Configure FortiGates networking
Configure FortiGates networking
To configure FortiGates networking:
- Log into both FortiGate instances. See the instructions in this document for single FortiGate deployment for instructions on initial login, licensing, and post-deployment steps.
- Go to Network > Static routes.
- Add a static route to 0.0.0.0/0 via the port1 interface. Specify the first address in the external subnet as the gateway address. Ignore the warning that the gateway IP address may be unreachable.
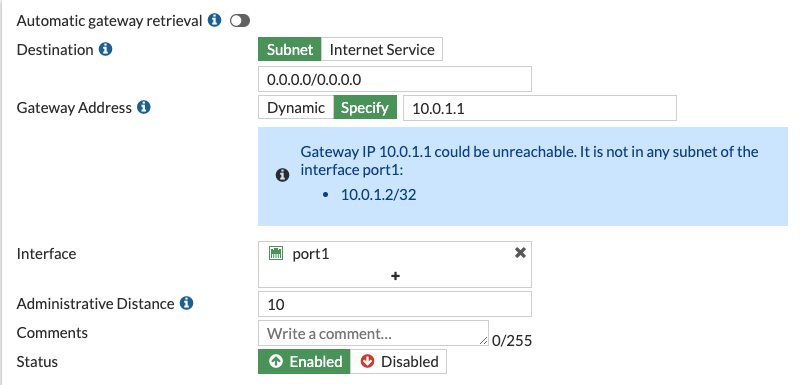
- Add a static route to internal subnet via port2. Specify the first address in the internal subnet as the gateway address. Ignore the gateway reachability warning.

- Add static routes to networks 35.191.0.0/16 and 130.211.0.0/22 via port2 with the first address of the internal subnet as the gateway address.

- In Network > Interfaces, open port1 and port2 and change the Addressing mode from DHCP to Manual. The proper IP address and netmask are autopopulated.
- In Network > Interfaces, open port3 and enable administrative (HTTPS and SSH) access.
Configure FortiGates networking
Configure FortiGates networking
To configure FortiGates networking:
- Log into both FortiGate instances. See the instructions in this document for single FortiGate deployment for instructions on initial login, licensing, and post-deployment steps.
- Go to Network > Static routes.
- Add a static route to 0.0.0.0/0 via the port1 interface. Specify the first address in the external subnet as the gateway address. Ignore the warning that the gateway IP address may be unreachable.

- Add a static route to internal subnet via port2. Specify the first address in the internal subnet as the gateway address. Ignore the gateway reachability warning.

- Add static routes to networks 35.191.0.0/16 and 130.211.0.0/22 via port2 with the first address of the internal subnet as the gateway address.

- In Network > Interfaces, open port1 and port2 and change the Addressing mode from DHCP to Manual. The proper IP address and netmask are autopopulated.
- In Network > Interfaces, open port3 and enable administrative (HTTPS and SSH) access.




