About the connector
FortiSIEM provides integrations that allow you to query and make changes to the CMDB, query events, and send incident notifications. Provide actions like get incidents, comment incident, cleared incident, get device details, get monitored organizations, report related actions and get all associated events for an incident from FortiSIEM.
This document provides information about the Fortinet FortiSIEM Connector, which facilitates automated interactions with your Fortinet FortiSIEM server using FortiSOAR™ playbooks. Add the Fortinet FortiSIEM Connector, as a step in FortiSOAR™ playbooks and perform automated operations such as retrieving device information for all devices configured on the Fortinet FortiSIEM server and retrieving a list of monitored organizations from the Fortinet FortiSIEM server.
You can use FortiSOAR™'s Data Ingestion Wizard to easily ingest data into FortiSOAR™ by pulling incidents from Fortinet FortiSIEM.
For more information, see the Data Ingestion Support section.
NOTE: You must reconfigure data ingestion if you have upgraded your FortiSIEM connector to version5.0.0 (or later) from version 4.5.0. For more information, see the Reconfiguring FortiSIEM Data Ingestion section.
Version information
Connector Version: 5.0.2
FortiSOAR™ Version Tested on: 7.4.0-3204
Fortinet FortiSIEM Version Tested on: 6.7.0 1716
Authored By: Fortinet
Certified: Yes
Release Notes for version 5.0.2
Following changes have been made to the Fortinet FortiSIEM Connector in version 5.0.2:
- Fixed Run Advanced Search Query, Search Events and Get Event Details actions to support the progress response change that occurred with FortiSIEM v6.7.0 and later
- Only FortiSIEM releases 6.7.0 and later are supported by this connector
- The FortiSIEM API no longer supports filtering incidents based on severity and sub-category in the List Incidents action
- Reconfigure Data Ingestion after upgrading the connector
Installing the connector
Use the Content Hub to install the connector. For the detailed procedure to install a connector, click here.
You can also use the yum command as a root user to install the connector:
yum install cyops-connector-fortinet-fortisiem
Prerequisites to configuring the connector
- You must have the URL of Fortinet FortiSIEM server to connect and perform automated operations and credentials to access that server.
- The FortiSOAR™ server should have outbound connectivity to port 443 on the Fortinet FortiSIEM server.
Minimum Permissions Required
Configuring the connector
For the procedure to configure a connector, click here
Configuration parameters
In FortiSOAR™, on the Connectors page, click the Fortinet FortiSIEM connector row (if you are in the Grid view on the Connectors page) and in the Configurations tab enter the required configuration details:
| Parameter |
Description |
| Server URL |
URL of the FortiSIEM server to connect and perform automated operations. |
| Username |
Username used to access the FortiSIEM server to connect and perform the automated operations. |
| Password |
Password used to access the FortiSIEM server to connect and perform the automated operations. |
| Organization |
Name of Organization that you will access on the Fortinet FortiSIEM server to perform the automated operations. |
| Verify SSL |
Specifies whether the SSL certificate for the server is to be verified or not.
By default, this option is set to True. |
Actions supported by the connector
The following automated operations can be included in playbooks and you can also use the annotations to access operations:
| Function |
Description |
Annotation and Category |
| List Incidents |
Retrieves a list and details of incidents from the Fortinet FortiSIEM server based on the search criteria you have specified. |
get_incidents
Investigation |
| Get Incident Details |
Get details of an incident from Fortinet FortiSIEM server based on the incident IDs you have specified. |
get_incident_details
Investigation |
| Update Incident |
Update attributes of specific incident on the Fortinet FortiSIEM server incident ID and other input parameters you have specified. |
update_incident
Investigation |
| Comment Incident |
Adds a comment to a specific incident on the Fortinet FortiSIEM server based on the incident ID you have specified. |
incident_comment
Investigation |
| Clear Incident With Reason |
Clears an incident on the Fortinet FortiSIEM server based on the reason and the incident ID you have specified. |
clear_incident
Investigation |
| Get Events For Incident |
Retrieves all associated events for an incident from the Fortinet FortiSIEM server based on the incident ID you have specified. |
get_associated_events
Investigation |
| Search Events |
Searches for events in the Fortinet FortiSIEM server based on search attributes and other input parameters you have specified. |
search_events
Investigation |
| Get Event Details |
Get details of an event on the Fortinet FortiSIEM server based on the event ID you have specified. |
get_event_details
Investigation |
| Get All Devices |
Retrieves a short description for all devices that are configured on the Fortinet FortiSIEM server. |
get_devices
Investigation |
| Get All Devices For Specified IP Address Range |
Retrieves a short description for devices that are configured on the Fortinet FortiSIEM server, based on the IP address range that you have specified. |
get_devices
Investigation |
| Get Device Information |
Retrieves details of a specific device configured on the Fortinet FortiSIEM server, based on the Device IP that you have specified. |
get_devices
Investigation |
| List Monitored Devices and Attributes |
Retrieves a list and associated attributes of all monitored devices that are configured on the Fortinet FortiSIEM server. |
get_devices
Investigation |
| List Monitored Organizations |
Retrieves a list of all monitored organizations that are configured on the Fortinet FortiSIEM server. |
get_organization
Investigation |
| Get Organization Details |
Retrieves the details of an organization based on the organization ID that you have specified from Fortinet FortiSIEM server. |
get_organization
Investigation |
| Run Advanced Search Query |
Runs an advanced search query on the Fortinet FortiSIEM server, based on the search conditions and other input parameters you have specified. |
run_report
Investigation |
| Get Event Attributes |
Retrieves all event attributes from the Fortinet FortiSIEM server. |
get_incident_attributes
Investigation |
| Get Events Data By Query ID |
Retrieves data for events or incidents from the Fortinet FortiSIEM server based on the executed query ID you have specified. |
get_events_by_query_id
Investigation |
| Create Watch List |
Creates a watch list in the FortiSIEM database. A watch list can contain one or more watch list entries. |
create_watch_list_group
Investigation |
| Get Watch Lists |
Retrieves details for all watch lists or for specific watch lists based on input parameters you have specified. |
get_watch_lists
Investigation |
| Get Watch List Entries Count |
Returns the count of all watch list entries from all watch lists in Fortinet FortiSIEM. |
get_watch_list_entries_count
Investigation |
| Get Watch List Entry |
Retrieves the specific watch list entry from Fortinet FortiSIEM based on the watch list entry ID you have specified. |
get_watch_list_entry
Investigation |
| Add Watch List Entries to Watch List |
Adds watch list entries to one or more watch lists based on watch list ID and other input parameters you have specified. |
update_watch_list_group
Investigation |
| Update Watch List Entry |
Updates a watch list entry in the FortiSIEM database based on watch list entry ID and other input parameters you have provided |
update_watch_list_entry
Investigation |
| Delete Watch List Entry |
Deletes watch list entries from the FortiSIEM database based on the ID of the watch list entries you have specified |
delete_watch_list_entry
Investigation |
| Delete Watch List |
Deletes watch lists from the FortiSIEM database based on the ID of the watch lists you have specified |
delete_watch_list
Investigation |
| Create Lookup Table |
Creates the definition of a lookup table in the FortiSIEM server based on the name, column list, and other input parameters you have specified. |
create_lookup_table
Investigation |
| Get All Lookup Table |
Retrieves the list of all lookupTable definitions from the FortiSIEM server based on the input parameters you have specified. |
get_all_lookup_tables
Investigation |
| Delete Lookup Table |
Deletes the lookupTable definition from the FortiSIEM server based on the lookup table ID you have specified. |
delete_lookup_table
Investigation |
| Import Lookup Table Data |
Imports the data of a specific CSV file in FortiSOAR to a specific lookup table in FortiSIEM based on the File/Attachment IRI, lookup table ID, and other input parameters you have specified. |
import_lookup_table_data
Investigation |
| Check Import Task Status |
Checks the status of the import lookup table data task in FortiSIEM based on the lookup table ID and task ID you have specified. |
check_import_task_status
Investigation |
| Get Lookup Table Data |
Retrieves items of the specified lookup table from FortiSIEM based on the lookup table ID and other input parameters you have specified. |
get_lookup_table_data
Investigation |
| Update Lookup Table Data |
Updates items of a specified lookup table based on the lookup table ID, key, column data, and other input parameters you have specified. |
update_lookup_table_data
Investigation |
| Delete Lookup Table Data |
Delete items of the specified lookup table in FortiSIEM based on the lookup table ID and primary keys you have specified. |
delete_lookup_table_data
Investigation |
| Get All Resource Lists |
Retrieves a list of all resources from the Fortinet FortiSIEM server. |
get_all_resource_list
Investigation |
| Get Resource List Entries |
Retrieves a list of elements that belong to a specific resource list in FortiSIEM based on the resource group ID, resource type, and other input parameters you have specified. |
get_resource_list_entries
Investigation |
| Add Entries To Resource List |
Adds new elements to a specific resource list in FortiSIEM based on the resource group ID, resource data, and resource type you have specified |
add_entries_to_resource_list
Investigation |
| Remove Entries From Resource List |
Deletes elements from a resource list in FortiSIEM based on the resource IDs and resource type you have specified. |
remove_entries_from_resource_list
Investigation |
operation: List Incidents
Input parameters
| Parameter |
Description |
| From |
(Optional) Specify the start datetime to retrieve the incidents from Fortinet FortiSIEM server. |
| To |
(Optional) Specify the end datetime to retrieve the incidents from Fortinet FortiSIEM server. |
| Incident Status |
Select one or more incident status from following options to filter incidents.
- Active
- Manually Cleared
- System Cleared
- Auto Cleared
|
| Incident Category |
(Optional) Specify an incident category to retrieve incidents records for the specified incident category. |
| Incident Sub Category |
(Optional) Specify an incident sub-category to retrieve incidents records for specified incident sub category. |
| Incident Severity |
(Optional) Select one or more incident severities to retrieve incident records. You can choose from the following options:
|
| Event Type |
(Optional) Specify an event type to retrieve the incidents records for specified event type. |
| Other Filters |
Specify parameters in JSON format to filter the response. For example:
{
"status": [
0
],
"eventType": [
"PH_RULE_SERVER_CPU_WARN"
],
"incidentRptIp": [
"10.7.12.156"
]
}
|
| Number Of Items To Return In Response |
(Optional) Specify the maximum number of items for this operation to return in the response. By default, the page size is set to 500 items. |
| Offset |
(Optional) Specify the index of the first item to be returned by this operation. This parameter is useful if to get a subset of records say, incidents starting from the 10th incident. By default, this is set as 0. |
| Order By |
(Optional) Specify the field using which to sort the search results for the report to run on the Fortinet FortiSIEM server. You can also specify the sort direction of the specified field. For example, incidentLastSeen DESC |
| Event Fields To Show In Response |
Specify the fields to display in the response for the report to run on the Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"data": [
{
"count": "",
"customer": "",
"eventName": "",
"eventType": "",
"incidentId": "",
"incidentSrc": "",
"attackTactic": "",
"incidentReso": "",
"eventSeverity": "",
"incidentRptIp": "",
"incidentTitle": "",
"incidentDetail": "",
"incidentStatus": "",
"incidentTarget": {
"hostName": "",
"hostIpAddr": ""
},
"attackTechnique": [
{
"name": "",
"techniqueid": ""
}
],
"eventSeverityCat": "",
"incidentLastSeen": "",
"incidentFirstSeen": "",
"incidentRptDevName": "",
"phIncidentCategory": "",
"incidentClearedTime": "",
"incidentClearedReason": "",
"phSubIncidentCategory": ""
}
],
"size": "",
"start": "",
"total": ""
}
operation: Get Incident Details
Input parameters
| Parameter |
Description |
| Incident IDs |
Specify the ID of the incident to get details from the Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"total": "",
"size": "",
"data": [
{
"incidentTitle": "",
"eventSeverity": "",
"incidentFirstSeen": "",
"incidentReso": "",
"incidentRptIp": "",
"incidentLastSeen": "",
"incidentSrc": "",
"count": "",
"attackTechnique": "",
"eventType": "",
"phIncidentCategory": "",
"incidentClearedTime": "",
"incidentTarget": "",
"attackTactic": "",
"phSubIncidentCategory": "",
"eventSeverityCat": "",
"incidentDetail": "",
"incidentRptDevName": "",
"eventName": "",
"incidentId": "",
"incidentStatus": "",
"customer": ""
}
],
"start": ""
}
operation: Update Incident
Input parameters
| Parameter |
Description |
| Incident ID |
Specify the ID of the incident to update on the Fortinet FortiSIEM server. |
| Comment Text |
Specify the text of the comment to add to the specified incident on the Fortinet FortiSIEM server. |
| Incident Status |
Specify the incident status to update. |
| Incident Severity |
Specify the severity to set for the specified incident on the Fortinet FortiSIEM server. You can choose from the following options:
|
| Incident Resolution |
Specify the resolution to set for the specified incident on the Fortinet FortiSIEM server. You can choose from following options:
- True Positive
- False Positive
|
| External Ticket Type |
Specify the external ticket type to update. |
| External Ticket ID |
Specify the external ticket ID to update. |
| External Ticket State |
Specify the external ticket state to update. |
| External Assigned User |
Specify the external Assigned User to update. |
Output
The output contains the following populated JSON schema:
{
"message": "",
"incident_id": ""
}
operation: Comment Incident
Input parameters
| Parameter |
Description |
| Incident ID |
Specify the ID of the incident in which to add the comment on the Fortinet FortiSIEM server. |
| Comment Text |
Specify the text of the comment to add to the specified incident on the Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"message": "",
"incident_id": ""
}
operation: Clear Incident With Reason
Input parameters
| Parameter |
Description |
| Incident ID |
Specify the ID of the incident to clear from the Fortinet FortiSIEM server. |
| Reason |
Specify the text of the reason to provide which clearing the specified incident from the Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"message": "",
"incident_id": []
}
operation: Get Events For Incident
Input parameters
| Parameter |
Description |
| Incident ID |
Specify the ID of the incident for which to retrieve all events for specified incident from the Fortinet FortiSIEM server. |
| Number Of Items To Return In Response |
(Optional) Specify the maximum number of items for this operation to return in the response. By default, the page size is set to 10 items. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"nid": "",
"index": 0,
"custId": 2000,
"dataStr": {},
"eventType": "",
"attributes": {
"Count": "",
"Event ID": "",
"Source IP": "",
"Time skew": "",
"Event Type": "",
"Attack Name": "",
"Device Time": "",
"Relaying IP": "",
"Collector ID": "",
"Malware Name": "",
"Reporting IP": "",
"Raw Event Log": "",
"Destination IP": "",
"Event Severity": "",
"Organization ID": "",
"Reporting Model": "",
"Reporting Device": "",
"Reporting Vendor": "",
"Source Host Name": "",
"Virus/Malware ID": "",
"Event Parser Name": "",
"Organization Name": "",
"Event Parse Status": "",
"Event Receive Time": "",
"Event Rule Trigger": "",
"Source TCP/UDP Port": "",
"Destination Host Name": "",
"System Event Category": "",
"Event Severity Category": "",
"Destination TCP/UDP Port": "",
"External Event Receive Protocol": ""
},
"rawMessage": "",
"receiveTime": "",
"eventAttributes": []
}
operation: Search Events
Input parameters
| Parameter |
Description |
| Search Attributes |
Select attribute types based on which to search events. You can select from the following options and specify values for the fields that appear:
- Destination Port: Enter value for attribute Destination Port in the Destination Port IN field.
- Destination IP: Enter value for attribute Destination IP in the Destination IP IN field.
- Event ID: Enter value for attribute Event ID in the Event ID IN field.
- Event Action: Select a value for attribute Event Action in the Event Action field.
- Incident ID: Enter value for attribute Incident ID in the Incident ID IN field.
- File Name: Enter value for attribute File Name in the File Name CONTAINS field.
- Host Name: Enter value for attribute Host Name in the Host Name CONTAINS field.
- Organization Name: Enter value for attribute Organization Name in the Organization Name CONTAINS field.
- Process Name: Enter value for attribute Process Name in the Process Name CONTAINS field.
- Post-NAT Source IP: Enter value for attribute Post-NAT Source IP in the Post-NAT Source IP field.
- Raw Event Log: Enter value for attribute Raw Event Log in the Raw Event Log CONTAINS field.
- Relay IP: Enter value for attribute Relay IP in the Relay IP IN field.
- Reporting IP: Enter value for attribute Reporting IP in the Reporting IP IN field.
- Source IP: Enter value for attribute Source IP in the Source IP IN field.
- Source Port: Enter value for attribute Source Port in the Source Port IN field.
- Source MAC: Enter value for attribute Source MAC in the Source MAC CONTAINS field.
|
| Event Fields To Show In Response |
Specify the fields to display in the report summary for the report to run on the Fortinet FortiSIEM server. |
| Time Range |
(Optional) Specify the time duration to search for reports to run on the Fortinet FortiSIEM server. By default, this is set as Relative Time. You can select from following options:
- Relative Time: Specify values in the following fields:
- Relative Time: Select the unit of the duration from the following options:
- Last: Select the quantity of the units for duration selected. For example if the unit selected was hours, select
2 to set the relative time duration as 2 hours.
- Absolute Time: Specify values in the following fields:
- From: (Optional) Specify the start datetime for which to get events on the Fortinet FortiSIEM server.
- To: (Optional) Specify the end datetime for which to get events on the Fortinet FortiSIEM server.
|
| Number Of Items To Return In Response |
(Optional) Specify the maximum number of items for this operation to return in the response. By default, the page size is set to 50 items. |
| Offset |
(Optional) Specify the index of the first item to be returned by this operation. This parameter is useful if to get a subset of records say, incidents starting from the 10th incident. By default, this is set as 0. |
Output
The output contains the following populated JSON schema:
{
"@start": "",
"events": [
{
"id": "",
"nid": "",
"index": "",
"custId": "",
"dataStr": "",
"eventType": "",
"attributes": {
"type": "",
"uuid": "",
"vdom": "",
"count": "",
"fwRule": "",
"osType": "",
"eventId": "",
"ipProto": "",
"srcName": "",
"subtype": "",
"customer": "",
"destName": "",
"fwAction": "",
"logLevel": "",
"memberID": "",
"totFlows": "",
"trandisp": "",
"eventName": "",
"eventType": "",
"reptModel": "",
"sessionId": "",
"srcIpAddr": "",
"srcIpPort": "",
"totPkts64": "",
"destIpAddr": "",
"destIpPort": "",
"deviceTime": "",
"parserName": "",
"phRecvTime": "",
"recvPkts64": "",
"reptVendor": "",
"sentPkts64": "",
"srcMACAddr": "",
"totBytes64": "",
"collectorId": "",
"eventAction": "",
"rawEventMsg": "",
"recvBytes64": "",
"reptDevName": "",
"sentBytes64": "",
"serviceName": "",
"srcIntfName": "",
"timeSkewSec": "",
"appGroupName": "",
"destIntfName": "",
"durationMSec": "",
"eventParsedOk": "",
"eventSeverity": "",
"reptDevIpAddr": "",
"profileDetails": "",
"relayDevIpAddr": "",
"phEventCategory": "",
"eventRuleTrigger": "",
"eventSeverityCat": "",
"masterSrcMACAddr": "",
"postNATSrcIpAddr": "",
"postNATSrcIpPort": "",
"extEventRecvProto": ""
},
"receiveTime": ""
}
],
"@queryId": "",
"@errorCode": "",
"@totalCount": ""
}
operation: Get Event Details
Input parameters
| Parameter |
Description |
| Event ID |
Specify the ID of the event to get its details from Fortinet FortiSIEM server. |
| From |
(Optional) Specify the start datetime of the event to retrieve from Fortinet FortiSIEM server. |
| To |
(Optional) Specify the end datetime of the event to retrieve from Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"nid": "",
"index": "",
"custId": "",
"dataStr": "",
"eventType": "",
"attributes": {
"uuid": "",
"vdom": "",
"count": "",
"fwRule": "",
"eventId": "",
"ipProto": "",
"srcName": "",
"subtype": "",
"customer": "",
"destName": "",
"fwAction": "",
"logLevel": "",
"memberID": "",
"totFlows": "",
"trandisp": "",
"eventName": "",
"eventType": "",
"reptModel": "",
"sessionId": "",
"srcIpAddr": "",
"srcIpPort": "",
"totPkts64": "",
"destGeoOrg": "",
"destIpAddr": "",
"destIpPort": "",
"deviceTime": "",
"parserName": "",
"phRecvTime": "",
"recvPkts64": "",
"reptVendor": "",
"sentPkts64": "",
"totBytes64": "",
"collectorId": "",
"destGeoCity": "",
"eventAction": "",
"rawEventMsg": "",
"hostIpAddr": "",
"hostName": "",
"recvBytes64": "",
"reptDevName": "",
"sentBytes64": "",
"serviceName": "",
"srcIntfName": "",
"timeSkewSec": "",
"appGroupName": "",
"destGeoState": "",
"destIntfName": "",
"durationMSec": "",
"eventParsedOk": "",
"eventSeverity": "",
"reptDevIpAddr": "",
"destGeoCountry": "",
"profileDetails": "",
"relayDevIpAddr": "",
"destGeoLatitude": "",
"phEventCategory": "",
"destGeoLongitude": "",
"eventRuleTrigger": "",
"eventSeverityCat": "",
"postNATSrcIpAddr": "",
"postNATSrcIpPort": "",
"extEventRecvProto": "",
"destGeoCountryCodeStr": ""
},
"receiveTime": ""
}
operation: Get All Devices
Input parameters
| Parameter |
Description |
| Organization |
Specify the name of the organization for which to filter the devices from the Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"devices": {
"device": [
{
"name": "",
"accessIp": "",
"approved": "",
"creationMethod": "",
"discoverMethod": "",
"discoverTime": "",
"naturalId": "",
"unmanaged": "",
"updateMethod": "",
"version": "",
"deviceType": {
"accessProtocols": "",
"jobWeight": "",
"model": "",
"vendor": "",
"version": ""
},
"organization": {
"@id": "",
"@name": ""
}
}
]
}
}
operation: Get All Devices For Specified IP Address Range
Input parameters
| Parameter |
Description |
| Include IP SET |
Specify the value of IP addresses based on which for retrieve device information from the Fortinet FortiSIEM server. You must provide the value of this field as a range or in CSV format. For example, 192.168.20.1-192.168.20.100 or 192.168.1.10,192.168.1.11. |
| Exclude IP SET |
(Optional) Specify the value of the range of IP addresses to exclude from this search operation. You must provide the value of this field as a range or in CSV format. For example, 192.168.20.1-192.168.20.100 or 192.168.1.10,192.168.1.11. |
| Organization |
Specify the name of the organization for which to retrieve details of the device from the Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"devices": {
"device": [
{
"name": "",
"accessIp": "",
"approved": "",
"creationMethod": "",
"discoverMethod": "",
"discoverTime": "",
"naturalId": "",
"unmanaged": "",
"updateMethod": "",
"version": "",
"deviceType": {
"accessProtocols": "",
"jobWeight": "",
"model": "",
"vendor": "",
"version": ""
},
"organization": {
"@id": "",
"@name": ""
}
}
]
}
}
operation: Get Device Information
Input parameters
| Parameter |
Description |
| Device IP |
Specify the IP address of the device for which to retrieve details from the Fortinet FortiSIEM server. |
| Organization |
Specify the name of the organization for which to retrieve details of the device from the Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"device": {
"luns": "",
"name": "",
"status": "",
"version": "",
"accessIp": "",
"approved": "",
"storages": "",
"naturalId": "",
"unmanaged": "",
"components": "",
"deviceType": {
"model": "",
"vendor": "",
"version": "",
"category": "",
"jobWeight": ""
},
"interfaces": {
"networkinterface": {
"adminStatus": "",
"description": "",
"inSpeed": "",
"ipv4Addr": "",
"ipv4IsVirtual": "",
"ipv4Mask": "",
"isCritical": "",
"isMonitor": "",
"isTrunk": "",
"isWAN": "",
"macAddr": "",
"macIsVirtual": "",
"name": "",
"operStatus": "",
"outSpeed": "",
"snmpIndex": "",
"speed": "",
"type": ""
}
},
"processors": "",
"raidGroups": "",
"applications": "",
"discoverTime": "",
"organization": {
"@id": "",
"@name": ""
},
"updateMethod": "",
"ipToHostNames": "",
"storageGroups": "",
"creationMethod": "",
"description": "",
"discoverMethod": "",
"winMachineGuid": "",
"eventParserList": "",
"systemUpTime": "",
"softwarePatches": "",
"softwareServices": "",
"sanControllerPorts": ""
}
}
operation: List Monitored Devices and Attributes
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"monitoredDevices": {
"perfMonDevices": {
"device": {
"accessIp": "",
"deviceName": "",
"deviceType": "",
"monitors": {
"monitor": [
{
"category": "",
"method": ""
}
]
},
"organization": ""
}
},
"eventPullingDevices": ""
}
}
operation: List Monitored Organizations
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"@id": "",
"name": "",
"@xmlId": "",
"@custId": "",
"@ownerId": "",
"disabled": "",
"domainId": "",
"initialized": "",
"@creationTime": "",
"collectors": {
"collector": []
},
"@lastModified": "",
"@entityVersion": "",
"custProperties": ""
}
operation: Get Organization Details
Input parameters
| Parameter |
Description |
| Organization ID |
Specify the ID of the organization for which to retrieve details from Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"@entityVersion": "",
"@creationTime": "",
"@custId": "",
"@id": "",
"@lastModified": "",
"custProperties": "",
"collectors": {
"collector": []
},
"@ownerId": "",
"@xmlId": "",
"disabled": "",
"domainId": "",
"initialized": "",
"name": ""
}
operation: Run Advanced Search Query
Input parameters
| Parameter |
Description |
| Advanced Search Query |
Specify the conditions based on which to process the search results for the report to run on the Fortinet FortiSIEM server. For example: (incidentDetail CONTAIN "jobName" AND phEventCategory = 1) AND (phCustId IN (1)) |
| Event Fields To Show In Response |
Specify the comma-separated list of event fields to display in the report summary for the report to run on the Fortinet FortiSIEM server. |
| Group By |
(Optional) Specify the attribute based on which to group the search results for the report to run on the Fortinet FortiSIEM server. For example: reptDevIpAddr |
| Order By |
(Optional) Specify the field using which to sort the search results for the report to run on the Fortinet FortiSIEM server. You can also specify the sort direction of the specified field. For example, phRecvTime DESC |
| Time Range |
(Optional) Specify the time duration to search for reports to run on the Fortinet FortiSIEM server. By default, this is set as Relative Time. You can select from following options:
- Relative Time: Specify values in the following fields:
- Relative Time: Select the unit of the duration from the following options:
- Last: Select the quantity of the units for duration selected. For example if the unit selected was hours, select
2 to set the relative time duration as 2 hours.
- Absolute Time: Specify values in the following fields:
- From: (Optional) Specify the start datetime for which to get events on the Fortinet FortiSIEM server.
- To: (Optional) Specify the end datetime for which to get events on the Fortinet FortiSIEM server.
|
| Number Of Items To Return In Response |
(Optional) Specify the maximum number of items for this operation to return in the response. By default, the page size is set to 50 items. |
| Offset |
(Optional) Specify the index of the first item to be returned by this operation. This parameter is useful if to get a subset of records say, incidents starting from the 10th incident. By default, this is set as 0. |
Output
No output schema is available at this time.
operation: Get Event Attributes
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"FQDN": "",
"Type": "",
"UUID": "",
"User": "",
"VM IP": "",
"Domain": "",
"Host IP": "",
"ICMP Id": "",
"IP Port": "",
"Message": "",
"User Id": "",
"Agent ID": "",
"Checksum": "",
"Computer": "",
"Duration": "",
"Event ID": "",
"Host MAC": "",
"URI Stem": "",
"Disk Name": "",
"File Name": "",
"File Path": "",
"Host City": "",
"Host Name": "",
"Host VLAN": "",
"ICMP Code": "",
"ICMP Type": "",
"Rule Name": "",
"Server IP": "",
"TCP flags": "",
"URI Query": "",
"WLAN SSID": "",
"Event Name": "",
"Event Type": "",
"File Owner": "",
"Host Model": "",
"Host State": "",
"IP Version": "",
"Image File": "",
"Sent Bytes": "",
"Source IP ": "",
"Source MAC": "",
"Source TOS": "",
"User Group": "",
"VPN Status": "",
"Attack Name": "",
"Device Port": "",
"Device Time": "",
"Employee ID": "",
"Host Vendor": "",
"IP Protocol": "",
"Incident ID": "",
"Mail Sender": "",
"New Host IP": "",
"Object Name": "",
"Relaying IP": "",
"Server Name": "",
"Source City": "",
"Source VLAN": "",
"Target User": "",
"Total Bytes": "",
"Collector ID": "",
"Collector IP": "",
"DHCP Gateway": "",
"Event Action": ": ",
"Event Source": "",
"Host Country": "",
"Mail Subject": "",
"Malware Name": "",
"Malware Type": "",
"Process Name": "",
"Reporting IP": ": ",
"Sent Packets": "",
"Source State": "",
"VM Host Name": "",
"Win Logon Id": "",
"ARP Source IP": "",
"Connection Id": "",
"DNS Server IP": "",
"IPS Sensor Id": "",
"Mail Receiver": "",
"Object Handle": "",
"Raw Event Log": "",
"Software Name": "",
"Target Domain": "",
"Total Packets": "",
"VPN Conn Type": "",
"WLAN Radio Id": "",
"ARP Source MAC": "",
"Account Number": "",
"Auth Server IP": "",
"Collector Name": "",
"DNS Query Type": "",
"Destination IP": "",
"Event Severity": "",
"Hash Algorithm": "",
"Incident Title": "",
"Malware Action": "",
"OS Object Type": "",
"Received Bytes": "",
"Recv Auth Fail": "",
"Reporting City": "",
"Sent TCP flags": "",
"Snort Event ID": "",
"Source Country": "",
"TCP Connection": "",
"UDP Connection": "",
"Win Logon Type": "",
"DHCP Server MAC": "",
"Destination MAC": "",
"Destination TOS": "",
"Firewall Action": "",
"HTTP User Agent": "",
"Host Virtual IP": "",
"ICMP Connection": "",
"Incident Source": "",
"Incident Target": "",
"Organization ID": "",
"Relaying Device": "",
"Reporting Model": "",
"Reporting State": "",
"Target Computer": "",
"Target Host MAC": "",
"VPN Tunnel Name": "",
"WLAN Channel Id": "",
"WLAN User count": "",
"Application Name": "",
"Application Port": "",
"Auth Server Name": "",
"Destination City": "",
"Destination VLAN": "",
"Event Occur Time": "",
"Firewall Session": "",
"Operating System": "",
"Received Packets": "",
"Reporting Device": "",
"Reporting Vendor": "",
"Source Host Name": "",
"DHCP Request Type": "",
"Destination State": "",
"Event Description": "",
"Host Organization": "",
"Incident Category": "",
"Informational URL": "",
"Organization Name": "",
"Reporting Country": "",
"Target User Group": "",
"ARP Destination IP": "",
"Event Parse Status": "",
"Event Receive Time": "",
"IP Type of Service": "",
"Object Access Type": "",
"Post-NAT Source IP": "",
"Previous Source IP": "",
"Recv Packet Errors": "",
"Sent Packet Errors": "",
"Source Device Port": "",
"Vulnerability Name": "",
"Vulnerability Type": "",
"ARP Destination MAC": "",
"Destination Country": "",
"Host Interface Name": "",
"Recv Interface Util": "",
"Sent Interface Util": "",
"Source Organization": "",
"Source TCP/UDP Port": "",
"Vulnerability Score": "",
"Win Logon Fail Code": "",
"False Positive Check": "",
"IDS Database Version": "",
"Post-NAT Source Port": "",
"Source Firewall Zone": "",
"Vulnerability CVE Id": "",
"Business Service Name": "",
"Destination Host Name": "",
"IPS Event Risk Rating": "",
"Incident Reporting IP": "",
"Network Access Device": "",
"Recv Packet Error Pct": "",
"Sent Packet Error Pct": "",
"Source Interface Name": "",
"System Event Category": "",
"Pre-NAT Destination IP": "",
"Reporting Organization": "",
"Virus Database Version": "",
"Destination Device Port": "",
"Event Severity Category": "",
"IPS Event Threat Rating": ": ",
"Post-NAT Destination IP": "",
"Destination Organization": "",
"Destination Service Name": "",
"Destination TCP/UDP Port": "",
"Network Access Device IP": "",
"Operating System Version": "",
"Pre-NAT Destination Port": "",
"Destination Firewall Zone": "",
"Palo Alto Firewall Action": "",
"Destination Interface Name": "",
"Extension Database Version": "",
"Network Access Device Port": "",
"Source Interface SNMP Index": "",
"Firewall Session Utilization": "",
"Post-NAT Destination Ip Port": "",
"Previous Source TCP/UDP Port": "",
"Command and Control Host Name": "",
"Wireless Attack Signature Name": "",
"Incident Trigger Attribute List": "",
"Source Autonomous System Number": "",
"Command and Control TCP/UDP Port": "",
"Destination Interface SNMP Index": "",
"Destination Autonomous System Number": "",
"Anti-Virus Extension Database Version": ""
}
operation: Get Events Data By Query ID
Input parameters
| Parameter |
Description |
| Query ID |
Specify the ID of the executed query based on which to retrieve data of events from the Fortinet FortiSIEM server. You can retrieve the Query ID from the output of actions such as List Incidents, Search Query, etc. |
| Number Of Items To Return In Response |
(Optional) Specify the maximum number of items for this operation to return in the response. By default, the page size is set to 50 items. |
| Offset |
(Optional) Specify the index of the first item to be returned by this operation. This parameter is useful if to get a subset of records say, incidents starting from the 10th incident. By default, this is set as 0. |
Output
The output contains a non-dictionary value.
operation: Create Watch List
Input parameters
| Parameter |
Description |
| Watch List JSON Object |
Specify the JSON Object of a watch list with a watch list entry to create in the FortiSIEM database. For example:
{
"description":"Servers,networkorstoragedevices",
"displayName":"ResourceIssuesTest4",
"type":"DyWatchList",
"isCaseSensitive":false,
"dataCreationType":"USER",
"topGroup":false,
"valuePattern":null,
"valueType":"STRING",
"ageOut":"1d",
"custId":1,
"entries":[
{
"inclusive":true,
"entryValue":"PVVol_A001_A000356_5new",
"ageOut":"1d",
"count":1,
"custId":1,
"firstSeen":1612901760000,
"lastSeen":1612901760000,
"triggeringRules":"DatastoreSpaceWarning",
"dataCreationType":"USER"
}
]
}
NOTE: displayName and type are required fields. |
Output
The output contains the following populated JSON schema:
{
"response": [
{
"isCaseSensitive": "",
"naturalId": "",
"displayName": "",
"description": "",
"valuePattern": "",
"ageOut": "",
"topGroup": "",
"entries": [
{
"naturalId": "",
"firstSeen": "",
"count": "",
"triggeringRules": "",
"description": "",
"entryValue": "",
"expiredTime": "",
"ageOut": "",
"lastSeen": "",
"dataCreationType": "",
"custId": "",
"id": "",
"state": ""
}
],
"dataCreationType": "",
"valueType": "",
"custId": "",
"name": "",
"id": ""
}
],
"status": ""
}
operation: Get Watch Lists
Input parameters
| Parameter |
Description |
| Get Watch List Data By |
Select one of the following options to get watch list data based on the selection:
- Get Watch Lists: Select this options to get all watch lists.
- By Watch List ID: Specify the watch list ID of a specific watch list in the Watch List ID field.
- By Watch List Entry Value: Specify the entry value of watch list entry in the Entry Value field.
- By Watch List Entry ID: Specify the entry value of watch list entry ID in the Watch List Entry ID field.
|
Output
The output contains the following populated JSON schema:
If you choose Get All Watch Lists or By Watch List ID as Get Watch List Data By, then the output contains the following populated JSON schema:
{
"response": [
{
"isCaseSensitive": "",
"naturalId": "",
"displayName": "",
"description": "",
"valuePattern": "",
"ageOut": "",
"topGroup": "",
"entries": [
{
"naturalId": "",
"firstSeen": "",
"count": "",
"triggeringRules": "",
"description": "",
"entryValue": "",
"expiredTime": "",
"ageOut": "",
"lastSeen": "",
"dataCreationType": "",
"custId": "",
"id": "",
"state": ""
}
],
"dataCreationType": "",
"valueType": "",
"custId": "",
"name": "",
"id": ""
}
],
"status": ""
}
Output schema when you choose Get Watch List Data By as By Watch List Entry ID:
{
"response": {
"isCaseSensitive": "",
"naturalId": "",
"displayName": "",
"description": "",
"valuePattern": "",
"ageOut": "",
"topGroup": "",
"entries": [
{
"naturalId": "",
"firstSeen": "",
"count": "",
"triggeringRules": "",
"description": "",
"entryValue": "",
"expiredTime": "",
"ageOut": "",
"lastSeen": "",
"dataCreationType": "",
"custId": "",
"id": "",
"state": ""
}
],
"dataCreationType": "",
"valueType": "",
"custId": "",
"name": "",
"id": ""
},
"status": ""
}
This is the default output schema:
{
"response": [
{
"isCaseSensitive": "",
"naturalId": "",
"displayName": "",
"description": "",
"valuePattern": "",
"ageOut": "",
"topGroup": "",
"entries": [
{
"naturalId": "",
"firstSeen": "",
"count": "",
"triggeringRules": "",
"description": "",
"entryValue": "",
"expiredTime": "",
"ageOut": "",
"lastSeen": "",
"dataCreationType": "",
"custId": "",
"id": "",
"state": ""
}
],
"dataCreationType": "",
"valueType": "",
"custId": "",
"name": "",
"id": ""
}
],
"status": ""
}
operation: Get Watch List Entries Count
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"status": "",
"response": {
"entry_count": ""
}
}
operation: Get Watch List Entry
Input parameters
| Parameter |
Description |
| Watch List Entry ID |
Specify the watch list entry ID to retrieve a specific watch list entry from the Fortinet FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"status": "",
"response": {
"id": "",
"count": "",
"state": "",
"ageOut": "",
"custId": "",
"lastSeen": "",
"firstSeen": "",
"naturalId": "",
"entryValue": "",
"description": "",
"expiredTime": "",
"triggeringRules": "",
"dataCreationType": ""
}
}
operation: Add Watch List Entries to Watch List
Input parameters
| Parameter |
Description |
| Watch List ID |
Specify the ID of the watch list to which to add watch list entries. |
| Other parameters |
Specify the JSON Array of watch list entry objects to add to specific watch list groups. For example
{
"inclusive": false,
"count": 10,
"custId": 1,
"triggeringRules": "Datastore Space Warning",
"entryValue": "PVVol_A001_A000356_POWER2",
"ageOut": "1d",
"lastSeen": 1613601369215,
"firstSeen": 1613601369215,
"disableAgeout": false,
"dataCreationType": "USER"
}
|
Output
The output contains the following populated JSON schema:
{
"response": "",
"status": ""
}
operation: Update Watch List Entry
Input parameters
| Parameter |
Description |
| Watch List Entry ID |
Specify the ID of the watch list entry to update in the FortiSIEM database. |
| Count |
(Optional) Specify the occurrence count of the watch list entry to update in the FortiSIEM database. |
| Last Seen Time |
(Optional) Specify the value of the last seen time, i.e., the Unix timestamp, of the specific watch list to update in the FortiSIEM database. |
| State |
Select specific entry to Active/Inactive state. |
| Other Parameters |
JSON Object of a watch list to update in the FortiSIEM database. For example
{
"lastSeen": 1612901760002,
"dataCreationType": "USER",
"firstSeen": 1612901760001,
"count": 100,
"custId": 1,
"triggeringRules": "Datastore Space Warning",
"description": "Testing again",
"id": 889400,
"inclusive": true,
"entryValue": "PVVol_A001_A000356_POWER23",
"expiredTime": 1612988160001,
"ageOut": "2d"
}
|
Output
The output contains the following populated JSON schema:
{
"response": {
"naturalId": "",
"firstSeen": "",
"count": "",
"triggeringRules": "",
"description": "",
"entryValue": "",
"expiredTime": "",
"ageOut": "",
"lastSeen": "",
"dataCreationType": "",
"custId": "",
"id": "",
"state": ""
},
"status": ""
}
operation: Delete Watch List Entry
Input parameters
| Parameter |
Description |
| Watch List Entry IDs |
Specify the IDs of the watch list entries, in the CSV or list format, to delete from the FortiSIEM database. For example,??[500000, 500001] |
Output
The output contains the following populated JSON schema:
{
"response": "",
"status": ""
}
operation: Delete Watch List
Input parameters
| Parameter |
Description |
| Watch List IDs |
Specify the IDs of the watch lists, in the CSV or list format, to delete from the FortiSIEM database. For example, [500000, 500001] |
Output
The output contains the following populated JSON schema:
{
"response": "",
"status": ""
}
operation: Create Lookup Table
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the lookup table to create in FortiSIEM.
NOTE:The table name must contain only alphabets and numbers |
| Column List |
Specify the list of column definitions for the lookup table to create in FortiSIEM. For each column you must specify the following three values:
key: Specify a key indicating whether the column is a primary columnname: Specify the name of the columntype: Specify the type of the column, for example, STRING, LONG, or DOUBLE.
For example,
[
{
"key": true,
"name": "url",
"type": "STRING"
},
{
"key": false,
"name": "wfCategoryID",
"type": "LONG"
}
]
|
| Description |
(Optional) Specify the description of the lookup table to create in FortiSIEM. |
| Organization Name |
(Optional) Specify the organization name to be assigned to the lookup table to create in FortiSIEM. By default, this is set to the organization of the current user. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"name": "",
"columnList": [
{
"key": "",
"name": "",
"type": ""
}
],
"description": "",
"lastUpdated": "",
"organizationName": ""
}
operation: Get All Lookup Table
Input parameters
| Parameter |
Description |
| Offset |
(Optional) Specify the index of the first item to be returned by this operation. This parameter is useful if to get a subset of records, say lookup table definitions starting from the 10th position. By default, this is set as 0. |
| Number Of Items To Return |
(Optional) Specify the maximum number of items that this operation to return in the response. By default, the page size is set to 25 items, and the maximum is set at 1000. |
Output
The output contains the following populated JSON schema:
{
"data": [
{
"id": "",
"name": "",
"columnList": [
{
"key": "",
"name": "",
"type": ""
}
],
"description": "",
"lastUpdated": "",
"organizationName": ""
}
],
"size": "",
"start": "",
"total": ""
}
operation: Delete Lookup Table
Input parameters
| Parameter |
Description |
| Lookup Table ID |
Specify the unique identifier representing the lookup Table whose definitions to delete from the FortiSIEM server. |
Output
The output contains the following populated JSON schema:
{
"status": "",
"message": ""
}
operation: Import Lookup Table Data
Input parameters
| Parameter |
Description |
| File IRI/Attachment ID |
Select the method using which to import CSV file present in FortiSOAR to the FortiSIEM lookup table. You can choose from following options:
- Attachment ID: Specify the Attachment ID of the CSV file to import into the specified lookup table in FortiSIEM.
- File IRI: Specify the CSV file to import into the specified lookup table in FortiSIEM.
|
| Lookup Table ID |
Specify the unique identifier representing the lookup table in FortiSIEM into which to import the CSV file in FortiSIEM. |
| Mapping |
Specify the configuration that matches the position of columns in the CSV file to columns in the specified lookup table. The format of the mapping is as follows: {"":,"":} For example,
{
"url": 1,
"wfCategoryID": 2
}
|
| File Separator |
Specify the file separator for the specified CSV file. By default, this is set as the comma character(,) |
| File Quote Char |
Specify the file quote character for the specified CSV file. By default, this is set as the double quotation character("). |
| Skip Header |
Select this option to ignore the header of the specified CSV file. |
| Update Type |
Select the method of updating the data in FortiSIEM. You can choose between Overwrite (default) or Append. |
Output
The output contains the following populated JSON schema:
{
"taskId": ""
}
operation: Check Import Task Status
Input parameters
| Parameter |
Description |
| Lookup Table ID |
Specify the unique identifier representing the lookup table in FortiSIEM for which to check the import task status. |
| Task ID |
Specify the task ID of the importing data to the specified lookup table. You can retrieve the task ID from the response of the Import Lookup Table Data action. |
Output
The output contains the following populated JSON schema:
{
"actionResult": "",
"id": "",
"progress": "",
"status": ""
}
operation: Get Lookup Table Data
Input parameters
| Parameter |
Description |
| Lookup Table ID |
Specify the unique identifier representing the lookup table for which to retrieve items from FortiSIEM. |
| Start |
(Optional) Specify the index of the first item to be returned by this operation. This parameter is useful if to get a subset of records, say lookup table items starting from the 10th position. By default, this is set as 0. |
| Number Of Items To Return |
(Optional) Specify the maximum number of items that this operation to return in the response. By default, the page size is set to 25 items, and the maximum is set at 1000. |
| Search Text |
(Optional) Specify the Search text using which to filter items of the specified lookup table in FortiSIEM. |
| Sort By |
(Optional) Specify the lookup table columns using which to sort the search results retrieved from FortiSIEM. You can also specify the sort direction of the specified lookup table columns, i.e, descending (DESC) or ascending (ASC). |
Output
The output contains the following populated JSON schema:
{
"data": [],
"size": "",
"start": "",
"total": ""
}
operation: Update Lookup Table Data
Input parameters
| Parameter |
Description |
| Lookup Table ID |
Specify the unique identifier representing the lookup table whose items to update in FortiSIEM. |
| Key |
Specify the primary key of the item column and its value to update in the specified lookup table. The format is keyColumn_1:value For example, key={"url":"http://example.com"} |
| Column Data |
Specify the dictionary of column values to update in the specified lookup table. For example,
{
"url": "www.test.com",
"wfCategoryID": 30,
"score": 0.50119
}
|
Output
The output contains the following populated JSON schema:
{
"response": "",
"message": ""
}
operation: Delete Lookup Table Data
Input parameters
| Parameter |
Description |
| Lookup Table ID |
Specify the unique identifier representing the lookup table whose items to delete in FortiSIEM. |
| Primary Keys |
Specify the list of primary keys of the item columns and their values to delete from the specified lookup table. The format is:
[
{
"keyColumn_1": "value",
"keyColumn_2": "value"
}
]
|
Output
The output contains the following populated JSON schema:
{
"status": "",
"message": ""
}
operation: Get All Resource Lists
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"id": "",
"pid": "",
"version": "",
"displayName": "",
"description": "",
"groupType": {
"name": "",
"displayName": ""
},
"naturalId": "",
"children": [
{
"id": "",
"pid": "",
"version": "",
"displayName": "",
"description": "",
"groupType": {
"name": "",
"displayName": ""
},
"naturalId": "",
"children": [],
"retiredChildren": [],
"itemIds": "",
"systemGroup": "",
"custId": "",
"groupConfig": "",
"valueType": "",
"dataCreationType": "",
"fullPathName": "",
"valuePattern": "",
"topGroup": "",
"displayOrder": "",
"dashboardStatus": "",
"myDashboard": "",
"myWidgetDashboard": "",
"myBizServiceDashboard": "",
"mySummaryDashboard": "",
"myLinkUsageDashboard": "",
"superGlobal": "",
"rootOfMyDashboard": "",
"myIdentityLocationDashboard": "",
"myPCIDashboard": ""
}
],
"retiredChildren": [],
"itemIds": "",
"systemGroup": "",
"custId": "",
"groupConfig": "",
"valueType": "",
"dataCreationType": "",
"fullPathName": "",
"valuePattern": "",
"topGroup": "",
"displayOrder": "",
"dashboardStatus": "",
"myDashboard": "",
"myWidgetDashboard": "",
"myBizServiceDashboard": "",
"mySummaryDashboard": "",
"myLinkUsageDashboard": "",
"superGlobal": "",
"rootOfMyDashboard": "",
"myIdentityLocationDashboard": "",
"myPCIDashboard": ""
}
operation: Get Resource List Entries
Input parameters
| Parameter |
Description |
| Resource Group ID |
Specify the ID of the resource group from which to retrieve the specific element types. You can use the 'Get All Resource Lists' operation to find the IDs of the resource groups. |
| Resource Type |
Select the type of resource (element) to retrieve from the specified resource group in the Fortinet FortiSIEM server. You can choose from the following options: Malware IP, Malware Domains, Malware Urls, Malware Hash, or Malware Processes. |
| Offset |
(Optional) Specify the index of the first item to be returned by this operation. This parameter is useful if to get a subset of records, say incidents starting from the 10th incident. By default, this is set as 0. |
| Number Of Items To Return In Response |
(Optional) Specify the maximum number of entries for this operation to return in the response. By default, the page size is set to 100 entries. |
Output
The output contains the following populated JSON schema:
{
"headerData": {
"objectTypeName": "",
"columnNames": [],
"columnTypes": [],
"methodNames": [],
"columnWidths": [],
"columnActions": [],
"keys": [],
"attrKeys": []
},
"lightValueObjects": [
{
"objectId": "",
"custId": "",
"parentId": "",
"collectorId": "",
"data": [],
"extData": "",
"naturalId": "",
"aoSys": ""
}
],
"errCode": "",
"errObj": "",
"dataType": "",
"totalCount": ""
}
operation: Add Entries To Resource List
Input parameters
| Parameter |
Description |
| Resource Group ID |
Specify the ID of the resource group to which to add the specified element. You can use the 'Get All Resource Lists' operation to find the IDs of the resource groups. |
| Resource Data |
Specify the resource (element) data in a key-value pair to add to the specified resource group in the Fortinet FortiSIEM server. For example,
{
"singleIp": "3.3.3.3",
"enableDateFound": false,
"enableLastSeen": false,
"dateFound": null,
"lastSeen": null,
"name": "3.3.3.3",
"malwareType": "ip",
"severity": "low",
"highIp": "3.3.3.3",
"lowIp": "3.3.3.3",
"sysDefined": false,
"active": true,
"groupId": 15732450304
}
|
| Resource Type |
Select the type of resource (element) to add to the specified resource group in the Fortinet FortiSIEM server. You can choose from the following options:
- Malware IP
- Malware Domains
- Malware URLs
- Malware Hash
- Malware Processes
|
Output
The output contains the following populated JSON schema:
{
"lastModified": "",
"creationTime": "",
"custId": "",
"ownerId": "",
"collectorId": "",
"grpNid": "",
"id": "",
"naturalId": "",
"name": "",
"lowIp": "",
"highIp": "",
"description": "",
"sysDefined": "",
"active": "",
"malwareType": "",
"confidence": "",
"severity": "",
"country": "",
"asn": "",
"dateFound": "",
"lastSeen": "",
"org": "",
"groupId": "",
"naturalIdProperty": "",
"creationDate": "",
"lastModifiedDate": "",
"xmlId": "",
"systemEntity": ""
}
operation: Remove Entries From Resource List
Input parameters
| Parameter |
Description |
| Resource IDs |
Specify the IDs of the resources to delete from the Fortinet FortiSIEM server. |
| Resource Type |
Select the type of resource (element) to delete from the Fortinet FortiSIEM server. You can choose from the following options:
- Malware IP
- Malware Domains
- Malware URLs
- Malware Hash
- Malware Processes
|
Output
The output contains a non-dictionary value.
Included playbooks
The Sample - Fortinet FortiSIEM - 5.0.2 playbook collection comes bundled with the Fortinet FortiSIEM connector. These playbooks contain steps using which you can perform all supported actions. You can see bundled playbooks in the Automation > Playbooks section in FortiSOAR™ after importing the Fortinet FortiSIEM connector.
- > FortiSIEM > Fetch
- >> FortiSIEM > Fetch Associated events for Incident
- Device: Get All Devices
- Device: Get All Devices For Specified IP Address Range
- Device: Get Device Information
- Device: List Monitored Devices and Attributes
- Event: Get Event Attribute
- Event: Get Event Details
- Event: Get Events For Incident
- Event: Search Events
- FortiSIEM > Ingest
- Get Events Data By Query ID
- Incident: Clear Incident With Reason
- Incident: Comment Incident
- Incident: Get Incident Details
- Incident: List Incidents
- Incident: Update Incident
- Lookup Table: Check Import Task Status
- Lookup Table: Create Lookup Table
- Lookup Table: Delete Lookup Table
- Lookup Table: Delete Lookup Table Data
- Lookup Table: Get All Lookup Table
- Lookup Table: Get Lookup Table Data
- Lookup Table: Import Lookup Table Data
- Lookup Table: Update Lookup Table Data
- Organization: Get Organization Details
- Organization: List Monitored Organizations
- Resource List: Add Entries To Resource List
- Resource List: Get All Resource Lists
- Resource List: Get Resource List Entries
- Resource List: Remove Entries From Resource List
- Run Advanced Search Query
- Watch List: Add Watch List Entries To Watch List
- Watch List: Create Watch List
- Watch List: Delete Watch List
- Watch List: Delete Watch List Entry
- Watch List: Get Watch List Entries Count
- Watch List: Get Watch List Entry
- Watch List: Get Watch Lists
- Watch List: Update Watch List Entry
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection, since the sample playbook collection gets deleted during connector upgrade and delete.
Data Ingestion Support
Use the Data Ingestion Wizard to easily ingest data into FortiSOAR™ by pulling incidents from Fortinet FortiSIEM. Currently, Incidents in Fortinet FortiSIEM are mapped to Alerts in FortiSOAR™. For more information on the Data Ingestion Wizard, see the Connectors Guide in the FortiSOAR™ product documentation.
NOTE: To link MITRE techniques records to alerts that are being created using the Data Ingestion Wizard, use the MITRE ATT&CK Enrichment Framework and MITRE ATT&CK Threat Hunting Solution Packs.
Configure Data Ingestion
You can configure data ingestion using the Data Ingestion Wizard to seamlessly map the incoming FortiSIEM Incidents to FortiSOAR™Alerts.
IMPORTANT: You must reconfigure data ingestion if you have upgraded your FortiSIEM connector to version 5.0.0 (or later) from version 4.5.0. For more information, see the Reconfiguring FortiSIEM Data Ingestion section.
The Data Ingestion Wizard enables you to configure the scheduled pulling of data from FortiSIEM into FortiSOAR™. It also lets you pull some sample data from FortiSIEM using which you can define the mapping of data between FortiSIEM and FortiSOAR™. The mapping of common fields is generally already done by the Data Ingestion Wizard; users are mostly required to only map any custom fields that are added to the FortiSIEM incident.
-
To begin configuring data ingestion, click Configure Data Ingestion on the Fortinet FortiSIEM connector's Configurations page.
Click Let's Start by fetching some data, to open the Fetch Sample Data screen.
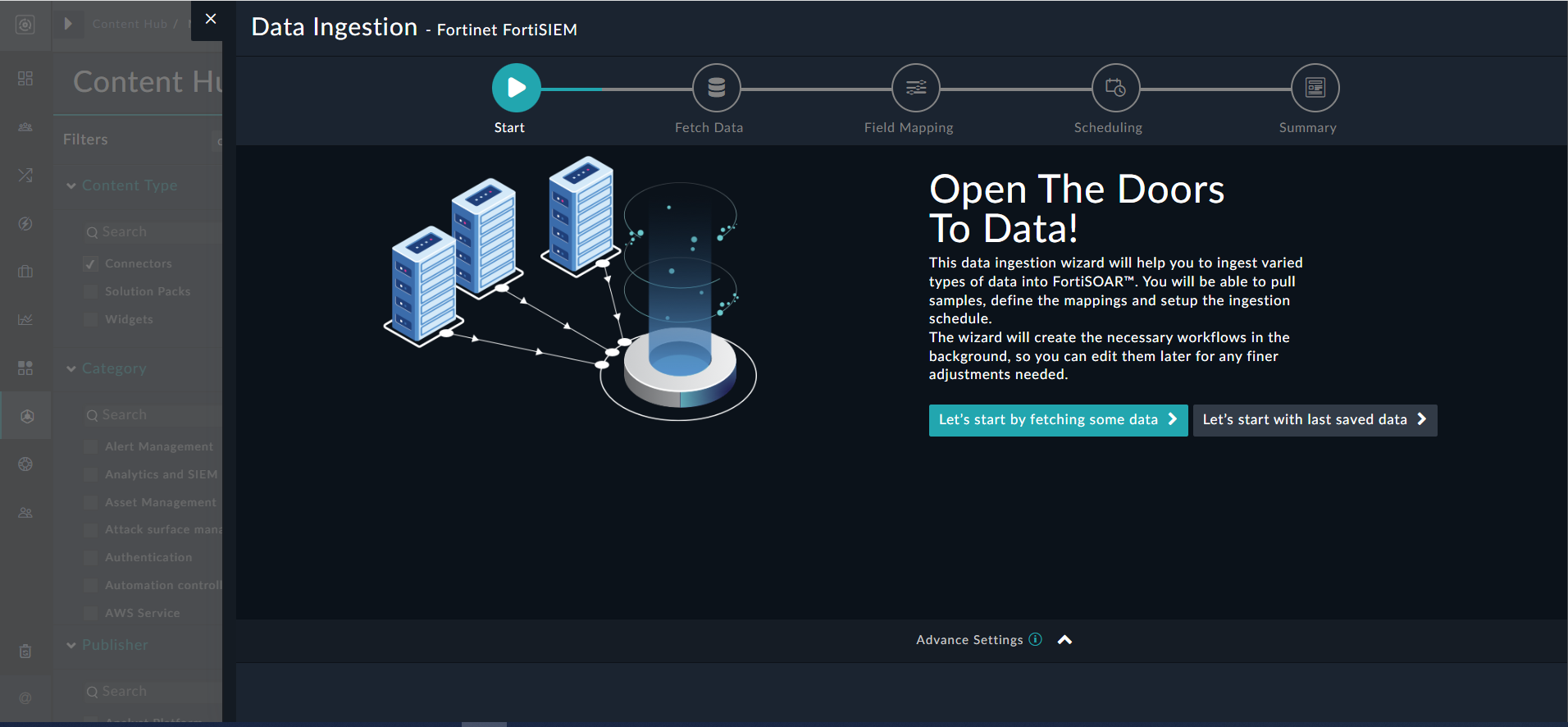
Sample data is required to create a field mapping between FortiSIEM data and FortiSOAR™. The sample data is pulled from connector actions or ingestion playbooks.
-
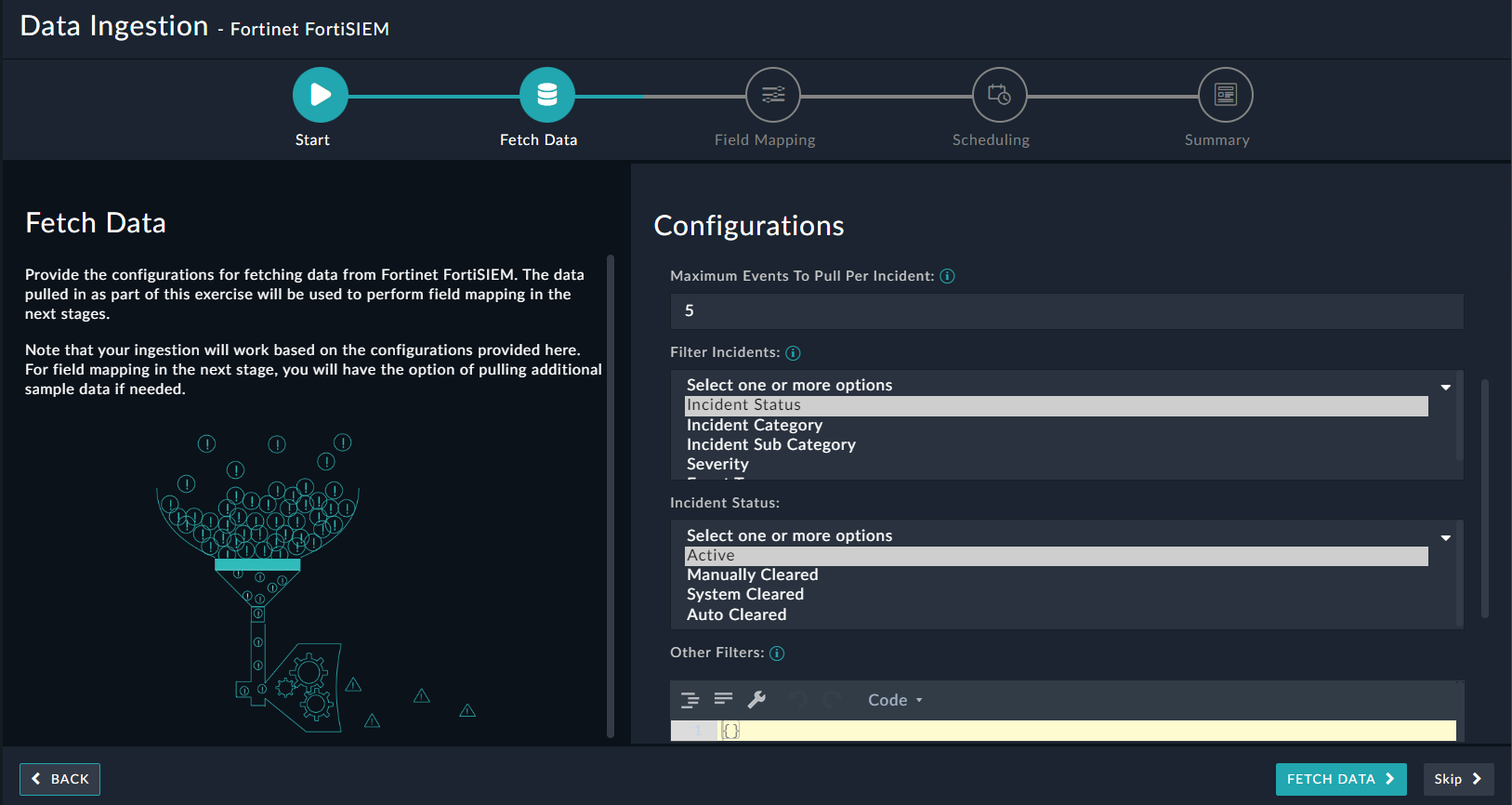
On the Fetch Data screen, provide the configurations required to fetch Fortinet FortiSIEM data.
Users can choose to pull data from Fortinet FortiSIEM by either specifying the last X minutes in which the incidents have been created or updated in FortiSIEM (By Updates in Last X Minutes) or by specifying an Incident ID (By Sample Incident ID). When fetching data based on By Updates in Last X Minutes, specify the number of minutes from when to retrieve incidents that were created or updated in Fortinet FortiSIEM, in the Pull Incidents Creates/Updates In Last X Minutes field. When fetching data based on By Sample Incident ID, specify the ID of the incident to retrieve from Fortinet FortiSIEM, in the Incident ID field. When fetching data based on By Updates in Last X Minutes , you can apply additional parameters such as:
- Maximum Incidents To Pull
- Maximum Events To Pull Per Incident
- Filter Incidents - based on Status, Category, Sub-category, Severity, and Event Type
- Incident Status - Filter incidents based on incident status
- Other Filters - Specify parameters using which to filter the incidents retrieved from the Fortinet FortiSIEM server. For example,
{
"status": [0],
"eventType": ["PH_RULE_SERVER_CPU_WARN"],
"incidentRptIp": ["10.7.12.156"]
}
The fetched data is used to create a mapping between the FortiSIEM data and FortiSOAR™ alerts. Once you have completed specifying the configurations, click the Fetch Data button.
When configuring data ingestion for MSSP systems, if Configure Multi-Tenant Mappings checkbox is checked, ensure that you map the organization name defined in FortiSIEM as a tenant in FortiSOAR™, in the Organization Mapping field:
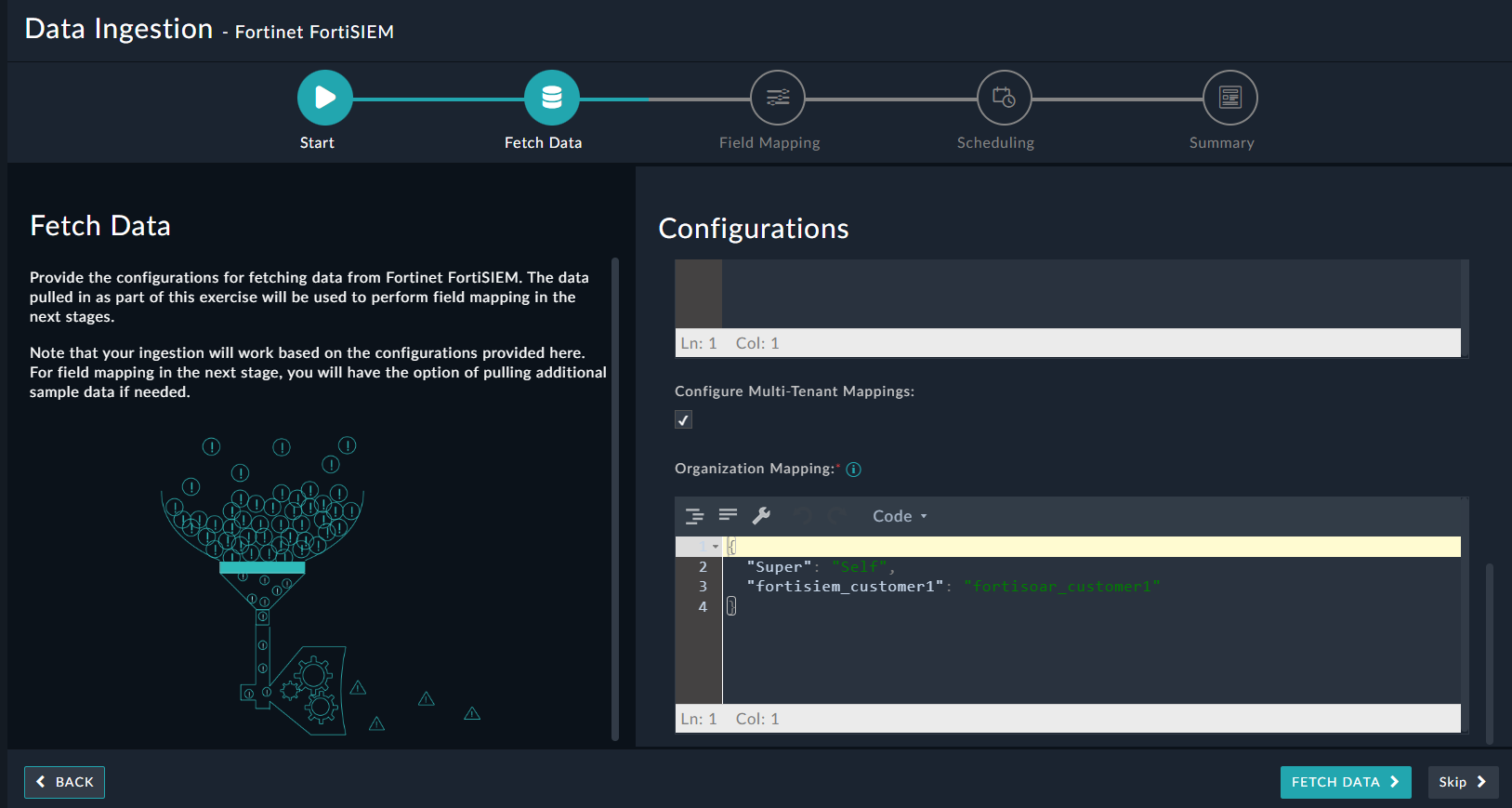
NOTE: If you have not mapped or wrongly mapped an organization, then the incident record will be created as a Self entry.
-
On the Field Mapping screen, map the fields of a FortiSIEM incident to the fields of an alert present in FortiSOAR™
To map a field, click the key in the sample data to add the Jinja value of the field. For example, to map the customer parameter of a FortiSIEM incident to the Username parameter of a FortiSOAR™ alert, click the Username field and then click the customer field to populate its keys:
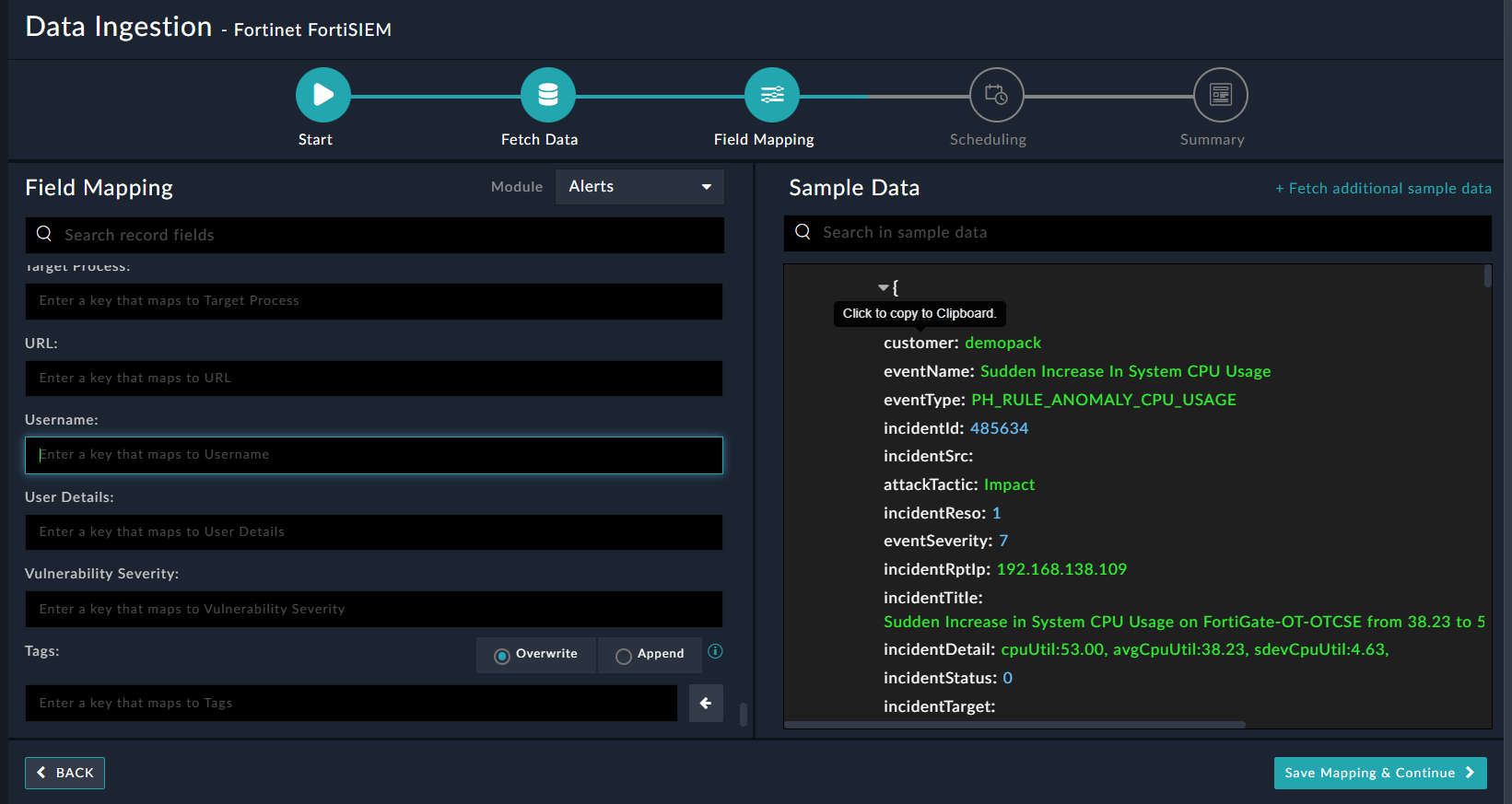
For more information on field mapping, see the Data Ingestion chapter in the FortiSOAR™ product documentation's Connectors Guide. Once you have completed the mapping of fields, click Save Mapping & Continue.
-
(Optional) Use the Scheduling screen to configure schedule-based ingestion, i.e., specify the polling frequency to FortiSIEM, so that the content gets pulled from the FortiSIEM integration into FortiSOAR™
On the Scheduling screen, from the Do to schedule the ingestion? drop-down list, select Yes.
In the Configure Schedule Settings section, specify the Cron expression For example, if you want to pull data from FortiSIEM every morning at 5 am, click Daily, in the hour box enter 5, and in the minute box enter 0:
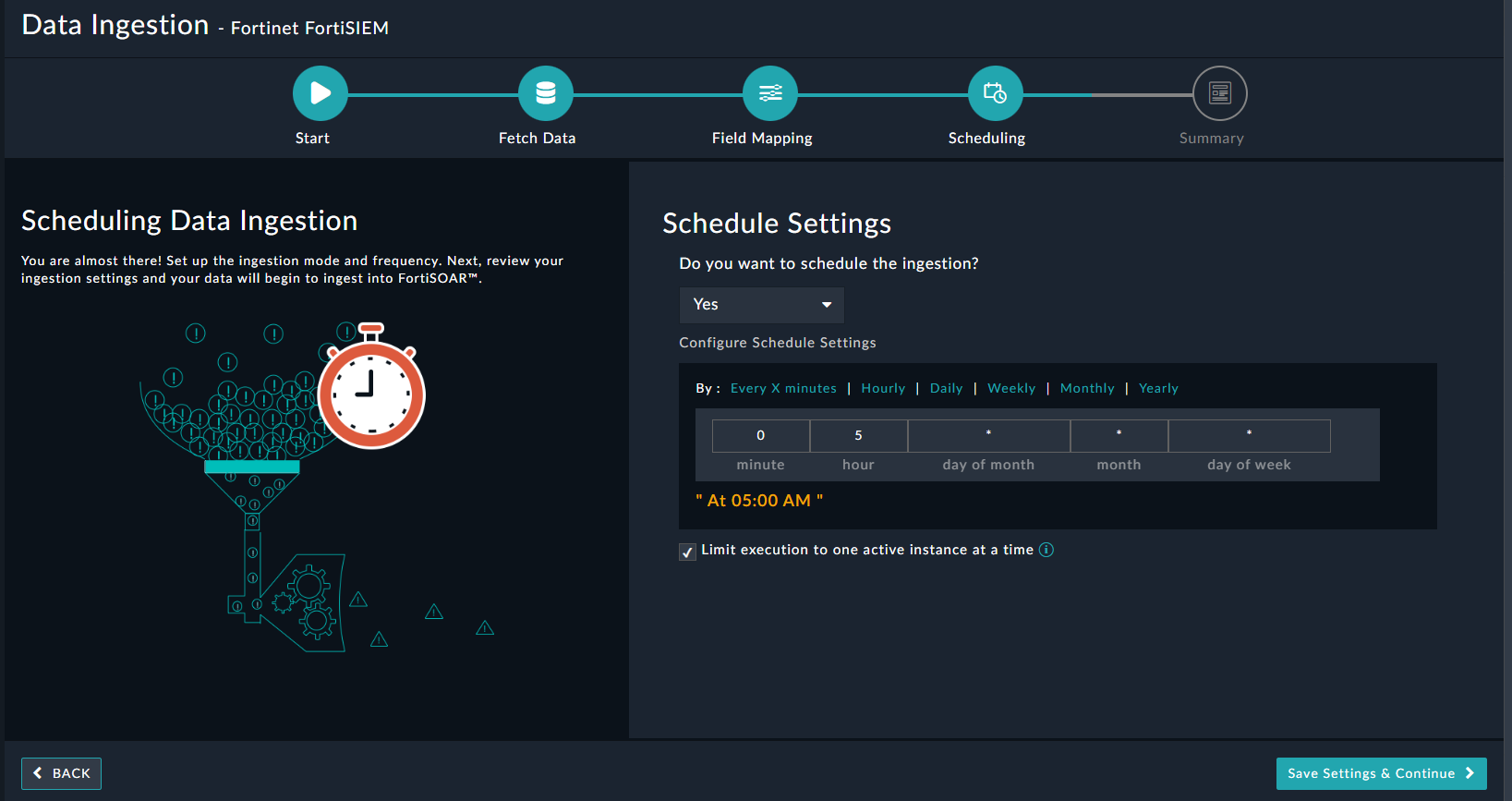
Once you have completed scheduling, click Save Settings & Continue.
-
The Summary screen displays a summary of the mapping done, and it also contains links to the Ingestion playbooks. Click Done to complete the data ingestion and exit the Data Ingestion Wizard.
If you have upgraded your FortiSIEM connector to version 5.0.0 or later from version 4.5.0, then you must reconfigure the FortiSIEM Data Ingestion.
Use Data Ingestion on FortiSIEM v5.0.0 and later: Post-upgrade re-run the Data Ingestion Wizard to reconfigure FortiSIEM data ingestion, i.e., Open the Configurations page of the FortiSIEM connector and click Configure Data Ingestion.
Use Data Ingestion on FortiSIEM v4.5.0: Reconfigure FortiSIEM Data Ingestion using one of the following methods:
- Before upgrading the connector, open the data ingestion playbooks and save the connector step again.
OR
- If you have not performed the above pre-upgrade step, then post-upgrade, export the data ingestion playbooks of the previous version, edit the
playbooks.json file to update the version of the FortiSIEM connector from version 5.0.2 or 5.0.0 to the previous version of the connector, and then re-import the playbooks.json file.
Best Practices - Working with FortiSOAR FortiSIEM Integration
Following is a list of recommendations and suggested best practices for working with the FortiSOAR FortiSIEM integration:
- As the number of incidents in FortiSIEM might be very high, it is suggested to only pull the incidents that are of importance and need further action. For example, incidents of certain types and certain severity. The ingestion experience allows the configuration of these filters to meet the right requirements.
- It is strongly suggested to use the Maximum Events To Pull Per Incident parameter to limit and only fetch required or latest events per incident.
- It is recommended to tune the Maximum Incidents To Pull parameter to limit the incidents fetched per iteration. Tune this parameter based on your scheduled time and the average number of incidents being pulled (with some buffer for peaks).
- Various performance improvements are done with each important release of the connector, and hence it is suggested to upgrade to the latest version of the integration. Before upgrading, we strongly recommend reading the release notes and the connector documentation to understand the upgrade requirements/precursors/compatibility.
- There are important API enhancements support from FortiSIEM that are incorporated from v5.0.0 (and later) of the connector. Hence, upgrades from earlier versions (for example, from 4.5.0 - 5.0.0) requires to be well-planned. This has been documented in the Reconfiguring FortiSIEM Data Ingestion section.










