Overview
VNet
The virtual network (VNet) requires at least one subnet, which this document refers to as Subnet 1. Other subnets are optional.
- The required subnet is directly associated with FortiGate Autoscale.
- You deploy two FortiGate VMSSes into Subnet 1.
- You associate Subnet 1 with Port 1 on the FortiGate.
- You associate a network security group with Subnet 1.
The FortiGate autoscale deployment template can configure up to four subnets per FortiGate in the cluster.
- Each FortiGate initially has one network interface available per subnet.
- Additional subnets specified in the template are associated as ports 2, 3, and 4 as required on the FortiGate. The association of ports depends on the order in which the subnet is specified in the template.
- In a three-subnet deployment, port 2 points to the subnet with the lower number and port 3 points to the subnet with the higher number. The deployment does not use port 4.
- In a two-subnet deployment, port 2 points to the subnet. The deployment does not use ports 3 and 4.
- The following table describes example scenarios:
Scenario
Subnet parameter on the template
FortiGate port associations
Four-subnet deployment
Subnet 2: ✓
Subnet 3: ✓
Subnet 4: ✓
Port 2 points to subnet 2.
Port 3 points to subnet 3.
Port 4 points to subnet 4.
Three-subnet deployment
Subnet 2: ✓
Subnet 3: ✕
Subnet 4: ✓
Port 2 points to subnet 2.
Port 3 points to subnet 4.
Two-subnet deployment
Subnet 2: ✕
Subnet 3: ✕
Subnet 4: ✓
Port 2 points to subnet 4.
- FortiGate autoscale is only configured for the subnets specified in the VNet. Users can modify the VNet after the initial deployment. This case requires additional manual configuration.
- In a multiple subnet deployment scenario, using one network security group for Subnet 1 and another network security group for the other subnets is recommended.
You must create the autoscale resource group in the same region as the VNet resource group specified in the parameter VNet Resource Group Name.
Subnet 1 Network Security Group Rule Priority
This parameter refers to the highlighted area of the following image:
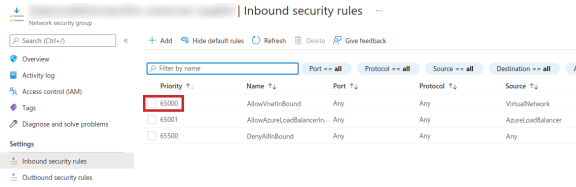
When using an existing VNet that has associated a network security group with Subnet 1 (the subnet that will be used to deploy the Autoscale VMSS) the network security group may already have existing rules. As the template deployment will add new rules to this network security group, specifying the Subnet 1 Network Security Group Rule Priority parameter can help users avoid potential rule conflicts. For details on setting the rule priority, refer to the Microsoft article Network security groups > Security rules.
FortiAnalyzer integration
When FortiAnalyzer integration is selected, a new FortiAnalyzer resource will be created in the VNet to be used by FortiGate Autoscale. As FortiGate Autoscale and the FortiAnalyzer are configured to work with each other, this FortiAnalyzer is not intended to be replaced.
FortiAnalyzer requires a public IP address resource to work with and the deployment defaults to creating a new resource.
Using an existing public IP address
By default, the deployment template will create a new public IP address for the FortiAnalyzer (if deploying with FortiAnalyzer integration) and the front-end load balancer. Specifying the ID of a public IP resource will associate the existing resource for use in the FortiGate Autoscale deployment.
To use an existing public IP address:
- Ensure the public IP address is available for use.
- Look up the Resource ID of the existing public IP resource. This is found in the Properties of the Azure resource.
- Specify the full Resource ID in the relevant parameter:
- For the FortiAnalyzer, specify the Resource ID in the parameter FortiAnalyzer Public IP Address ID.
- For the Front End Load Balancer, specify the Resource ID in the parameter Frontend IP Address ID.
|
|
Confirm the public IP resource quota before starting a deployment to ensure resource allocation is successful. Not enough IP address resources will result in deployment failures. |
|
|
The SKU of the public IP address for the FortiAnalyzer isn’t restricted. In comparison, the IP address for the external Load Balancer must be of the 'standard' SKU in order to match the VMSS. |
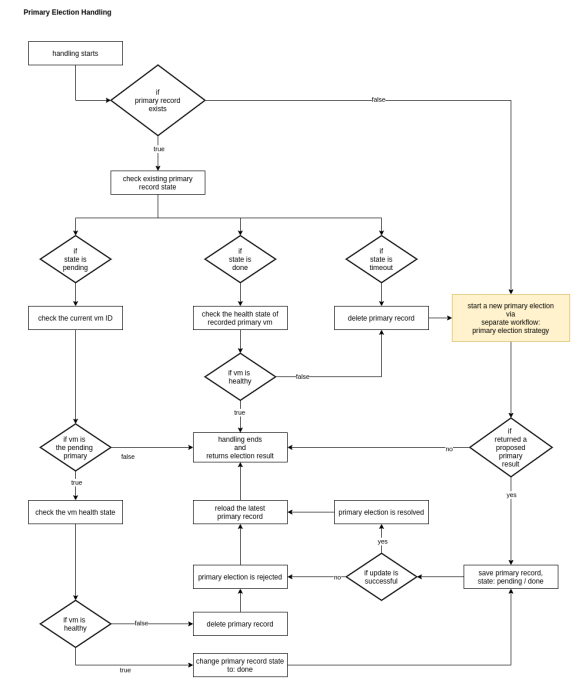
Election of the primary instance
A core feature of FortiGate Autoscale is the election of the primary instance. FortiGates in the VMSS are constantly monitored and if the conditions of the environment have changed, the election of a new primary instance may be required.
As the following flowchart depicts, a primary election happens when the following occur:
-
No primary record is found in the database
-
FortiGate noted in the primary record is deemed unhealthy
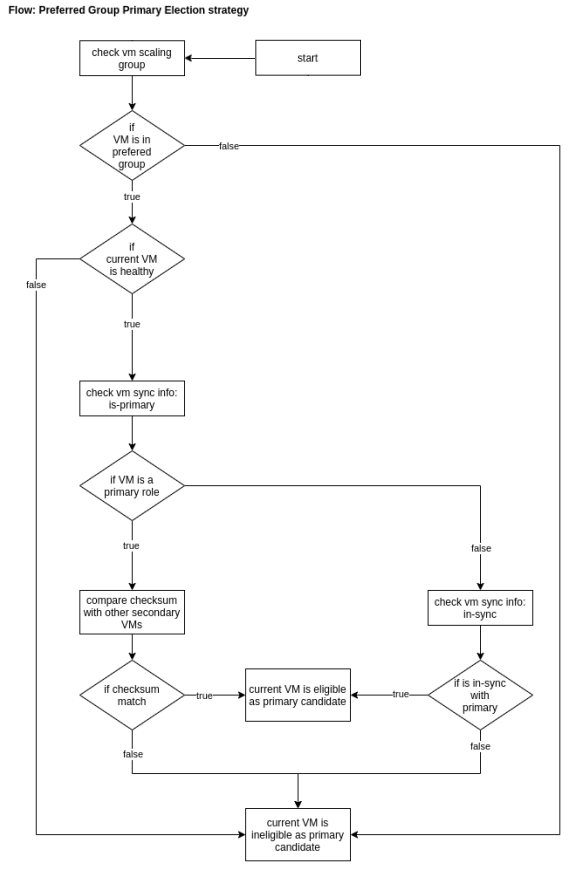
The following flowchart depicts preferred group primary election strategy:
Heartbeat
FortiGate Autoscale monitors the heartbeat sent from each FortiGate. The default heartbeat interval is 30 seconds, as defined by the parameter Heart Beat Interval.
To change the heartbeat interval after deployment:
- Locate the Settings item with key: heartbeat-interval. For details, refer to the section Modifying the Autoscale settings in Cosmos DB.
- Update the numeric value to the desired duration.
- Update the
auto-scale hb-intervalinterval on the primary FortiGate to match the value specified in the Cosmos DB using the following:config system auto-scaleset hb-interval <desired interval>end
Late heartbeat
The FortiGate sends heartbeats to the Autoscale handler via HTTPS. As such, network conditions may result in heartbeats arriving later than expected. When this happens, the heartbeat is considered a late heartbeat and the Heart Beat Loss Count will be increased by 1.
Heartbeat loss count
Any late heartbeat will increase the heartbeat loss count by 1. If this count reaches a defined threshold, the FortiGate will be deemed temporarily unhealthy. Any heartbeat arriving at the handler on time will reset the count to 0. The default heartbeat loss count is 10 (seconds) and is defined in the parameter Heart Beat Loss Count.
To change the heartbeat loss count after deployment:
- Locate the Settings item with key: heartbeat-loss-count. For details, refer to the section Modifying the Autoscale settings in Cosmos DB.
- Update the numeric value to the desired duration.
Heartbeat delay allowance
FortiGate Autoscale offsets a certain amount of network latency on the Internet with the parameter Heart Beat Delay Allowance. The default allowance is 2 seconds.
To change the heartbeat delay allowance after deployment:
- Locate the Settings item with key: heartbeat-delay-allowance. For details, refer to the section Modifying the Autoscale settings in Cosmos DB.
- Update the numeric value to the desired duration.
Unhealthy state and eligibility for primary role
A FortiGate-VM in an unhealthy state is excluded from participating in the election of the primary instance.
If the current primary FortiGate is deemed unhealthy, it will still work in the primary role until the next Primary Election, after which the primary role will be assigned to another eligible FortiGate and the previous primary FortiGate will change its role to secondary during its next heartbeat.
An unhealthy VM will stay running in the cluster in a secondary role until it recovers from the unhealthy state. This behavior does not cause any scaling activity to happen.
It takes some time, usually within one heartbeat interval, for each FortiGate to be individually notified about the new primary so the change of primary does not happen synchronously on every FortiGate but eventually they will be in-sync with the new primary.
Sync recovery count
FortiGate Autoscale helps an unhealthy FortiGate recover by counting the on-time heartbeats it sends. When the counter reaches the sync recovery count, the FortiGate is deemed healthy and is again eligible to be elected the primary instance.
To change the sync recovery count after deployment:
- Locate the Settings item with key: sync-recovery. For details, refer to the section Modifying the Autoscale settings in Cosmos DB.
- Update the numeric value to the desired duration.
Selecting the instance type
The Instance Type and FortiAnalyzer Instance Type parameters specify the FortiGate and FortiAnalyzer (optional) sizes. The string value entered in these parameters is created from the words of the size.
To select the instance type for FortiGate:
- Go to Fortinet FortiGate Next-Generation Firewall in Azure Marketplace.

- Click Get It Now.
- Click Continue.
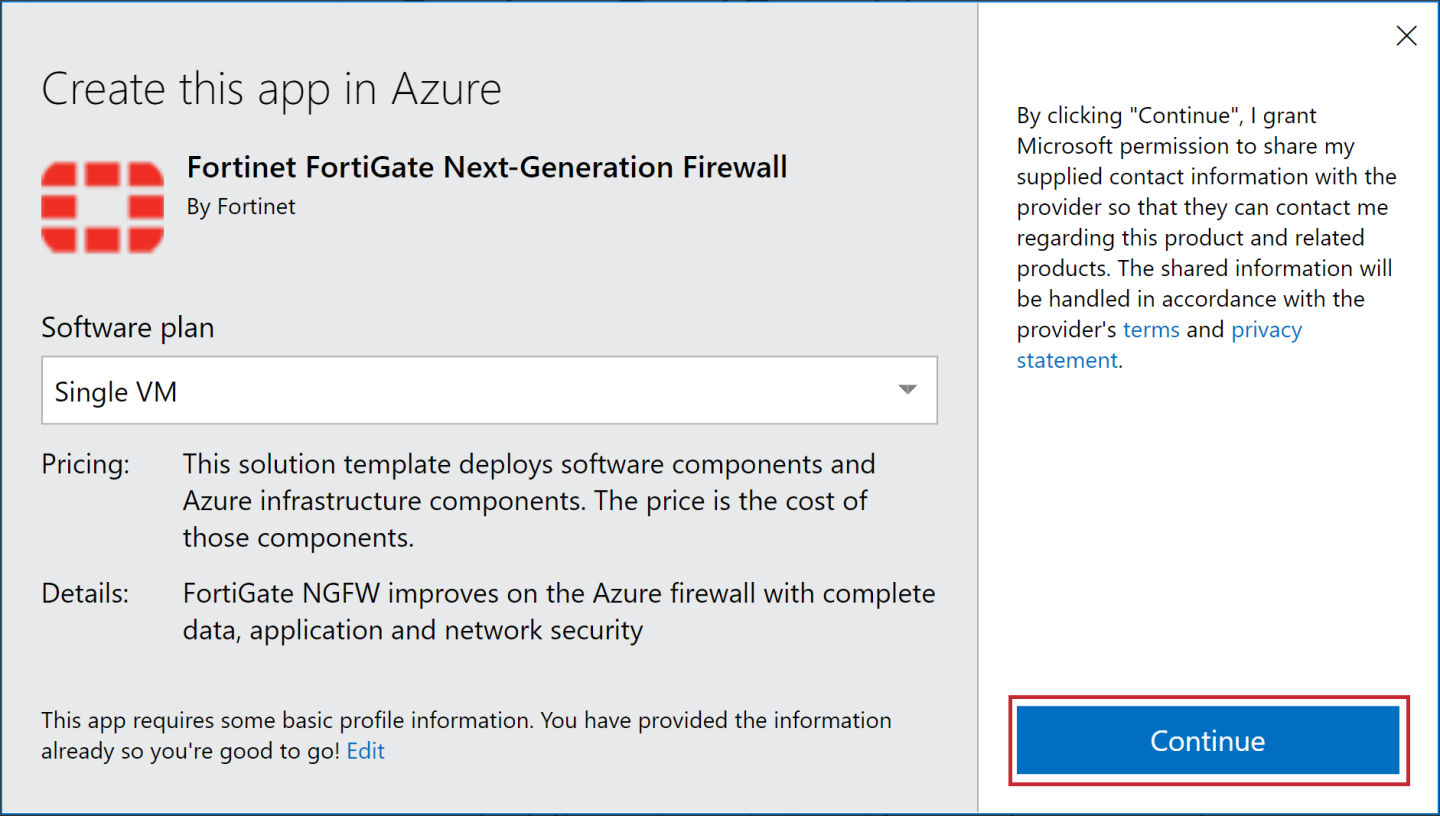
- Click Create using Plan: Single VM.
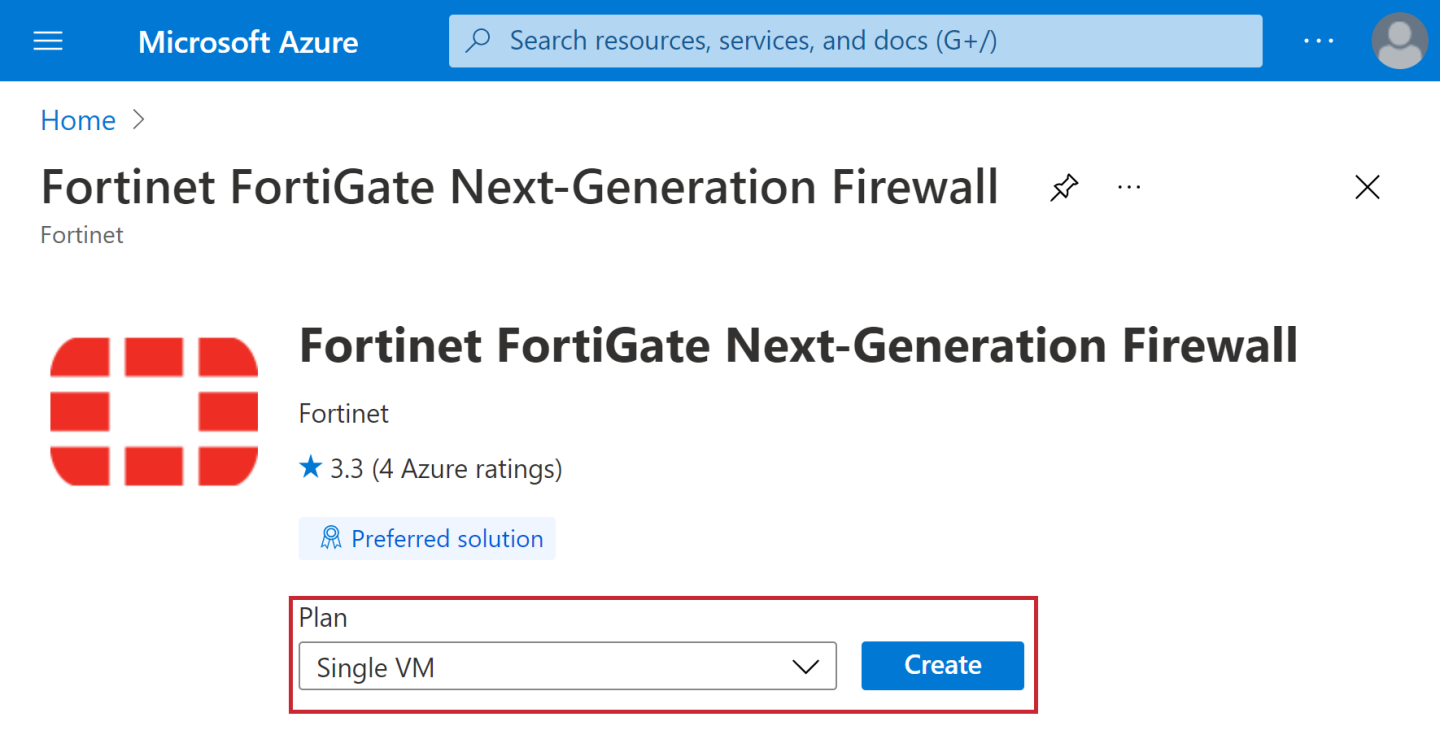
- Click Instance Type as illustrated.
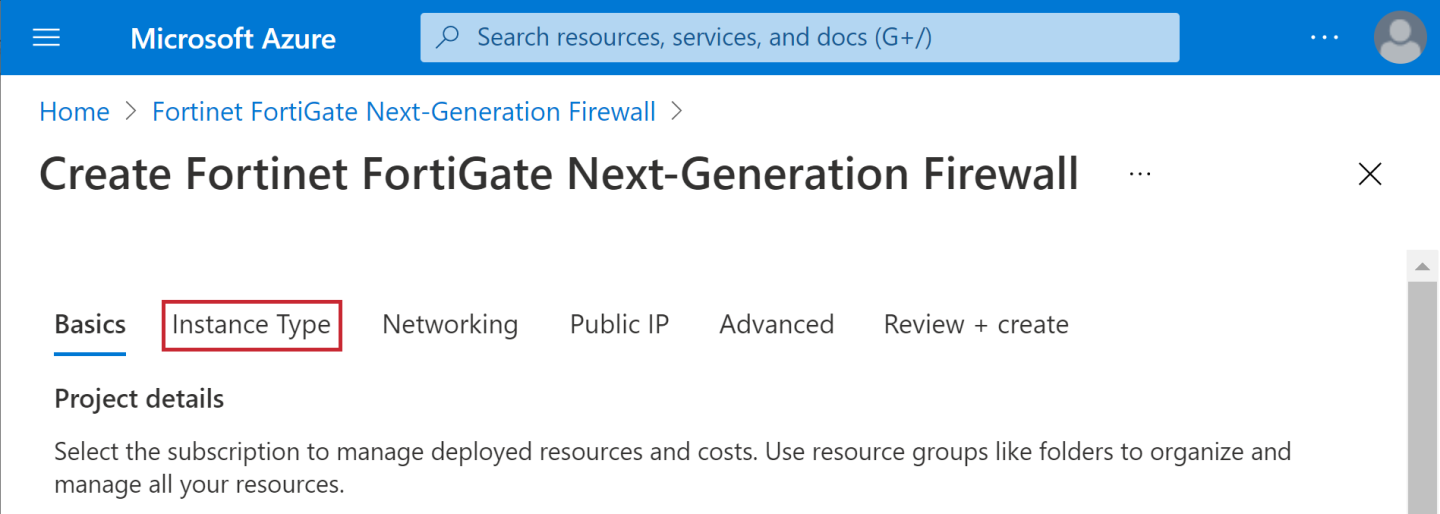
- Click Change size to view the full list of available Instance types.
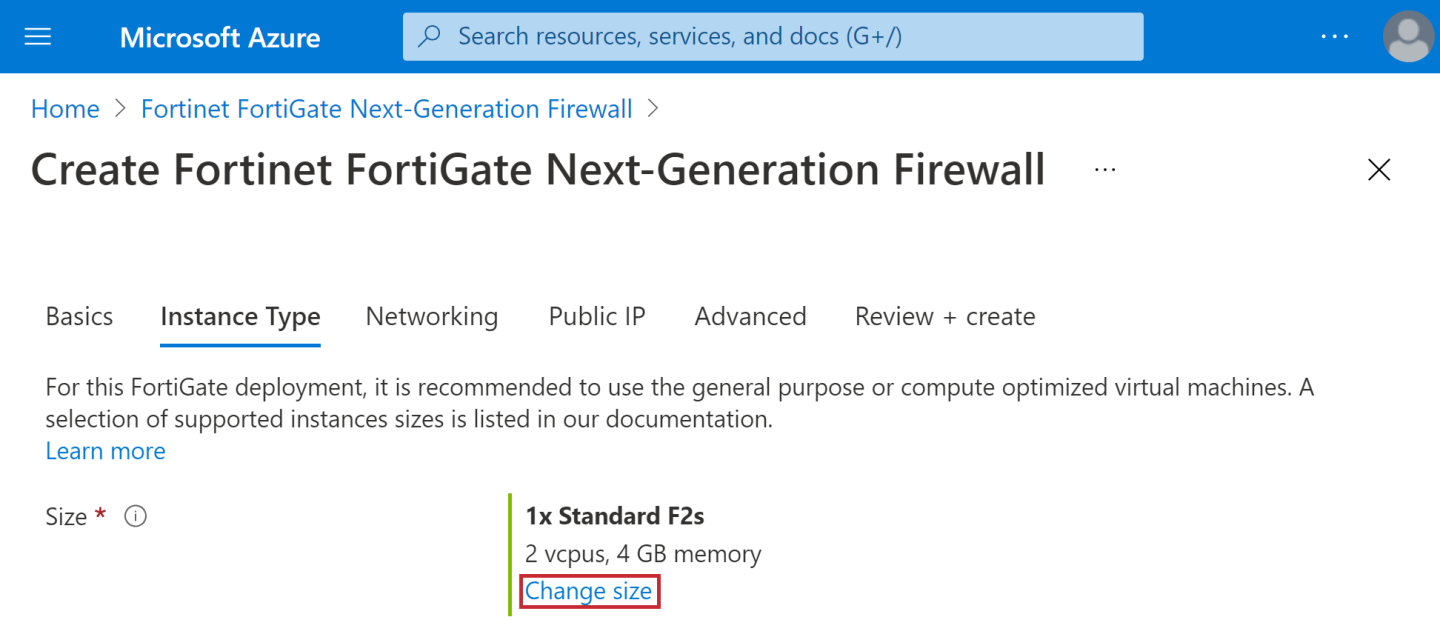
- Review the information and capacity of the VM sizes and select the best one for your deployment.

For BYOL VM sizes, users should also match the vCPU capacity of the selected Instance Type with the limit of the FortiGate license. Each license has a limit for the maximum number of vCPU per VM.
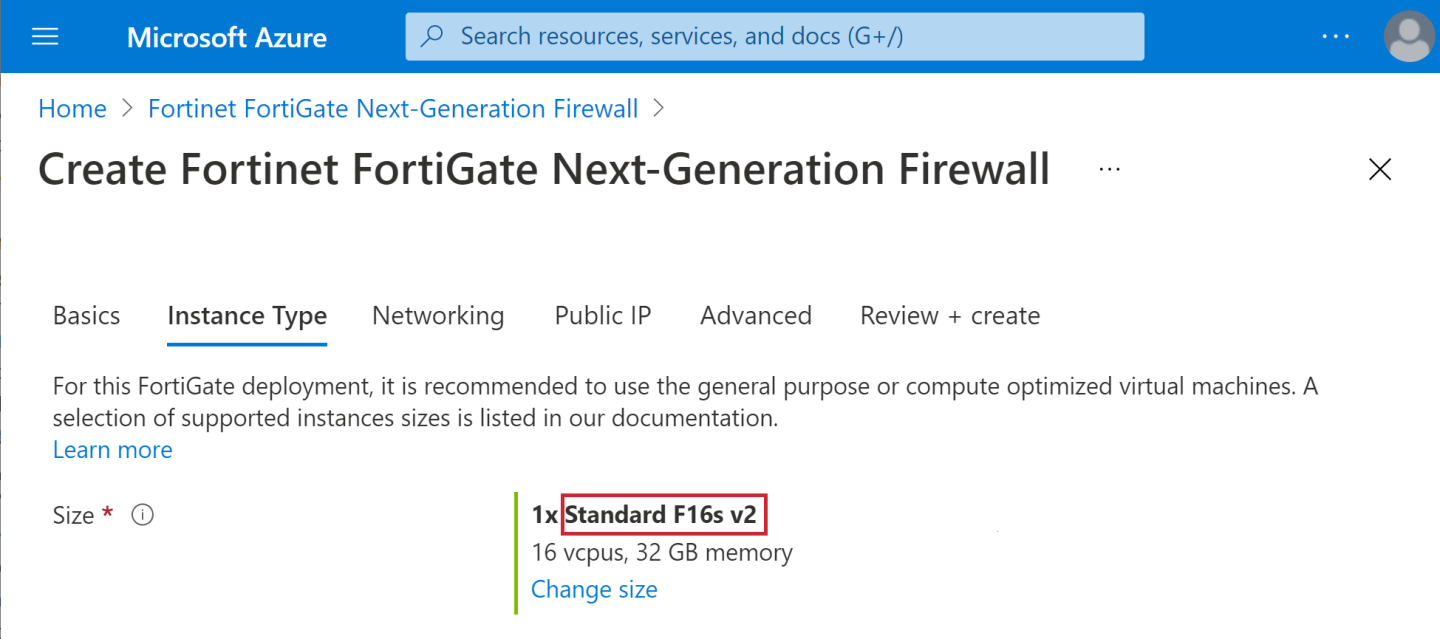
The following example selects F16s_v2.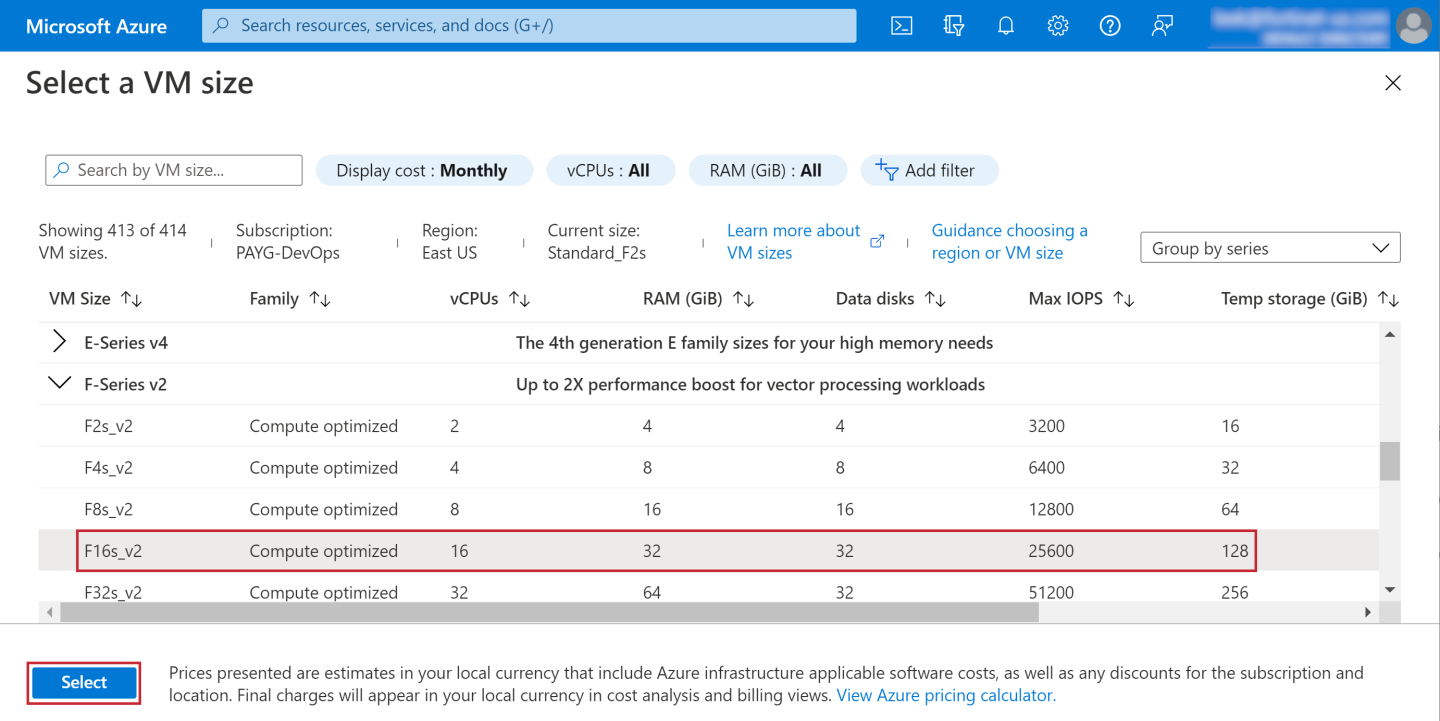
- Click Select.
To select the instance type for FortiAnalyzer:
- Go to FortiAnalyzer Centralized Log Analytics in Azure Marketplace.

- Click Get It Now.
- Click Continue.
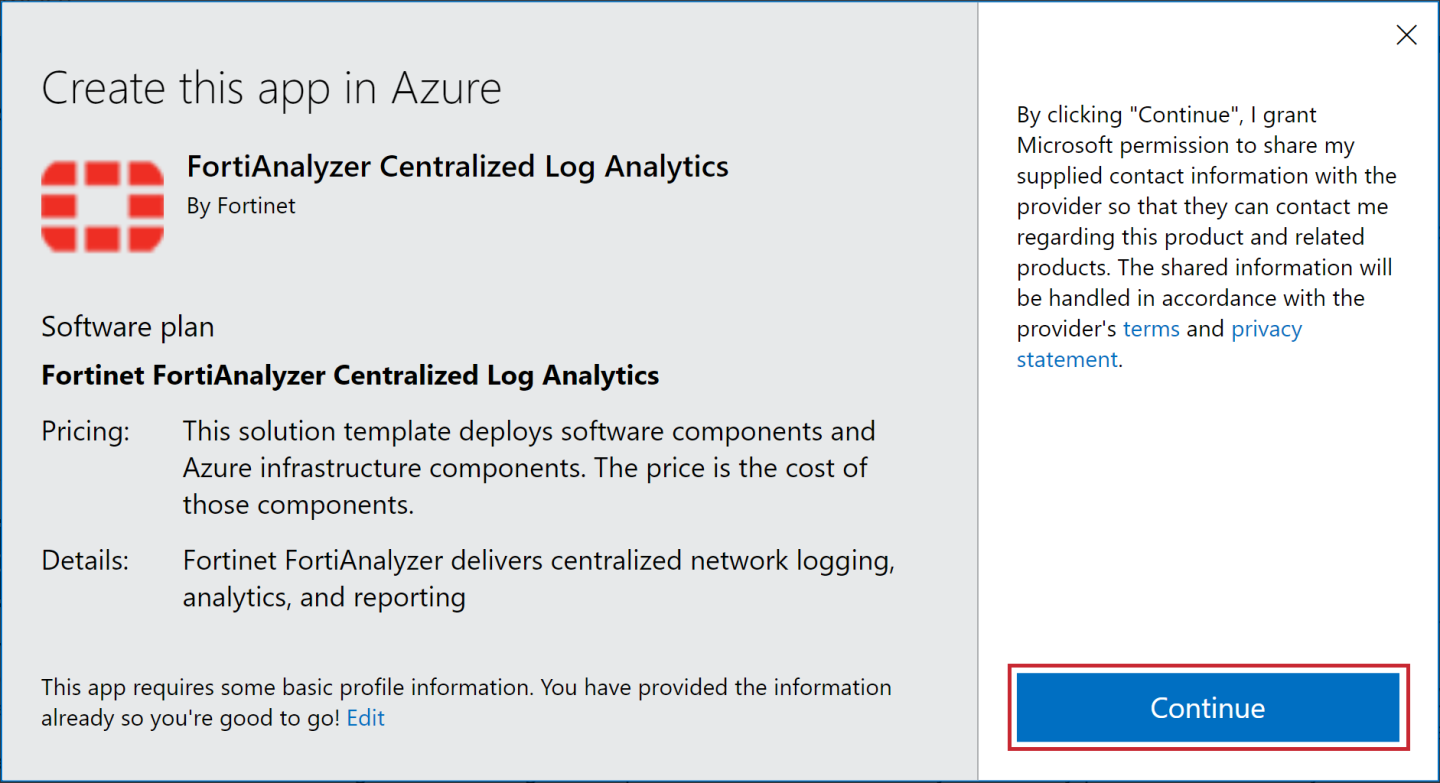
- Click Create.
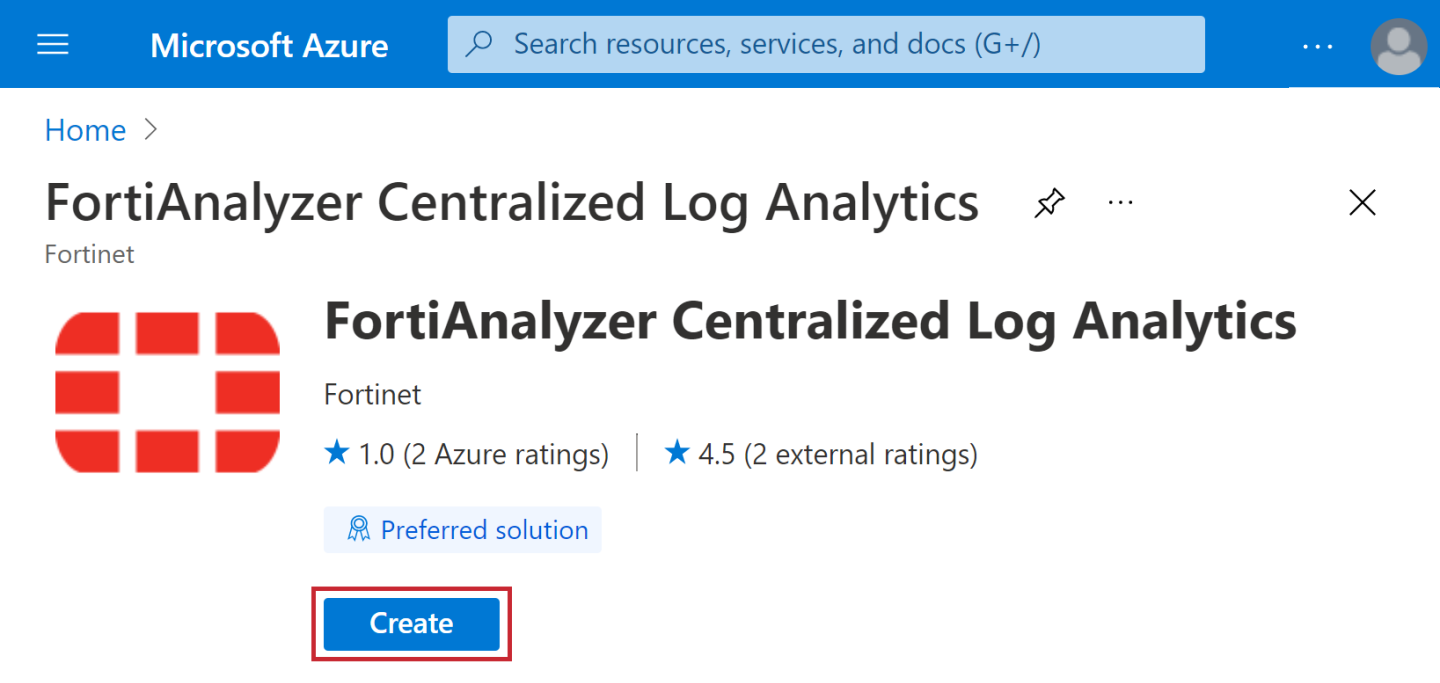
- Click Network and Instance Settings as illustrated.
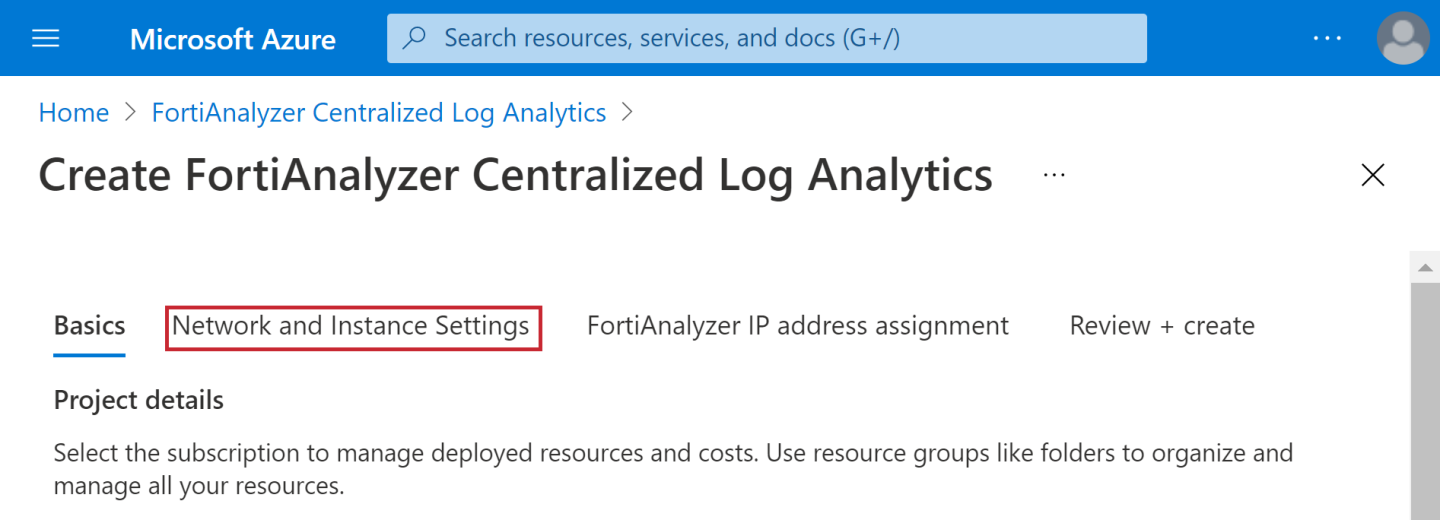
- Click Change size to view the full list of available instance types.
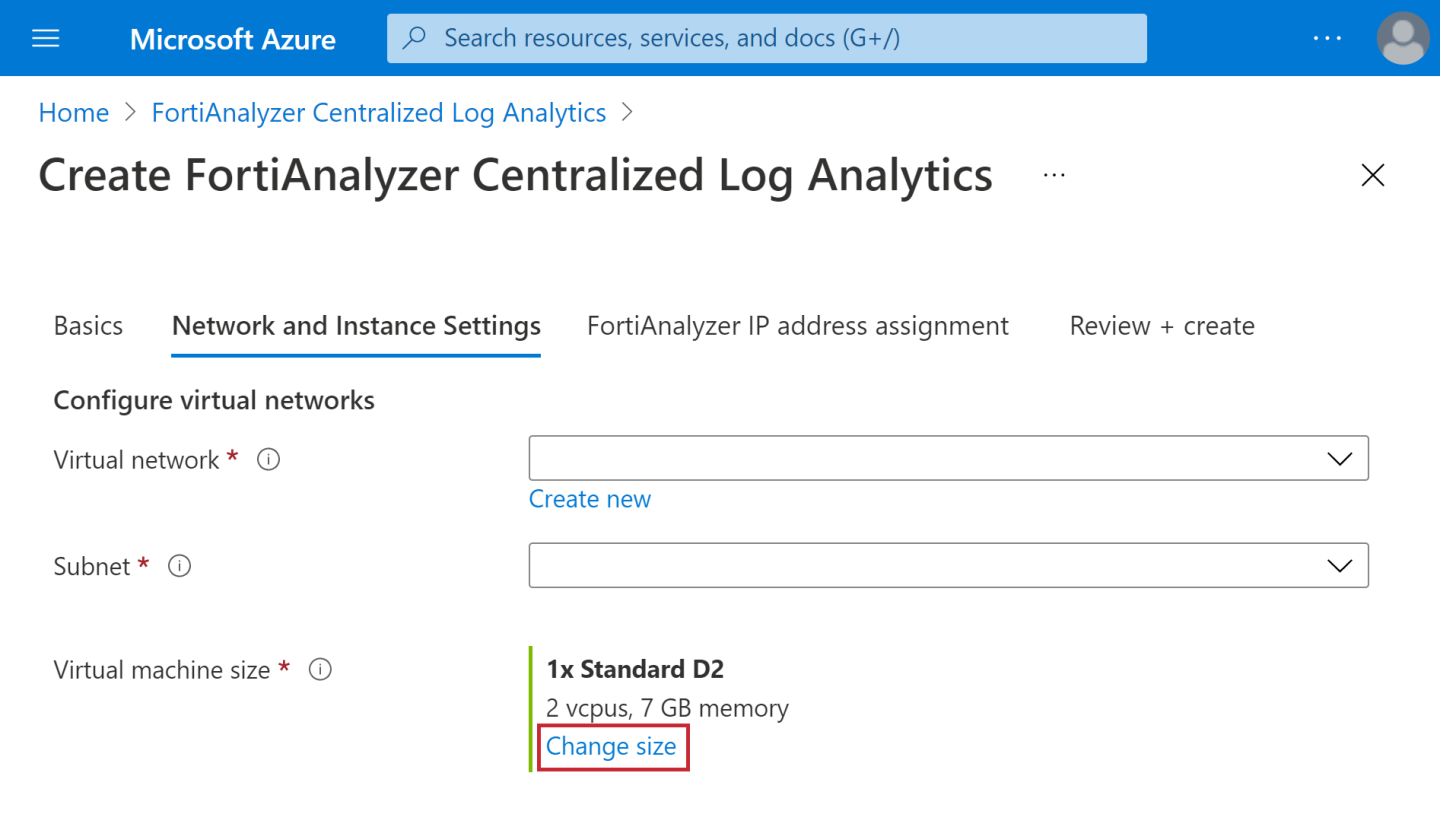
- Review the information and capacity of the VM sizes and select the best one for your deployment.

For BYOL VM sizes, users should also match the vCPU capacity of the selected Instance Type with their FortiGate License. The License has a limit for the maximum number of vCPU per VM. - Click Select.
To create the instance type string:
During the template deployment the FortiGate instance type is entered in the parameter Instance Type and the FortiAnalyzer instance type is entered in the parameter FortiAnalyzer Instance Type. The value of each instance type is constructed by creating a string by joining the words of the Size (Virtual machine size) with an underscore ( _ ). The following screenshot highlights these words. The constructed string for Standard F16s v2 is Standard_F16s_v2.