Determining Entra ID SSO credentials
Before you can search user groups from Microsoft Entra ID (formerly known as Azure Active Directory or Azure AD) single sign on (SSO), you must perform some preliminary steps and then determine the SAML provider credentials from the Entra ID portal.
To access the Entra ID portal:
- Log into the Azure portal. You should already have an enterprise application created in Entra ID. If this has not been created, see Creating an enterprise application using FortiSASE as a template from the gallery and collecting SAML IdP URL information.
- On the homepage, do one of the following:
- Under Azure Services, click Microsoft Entra ID.
- Click the navigation menu and under All Services, click Microsoft Entra ID.
To add Microsoft Graph API application permissions required for searching user groups:
- In the left menu, click App registrations, then click the All applications tab.
- Look for the name of your FortiSASE SSL VPN enterprise application and click the hyperlinked name.
- In the left menu, click API permissions, and click Add a permission.

- In the Request API permissions slide-in window, click Microsoft Graph.

- Select Application permissions.
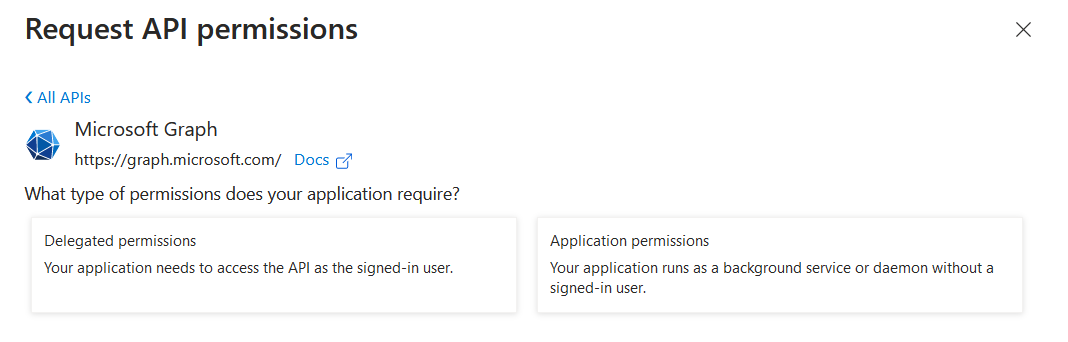
- In the Select permissions section, search for, and select the following permissions by clicking the checkboxes next to these permissions:
- Group.Read.All – Read all groups
- GroupMember.Read.All – Read all group memberships
- Click Add permissions.
- In the API permissions page, click Grant admin consent for Default Directory. If this option is grayed out, you must log into an Entra ID admin account to perform this step.
To add a client secret string and determine the value of the client secret string:
- In the left menu, click App registrations, then click the All applications tab.
- Look for the name of your FortiSASE SSL VPN enterprise application and click the hyperlinked name.
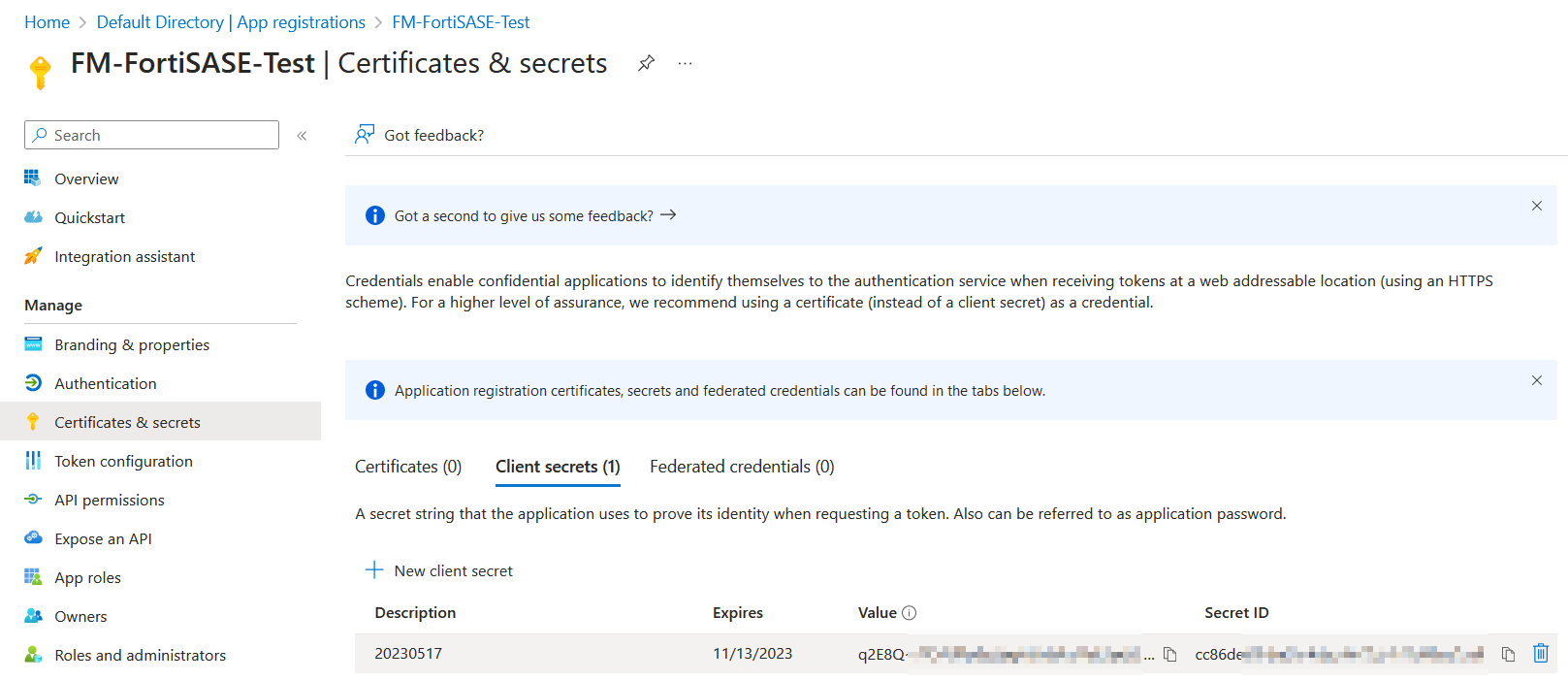
- In the left menu, click Certificates & secrets, and click New client secret.
- In the Add a Client Secret slide-in window, add a Description and select the Expires option of your choice. Click Add.
- Observe that a new client secret has been created. Immediately after creation, ensure you copy the Value of the client secret string, which FortiSASE uses as the Client Secret. This value is not visible after this initial creation step and moving to another page.
To determine the tenant and client IDs:
- In the left menu, click App registrations, then click the All applications tab.
- Look for the name of your FortiSASE SSL VPN enterprise application and click the hyperlinked name.
- In the left menu, click Overview and note the following values:
- Application (client) ID, which FortiSASE uses as the Client ID
- Directory (tenant) ID, which FortiSASE uses as the Tenant ID
Therefore, in summary, you should note the following credentials:
|
Entra ID page within specific enterprise application |
Entra ID field |
FortiSASE field |
|---|---|---|
|
Overview |
Directory (tenant) ID |
Tenant ID |
|
Overview |
Application (client) ID |
Client ID |
|
Certificates & Secrets |
Value |
Client Secret |

