Legacy SD-WAN
For decades now, the traditional architecture of hub-and-spoke has served distributed enterprises of all sizes well. Typically, in such architectures, network traffic flows through a central corporate data center — including traffic moving from branch locations to the public internet.
The challenges we are witnessing today with hub-and-spoke designs are confined to the transport mechanisms, not the fundamental structure of hub-and-spoke. The WAN has drastically changed in its consumption, availability, and scalability.
More commonly referred to as SD-WAN, the software-defined WAN sets out to challenge the network designs that have largely remained unchanged for decades. Technological advancements to WAN technologies, alongside a shift in network consumption dynamics, have forced network designers to revisit the tried and tested hub-and-spoke architecture.
The unprecedented growth of SD-WAN is not surprising. Technological transformation of any kind should save money for a business or increase a performance metric. SD-WAN sets out to do both. When implemented correctly, these benefits can be realized within 12 months. This is precisely why the year-on-year growth of SD-WAN shows little sign of stagnation.
Cloud adoption, be it software, infrastructure, or Platform-as-a-Service, and the proliferation of Internet-of-Things (IoT) devices at the network edge are finding a permanent footing within organizations. This contrasts with the traditional HQ data center, where applications, services, and platforms traditionally reside. While the legacy data centers and their traffic flows will remain for the foreseeable future, broader cloud adoption and the proliferation of IoT devices mean the enterprise boundaries are expanding beyond the traditional on-premises data center. This requires a new approach to both network and security architecture.
SD-WAN solutions are not created equally. The first generation of SD-WAN only addressed the transition to cost-effective public WAN options.
Private WAN connections are often expensive. For example, the first generation of SD-WAN technology witnessed many enterprises switch MPLS and P2P lease line connections to broadband or DSL. These connection types are referred to as public WAN connections, which are cost-effective. The first generation of SD-WAN would simply create overlay tunnels ensuring the public WAN connection was secure. This very quickly saved organizations money when compared to the cost of private WAN offering a similar service.
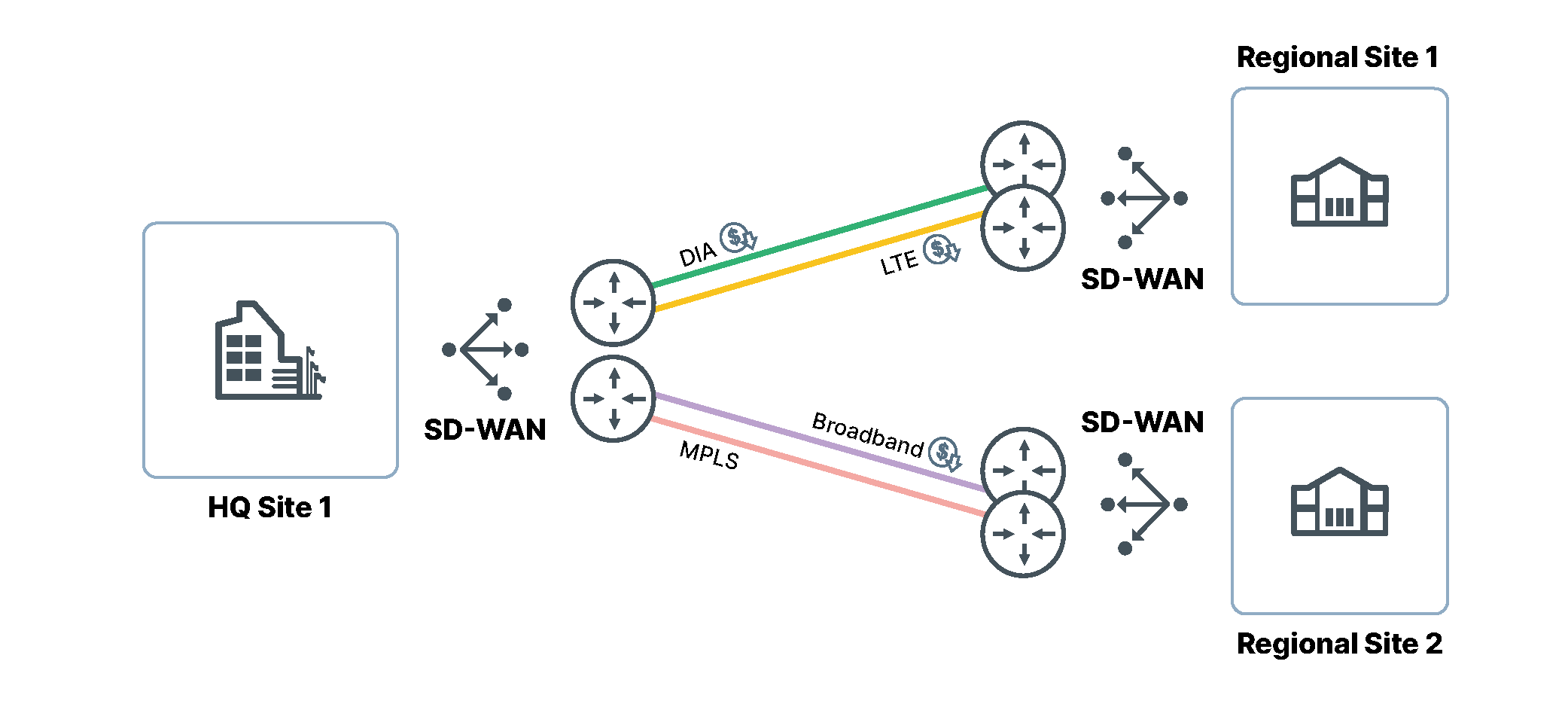
However, aside from cost savings, there was not much more to be gained from the first SD-WAN solutions. There was no technology convergence. In contrast, additional technology was being introduced. The SD-WAN solution of choice also required being managed and maintained. For the modern enterprise, such additional management overheads can quickly offset any savings derived from updating the WAN.
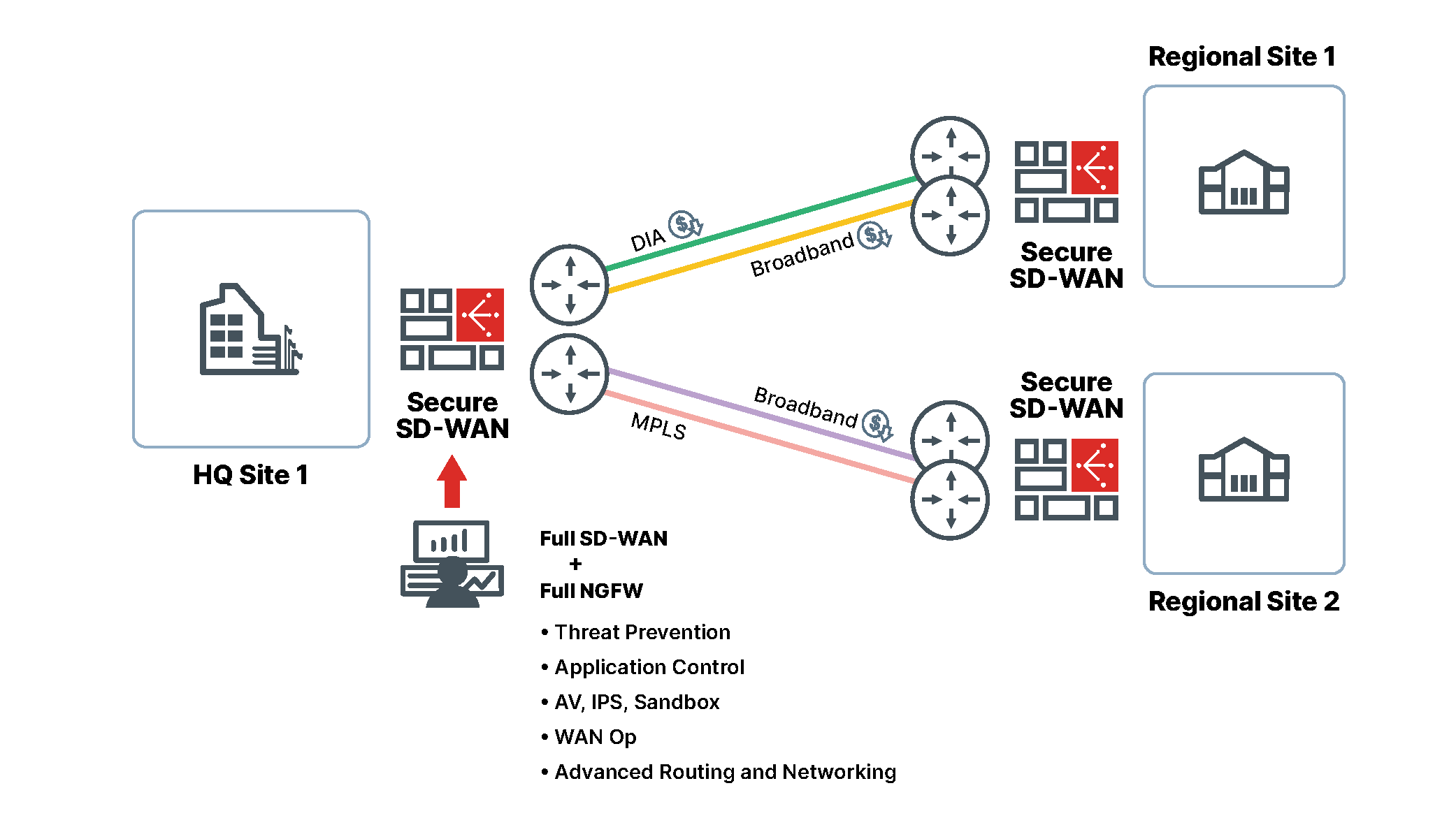
The next generation of SD-WAN witnessed vendors address this technology sprawl issue by combining SD-WAN solutions with other technologies, such as Next-Generation Firewalls. This approach, in theory, is great for enterprises. You save on WAN costs and combine some existing technologies.
The challenges surface when you unpack and validate these combined or embedded technologies. Historically, incorporating technologies that were not designed and built to coexist together does not work well. This is especially true when solutions are under the duress of complex workloads such as SSL and multi-threat inspection workloads.
Ideally, a single solution should be sought to manage SD-WAN and edge security. Such solutions should not be comprised of stitched, bolted, or embedded offerings from technology acquisitions and mergers. Solutions that combine multivendor technology should be avoided or at least thoroughly tested. A single-vendor secure SD-WAN solution should be sought.