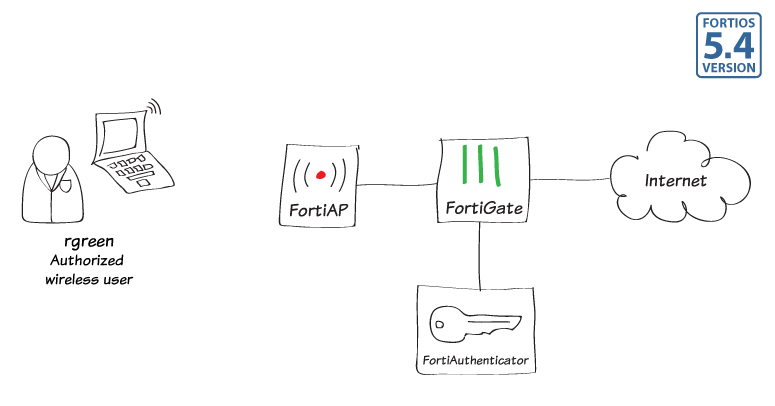
WiFi RADIUS authentication with FortiAuthenticator
In this example, you use a RADIUS server to authenticate your WiFi clients.
The RADIUS server is a FortiAuthenticator (v4.00-build0008) that is used authenticate users who belong to the employees user group.
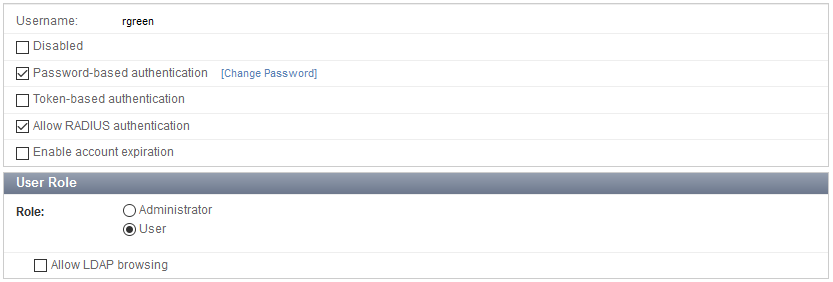
1. Create the user accounts and user group on the FortiAuthenticator
Go to Authentication > User Management > Local Users and create a user account.
User Role settings are available after you click OK.
Create additional user accounts as needed, one for each employee.
Go to Authentication > User Management > User Groups and create the local user group “employees” on the FortiAuthenticator.

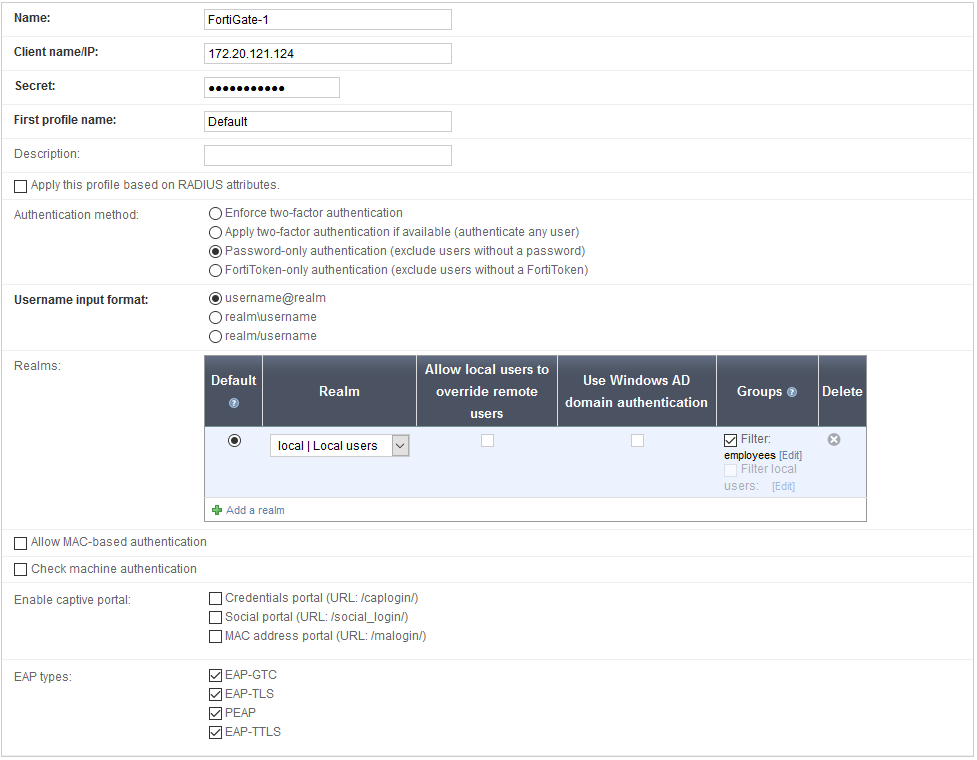
2. Register the FortiGate as a RADIUS client on the FortiAuthenticator
Go to Authentication > RADIUS Service > Clients and create a client account.
Enable all of the EAP types.
3. Configure FortiGate to use the RADIUS server
Go to User & Device > RADIUS Servers and add the FortiAuthenticator as a RADIUS server.

4. Create the SSID and set up authentication
Go to WiFi Controller > SSID and define your wireless network.

Set up DHCP for your clients.
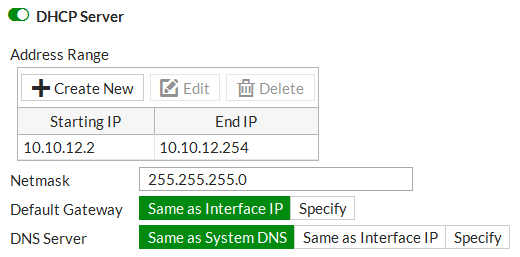
Configure WPA2 Enterprise security that uses the RADIUS server.
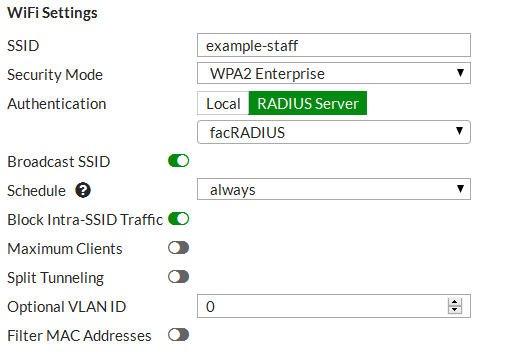
5. Connect and authorize the FortiAP
Go to Network > Interfaces and configure a dedicated interface for the FortiAP.

Connect the FortiAP unit. Go to WiFi Controller > Managed FortiAPs.
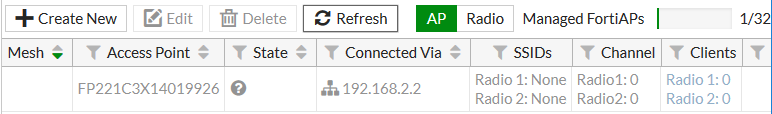
When the FortiAP is listed, select and authorize it.

Go to WiFi Controller > FortiAP Profiles and edit the profile.
This example used a FortiAP-221C, so the FAP221C-default profile applies.
For each radio:
- Enable Radio Resource Provision.
- Select your SSID.

6. Create the security policy
Go to Policy & Objects > IPv4 Policy and add a policy that allows WiFi users to access the Internet.
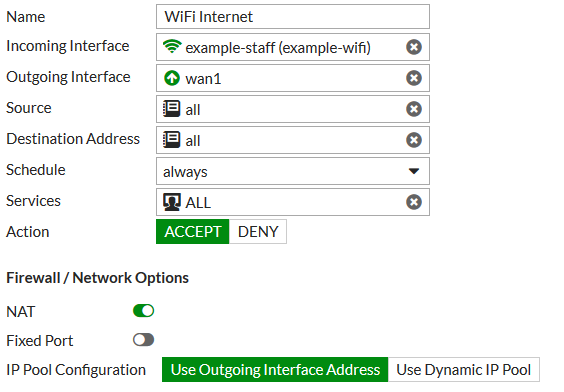
Results
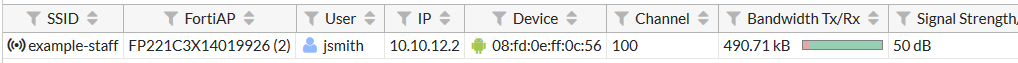
Connect to the example-staff network and browse Internet sites.
Go to Monitor > Client Monitor to see that clients connect and authenticate.