Configuring SSOMA with AD
The FortiClient single sign on mobility agent (SSOMA) supports the following features:
-
Support for pure Microsoft Entra ID (formerly known as Azure Active Directory (AD)) mode. SSOMA sends the Entra ID domain and tenant ID to FortiAuthenticator in pure/native Entra ID mode.
-
Sends FortiClient UUID and EMS serial number/tenant ID to FortiAuthenticator.
-
Sets the SNI field when communicating with FortiAuthenticator.
The following document uses two use cases to illustrate these features. Use case A illustrates a scenario using a local AD. Use Case B illustrates a scenario using a pure/native Entra ID or a hybrid Entra ID.
Use case A: local AD
-
Configure FortiAuthenticator:
-
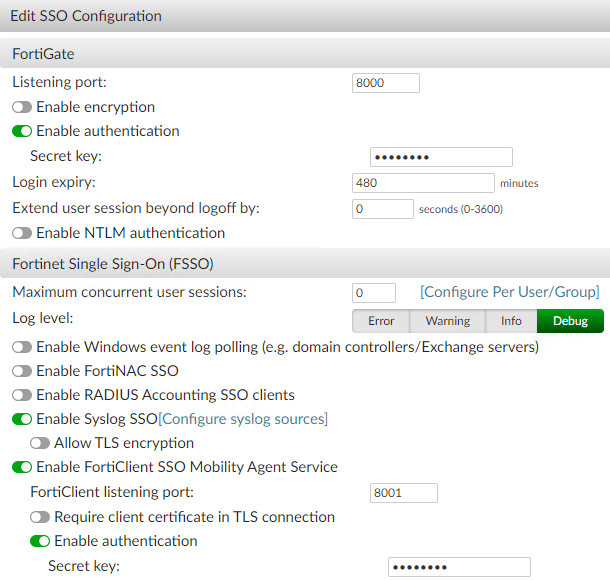
In FortiAuthenticator, go to Fortinet SSO Methods > SSO > General.
-
Toggle on Enable FortiClient SSO Mobility Agent Service.
-
In the FortiClient listening port field, enter 8001.
-
Toggle on Enable authentication.
-
In the Secret key field, enter the desired preshared key. In this example, it is Fortinet123!
-
Go to Authentication > Remote Auth. Servers > LDAP.
-
Add the remote authentication server. In this case, it is the local AD server.
-
-
In EMS, edit the desired endpoint profile's XML configuration to match the IP address, port, and PSK configured on the FortiAuthenticator:
<fssoma> <enabled>1</enabled> <serveraddress>fac0824.local:8001</serveraddress> <presharedkey>Fortinet123!</presharedkey> </fssoma>
- After FortiClient connects to EMS and receives the profile changes, go to Settings. Under Advanced, confirm that SSOMA is enabled and the configuration is updated.
- Under Logging, click Export logs. Confirm that SSOMA sends the FortiClient UUID and EMS serial number/tenant ID to FortiAuthenticator:
6/13/2023 11:38:04 AM debug fsso UUID:2ECE708... 6/13/2023 11:38:04 AM debug fsso strUsername:administrator, strAZDomain:MYFOREST.LOCAL 6/13/2023 11:38:26 AM debug fsso GetAZureSessionUserInfo(), Calling of RunExternalProgram is successful 6/13/2023 11:38:26 AM debug fsso GetAZureSessionUserInfo(), Calling of ParseConsoleOutput is failed, error:-1 6/13/2023 11:38:26 AM debug fsso session ID:2 has added to session table 6/13/2023 11:38:26 AM debug fsso Succeede to add session 2 6/13/2023 11:38:26 AM debug fsso Found current user, session ID: 2 6/13/2023 11:38:26 AM debug fsso CSessionManager::AddSession has been called, dwSession:65536 6/13/2023 11:38:26 AM debug fsso Failed to call WTSQueryUserToken for session ID:65536,error:2 6/13/2023 11:38:26 AM debug fsso Failed to get token for session ID:65536,error:2 6/13/2023 11:38:26 AM debug fsso failed to add session 65536 6/13/2023 11:38:26 AM debug fsso current active session 2 6/13/2023 11:38:26 AM debug fsso Found current logon session 2 in session list 6/13/2023 11:38:26 AM debug fsso CSessionManager::GetAllIPAddress is called 6/13/2023 11:38:26 AM debug fsso CSessionManager::GetAllIPAddress:1293 IPv4 address:192.168.90.2 6/13/2023 11:38:26 AM debug fsso EMS SN:FCTEMS8821090628 6/13/2023 11:38:26 AM debug fsso Start to resolve address for FortiAuthenticator:fac0824.local, TICC:5894281, TID:9072 6/13/2023 11:38:26 AM debug fsso Succeeded to resolve address for FortiAuthenticator:fac0824.local, FAC IP:172.19.200.110, TICC:5894281, TID:9072 6/13/2023 11:38:26 AM debug fsso SendAndReceive(), Local IP:192.168.90.2, FAC IP:172.19.200.110, FAC Port:8001, TICC:5894281, TID:9072 6/13/2023 11:38:26 AM debug fsso SendAndReceive(), succeeded to send event to authenticator, TID:9072 6/13/2023 11:38:26 AM debug fsso FortiAuthenticator config:fac0824.local:8001 6/13/2023 11:38:26 AM debug fsso Address Category:0 6/13/2023 11:38:26 AM info fsso date=2023-06-13 time=11:38:25 logver=1 id=96980 type=securityevent subtype=fsso eventtype=status level=info uid=2ECE708... devid=FCT8000... hostname=DESKTOP-JSOHIL9 pcdomain=myforest.local deviceip=192.168.90.2 devicemac=00-15-5d-23-03-0e site=default fctver=7.2.0.0690 fgtserial=N/A emsserial=FCTEMS88... usingpolicy=Default os="Microsoft Windows 10 Professional Edition, 64-bit (build 19045)" user=administrator msg="Single Sign-On event" action=logon domain="MYFOREST.LOCAL,Workstation Name:DESKTOP-JSOHIL9,IP:192.168.90.2,FAC:172.19.200.110,succeeded to send session info, TICC:5894375, TID:9072"
Use case B: pure/native or hybrid Entra ID
-
Configure Entra ID and add an enterprise application for FSSO:
- Sign in to the Entra ID portal as an administrator. Some configurations require a global administrator privilege.
Create a user and ensure that users may join devices:
Go to Home > Manage Azure Active Directory > View button > Manage > Users > New User. Configure a new user as desired.
- Go to Home > Manage Azure Active Directory > View button > Manage > Devices > Device Settings. Enable Users may join devices to Entra ID.
Create an enterprise application:
Go to Home > Manage Azure Active Directory > View button > Manage > Enterprise Applications > New Application > Create Your Own Application.
Select Integrate any other application you don't find in the gallery (Non-gallery). Configure other settings as desired.
Set the newly created enterprise application as a directory reader:
Go to Home > Manage Azure Active Directory > View button > Manage > Roles and Administrators.
In the Administrative Roles list, search for and select Directory Readers.
Add Assignments > Search for the name of the newly created enterprise application > Add button.
- Register the enterprise application with the Microsoft Identity Platform and generate an authentication key:
Go to Home > Manage Azure Active Directory > View button > Manage > App Registrations > All Applications.
Search for and select the newly created enterprise application.
Click Manage > Certificates & Secrets > New Client Secret.
In the Add a Client dialog, set a description and expiry date, then click Add.
Note down the string in the Value column. This value is only visible immediately after creation and will be hidden after you leave this page. You will use this value later.
-
In EMS, edit the desired endpoint profile's XML configuration to match the IP address, port, and PSK configured on the FortiAuthenticator, and to have FortiClient detect Azure user information and send it to FortiAuthenticator:
<fssoma> <enabled>1</enabled> <serveraddress>fac0824.local:8001</serveraddress> <presharedkey>Fortinet123!</presharedkey> <prefer_azure>1</prefer_azure> </fssoma> - In FortiAuthenticator, configure OAuth:
- Go to Authentication > Remote Auth. Servers > OAUTH > Create New.
- From the OAuth source dropdown list, select Azure Directory.
- In the Client ID field, enter the application ID of the enterprise application that you created. You can find the client ID in Azure by going to Home > Manage Azure Active Directory > View button > (in sidebar) Manage > Enterprise Applications > Search for Application Name.
- In the Client Key field, enter the value from the Value column in step 1.e.v.
- Enable Include for SSO.
- In the Azure AD tenant ID field, enter the tenant ID. You can find this value in Azure by going to Home > Manage Azure Active Directory > View button > Overview > Tenant ID. Click OK.

- Connect the endpoint with Entra ID. On the endpoint, go to Settings > Accounts. Beside Add a work or school account, click Connect.
- Install FortiClient on the endpoint. Go to Settings and verify that FortiClient has received the SSOMA configuration from EMS.
- In FortiAuthenticator, go to Monitor > SSO > SSO Sessions. Confirm that there is an entry for the endpoint.
- In FortiClient, go to Settings > Logging and click Export logs. Confirm that SSOMA sends the FortiClient UUID and EMS serial number/tenant ID to FortiAuthenticator:
6/13/2023 11:29:30 AM debug fsso GetAZureSessionUserInfo(), Calling of RunExternalProgram is successful 6/13/2023 11:29:30 AM debug fsso GetAZureSessionUserInfo(), username:jkim, domain:fortinetvan.onmicrosoft.com, tenantID:f1a72219-... 6/13/2023 11:29:30 AM debug fsso strAZUsername:jkim, strAZDomain:fortinet.onmicrosoft.com, strAZTenantID:f1a72219-... 6/13/2023 11:29:30 AM debug fsso session ID:2 has added to session table 6/13/2023 11:29:30 AM debug fsso Succeede to add session 2 6/13/2023 11:29:30 AM debug fsso Found current user, session ID: 2 6/13/2023 11:29:30 AM debug fsso CSessionManager::AddSession has been called, dwSession:65536 6/13/2023 11:29:30 AM debug fsso Failed to call WTSQueryUserToken for session ID:65536,error:2 6/13/2023 11:29:30 AM debug fsso Failed to get token for session ID:65536,error:2 6/13/2023 11:29:30 AM debug fsso failed to add session 65536 6/13/2023 11:29:30 AM debug fsso CSessionManager::AddSession has been called, dwSession:65537 6/13/2023 11:29:30 AM debug fsso Failed to call WTSQueryUserToken for session ID:65537,error:2 6/13/2023 11:29:30 AM debug fsso Failed to get token for session ID:65537,error:2 6/13/2023 11:29:30 AM debug fsso failed to add session 65537 6/13/2023 11:29:30 AM debug fsso current active session 2 6/13/2023 11:29:30 AM debug fsso Found current logon session 2 in session list 6/13/2023 11:29:30 AM debug fsso CSessionManager::GetAllIPAddress is called 6/13/2023 11:29:30 AM debug fsso CSessionManager::GetAllIPAddress:1325 IPv4 address:192.168.90.5 6/13/2023 11:29:30 AM debug fsso EMS SN:FCTEMS882... 6/13/2023 11:29:30 AM debug fsso Start to resolve address for FortiAuthenticator:fac0824.local, TICC:-1981885328, TID:9452 6/13/2023 11:29:30 AM debug fsso Succeeded to resolve address for FortiAuthenticator:fac0824.local, FAC IP:172.19.200.110, TICC:-1981885328, TID:9452 6/13/2023 11:29:30 AM debug fsso SendAndReceive(), Local IP:192.168.90.5, FAC IP:172.19.200.110, FAC Port:8001, TICC:-1981885312, TID:9452 6/13/2023 11:29:30 AM info fsso date=2023-06-13 time=11:29:29 logver=1 id=96980 type=securityevent subtype=fsso eventtype=status level=info uid=FDE6A554A2... devid=FCT800... hostname=Arjuna pcdomain=N/A deviceip=192.168.90.5 devicemac=00-15-5d-23-03-3f site=default fctver=7.2.1.0759 fgtserial=N/A emsserial=FCTEMS882... usingpolicy=Default os="Microsoft Windows 11 Professional Edition, 64-bit (build 22621)" user=jkim msg="Single Sign-On event" action=logon domain="fortinet.onmicrosoft.com,Workstation Name:Arjuna,IP:192.168.90.5,FAC:172.19.200.110,succeeded to send session info, TICC:-1981885234, TID:9452" 6/13/2023 11:29:30 AM debug fsso SendAndReceive(), succeeded to send event to authenticator, TID:9452 6/13/2023 11:29:30 AM debug fsso FortiAuthenticator config:fac0824.local:8001 6/13/2023 11:29:30 AM debug fsso Address Category:0

