Configuring IP mapping in HA mode
Prerequisites:
Please follow High Availability to make sure native HA mode works before configuring IP Mapping in HA mode.
Configuring IP Mapping in HA mode includes the following steps:
- FortiIsolator configuration
- FortiGate configuration
- Client system configuration
Single-node setting (one-primary only)
To configure IP mapping of FortiIsolator in HA mode with one single primary node:
- Configure port forwarding mappings using the following commands in the FortiIsolator CLI:
set fis-ipmap <port_map_to_443> <external_IP_address>For example,
set fis-ipmap 12443 172.30.147.207set fis-ipmap-vip <external IP> <vip_port_map_to_443>For example,
set fis-ipmap-vip 172.30.147.207 14443set fis-ipmap-ha <priority> <external_IP_address> <internal_IP_address:primary> <port_map_to_443>For example,
set fis-ipmap-ha 19 172.30.147.207 172.30.157.148 12443

- Make sure HA is Enabled in Fortilsolator.

FortiGate configuration
Complete the following steps in the FortiGate UI.
- Go to Policy & Objects > Virtual IPs.
- Create an IPv4 virtual IP with the following information:
IP-Mapping-HA-443: external_IP_address -> FIS_IP (TCP: 12443 > 443)
For example, 172.30.147.207 -> 172.30.157.96 (TCP: 12443 > 443).

In this example, we are using:
- External_IP_address: 172.30.147.207
- FIS HA Virtual IP: 172.30.157.96
- FIS_IP: 172.30.157.148
Settings of IP-Mapping-443:

Settings of IP-Mapping-HA-443:

- Go to Policy & Objects > IPv4 Policy > Create New.
- Create an IPv4 policy that includes the virtual IP that you created.

Client system configuration
Complete the following steps on the client system (for example, Windows 10).
- In Windows 10, launch CMD as administrator.
- Use the following commands to add the FortiGate IP address to the routing table on the client system:
- At the command prompt, type
route -p ADD <external_IP_address> Mask 255.255.255.255 <FGT_IP_address>.For example,
route –p ADD 172.30.147.207 MASK 255.255.255.255 172.30.157.90 - To confirm the setup, type
route print.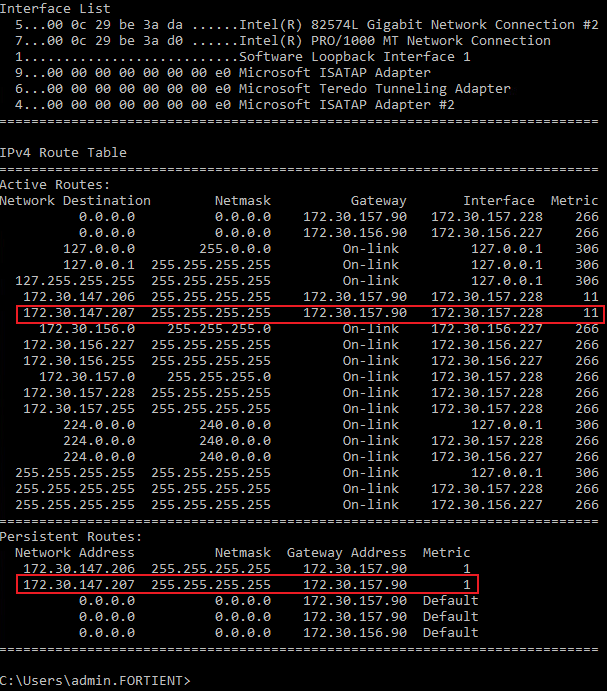
- At the command prompt, type
- Check the Client IPv4 setting. Make sure default gateway is the FortiGate IP.

- Configure your browser by following the steps in IP Forwarding mode, depending on your browser type.
- Verify that it works by browsing to the following address:
https://<external_IP_address>:<port_map_to_HA_443>/isolator/https://www.fortinet.come.g.:
https://172.30.147.207:14443/isolator/https://www.fortinet.com(It will now redirect to:
https://172.30.147.207:12443/isolator/https://www.fortinet.com)
Multiple-nodes setting (one-primary-one-secondary)
To configure IP mapping of FortiIsolator in HA mode with one primary node and one secondary node:
- In the primary node, configure port forwarding mappings using the following commands in the FortiIsolator CLI:
set fis-ipmap <port_map_to_443> <external_IP_address>For example,
set fis-ipmap 12443 172.30.147.207set fis-ipmap-vip <external IP> <vip_port_map_to_443>For example,
set fis-ipmap-vip 172.30.147.207 14443set fis-ipmap-ha <priority> <external_IP_address> <internal_IP_address:primary> <port_map_to_443>For example,
set fis-ipmap-ha 19 172.30.147.207 172.30.157.148 12443set fis-ipmap-ha <priority> <external_IP_address> <internal_IP_address:secondary1> <port_map_to_443>For example,
set fis-ipmap-ha 20 172.30.147.207 172.30.157.149 13443

- In the secondary node, configure port forwarding mappings using the following commands in the FortiIsolator CLI:
set fis-ipmap <port_map_to_443> <external_IP_address>For example,
set fis-ipmap 13443 172.30.147.207

- Make sure the primary and secondary nodes have different HA priority but the same group id.

Below is a summary of the example:
- Primary:
172.30.156.148set fis-ipmap 12443 172.30.147.207set fis-ipmap-vip 172.30.147.207 14443set fis-ipmap-ha 19 172.30.147.207 172.30.157.148 12443set fis-ipmap-ha 20 172.30.147.207 172.30.157.149 13443
- Secondary:
172.30.156.149set fis-ipmap 13443 172.30.147.207
FortiGate configuration
Complete the following steps in the FortiGate UI.
- Go to Policy & Objects > Virtual IPs.
- Create an IPv4 virtual IP for the secondary node with the following information:
IP-Mapping-HA-443: <external_IP_address> -> FIS_IP (TCP: 14443 > 443)
For example, 172.30.147.207 -> 172.30.157.96 (TCP: 14443 > 443)

This example uses the following:
- External_IP_address: 172.30.147.207
FIS HA Virtual IP: 172.30.157.96
- FIS_IP_Primary: 172.30.157.148
FIS_IP_Secondary: 172.30.157.149

Settings of second ip-mapping-443:

- Go to Policy & Objects > IPv4 Policy > Create New.
- Create an IPv4 policy that includes the virtual IP that you created.

Client system configuration
Complete the following steps on the client system (for example, Windows 10).
- In Windows 10, launch CMD as administrator.
- Use the following commands to add the FortiGate IP address to the routing table on the client system:
At the command prompt, type
route –p ADD <external_IP_address> Mask 255.255.255.255 <FGT_IP_address>For example,
route –p ADD 172.30.147.207 MASK 255.255.255.255 172.30.157.90
To confirm the setup, type
route print.

- Check the Client IPv4 setting. Make sure default gateway is the FortiGate IP.

- Configure your browser by following the steps in IP Forwarding mode, depending on your browser type.
- Verify that it works by browsing to the following address:
https://<external_IP_address>:<port_map_to_HA_443>/isolator/https://www.fortinet.come.g.:
https://172.30.147.207:14443/isolator/https://www.fortinet.comThe address will now redirect to the primary node:
https://172.30.147.207:12443/isolator/https://www.fortinet.comor the secondary node:
https://172.30.147.207:13443/isolator/https://www.fortinet.com

