypo is enabled.
Security Fabric
This section includes new features related to the Security Fabric:
FortiAI integration
FortiAI can now be added to the Security Fabric.
To add FortiAI to the Security Fabric in the GUI:
- Go to System > Settings.
- In the FortiAI section, enable Status.
- Click Apply.
- Go to Security Fabric > Fabric Connectors.
- Double-click Security Fabric Setup to enable the Security Fabric and configure the interface to allow other Security Fabric devices to join.
- Click OK.
-
In FortiAI, configure the device to join the Security Fabric:
-
Go to Security Fabric > Fabric Connectors and double-click the connector card.
-
Enable Enable Security Fabric.
-
Enter the FortiProxy root IP address and the FortiAI IP address.
-
Click OK.
-
-
Authorize FortiAI in FortiProxy:
-
Go to Security Fabric > Fabric Connectors.
-
In the topology tree in the rightmost pane, click the highlighted FortiAI serial number and click Authorize.
The authorized device appears in the topology tree. Hover over the device name to view the tooltip.
The Security Fabric widget on the dashboard also updates when the FortiAI is authorized.
- Click OK.
-
To add a Fabric Device widget for FortiAI:
-
Go to Dashboard > Status and click Add Widget.
-
In the Security Fabric section, click the + beside Fabric Device.
-
For Device, select the FortiAI device.
-
Select a Widget name and Visualization type from the dropdowns.
-
Click Add Widget and click Close.
The Fabric Device widget is displayed in the dashboard.
To add FortiAI to the Security Fabric in the CLI:
- Configure the interface to allow other Security Fabric devices to join:
config system interface edit "port1" ... set allowaccess ping https ssh http fgfm fabric ... next end
- Configure the Security Fabric:
config system csf set status enable set group-name "FortiAI" set group-password ******** config trusted-list edit "FAIVMSTM21000000" set authorization-type certificate set certificate "****************" next end end
- In FortiAI, configure the device to join the Security Fabric:
config system csf set status enable set upstream-ip 172.18.64.122 set managment-ip 172.18.64.114 end
- In FortiProxy, enable FortiAI:
config system fortiai set status enable end
Support new external resource type for URL lists
You can now create and use lists of external URLs. The URL list is a plain text file with one URL on each line.
To specify external URL lists in the GUI:
- Go to Security Fabric > External Connectors.
- Click Create New.
- Under Threat Feeds, click URL List.
- In the Name field, enter a name for the URL list.
- In the URL of external resource field, enter the Uniform Resource Identifier (URI) of the URL list.
- If you enable HTTP basic authentication, enter the user name and password.
- In the Refresh Rate field, enter the number of minutes before the URL list is refreshed.
- In the Comments field, enter a description of the URL list.
- Make certain that Status is enabled.
- Click OK.
To specify external URL lists in the CLI:
- Specify the URL list as an external resource:
config system external-resource
edit <external_resource_name>
set type url
set resource <URI_of_URL_list>
set username <user_name_for_HTTP_basic_authentication>
set password <password_for_HTTP_basic_authentication>
set refresh-rate <1-43200 minutes>
set comments <string>
set status enable
next
end
For example:
config system external-resource
edit "user-list1"
set type url
set resource "http://172.16.80.129/byte1.txt"
next
end
- Create a web proxy address that uses the URL list:
config firewall proxy-address
edit "<address_name>
set type url-list
set host {all | none | <string>}
set url-list <external_URL_list>
next
end
For example:
config firewall proxy-address
edit "xaddr-list"
set type url-list
set host all
set url-list "user-list1"
next
end
Log and report
This section includes new features related to logs and reports:
ICAP group and user reported in logs
The ICAP server now reports the group name and user name in the data leak prevention (DLP), antivirus, web filter, and scan unit error logs when an ICAP request meets the blocking criteria.
Web filter log contains more information about HTTP traffic
The web filter log now contains the following information:
- How long it takes to scan the HTTP request
- Client request host header
- Client request host inside of the request line
- Server response code

