Security
Authentication and Encryption Methods: Since Wi-Fi is transmitted over the air, there is no reliable way to limit physical access to the network. Because the network can be sniffed (listened to by another radio), it needs encryption if it is to be private. Nevertheless, open networks are common for guest use or in public venues, possibly with Captive Portals (see below) included.
WPA2 and WPA3 Enterprise are RADIUS based authentication methods. These are the standards any enterprise class network should be using. If you have a database of users with a RADIUS front end available, this is the method to use. Add the RADIUS server under Configuration > My RADIUS Server and then it can be used when configuring an SSID.
Both encryption and authentication are strongest with WPA2/3 Enterprise. We are currently in a technology transition period, as there are still many clients out there that do not support WPA3 enterprise. WPA3 enterprise should be supported by Windows 11 with a compatible Wi-Fi card, Mac computers after 2013, iPhone 11 and more, but you may need a transition plan for your network if you have older clients.
FortiLAN Cloud as the RADIUS server: If you want to use WPA2/3 Enterprise Authentication and do not already have a RADIUS fronted database of users, you can use FortiLAN Cloud instead. You can define users and user groups in FortiLAN Cloud and use it as the RADIUS server. Note that the WLAN will have to be bridged, not NATed, but that users can be assigned to specific VLANs.
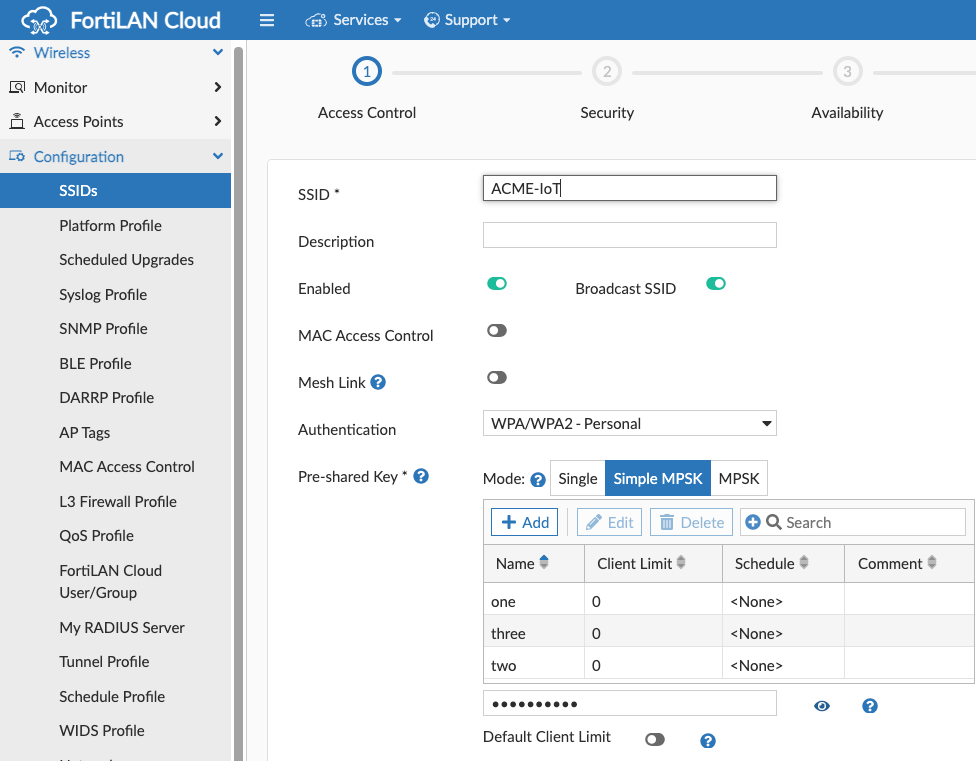
WPA2 Personal and WPA3 SAE use a Pre-Shared Key (PSK) for authentication and encryption. This is usually referred to as "the Wi-Fi password". This is meant for home use and small offices and should be avoided in locations where more than a few users are to be authenticated.
A WPA2 Personal/WPA3 SAE SSID may be necessary even in large environments because of IoT devices that do not support the enterprise options. If so, security best practices are to isolate such WLANs to a specific VLAN.
MPSK (Multiple PSK): A Fortinet Wi-Fi option when creating a WPA2 Personal network is to use multiple keys. In this case, not every device uses the same PSK, sharing the keys among groups of devices or even a unique entry for each device. WPA3 SAE does not need this option. SAE (Simultaneous Authentication of Equals) generates a unique encryption key for each session/device.
Captive Portals and Open Networks: Open Networks have no Layer 2 encryption or authentication, while a Captive Portal is a web page than can be used for authentication above Layer 2, or simply present a click through disclaimer page. The authentication portal can be hosted at the FortiGate or use an external 3rd party portal. Captive Portal can also be combined with WPA2 Personal.
-
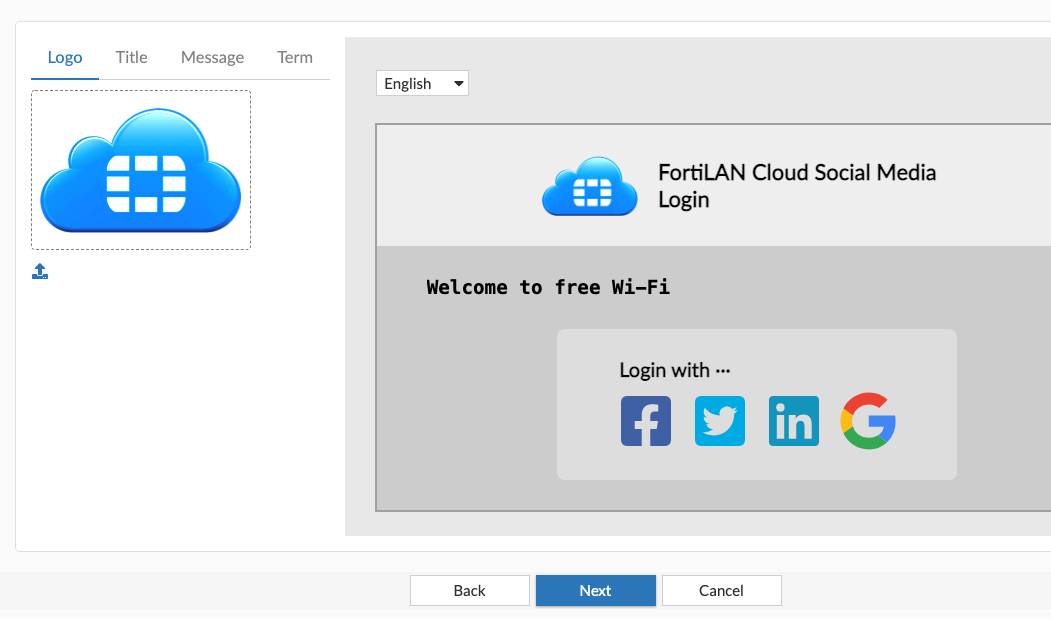
Public Networks, such as the local coffee shop, make frequent use of Captive portals, sometimes with a minimal disclaimer only, or sometimes with self-registration. FortLAN Cloud Wi-Fi supports email capture during self-registration via captive portal.
-
Guest Networks are usually used in Enterprise environments, where guests need permission from say a lobby administrator. Fortinet Wi-Fi supports this and several variations, such as a guest sponsorship.
FortiLAN Cloud supports several Captive Portal options, all customizable with logo, title, and text:
- Simple click through
- RADIUS and FortiLAN Cloud user groups based portal authentication
- Self-registration with email and/or phone capture
- Social media login
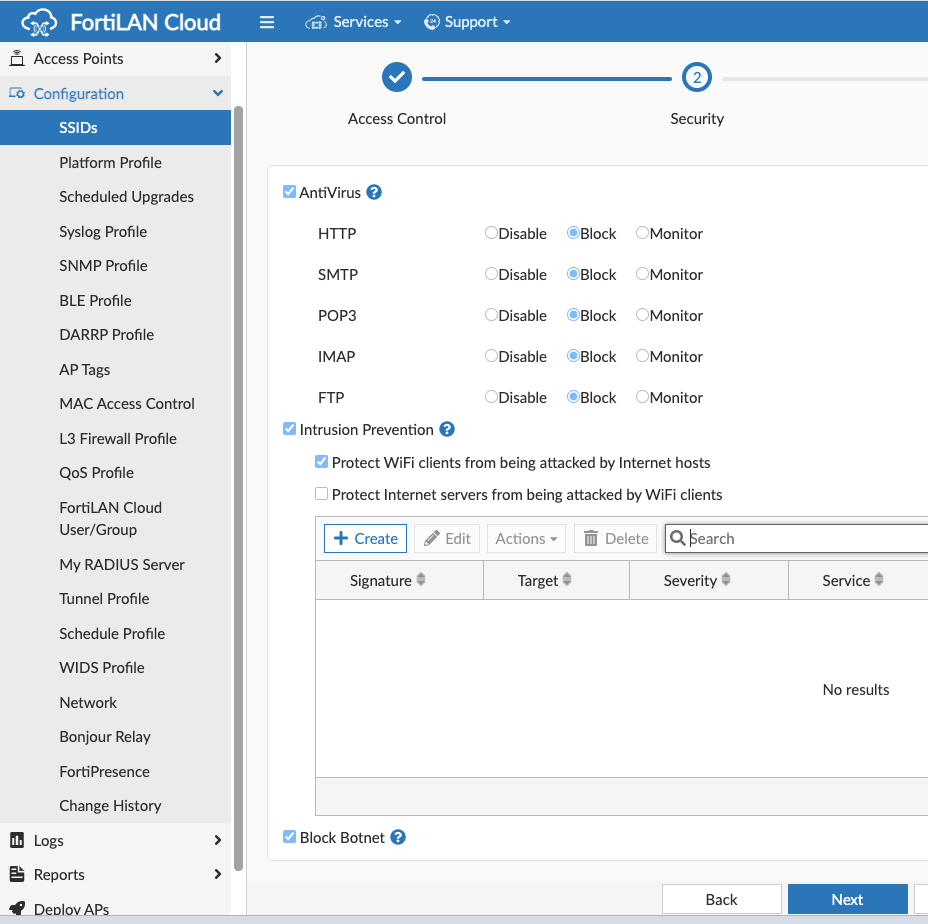
UTP (Universal Threat Protection) Security: UTP Security scans are supported on U series FortiAPs and can be enabled on a per SSID basis. The SSID creation process allows you to enable the following options with check boxes:
- Application control
- Web Access
- Block Botnet
- Intrusion Prevention
- AntiVirus
Wireless Intrusion Detection System (WIDS): WIDS profiles monitor and alert for a number of Wi-Fi attacks such as ASLEAP, authentication and association floods, and other Wi-fi attacks. WIDs profiles can be enabled on a per radio basis in AP profiles

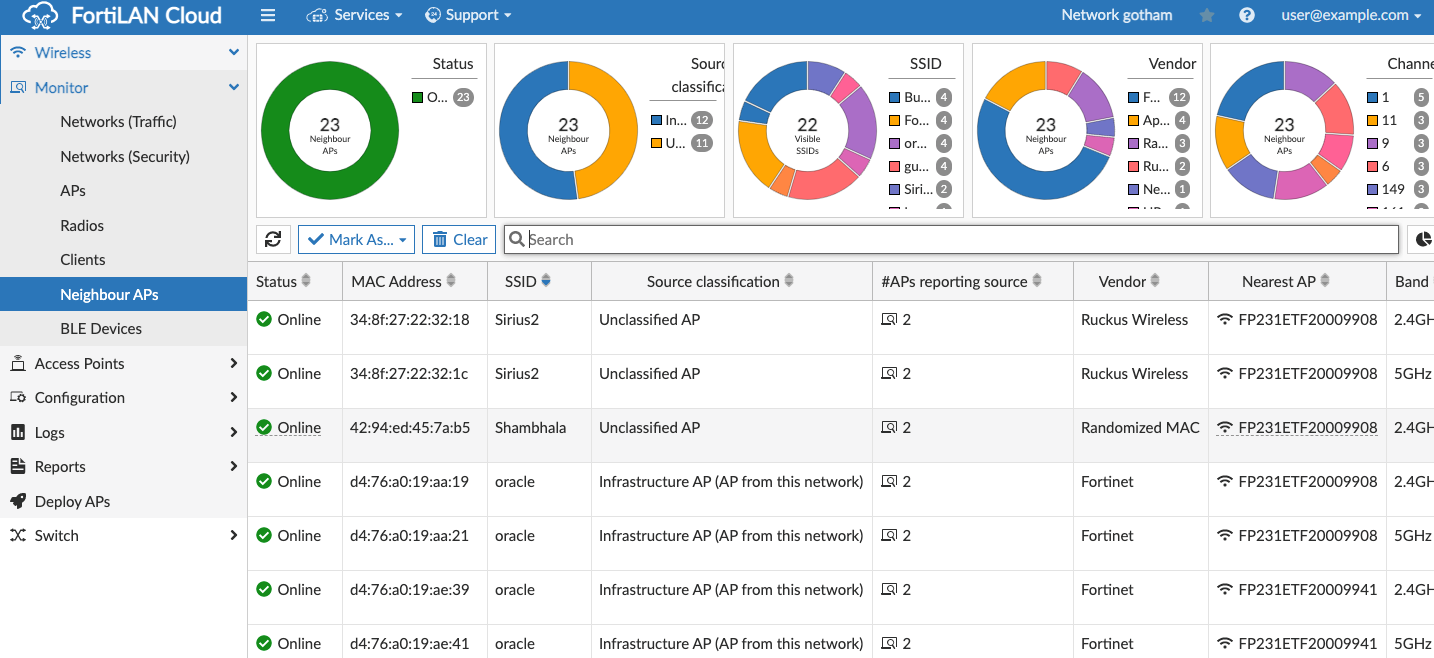
Rogue and Neighbor AP Detection: All Wi-Fi 6 FortiAPs have a third radio for monitoring purposes and it is highly recommended to enable Rogue AP scanning on the monitoring radio, which can scan the entire channel space while the service radios support network clients. Awareness of neighbor APs helps DARRP make better automatic channel plans.