Process Ethernet frames with Cisco Security Group Tag and VLAN tag
|
|
This information is also available in the FortiOS 7.4 Administration Guide: |
The FortiGate has the ability to process Ethernet frames with both the Cisco Security Group Tag and VLAN tag.
The FortiGate can read the Cisco Security Group Tag (SGT) in Ethernet frames with wildcard VLANs, and use them as matching criteria in firewall policies. A policy can match based on the presence of an SGT with wildcard VLAN, or the detection of a specific ID or IDs.
When a packet with an SGT passes through and a session is established, the ext_header_type=0xc5:0xc5 flag is included in the session table.
This feature is available in flow mode policies for virtual wire pair policies or policies in transparent mode VDOMs.
Example
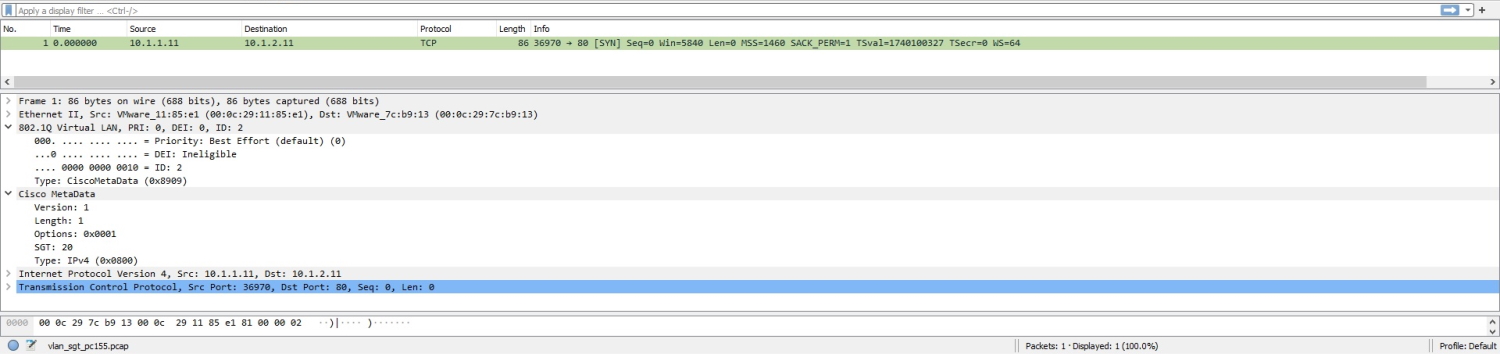
In this example, wan1 and wan2 are in a virtual wire pair. An Ethernet frame is sent from PC01 with an SGT tag (ID 20) and VLAN ID (2), which can pass through to PC05 based on the firewall policy because sgt-check is enabled, and sgt is set to 20.

To configure the FortiGate:
-
Configure the virtual wire pair:
config system virtual-wire-pair edit "test-vwp-1" set member "wan2" "wan1" set wildcard-vlan enable next end -
Configure the firewall policy:
config firewall policy edit 1 set srcintf "wan2" set dstintf "wan1" set action accept set srcaddr "all" set dstaddr "all" set schedule "always" set service "ALL" set auto-asic-offload disable set sgt-check enable set sgt 20 next end
To verify the configuration:
-
Check the session list:
# diagnose sys session list session info: proto=6 proto_state=01 duration=2007 expire=3482 timeout=3600 flags=00000000 socktype=0 sockport=0 av_idx=0 use=3 origin-shaper= reply-shaper= per_ip_shaper= class_id=0 ha_id=0 policy_dir=0 tunnel=/ vlan_cos=0/0 state=may_dirty br statistic(bytes/packets/allow_err): org=164/3/1 reply=120/2/1 tuples=2 tx speed(Bps/kbps): 0/0 rx speed(Bps/kbps): 0/0 orgin->sink: org pre->post, reply pre->post dev=8->7/7->8 gwy=0.0.0.0/0.0.0.0 hook=pre dir=org act=noop 10.1.1.11:36970->10.1.2.11:80(0.0.0.0:0) hook=post dir=reply act=noop 10.1.2.11:80->10.1.1.11:36970(0.0.0.0:0) pos/(before,after) 0/(0,0), 0/(0,0) misc=0 policy_id=1 pol_uuid_idx=572 auth_info=0 chk_client_info=0 vd=0 serial=0432fb8f tos=ff/ff app_list=0 app=0 url_cat=0 rpdb_link_id=00000000 ngfwid=n/a vlanid=2 npu_state=0x4000001 no_offload no_ofld_reason: disabled-by-policy ext_header_type=0xc5:0xc5 -
Perform a packet capture on PC05 (Wireshark is used in this example) and check that the packet includes the VLAN ID and Cisco SGT fields.