FortiClient (macOS) VPN connection with FortiToken Mobile
Improvements have been made to the FortiClient (macOS) GUI when connecting SSL VPN using FortiToken Mobile (FTM) two-factor authentication (2FA). In the following example, a FortiClient endpoint connects via SSL VPN to a FortiGate with FTM AutoPush enabled.
For an SSL VPN user with FortiToken 2FA enabled, the SSL VPN connection prompt no longer displays an FTM push button. You can proceed with the VPN connection in one of the following ways:
- In the Connecting to VPN dialog, manually enter the FortiToken. Click OK.
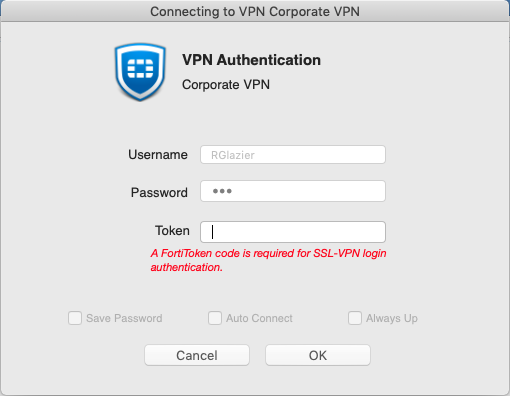
- On your mobile device, select Approve on the push notification that you received via your FTM application.

FortiClient sends the token to the FortiGate and the VPN connection establishes successfully.
To configure FortiOS:
The WAN interface is the interface connected to ISP. This example shows a configuration for static mode. You can also use DHCP or PPPoE mode. This example establishes the SSL VPN connection over the WAN interface.
- In the FortiOS GUI, configure the interface and firewall address. The port1 interface connects to the internal network:
- Go to Network > Interfaces and edit the wan1 interface.
- Set IP/Network Mask to 172.20.120.123/255.255.255.0.
- Edit the port1 interface and set IP/Network Mask to 192.168.1.99/255.255.255.0.
- Click OK.
- Go to Firewall & Objects > Address. Create an address for the Internet subnet 192.168.1.0.
-
Register the FortiGate for FortiCare Support. To add or download a mobile token on the FortiGate, you must register the FortiGate for FortiCare Support. If your FortiGate is registered, go to step 3.
- Go to Dashboard > Licenses.
- Hover the cursor on FortiCare Support to check if the FortiGate is registered for FortiCare. If not, click FortiCare Support, then click Register.
- Add FTM to the FortiGate. If your FortiGate has FortiToken installed, go to step 4.
- Go to User & Device > FortiTokens. Click Create New.
- Select Mobile Token.
- In the Activation Code field, enter the activation code.
- Every FortiGate has two free mobile tokens. Go to User & Device > FortiTokens and click Import Free Trial Tokens.
-
In the FortiOS CLI, enable FTM push. Ensure that server-ip is reachable from the Internet, then enter the following CLI commands:
config system ftm-push
set server-ip 172.20.120.123
set status enable
end

