Allow better control over the source IP used by each egress interface for local out traffic
|
|
This information is also available in the FortiOS 7.4 Administration Guide: |
Better control over the source IP used by each egress interface is feasible by allowing a preferred source IP to be defined in each of these scenarios.
-
Configuring a static route:
config router static edit <id> set preferred-source <ip_address> next end -
Configuring an SD-WAN member:
config system sdwan config members edit <id> set preferred-source <ip_address> next end end -
Configuring a route map so that a BGP route can support a preferred source:
config router route-map edit <name> config rule edit <id> set set-ip-prefsrc <ip_address> next end next end
Example configurations
In scenarios where multiple CPE (customer premise equipment) routers are used for each transport, it is easy to define a public IP per router as a loopback IP. Then, locally sourced traffic and BGP routes can use the public loopback IP as source.
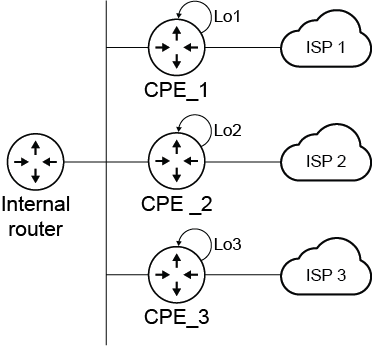
When a FortiGate is used to replace multiple CPE routers, it must be able to source traffic with the public IP assigned by their respective ISP that is assigned to the loopback interfaces.

This feature allows the preferred source IP to be configured in the following scenarios so that local out traffic is sourced from these IPs.
Example 1
In this example, a source IP is defined per static route. Local traffic that uses the static route will use the source IP instead of the interface IP associated with the route.
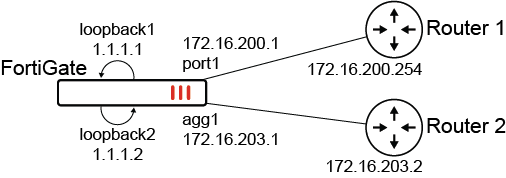
To configure preferred source IPs for static routes:
-
Configure the static routes:
config router static edit 22 set dst 172.17.254.0 255.255.255.0 set gateway 172.16.200.254 set preferred-source 1.1.1.1 set distance 2 set device "port1" next edit 23 set dst 172.17.254.0 255.255.255.0 set gateway 172.16.203.2 set preferred-source 1.1.1.2 set distance 2 set device "agg1" next end -
Configure the primary DNS server IP address:
config system dns set primary 172.17.254.148 end
To verify the configuration:
-
Verify the kernel routing table:
# get router info kernel ... tab=254 vf=0 scope=0 type=1 proto=11 prio=1 0.0.0.0/0.0.0.0/0->172.17.254.0/24 pref=0.0.0.0 gwy=172.16.200.254 flag=14 hops=0 oif=9(port1) pref=1.1.1.1 gwy=172.16.203.2 flag=14 hops=0 oif=33(agg1) pref=1.1.1.2 -
Verify the routing table for 172.17.254.148:
# get router info routing-table details 172.17.254.148 Routing table for VRF=0 Routing entry for 172.17.254.0/24 Known via "static", distance 2, metric 0, best * vrf 0 172.16.200.254, via port1, prefsrc 1.1.1.1 * vrf 0 172.16.203.2, via agg1, prefsrc 1.1.1.2
-
Run a sniffer trace after some traffic passes:
# diagnose sniffer packet any "host 172.17.254.148" 4 interfaces=[any] filters=[host 172.17.254.148] 1.319811 port1 out 1.1.1.1.1371 -> 172.17.254.148.53: udp 43 1.320095 port1 in 172.17.254.148.53 -> 1.1.1.1.1371: udp 310 1.921718 port1 out 1.1.1.1.1371 -> 172.17.254.148.53: udp 27 2.031520 port1 in 172.17.254.148.53 -> 1.1.1.1.1371: udp 213
When DNS traffic leaves the FortiGate and is routed through port1, the source address 1.1.1.1 is used.
Example 2:
In this example, a route map is configured to set the preferred source IP so that the BGP route can support the preferred source.

To configure preferred source IPs for BGP routing:
-
Configure the route maps:
config router route-map edit "map1" config rule edit 1 set set-ip-prefsrc 1.1.1.1 next end next edit "map2" config rule edit 1 set set-ip-prefsrc 1.1.1.2 next end next end -
Configure the BGP settings:
config router bgp set as 65412 set router-id 1.1.1.1 set ibgp-multipath enable set cluster-id 1.1.1.1 set graceful-restart enable config aggregate-address edit 1 set prefix 172.28.0.0 255.255.0.0 set as-set enable set summary-only enable next end config neighbor edit "3.3.3.3" set capability-graceful-restart enable set soft-reconfiguration enable set prefix-list-out "local-out" set remote-as 65412 set route-map-in "map2" set route-map-out "as-prepend" set keep-alive-timer 30 set holdtime-timer 90 set update-source "loopback1" set route-reflector-client enable next edit "2.2.2.2" set advertisement-interval 5 set activate6 disable set capability-graceful-restart enable set soft-reconfiguration enable set distribute-list-out "local-out-FGTB-deny" set remote-as 65412 set route-map-in "map1" set route-map-out "as-rewrite" set keep-alive-timer 30 set holdtime-timer 90 set update-source "loopback1" next end end
To verify the configuration:
-
Verify the BGP routing table for 172.25.1.0/24:
# get router info bgp network 172.25.1.0/24 VRF 0 BGP routing table entry for 172.25.1.0/24 Paths: (1 available, best #1, table Default-IP-Routing-Table) Not advertised to any peer Original VRF 0 Local 2.2.2.2 (metric 10050) from 2.2.2.2 (2.2.2.2) Origin IGP metric 0, localpref 100, valid, internal, best, prefsrc 1.1.1.1 Last update: Wed Jan 25 15:15:48 2023 -
Verify the BGP routing table for 172.28.5.0/24:
# get router info bgp network 172.28.5.0/24 VRF 0 BGP routing table entry for 172.28.5.0/24 Paths: (1 available, best #1, table Default-IP-Routing-Table, Advertisements suppressed by an aggregate.) Not advertised to any peer Original VRF 0 65050, (Received from a RR-client) 3.3.3.3 (metric 11000) from 3.3.3.3 (3.3.3.3) Origin IGP metric 0, localpref 100, valid, internal, best, prefsrc 1.1.1.2 Last update: Wed Jan 25 15:15:48 2023 -
Verify the kernel routing table for 172.28.5.0/24:
# get router info kernel | grep -B 2 172.28.5.0/24 tab=254 vf=0 scope=0 type=1 proto=11 prio=1 0.0.0.0/0.0.0.0/0->172.28.1.0/24 pref=1.1.1.2 gwy=172.16.200.4 dev=9(port1) tab=254 vf=0 scope=0 type=1 proto=11 prio=1 0.0.0.0/0.0.0.0/0->172.28.2.0/24 pref=1.1.1.2 gwy=172.16.200.4 dev=9(port1) tab=254 vf=0 scope=0 type=1 proto=11 prio=1 0.0.0.0/0.0.0.0/0->172.28.5.0/24 pref=1.1.1.2 gwy=172.16.200.4 dev=9(port1)
-
Verify the kernel routing table for 172.25.1.0/24:
# get router info kernel | grep -A 2 172.25.1.0/24 tab=254 vf=0 scope=0 type=1 proto=11 prio=1 0.0.0.0/0.0.0.0/0->172.25.1.0/24 pref=1.1.1.1 gwy=172.16.203.2 dev=33(agg1) tab=254 vf=0 scope=0 type=1 proto=11 prio=1 0.0.0.0/0.0.0.0/0->172.26.1.0/24 pref=1.1.1.1 gwy=172.16.203.2 dev=33(agg1) tab=254 vf=0 scope=0 type=1 proto=11 prio=1 0.0.0.0/0.0.0.0/0->172.26.2.0/24 pref=1.1.1.1 gwy=172.16.203.2 dev=33(agg1)
The FortiGate learns routes from router 3.3.3.3 and prefers the source IP of 1.1.1.2. It learns routes from router 2.2.2.2 and prefers source IP of 1.1.1.1.
-
Run a sniffer trace after some traffic passes.
-
When trying to reach a destination in the 172.25.1.0/0 subnet through router 2.2.2.2:
# diagnose sniffer packet any "icmp" 4 interfaces=[any] filters=[icmp] 9.244334 agg1 out 1.1.1.1 -> 172.25.1.2: icmp: echo request 9.244337 port12 out 1.1.1.1 -> 172.25.1.2: icmp: echo request 10.244355 agg1 out 1.1.1.1 -> 172.25.1.2: icmp: echo request 10.244357 port12 out 1.1.1.1 -> 172.25.1.2: icmp: echo request
-
When trying to reach a destination in the 172.28.5.0/24 subnet through router 3.3.3.3:
# diagnose sniffer packet any "icmp" 4 interfaces=[any] filters=[icmp] 2.434035 port1 out 1.1.1.2 -> 172.28.5.2: icmp: echo request 3.434059 port1 out 1.1.1.2 -> 172.28.5.2: icmp: echo request
Traffic destined for the 172.25.1.0/24 subnet uses 1.1.1.1 as source. Traffic destined for the 172.28.5.0/24 subnet uses 1.1.1.2 as source.
-
Example 3:
In this example, two SD-WAN members, port5 and port6, will use loopback1 and loopback2 as sources instead of their physical interface address. A static route is created for destination 200.0.0.0/24 to use the virtual-wan-link. In turn, the FortiGate will create two ECMP routes to the member gateways and source the traffic from the loopback IPs.

To configure preferred source IPs for SD-WAN members:
-
Configure the SD-WAN members and other settings:
config system sdwan set status enable config zone edit "virtual-wan-link" next end config members edit 1 set interface "port5" set gateway 10.100.1.1 set preferred-source 1.1.1.1 set source 1.1.1.1 next edit 2 set interface "port7" set gateway 10.100.1.5 set preferred-source 1.1.1.2 set source 1.1.1.2 next end end
In the SD-WAN
config memberssettings, configuring thesourcefor the health check probes is still required. SD-WAN adds dedicated kernel routes (proto=17) for the health checks using the interface IP or source IP when specified. To view the kernel routes, usediagnose ip route list. -
Configure the static route:
config router static edit 2000 set dst 200.0.0.0 255.255.255.0 set distance 1 set sdwan-zone "virtual-wan-link" next end
To verify the configuration:
-
Verify the kernel routing table for 200.0.0.0/24:
# get router info kernel | grep -A 2 200.0.0.0/24 tab=254 vf=0 scope=0 type=1 proto=11 prio=1 0.0.0.0/0.0.0.0/0->200.0.0.0/24 pref=0.0.0.0 gwy=10.100.1.1 flag=14 hops=255 oif=13(port5) pref=1.1.1.1 gwy=10.100.1.5 flag=14 hops=254 oif=15(port7) pref=1.1.1.2 -
Verify the routing table for 200.0.0.0/24:
# get router info routing-table details 200.0.0.0/24 Routing table for VRF=0 Routing entry for 200.0.0.0/24 Known via "static", distance 1, metric 0, best * vrf 0 10.100.1.1, via port5, prefsrc 1.1.1.1 * vrf 0 10.100.1.5, via port7, prefsrc 1.1.1.2
-
Run a sniffer trace after some traffic passes.
-
When traffic leaves port5:
# diagnose sniffer packet any "host 200.0.0.1" 4 interfaces=[any] filters=[host 200.0.0.1] 6.592488 port5 out 1.1.1.1 -> 200.0.0.1: icmp: echo request 7.592516 port5 out 1.1.1.1 -> 200.0.0.1: icmp: echo request 8.592532 port5 out 1.1.1.1 -> 200.0.0.1: icmp: echo request
-
When traffic leaves port7:
# diagnose sniffer packet any "host 200.0.0.1" 4 interfaces=[any] filters=[host 200.0.0.1] 75.664173 port7 out 1.1.1.2 -> 200.0.0.1: icmp: echo request 76.664194 port7 out 1.1.1.2 -> 200.0.0.1: icmp: echo request
Traffic exiting each interface is sourced from the corresponding loopback IP.
-

