Introduction to FortiGate-6000 FGCP HA
FortiGate-6000 supports active-passive FortiGate Clustering Protocol (FGCP) HA between two (and only two) identical FortiGate-6000s. You can configure FortiGate-6000 HA in much the same way as any FortiGate HA setup except that only active-passive HA is supported.
|
|
In Multi VDOM mode, virtual clustering is supported. Virtual clustering is not supported in Split-Task VDOM mode. Split-Task VDOM mode supports standard FGCP HA. |
You must use the 10Gbit HA1 and HA2 interfaces for HA heartbeat communication. The recommended HA heartbeat configuration is to use a cable to directly connect the HA1 interfaces of each FortiGate-6000 and another cable to directly connect the HA2 interfaces of each FortiGate-6000.
You can use switches to connect the HA heartbeat interfaces. Heartbeat packets are VLAN-tagged and you can configure the VLANs used. If you are using switches you must configure the switch interfaces in trunk mode and the switches must allow the VLAN-tagged packets.
To successfully form an FGCP HA cluster, both FortiGate-6000s must be operating in the same VDOM mode (Multi or Split-Task). You can change the VDOM mode after the cluster has formed, but this will disrupt traffic.
As part of the FortiGate-6000 HA configuration, you assign each of the FortiGate-6000s in the HA cluster a chassis ID of 1 or 2. The chassis IDs just allow you to identify individual FortiGate-6000s and do not influence primary unit selection.
|
|
If both FortiGate-6000s in a cluster are configured with the same chassis ID, both chassis begin operating in HA mode without forming a cluster. A message similar to the following is displayed on the CLI console of both devices: HA cannot be formed because this box's chassis-id 1 is the same from the HA peer 'F76E9D3E17000001' chassis-id 1. As well, a log message similar to the following is created: Jan 29 16:29:46 10.160.45.70 date=2020-01-29 time=16:29:51 devname="CH-02" devid="F76E9D3E17000001" slot=1 logid="0108037904" type="event" subtype="ha" level="error" vd="mgmt-vdom" eventtime=1580344192162305962 tz="-0800" logdesc="Device set as HA master" msg="HA group detected chassis-id conflict" ha_group=7 sn="F76E9DT018900001 chassis-id=1" You can resolve this issue by logging into one of the FortiGates and changing its Chassis ID to 2. When this happens, the two chassis will form a cluster. |
Example FortiGate-6000 HA configuration
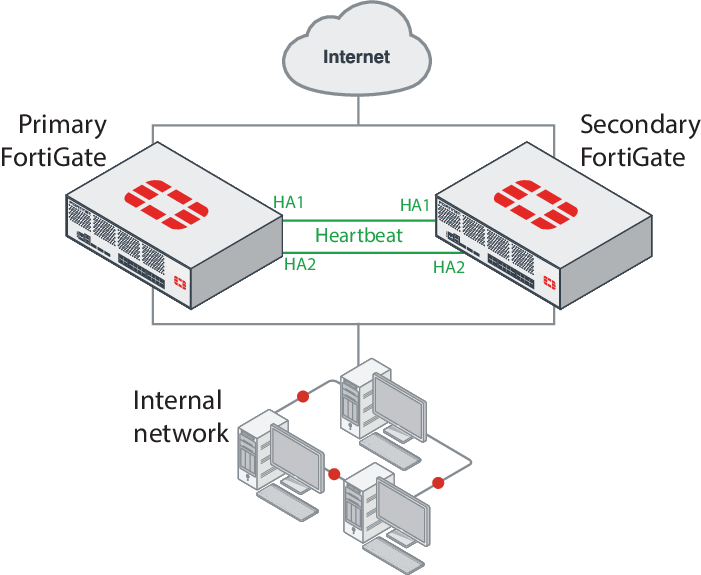
In a FortiGate-6000 FGCP HA configuration, the primary (or master) FortiGate-6000 processes all traffic. The secondary FortiGate-6000 operates in hot standby mode. The FGCP synchronizes the configuration, active sessions, routing information, and so on to the secondary FortiGate-6000. If the primary FortiGate-6000 fails, traffic automatically fails over to the secondary.

