Use SD-WAN rules for WAN link selection with load balancing
This example covers a use case where a user has multiple WAN links and wants to optimize the WAN link selection and performance while limiting the use of more expensive and bandwidth intensive interfaces, such as 5G or LTE.
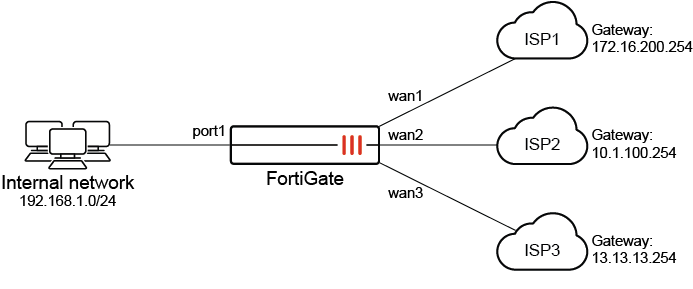
In this scenario, the user has three WAN links. The goal is to balance the load between wan1 and wan2; however, wan3, which is quite costly to operate, should only be used if both wan1 and wan2 are unavailable.
This configuration involves the following steps:
Configuring the SD-WAN members
SD-WAN must be enabled first, and member interfaces must be selected and added to a zone. See Configuring the SD-WAN interface for more information.
To configure the SD-WAN members in the GUI:
-
Configure the wan1, wan2, and wan3 interfaces (see Interface settings for more details).
-
Set the wan1 interface IP/Netmask to 172.16.200.1 255.255.255.0.
-
Set the wan2 interface IP/Netmask to 10.1.100.1 255.255.255.0.
-
Set the wan3 interface IP/Netmask to 13.13.13.1 255.255.255.0.
-
-
Go to Network > SD-WAN, select the SD-WAN Zones tab, and click Create New > SD-WAN Member.
-
Configure the wan1 SD-WAN member:
-
Set the Interface to wan1.
-
Leave the SD-WAN Zone as virtual-wan-link.
-
Set the Gateway to 172.16.200.254.
-
Set the Status to Enable
-
Click OK.
-
-
Repeat step 3 for wan2 and wan3.
-
For wan2, set the Gateway to the ISP’s gateway, 10.1.100.254.
-
For wan3, set the Gateway to the ISP’s gateway, 13.13.13.254.
-
To configure the SD-WAN members in the CLI:
config system sdwan
set status enable
config zone
edit "virtual-wan-link"
next
end
config members
edit 1
set interface "wan1"
set gateway 172.16.200.254
next
edit 2
set interface "wan2"
set gateway 10.1.100.254
next
edit 3
set interface "wan3"
set gateway 13.13.13.254
next
end
end
Configuring the manual SD-WAN rule
SD-WAN rules define specific routing options to route traffic to an SD-WAN member. See SD-WAN rules and Manual strategy for more information.
To configure a manual SD-WAN rule in the GUI:
-
Go to Network > SD-WAN, select the SD-WAN Rules tab, and click Create New.
-
Configure the following settings:
Name
test
Source > Address
all
Destination > Address
all
Interface selection strategy
Manual
Interface preference
wan1, wan2
Load balancing
Enable this setting.
-
Configure the other settings as needed.
-
Click OK.
To configure a manual SD-WAN rule in the CLI:
config system sdwan
config service
edit 1
set name "test"
set load-balance enable
set dst "all"
set src "all"
set priority-members 1 2
next
end
end
Configuring a static route
A default route for SD-WAN must be configured. See Adding a static route for more information.
To configure a static route for SD-WAN in the GUI:
-
Go to Network > Static Routes and click Create New. The New Static Route page opens.
-
Set the Destination to Subnet, and leave the IP address and subnet mask as 0.0.0.0/0.0.0.0.
-
Set the Interface to the SD-WAN zone, virtual-wan-link.
-
Set the Status to Enabled.
-
Click OK.
To configure a static route for SD-WAN in the CLI:
config router static
edit 1
set distance 1
set sdwan-zone "virtual-wan-link"
next
end
Configuring a firewall policy for SD-WAN
A firewall policy must be configured that allows traffic from the organization's internal network to the SD-WAN zone. See Configuring firewall policies for SD-WAN for more information.
To configure the firewall policy for SD-WAN in the GUI:
-
Go to Policy & Objects > Firewall Policy and click Create New.
-
Configure the following settings:
Name
sd-wan
Incoming interface
port1
Outgoing interface
virtual-wan-link
Source
all
Destination
all
Schedule
always
Service
ALL
Action
ACCEPT
NAT
Enable and select NAT.
IP Pool Configuration
Use Outgoing Interface Address
Enable this policy
Enable this setting.
-
Configure the other settings as needed.
-
Click OK.
To configure the firewall policy for SD-WAN in the CLI:
config firewall policy
edit 1
set name "sd-wan"
set srcintf "port1"
set dstintf "virtual-wan-link"
set action accept
set srcaddr "all"
set dstaddr "all"
set schedule "always"
set service "ALL"
set nat enable
next
end
Verifying the configuration
To verify the SD-WAN member status:
# diagnose sys sdwan member Member(1): interface: wan1, flags=0x0 , gateway: 172.16.200.254, priority: 1 1024, weight: 0 Member(2): interface: wan2, flags=0x0 , gateway: 10.1.100.254, priority: 1 1024, weight: 0 Member(3): interface: wan3, flags=0x0 , gateway: 13.13.13.254, priority: 1 1024, weight: 0
To verify the configuration when both wan1 and wan2 are up:
-
Verify the SD-WAN service rules status:
# diagnose sys sdwan service Service(1): Address Mode(IPV4) flags=0x24200 use-shortcut-sla use-shortcut Tie break: cfg Gen(1), TOS(0x0/0x0), Protocol(0): src(1->65535):dst(1->65535), Mode(manual hash-mode=round-robin) Members(2): 1: Seq_num(2 wan2 virtual-wan-link), alive, gid(1), selected 2: Seq_num(1 wan1 virtual-wan-link), alive, gid(1), selected Src address(1): 0.0.0.0-255.255.255.255 Dst address(1): 0.0.0.0-255.255.255.255This output indicates that both wan1 and wan2 are operational.
-
Verify the policy route list:
# diagnose firewall proute list list route policy info(vf=root): id=2130706433(0x7f000001) vwl_service=1(test) vwl_mbr_seq=1 2 dscp_tag=0xfc 0xfc flags=0x10 load-balance hash-mode=round-robin tos=0x00 tos_mask=0x00 protocol=0 port=src(0->0):dst(0->0) iif=0(any) path(2): oif=3(wan1) num_pass=0, oif=6(wan2) num_pass=0 source(1): 0.0.0.0-255.255.255.255 destination(1): 0.0.0.0-255.255.255.255 hit_count=154 last_used=2023-11-09 06:16:
This output indicates that both wan1 and wan2 are used to steer traffic.
To verify the configuration when wan2 is down and wan1 is up:
-
Verify the SD-WAN service rules status:
# diagnose sys sdwan service Service(1): Address Mode(IPV4) flags=0x24200 use-shortcut-sla use-shortcut Tie break: cfg Gen(1), TOS(0x0/0x0), Protocol(0): src(1->65535):dst(1->65535), Mode(manual hash-mode=round-robin) Members(2): 1: Seq_num(1 wan1 virtual-wan-link), alive, gid(1), selected 2: Seq_num(2 wan2 virtual-wan-link), dead, gid(1) Src address(1): 0.0.0.0-255.255.255.255 Dst address(1): 0.0.0.0-255.255.255.25This output indicates that wan1 is operational, and wan2 is not.
-
Verify the policy route list:
# diagnose firewall proute list list route policy info(vf=root): id=2130706433(0x7f000001) vwl_service=1(test) vwl_mbr_seq=1 dscp_tag=0xfc 0xfc flags=0x10 load-balance hash-mode=round-robin tos=0x00 tos_mask=0x00 protocol=0 port=src(0->0):dst(0->0) iif=0(any) path(1): oif=3(wan1) num_pass=0 source(1): 0.0.0.0-255.255.255.255 destination(1): 0.0.0.0-255.255.255.255 hit_count=482 last_used=2023-11-09 06:27:08
This output indicates that wan1 is used to steer traffic.
To verify the configuration when wan1 is down and wan2 is up:
-
Verify the SD-WAN service rules status:
# diagnose sys sdwan service Service(1): Address Mode(IPV4) flags=0x24200 use-shortcut-sla use-shortcut Tie break: cfg Gen(1), TOS(0x0/0x0), Protocol(0): src(1->65535):dst(1->65535), Mode(manual hash-mode=round-robin) Members(2): 1: Seq_num(2 wan2 virtual-wan-link), alive, gid(1), selected 2: Seq_num(1 wan1 virtual-wan-link), dead, gid(1) Src address(1): 0.0.0.0-255.255.255.255 Dst address(1): 0.0.0.0-255.255.255.255This output indicates that wan2 is operational, and wan1 is not.
-
Verify the policy route list:
# diagnose firewall proute list list route policy info(vf=root): id=2130706433(0x7f000001) vwl_service=1(test) vwl_mbr_seq=2 dscp_tag=0xfc 0xfc flags=0x10 load-balance has h-mode=round-robin tos=0x00 tos_mask=0x00 protocol=0 port=src(0->0):dst(0->0) iif=0(any) path(1): oif=6(wan2) num_pass=0 source(1): 0.0.0.0-255.255.255.255 destination(1): 0.0.0.0-255.255.255.255 hit_count=903 last_used=2023-11-09 06:41:55
This output indicates that wan2 is used to steer traffic.
To verify the configuration when both wan1 and wan2 down, and traffic is steered using wan3:
# diagnose sniffer packet wan3 Using Original Sniffing Mode interfaces=[wan3] filters=[none] 3.144417 13.13.13.1.52665 -> 204.79.197.239.443: 1610731732 ack 236747780 3.155250 204.79.197.239.443 -> 13.13.13.1.52665: ack 1610731733 5.047264 13.13.13.1.52613 -> 20.185.212.106.443: 1421254032 ack 3784884456 5.126008 20.185.212.106.443 -> 13.13.13.1.52613: ack 1421254033
This output indicates that wan3 is used to steer traffic.
To verify the configuration when either wan1 or wan2 is restored, and traffic ceases to be steered through wan3:
-
Verify the SD-WAN service rules status:
# diagnose sys sdwan service Service(1): Address Mode(IPV4) flags=0x24200 use-shortcut-sla use-shortcut Tie break: cfg Gen(1), TOS(0x0/0x0), Protocol(0): src(1->65535):dst(1->65535), Mode(manual hash-mode=round-robin) Members(2): 1: Seq_num(1 wan1 virtual-wan-link), alive, gid(1), selected 2: Seq_num(2 wan2 virtual-wan-link), dead, gid(1) Src address(1): 0.0.0.0-255.255.255.255 Dst address(1): 0.0.0.0-255.255.255.255This output indicates that wan1 is operational.
-
Verify the policy route list:
# diagnose firewall proute list list route policy info(vf=root): id=2130706433(0x7f000001) vwl_service=1(test) vwl_mbr_seq=1 dscp_tag=0xfc 0xfc flags=0x10 load-balance has h-mode=round-robin tos=0x00 tos_mask=0x00 protocol=0 port=src(0->0):dst(0->0) iif=0(any) path(1): oif=3(wan1) num_pass=0 source(1): 0.0.0.0-255.255.255.255 destination(1): 0.0.0.0-255.255.255.255 hit_count=986 last_used=2023-11-09 06:45:13
This output indicates that wan1 is used to steer traffic.

