Mimecast Cloud Gateway
FortiSIEM Support added: 7.2.0
Vendor: Mimecast
Vendor version tested: Mimecast API 2.0
Product Information: https://www.mimecast.com/
Overview
Mimecast provides cloud-based services for email security, archiving, and continuity.
FortiSIEM supports ingesting various logs relating to email activity, and activity within the Mimecast portal such as archive, search, and view logging. For details on how FortiSIEM uses Mimecast API, see Appendix - Mimecast API Information.
Configuring Mimecast
To configure Mimecast, you must create an application with appropriate permissions and subsequently generate an oauth2.0 client ID and client secret. After these steps are completed, you can then configure FortiSIEM.
Note: In the future, FortiSIEM will have a predefined API2.0 application tile in Mimecast portal, but in the interim, you must manually define the role and application here.
Step 1 - Define a Role with Necessary Permissions
-
Login to Mimecast Administration Console.
-
Navigate to Account > Roles.
-
Click New Role.
-
In the Role Name field, enter a name, such as "FortiSIEM_ReadOnly_Role".
-
In the Description field, enter a description, such as "FortiSIEM Read Only access to the Mimecast API".
-
For Security Permissions, select the Cannot Manage Roles button.
-
Under Application Permissions, for every single application permission drop-down, modify the permission so only Read is enabled.
-
When every single permission is set with "Read only", at the very top of the list, click the Save and Exit button.

Reference: https://community.mimecast.com/s/article/api-integrations-managing-api-2-0-for-cloud-gateway
Step 2 - Define a New API Application Integration
-
Login to the Mimecast Administration Console.
-
Navigate to Services > API and Platform Integrations.
-
Select the tile Mimecast API 2.0 at the top of the list.
-
On the next page, read and accept the disclaimer, and click Next.
-
On the Application Details page, set up the following:
-
In the Application Name field, enter a names, such as "FortiSIEM_App".
-
From the Category drop-down list, select SIEM Integration.
-
From the Products drop-down list, select all of them.
-
From the Application Role drop-down list, select the role you created earlier. If you used the example suggestion, it should be "FortiSIEM_ReadOnly_Role".
-
In the Description field, enter a description, such as "FortiSIEM integration with Mimecast 2.0 API".

-
At the bottom right corner, click Next.
-
-
On the next page, enter the Notification Settings.
-
In the Technical Point of Contact field, enter the name of the primary technical point of contact. You can provide a group contact instead of an individual.
-
-
In the Email field, enter the email address of the primary technical point of contact.
-
On bottom right corner, click Next.
-
On the last page click Add and Generate Keys.
A pop up will appear with the Client ID and Client Secret for the application.


The pop up will only appear once.
-
Store the Client ID and Client Secret securely in a password management utility. These will be needed to configure FortiSIEM shortly.
-
Click Close to navigate away from the credentials.
Reference: https://community.mimecast.com/s/article/api-integrations-managing-api-2-0-for-cloud-gateway
Step 3 - Configure FortiSIEM
Prerequisites: A valid Mimecast application created with the necessary permissions, and associated Client ID and Client Secret.
FortiSIEM configuration is comprised of two main steps.
Define Mimecast Credential
Log in to the FortiSIEM Supervisor node, and take the following steps.
- Go to the ADMIN > Setup > Credentials tab.
- In Step 1: Enter Credentials, click New:
- Follow the instructions in “Setting Credentials“ in the User's Guide to create a new credential.
- Enter these settings in the Access Method Definition dialog box and click Save:
| Settings | Description |
|---|---|
| Name | Enter a name for the credential, such as "Mimecast_CG". |
| Device Type | Mimecast Cloud Gateway |
| Access Protocol | MIMECAST_API |
| Pull Interval | 5 Minutes is the default. Leave as is unless there is a specific reason to change. |
| Client ID |
Enter/paste the Client ID from the Mimecast application credential. |
|
Client Secret/Confirm Client Secret |
Enter/paste the Client Secret associated with the client ID from the Mimecast application credential. |
| Description | Description of the device, such as "Mimecast FortiSIEM credential". |

Create IP Range to Credential Association and Test Connectivity
From the FortiSIEM Supervisor node, take the following steps.
- In Step 2: Enter IP Range to Credential Associations, if the organization has more than 1 collector, select the collector from the drop-down list that will do the API polling. If the organization has 1 or no collectors, there is no drop-down and you can proceed to the next step.
- Click New to create a new association.
- Select the name of the credential created in the Define Mimecast Credential from the Credentials drop-down list. If you used the example, it would be "Mimecast_CG".
- The IP/Host Name field will auto-populate. If you would like to use a region specific base URL, you can change the IP/Host Name field. For more information, see Appendix - Regional Endpoints for specific URLs.
- Click Save.

- Select the entry just created, click the Test drop-down list and select Test Connectivity without Ping to start the polling. A pop up will appear and show the Test Connectivity results.
 You should expect a success response here. Afterward, the initial event pulling job will be scheduled. It should take approximately 5 minutes for the first job to kick off.
You should expect a success response here. Afterward, the initial event pulling job will be scheduled. It should take approximately 5 minutes for the first job to kick off. - Go to ADMIN > Setup > Pull Events to observe the job progress.

- A yellow star means a job is scheduled for the first time and has not yet kicked off.
- A green checkbox means a successful poll (as of the last attempt)
- A yellow exclamation or other symbol next to the job indicates an error.
Checking for Events
To check for events, take the following steps.
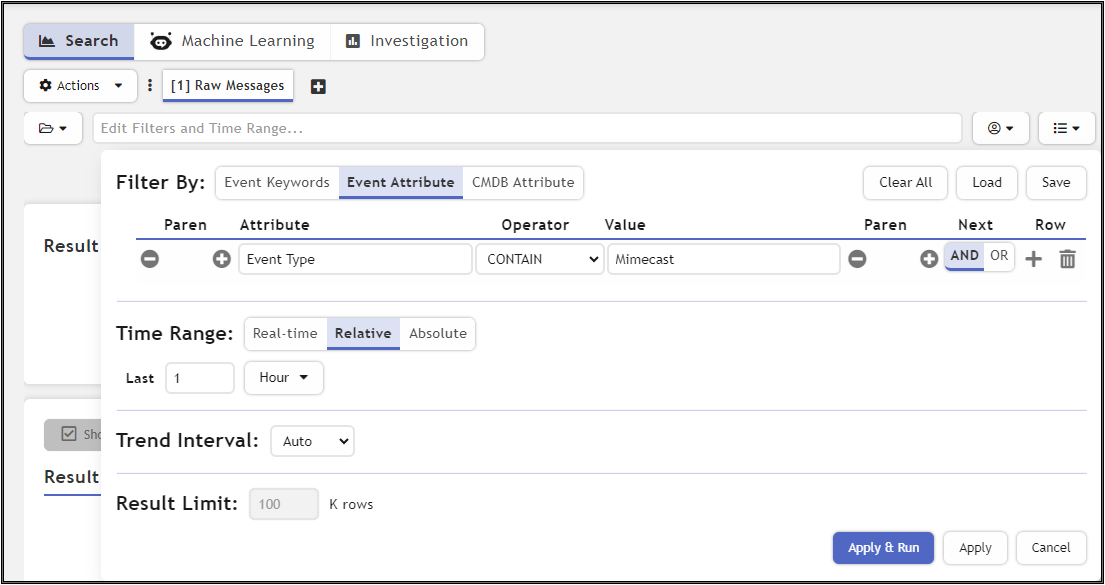
- Navigate to Analytics > Search.
- Click in the Edit Filters and Time Range... field.
- In the Attribute field, enter/select Event Type.
- From the Operator drop-down list, select CONTAIN.
- In the Value field, enter "Mimecast".
- Under Time Range, in the Last field, enter "1".
- Under Time Range, from the time unit drop-down list, select Hour.
- Click Apply & Run.
Rules
Note that the following is an example, and non-exhaustive. Navigate to Resources >Rules and search for "mimecast" in the main Search... field to see available rules.
-
Mimecast: User clicked malicious link in email
Reports
Note that the following are examples, and non-exhaustive. Navigate to Resources >Reports and search for "mimecast" in the main Search... field to see available reports.
- Mimecast: Clicked Malicious or Unsafe URL Details
- Mimecast: External Email Count
- Mimecast: Inbound Email Count
- Mimecast: Internal Email Count
- Mimecast: Outbound Email Count
- Mimecast: Top Clicked Malicious or Unsafe URLs
- Mimecast: Top delivery errors by code
- Mimecast: Top delivery errors by reason
- Mimecast: Top Inbound Mail Senders
- Mimecast: Top internal mail senders without TLS encryption
- Mimecast: Top malware found in emails
- Mimecast: Top malware receivers
- Mimecast: Top malware senders
- Mimecast: Top Message Held Reasons
- Mimecast: Top Outbound Mail Senders
- Mimecast: Top Recipients Clicking on Malicious or Unsafe URLs
- Mimecast: Top Senders and Receivers
- Mimecast: Top Senders with Held Messages
- Mimecast: Top Spam Recipients
- Mimecast: Top Spam Senders
- Mimecast: Top Spam Senders by Source IP
- Mimecast: Top Spam Types by Count
- Mimecast: Top TLS versions used
Dashboard
From the FortiSIEM GUI, navigate to Dashboard, and from the Dashboard drop-down list, select Mimecast. An Overview and Threats dashboard are available by clicking on the appropriate tab.
Note: Only visible under Admin View - Local or Organization Scope.
Appendix
Mimecast API Information
FortiSIEM utilizes the MimeCast 2.0 APIs to provide ingestion of common auditing data points.
Default Base URL: api.services.mimecast.com
OAUTH2.0 Token Endpoint: - /oauth/token
|
API |
Associated Permissions |
|---|---|
| /api/email/get-email-queues | Account | Dashboard | Read |
| /api/archive/get-archive-search-logs | Archive | Search Logs | Read |
| /api/archive/get-search-logs | Archive | Search Logs | Read |
| /api/archive/get-view-logs | Archive | View Logs | Read |
| /api/dlp/get-logs | Monitoring | Data Leak Prevention | Read |
| /api/ttp/attachment/get-logs | Monitoring | Attachment Protection | Read |
| /api/ttp/impersonation/get-logs | Monitoring | Impersonation Protection | Read |
| /api/ttp/url/get-logs | Monitoring | URL Protection | Read |
|
/api/audit/get-audit-events |
Account | Logs | Read |
|
/siem/v1/batch/events/cg |
Security Events and Data Retrieval | Threat and Security Events (SIEM)| Read permission |
|
/threats/v1/stats/attachment-scans |
|
|
/threats/v1/stats/url-clicks |
|
|
/threats/v1/stats/impersonations |
Security Events and Data Retrieval | Threat and Security Events (SIEM)| Read permission |
Notes on Monitoring with Mimecast
While the default polling interval from FortiSIEM is every 5 minutes, the Mimecast SIEM batch API can only be called every 15 minutes. This is enforced by Mimecast, so be aware that there is an intentional delay from the time some events occur and when they are available in FortiSIEM.
Regional Endpoints
|
Base URL Region |
Host |
|---|---|
| Europe (EU) [Excluding Germany] | https://eu-api.mimecast.com |
| Germany (DE) | https://de-api.mimecast.com |
| United States of America (US) | https://us-api.mimecast.com |
| United States of America (USB) | https://usb-api.mimecast.com |
| USPCOM | https://uspcom-api.mimecast-pscom-us.com |
| Canada (CA) | https://ca-api.mimecast.com |
| South Africa (ZA) | https://za-api.mimecast.com |
|
Australia (AU) |
https://au-api.mimecast.com |
| Offshore | https://je-api.mimecast.com |

