Testing and verification
Once the above configurations are completed, it is time to test ZTNA remote access on a workstation. Two test cases will be performed.
-
Verify access is denied when Critical Vulnerabilities are present on the PC.
-
Verify access is allowed when Critical Vulnerabilities are resolved, and user is logged into the FortiAD domain as a Domain User.
To verify access is denied:
-
On an administrator’s workstation, login to the FortiAD domain.
-
Open the FortiClient > Zero Trust Telemetry page.
-
Enter the EMS address or the invitation code. Connect to EMS.
-
Once EMS is connected, click the avatar to identify the current Zero Trust Tags assigned to this PC.

-
Open a browser, and enter the URL https://zfaz.ztnademo.com.
-
The browser will first prompt for the client certificate you want to use for this connection. Select the client certificate and press OK.

-
Next, the browser will prompt you for your user credentials. Enter your LDAP/Active Directory to continue.

-
If user authentication passes, the ZTNA rule will then assess the ZTNA tags. Since this workstation has Critical Vulnerabilities, access to the FortiAnalyzer is denied.

-
On the FortiGate, view the corresponding logs under Log & Report > ZTNA Traffic, or from the CLI:
# execute log filter category traffic
# execute log filter field subtype ztna
# execute log display
18 logs found.
10 logs returned.
1: date=2023-09-07 time=22:56:01 eventtime=1694152562128752275 tz="-0700" logid="0005000024" type="traffic" subtype="ztna" level="notice" vd="root" srcip=10.0.3.2 srcport=23006 srcintf="port3" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.0.3.10 dstport=443 dstintf="root" dstintfrole="undefined" sessionid=95357 srcuuid="24334ee0-4df0-51ee-c9e5-c9dcd0cfa2dc" dstuuid="8cbf3c68-f75d-51ea-4533-3cd1379a79dc" service="HTTPS" proxyapptype="http" proto=6 action="deny" policyid=1 policytype="proxy-policy" poluuid="d2e2ae4e-4e0a-51ee-037c-b6e9f4d86e25" policyname="ZTNA-Deny-Access" duration=1 user="tsmith" group="LDAP-Administrators" authserver="LDAP-fortiad" vip="ZTNA Webserver" accessproxy="ZTNA Webserver" clientdeviceid="9A016B5A6E914B42AD4168C066EB04CA" clientdevicemanageable="manageable" clientdevicetags="MAC_EMS1_ZTNA_all_registered_clients/EMS1_ZTNA_all_registered_clients/MAC_EMS1_ZTNA_Critical-Vulnerability" emsconnection="online" msg="Denied: proxy-policy action is deny. Matched tag: EMS1_ZTNA_Critical-Vulnerability" wanin=0 rcvdbyte=0 wanout=0 lanin=2554 sentbyte=2554 lanout=33288 fctuid="9A016B5A6E914B42AD4168C066EB04CA" appcat="unscanned" crscore=30 craction=131072 crlevel="high"3 logs found.
To verify access is allowed:
-
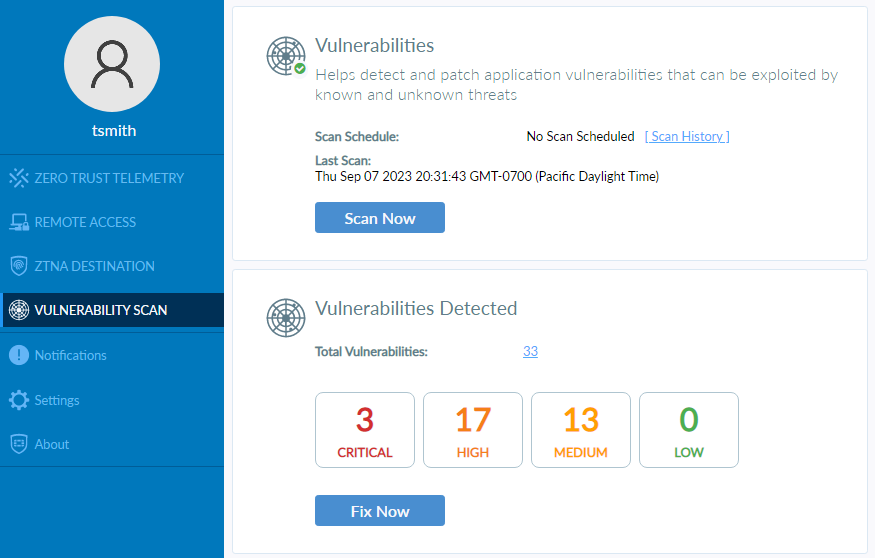
Open the FortiClient > Vulnerability Scan page.
-
Click on Critical to see the Application that has been identified with a critical vulnerability.

-
Apply the necessary fix to remove the vulnerability. Then perform a vulnerability scan.
-
Now that the workstation does not have a critical vulnerability, open your browser again to try accessing the FortiAnalyzer again.
-
Open a browser, and enter the URL https://zfaz.ztnademo.com.
-
If prior device certificate and user authentication are still valid, you will have access to your FortiAnalyzer right away. In not, select your device certificate and enter your user credentials. You should be able to access your FortiAnalyzer.

-
From the FortiGate, view the corresponding logs under Log & Report > ZTNA Traffic, or from the CLI:
# execute log filter category traffic
# execute log filter field subtype ztna
# execute log display
20 logs found.
10 logs returned.
1: date=2023-09-07 time=23:05:52 eventtime=1694153152135978887 tz="-0700" logid="0005000024" type="traffic" subtype="ztna" level="notice" vd="root" srcip=10.0.3.2 srcport=23114 srcintf="port3" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.88.0.2 dstport=443 dstintf="port2" dstintfrole="dmz" sessionid=95527 srcuuid="24334ee0-4df0-51ee-c9e5-c9dcd0cfa2dc" dstuuid="8cbf3c68-f75d-51ea-4533-3cd1379a79dc" service="HTTPS" proxyapptype="http" proto=6 action="accept" policyid=2 policytype="proxy-policy" poluuid="118ba452-4e0b-51ee-a7c9-6ab825e6b8ed" policyname="ZTNA-Administrators" duration=35 user="tsmith" group="LDAP-Administrators" authserver="LDAP-fortiad" gatewayid=1 vip="ZTNA Webserver" accessproxy="ZTNA Webserver" clientdeviceid="9A016B5A6E914B42AD4168C066EB04CA" clientdevicemanageable="manageable" clientdevicetags="MAC_EMS1_ZTNA_all_registered_clients/EMS1_ZTNA_all_registered_clients/MAC_EMS1_ZTNA_Domain-Users/EMS1_ZTNA_Domain-Users" emsconnection="online" wanin=653721 rcvdbyte=653721 wanout=14371 lanin=4108 sentbyte=4108 lanout=635085 fctuid="9A016B5A6E914B42AD4168C066EB04CA" appcat="unscanned"
-
Verify access to zfac.ztnademo.com.

