Configuring LDAP over SSL with Windows Active Directory
In this recipe you will learn how to configure LDAP over SSL (LDAPS) with Windows Server 2012. This external authentication server provides secure password checking for selected FortiGate users or groups.
The Lightweight Directory Access Protocol (LDAP) is used to read from Active Directory. By default, LDAP traffic is transmitted unsecured. You can make LDAP traffic confidential and secure by using Secure Sockets Layer (SSL).
The goal is to generate and export a CA certificate from the AD server, then import it, as an external CA certificate, into the FortiGate. Finally, enable the CA certificate in the LDAPS server object.
Active Directory Certificate Services (AD CS) must be installed in your Windows Server 2012.

1. Exporting the LDAPS Certificate in Active Directory (AD)
Open the Command Prompt, type mmc and hit enter. Select File and then click Add/Remove Snap-in. Select Certificates and then click Add. In Certificates snap-in select Computer account and then click Next.

In Select Computer, if you are working at the LDAP server requiring the certificate, select Local. Otherwise, select Another computer and click Browse to locate the LDAP server requiring the certificate. Once you have the correct computer selected, click OK and then click Finish.

In the console tree, expand Certificates (<computer>). In the certificates console of a computer that contains a certificate that can be used for Certificate Signing, right-click the CA certificate, click All Tasks, and then click Export.

On the Certificate Export Wizard welcome screen, click Next. On the Export Private Key screen, select No, then click Next.

On the Export File Format screen, select DER.

On the File to Export screen, enter a path, file name, and .cer file extension in the File name box and then click Next. Confirm the settings on the completion screen and then click Finish. You should see a pop-up message indicating that the export was successful. Click OK.

2. Importing the LDAPS Certificate into the FortiGate
Go to System > Config > Features, and enable Certificates.

Go to System > Certificates and select Import > CA Certificate. Select Local PC and Choose File, then browse for certificate file and click OK.

You may rename the system-generated CA_Cert_1 to be more descriptive.
CLI Example:
FGT # config vpn certificate ca FGT (ca) # rename CA_Cert_1 to LDAPS-CA FGT (ca) # end
The Name under External CA Certificates now shows as LDAPS-CA.

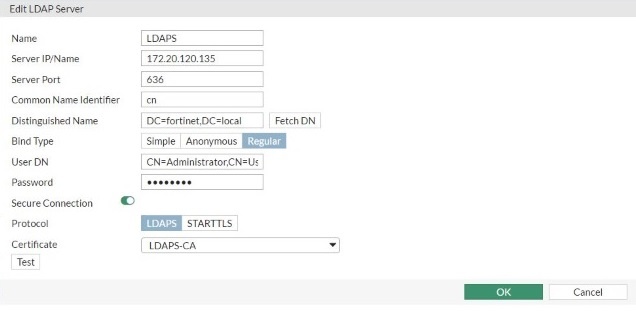
3. Creating the LDAPS Server object in the FortiGate
User DN must have server administrator access.
4. Results
Verifying that the LDAPS Server object is authenticating correctly.
On the FortiGate use the following diagnose command to test authenticating with the LDAPS server. When you enter the command use an actual username and password on the LDAPS server (in the example administrator and pa$$w0rd). If everything is configured correctly, the command output should indicate that authentication has succeeded and also list the group memberships.
FGT # diagnose test authserver ldap LDAPS administrator pa$$w0rd
authenticate 'administrator' against 'LDAPS' succeeded!
Group membership(s) - CN=Domain Admins,CN=Users,DC=fortinet,DC=local
CN=Administrators,CN=Builtin,DC=fortinet,DC=local
CN=Domain Users,CN=Users,DC=fortinet,DC=local

