Threat intelligence
FortiNDR Cloud ingests threat intelligence from a wide variety of sources, including commercially purchased feeds, open source threat intelligence data, vertical/industry/government information sharing organizations, and closed trust-based communities. This threat intelligence is reviewed and curated by the Fortinet FortiGuard Labs team, and allows for real-time matching of network traffic against known indicators.
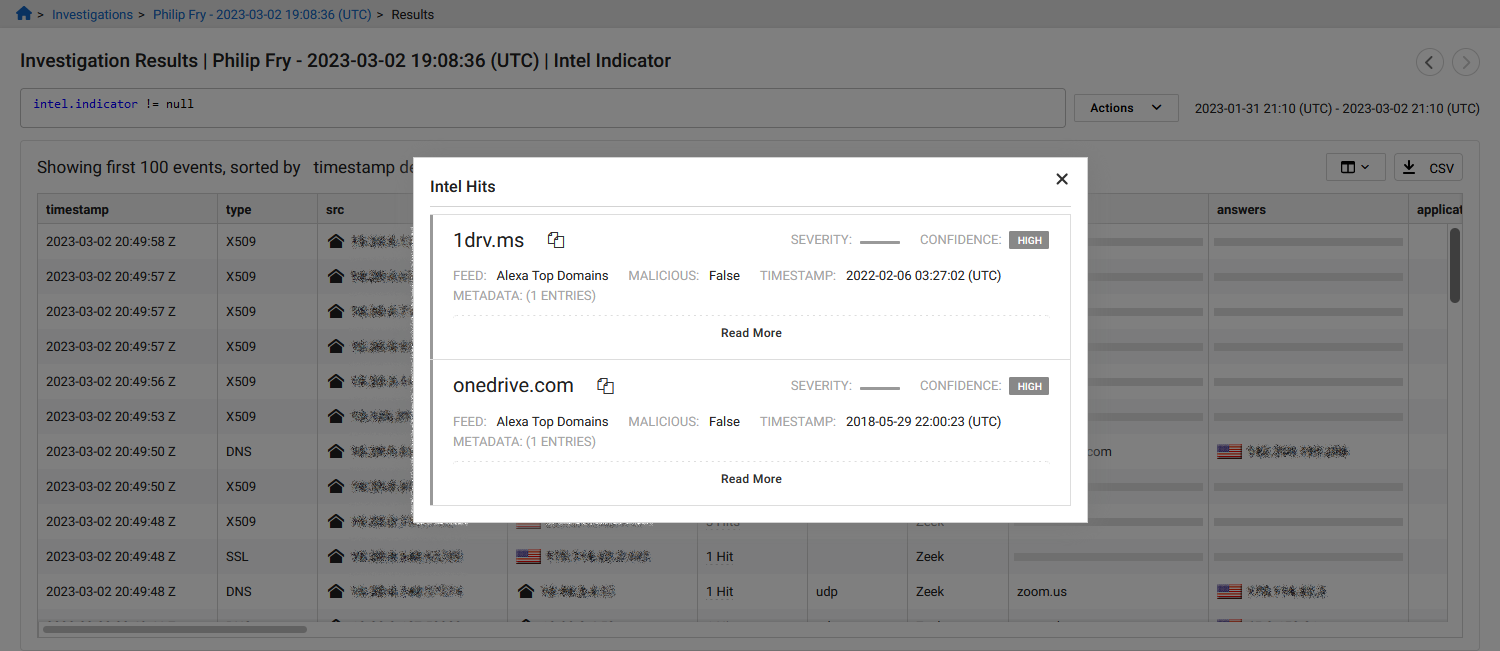
Events are enriched with ingested threat intelligence by matching indicators from the data to entities within an event. All matched intel records are contained within the intel field, which is a common field across all event types. The intel records are then searchable with IQL.
|
|
Contact your TSM if you have access to an intel source or feed that you would like integrated with FortiNDR Cloud. |
Example query:
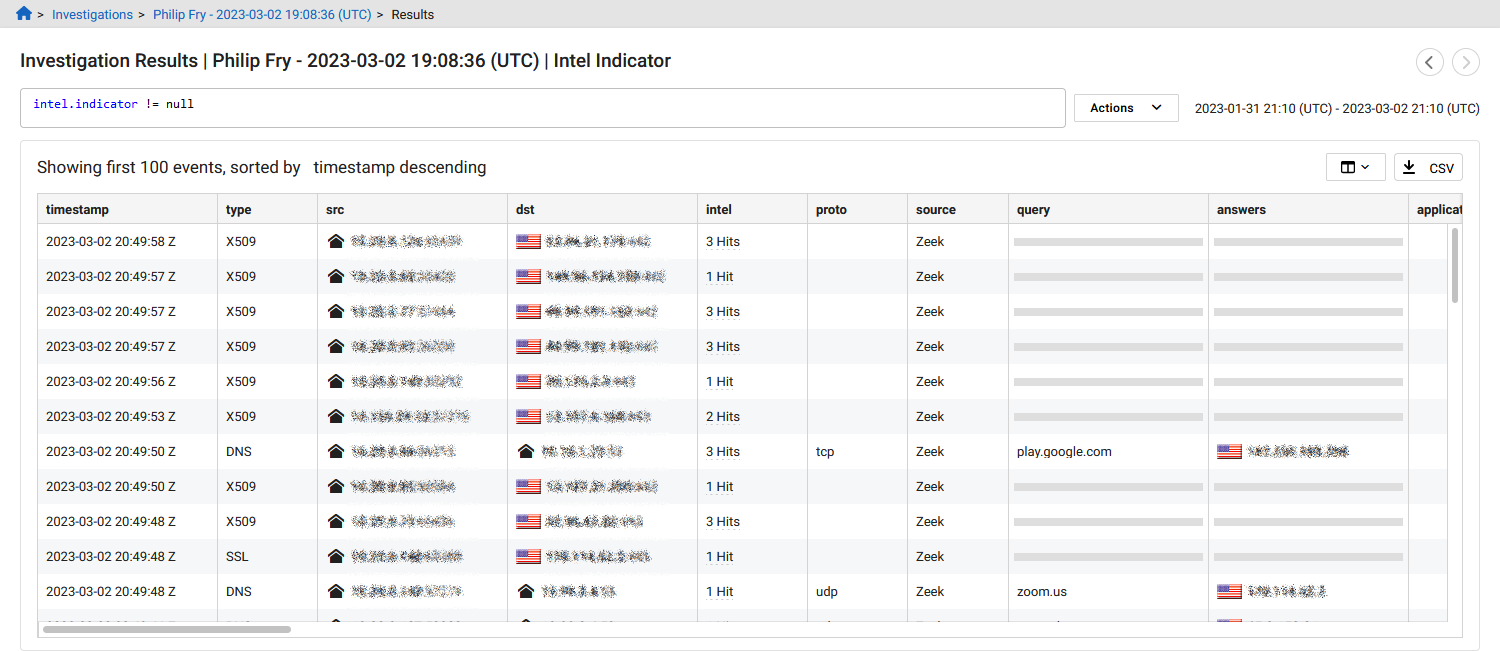
The following query is a simple way to determine whether or not network traffic has matched with threat intelligence data in your network. When the results load, you will notice the intel column shows whether or not an event has a match against a threat intelligence source.
// show events that have at least one matched intel record
intel.indicator != null
Click the number of hits in the Intel column to view the matched intel records.