Automatically updating dynamic addresses using Calico FortiGate integration
When deploying a Kubernetes (K8s) cluster, you can install a third-party network policy provider. Calico is a popular provider that provides the necessary framework to protect and secure the network. The largest public cloud providers have selected Calico to provide network security for their hosted K8s services (Amazon EKS, Azure AKS, Google GKE, and IBM IKS) running across tens of thousands of clusters.
Through its Firewall Manager integration, Calico can effectively separate network controls and security controls. Operationally, this allows a company to assign security tasks to the Security Operations team using a familiar firewall such as the FortiGate and management tool such as FortiManager.
Nearly every application has dependencies external to K8s that require some level of access control, such as access requirements for database, third-party APIs, and cloud services.
Calico implements zone-based security in order to secure K8s workloads. For example, Internet-facing workloads run in the demilitarized zone, while other workloads for backend business logic may run in the trusted zone. These workloads are dynamic in nature and can be brought up/down and moved across nodes and clusters frequently. Therefore, a Firewall Manager must be informed of each dynamic address change to properly secure the workload.
See Extend FortiGate Firewalls to Kubernetes with Calico Enterprise in Tigera's documentation for the general workflow. Following is a high-level overview of the workflow:
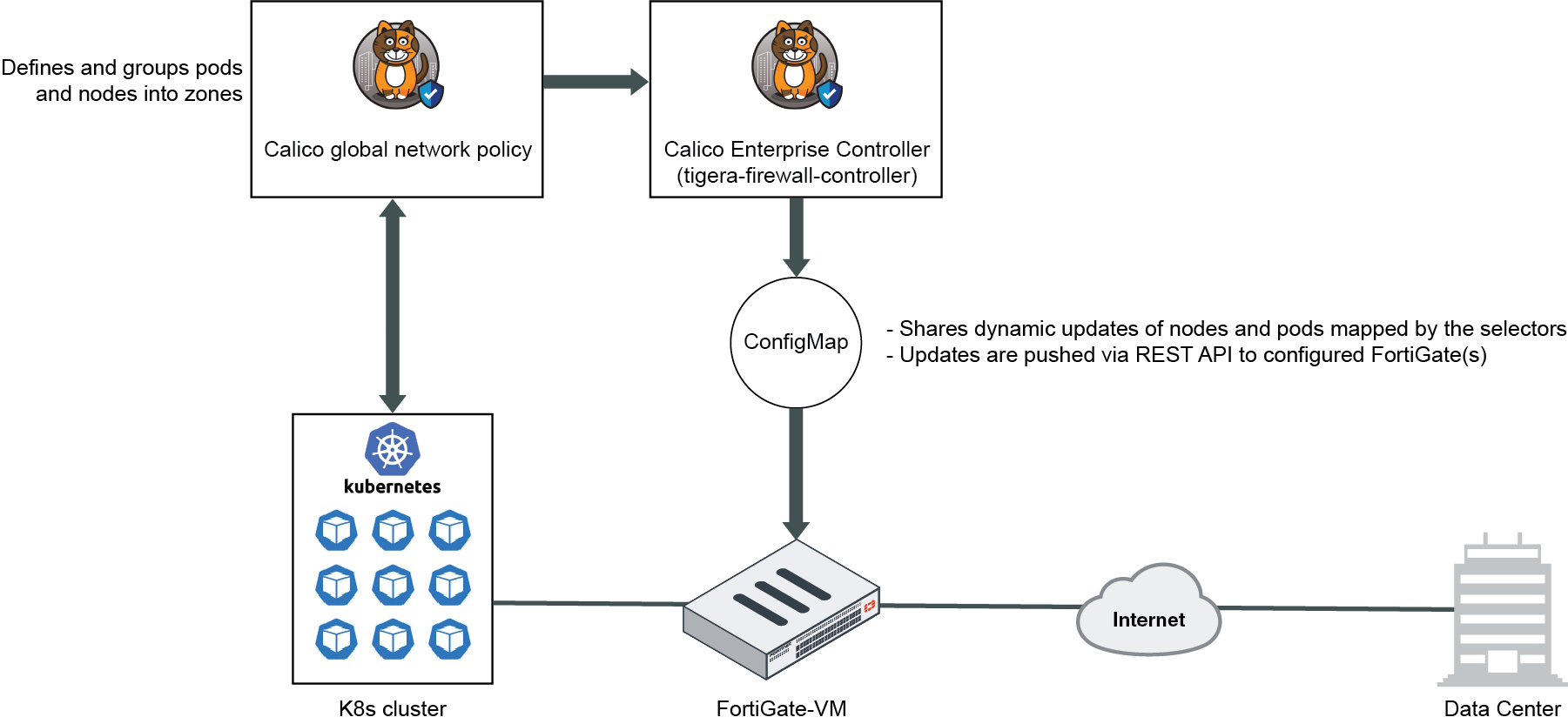
The Calico Enterprise Controller, also called tigera-firewall-controller, shares K8s node and pod addresses with FortiGate. The controller uses a ConfigMap to define the selectors for mapping the workloads to firewall address groups. The ConfigMap also defines the desired FortiGate(s)/FortiManager(s) to communicate with. The controller then pushes dynamic updates to the FortiGate(s) via REST API. Subsequently, traffic from the K8s cluster passes through the FortiGate, and you can administer zone-based security using firewall policies.
To configure automatically updating dynamic addresses using Calico FortiGate integration:
- Configure Calico assets as Extend FortiGate Firewalls to Kubernetes with Calico Enterprise describes.
- Configure a REST API administrator in FortiOS:
- Go to System > Administrators, then select Create New > REST API Admin.
- In the Username field, enter a username, such as calico_enterprise_api_user.
- If desired, enter comments.
- Creating a new administrator profile with minimal privileges is recommended. Create a new profile:
- From the Administrator Profile dropdown list, select Create.
- In the Name field, enter the desired name, such as tigera_api_user_profile.
- Under Access Permissions, configure the following:
- For Firewall, select Custom.
- For Address, select Read/Write. The REST API can send read and write requests (HTTP GET/POST/PUT/DELETE) to the resource.
- For all others, leave as None.
- Click OK.
- FortiOS displays an API key. Copy and store the key securely, as it is only shown once.
Once configuration is complete on the FortiGate and Calico, you see address objects being created on the FortiGate. When changes occur on your workloads, the address objects change as well. The address objects are marked with a “Managed by Tigera Calico Enterprise” comment.
With these new dynamic address groups, you can define firewall policies to deploy zone-based security for your K8s network.

