Configuring network
After you complete the configurations in the Wizard, you can navigate to Network if you want to change the network settings, or configure advanced settings, such as specifying the SSL certificate for HTTPS connections, adding origin servers, etc.
Before setting up the network, it is helpful to understand the traffic flow between the clients, FortiWeb Cloud, and origin servers.
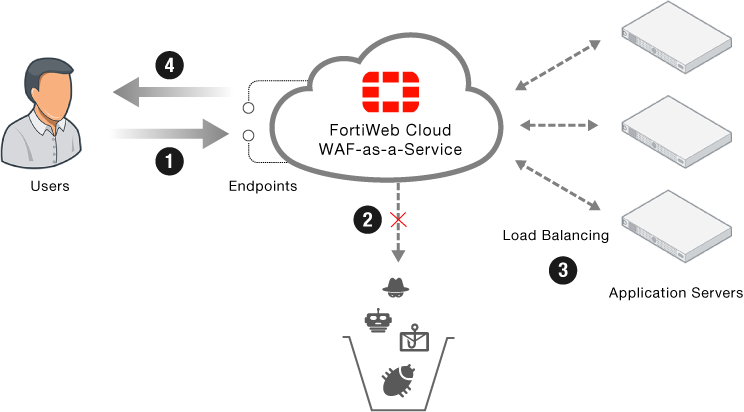
The figure above illustrates the following points:
- When users visit your application, the traffic is directed to the endpoints on FortiWeb Cloud.
- FortiWeb Cloud filters the incoming traffic from users, blocking the OWASP Top 10 attacks, zero day threats, and other application layer attacks.
- Legitimate traffic arrives at origin servers. Load balancing algorithm is used to distribute traffic among servers.
- When FortiWeb Cloud sends responses to your users, it obfuscates sensitive data such as the credit card number and other information that are likely to be used by hackers to damage your business.

