Introduce LAN extension mode for FortiExtender
LAN extension is a new configuration mode on the FortiGate that allows the FortiExtender to provide remote thin edge connectivity back to the FortiGate over a backhaul connection. The FortiExtender deployed at a remote location will discover the FortiGate access controller (AC) and form an IPsec tunnel (or multiple tunnels when multiple links exist on the FortiExtender) back to the FortiGate. A VXLAN is established over the IPsec tunnels to create an L2 network between the FortiGate and the network behind the remote FortiExtender.

In the following example, the FortiGate 501E is the FortiExtender AC that provides secure internet access to the remote network behind the FortiExtender 200F thin edge. The FortiGate 501E has two WAN connections: one is used as an inbound backhaul connection and the other for outbound internet access. The FortiExtender 200F has two wired WAN/uplink ports connected to the internet. Once the FortiExtender discovers the FortiGate AC and is authorized by the FortiGate, the FortiGate pushes an extender profile to the FortiExtender. From the profile, the extender uses the configurations to form two IPsec tunnels back to the FortiGate. Additional VXLAN aggregate interfaces are automatically configured to create an L2 network between the FortiExtender LAN port and a virtual LAN extension interface on the FortiGate. Clients behind the FortiExtender can now connect to the internet through the FortiGate that secures the internet connection.

Authorizing the devices
To discover and authorize the FortiExtender in the GUI:
- On the FortiGate, enable the Security Fabric connection on port3 to allow the FortiExtender to connect over CAPWAP:
- Go to Network > Interfaces and edit port3.
- In the Administrative Access section, select PING and Security Fabric Connection.
- Click OK.
- On the FortiExtender, connect to the CLI via SSH and set the AC server address to the FortiGate:
config system management set discovery-type fortigate config fortigate set ac-discovery-type static config static-ac-addr edit 1 set server 1.1.1.10 next end set ac-ctl-port 5246 set ac-data-port 25246 set discovery-intf port1 port2 set ingress-intf end endOnce the FortiExtender’s discovery packet reaches port3 on the FortiGate, the FortiExtender will appear under Network > FortiExtenders as unauthorized.

The FortiGate automatically creates a VPN profile for this FortiExtender, which appears on the VPN > IPsec Tunnels page.

The FortiGate also creates an extender profile for that model of FortiExtender, which appears on the Network > FortiExtenders > Profiles tab.

The FortiExtender profile is configured based on the FortiExtender model. It automatically selects Load Balance (as the Link load balance setting), the IPsec interface, and the pre-configured tunnel.

- Authorize the FortiExtender:
- Go to Network > FortiExtenders, select the Managed FortiExtenders tab, and edit the discovered FortiExtender.
- In the Status section, enable Authorized.

- Click OK. The device now displays as authorized.

To discover and authorize the FortiExtender in the CLI:
- On the FortiGate, enable the Security Fabric connection on port3 to allow the FortiExtender to connect over CAPWAP:
config system interface edit "port3" set vdom "root" set ip 1.1.1.10 255.255.255.0 set allowaccess ping fabric next end -
On the FortiExtender, connect to the CLI via SSH and set the AC server address to the FortiGate:
config system management set discovery-type fortigate config fortigate set ac-discovery-type static config static-ac-addr edit 1 set server 1.1.1.10 next end set ac-ctl-port 5246 set ac-data-port 25246 set discovery-intf port1 port2 set ingress-intf end end - The FortiGate discovers the FortiExtender and some basic configurations are automatically initialized in FortiOS:
config extension-controller extender edit "FX0035919000000" set id "FX200F5919000000" set device-id 0 set extension-type lan-extension set profile "FX200F-lanext-default" next end - An IPsec tunnel is automatically created for the detected FortiExtender:
config vpn ipsec phase1-interface edit "fext-ipsec-ksKS" set type dynamic set interface "port3" set ike-version 2 set peertype one set net-device disable set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1 set localid "localid-5bzuqs54dGni2TT0x2NePg0HexHW2piQ44aZ4NiGe8SVxxBnFuiqZqo" set dpd on-idle set comments "[FX200F-lanext-default] Do NOT edit. Automatically generated by extender controller." set peerid "peerid-svxVy5bZbPxZdfoIQBNA7YrkSKBA9Ui1vZsvYcVrgp1Uy0aFMCVZzGzh" set psksecret ENC <secret> set dpd-retryinterval 60 next end config vpn ipsec phase2-interface edit "fext-ipsec-ksKS" set phase1name "fext-ipsec-ksKS" set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256 aes128gcm aes256gcm chacha20poly1305 set comments "[FX200F-lanext-default] Do NOT edit. Automatically generated by extender controller." next end - A FortiExtender profile is created for the model of the detected FortiExtender:
config extension-controller extender-profile edit "FX200F-lanext-default" set id 0 set model FX200F set extension lan-extension config lan-extension set link-loadbalance loadbalance set ipsec-tunnel "fext-ipsec-ksKS" set backhaul-interface "port3" config backhaul edit "1" set port port1 next edit "2" set port port2 next end end - Authorize the FortiExtender:
config extension-controller extender edit "FX0035919000000" set authorized enable next end
Backhaul tunnel and VXLAN auto-deployment
Once the FortiExtender is authorized, the FortiGate immediately pushes the IPsec tunnel configuration to the extender. This forces the FortiExtender to establish the tunnel and form the VXLAN mechanism.
In the following diagram, the VXLANs are built on the IPsec tunnels between the FortiExtender and the FortiGate. The two VXLAN interfaces are aggregated to provide load balancing and redundancy. A softswitch is also used to combine the aggregate interface with the local LAN ports, which allows the LAN ports to be part of the VXLAN. This ultimately combines the local LAN ports with the virtual LAN extension interface on the FortiGate AC.
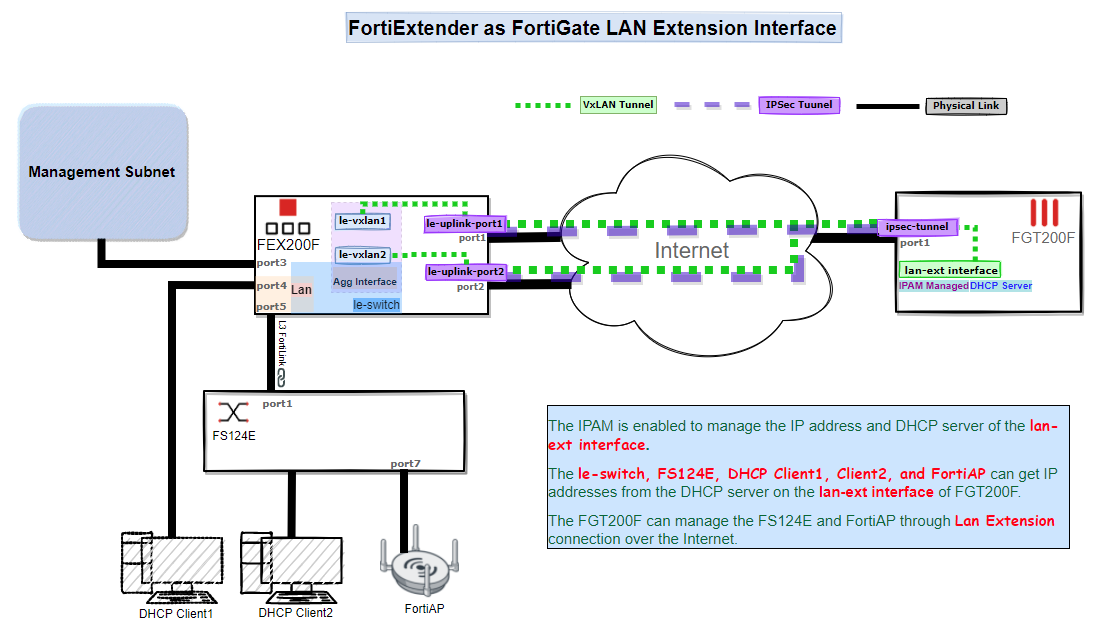
Underlying configurations that are automatically configured:
- The FortiExtender receives the IPsec configurations from the FortiGate and creates the corresponding tunnels for each uplink:
config vpn ipsec phase1-interface edit le-uplink-port1 set ike-version 2 set keylife 86400 set proposal aes128-sha256 aes256-sha256 3des-sha256 aes128-sha1 aes256-sha1 3des-sha1 set dhgrp 14 5 set interface port1 set type static set remote-gw 1.1.1.10 set authmethod psk set psksecret ****** set localid peerid-svxVy5bZbPxZdfoIQBNA7YrkSKBA9Ui1vZsvYcVrgp1Uy0aFMCVZzGzh set peerid localid-5bzuqs54dGni2TT0x2NePg0HexHW2piQ44aZ4NiGe8SVxxBnFuiqZqo set add-gw-route enable set dev-id-notification disable next edit le-uplink-port2 set ike-version 2 set keylife 86400 set proposal aes128-sha256 aes256-sha256 3des-sha256 aes128-sha1 aes256-sha1 3des-sha1 set dhgrp 14 5 set interface port2 set type static set remote-gw 1.1.1.10 set authmethod psk set psksecret ****** set localid peerid-svxVy5bZbPxZdfoIQBNA7YrkSKBA9Ui1vZsvYcVrgp1Uy0aFMCVZzGzh set peerid localid-5bzuqs54dGni2TT0x2NePg0HexHW2piQ44aZ4NiGe8SVxxBnFuiqZqo set add-gw-route enable set dev-id-notification disable next end - VXLAN interfaces are formed over each tunnel:
config system vxlan edit le-vxlan-port1 set vni 0 set remote-ip 10.252.0.1 set local-ip 10.252.0.2 set dstport 9999 next edit le-vxlan-port2 set vni 0 set remote-ip 10.252.0.1 set local-ip 10.252.0.3 set dstport 9999 next end - An aggregate interface is configured to load balance between the two VXLAN interfaces:
config system aggregate-interface edit le-agg-link set mode loadbalance set mapping-timeout 60 config members edit le-vxlan-port1 set interface le-vxlan-port1 set weight 1 set health-check-event le-agg-port1 set health-check-fail-cnt 5 set health-check-recovery-cnt 5 next edit le-vxlan-port2 set interface le-vxlan-port2 set weight 1 set health-check-event le-agg-port2 set health-check-fail-cnt 5 set health-check-recovery-cnt 5 next end next end - The softswitch bridges the aggregate interface and the local LAN to connect the LAN to the VXLAN bridged L2 network, which spans across to the FortiGate LAN extension interface:
config system switch-interface edit le-switch set members le-agg-link lan set stp disable next end
Configuring the LAN extension and firewall policy
Once the IPsec tunnel is set up and the VXLAN is created over the IPsec tunnel, the new LAN extension interface appears on the FortiGate.

To configure the LAN extension interface and firewall policy:
- Edit the LAN extension interface:
- Go to Network > Interfaces and edit the LAN extension interface.
Configure the IP/Netmask (9.9.9.99/255.255.255.0). Other devices on the remote LAN network will configure this as their gateway.
Optionally, enable DHCP Server to assign IPs to the remote devices using DHCP.
Click OK.
- Configure the firewall policy to allow traffic from the LAN extension interface to the WAN (port1):
- Go to Policy & Objects > Firewall Policy and click Create New.
- Enter the following:
Incoming Interface
FX0035919000000
Outgoing Interface
port1
Source
all
Destination
all
Schedule
always
Service
ALL
Action
ACCEPT
NAT
Enable (NAT)
- Configure the other settings as needed, such as security profiles.
- Click OK.
This policy allows the remote LAN clients to access the internet through the backhaul channel. Clients in the remote LAN behind the FortiExtender will now be able to receive an IP over DHCP and reach the internet securely through the FortiGate.

