About the connector
Fortinet FortiGate enterprise firewall provide high performance, consolidated advanced security and granular visibility for broad protection across the entire digital attack surface.
This document provides information about the Fortinet FortiGate Connector, which facilitates automated interactions, with a Fortinet FortiGate server using FortiSOAR™ playbooks. Add the Fortinet FortiGate Connector as a step in FortiSOAR™ playbooks and perform automated operations with Fortinet FortiGate.
Version information
Connector Version: 5.2.3
FortiSOAR™ Version Tested on: 7.4.0-3024
Fortinet FortiGate Version Tested on: FortiGate VM64 v7.2.3 build1262
Authored By: Fortinet
Certified: Yes
Release Notes for version 5.2.3
Following enhancements have been made to the Fortinet FortiGate Connector in version 5.2.3:
- Added support for policy based blocking and unblocking IP addresses.
- Added
NGFW Mode parameter in following actions:
- Get Blocked IP Addresses
- Block IP Address
- Unblock IP Address
- Get List of Policies
- Added a new Never option for Time to Live parameter in Block IP Address action to ban IP addresses permanently.
Installing the connector
Use the Content Hub to install the connector. For the detailed procedure to install a connector, click here.
You can also use the yum command as a root user to install the connector:
yum install cyops-connector-fortigate-firewall
Prerequisites to configuring the connector
- You must have the IP address or Hostname of the Fortinet FortiGate server to connect and perform the automated operations and the API Key to access that server.
- The FortiSOAR™ server should have outbound connectivity to port 443 on Fortinet FortiGate.
- To block or unblock IP addresses, URLs, or applications, you need to add the necessary configuration to Fortinet FortiGate. See the Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate section.
- VDOM is configured using a network interface in FortiGate which has its own IP address with different subnets (separate from global or root VDOM). When users select VDOM in the connector Configuration, users should specify the VDOM interface IP in the Hostname section, otherwise, an
Unauthorized Error is encountered. See the following screenshots for VDOM-specific connector configuration:
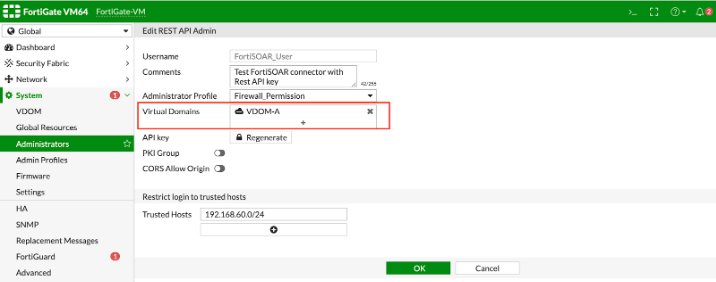
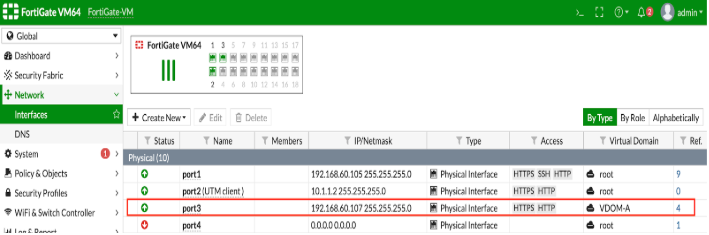
Minimum Permissions Required
- Ensure the user has the permissions required for the actions you wish to perform on Fortinet FortiGate.
- To execute Fortinet FortiGate connector actions, the following minimal profile permissions are required:
- User and Device: Read and Write permissions.
- Firewall: Read and Write permissions for Policy, Address, and Service.
- Security Profile: Read and Write permissions for Web Filter and Application Control.
- Security Fabric - Read and Write permissions.
- WiFi & Switch - Read and Write permissions.
- Log & Report - Read and Write permissions.
Configuring the connector
For the procedure to configure a connector, click here
Configuration parameters
In FortiSOAR™, on the Connectors page, click the Fortinet FortiGate connector row (if you are in the Grid view on the Connectors page) and in the Configurations tab enter the required configuration details:
| Parameter |
Description |
| Hostname |
IP address or Hostname of the Fortinet FortiGate endpoint server to connect and perform the automated operations. |
| API Key |
API Key of the Fortinet FortiGate endpoint server to connect and perform the automated operations. You can get the API key from the administration settings in FortiGate. Important:To create a REST API key from Fortinet FortiGate, see the "Create a REST API administrator" section in the Fortinet FortiGate Documentation. |
| Port |
Port number used for connecting to the Fortinet FortiGate server. Defaults to 443. |
| Web Filter Profile Name |
Name of the Web Filter Profile that you have specified on Fortinet FortiGate for blocking or unblocking IP addresses. Based on our example, enter default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in the Fortinet FortiGate section. |
| Application Control Profile Name |
Name of the Application Control Profile that you have specified on Fortinet FortiGate for blocking or unblocking IP addresses. Based on our example, enter default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in the Fortinet FortiGate section. |
| VDOM |
VDOMs, in the CSV or List format, if the VDOM mode is enabled. |
| Verify SSL |
Specifies whether the SSL certificate for the server is to be verified or not.
By default, this option is set as True. |
Actions supported by the connector
The following automated operations can be included in playbooks and you can also use the annotations to access operations from FortiSOAR™ release 4.10.0 and onwards:
| Function |
Description |
Annotation and Category |
| Get Applications Detail |
Retrieves a list of all application names and associated details from the Fortinet FortiGate server. |
get_app_details
Investigation |
| Get Blocked IP Addresses |
Retrieves a list of IP Addresses that are blocked on Fortinet FortiGate. |
get_blocked_ip
Investigation |
| Get Blocked Applications |
Retrieves a list of application names that are blocked on Fortinet FortiGate. |
get_blocked_app
Investigation |
| Get Blocked URLs |
Retrieves a list of URLs that are blocked on Fortinet FortiGate. |
get_blocked_url
Investigation |
| Block IP Address |
Blocks IP addresses on Fortinet FortiGate using the IPv4 Block Policy that you have specified as the "action" parameter of Fortinet FortiGate or by Quarantine based- adds IP into the banned IP list. For more information see the "Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate" section. |
block_ip
Containment |
| Block Application |
Blocks applications on Fortinet FortiGate using the Application Control Profile Name that you have specified while configuring Fortinet FortiGate. For more information see the "Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate" section. |
block_app
Containment |
| Block URL |
Blocks URLs on Fortinet FortiGate using the Web Filter Profile Name Policy that you have specified while configuring Fortinet FortiGate. For more information see the "Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate" section. |
block_url
Containment |
| Unblock IP Address |
Unblocks IP addresses on Fortinet FortiGate using the IPv4 Block Policy that you have specified as the "action" parameter of Fortinet FortiGate. For more information see the "Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate" section. |
unblock_ip
Remediation |
| Unblock Application |
Unblocks applications on Fortinet FortiGate using the Application Control Profile Name that you have specified while configuring Fortinet FortiGate. For more information see the "Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate" section. |
unblock_app
Remediation |
| Unblock URL |
Unblocks URLs on Fortinet FortiGate using the Web Filter Profile Name that you have specified while configuring Fortinet FortiGate. For more information see the "Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate" section. |
unblock_url
Remediation |
| Quarantine Host |
Quarantines hosts on the Fortinet FortiGate server based on MAC addresses and other input parameters you have specified |
quarantine_host
Containment |
| Unquarantine Host |
Unquaratines host entries from the Fortinet FortiGate server based on MAC addresses and other input parameters you have specified. |
unquarantine_host
Containment |
| Get Quarantine Hosts |
Retrieves a list of all quarantine hosts from Fortinet FortiGate. |
get_quarantine_hosts
Investigation |
| Create Address |
Create a new address on Fortinet FortiGate based on the name of the address, type, and other input parameters you have specified. |
create_address
Investigation |
| Get Addresses |
Retrieves a list of all addresses or specific addresses that are configured on Fortinet FortiGate based on the input parameters you have specified. |
get_addresses
Investigation |
| Update Address |
Update an existing address on Fortinet FortiGate based on the address name, type, and other input parameters you have specified. |
update_address
Investigation |
| Delete Address |
Deletes an address that is configured on Fortinet FortiGate based on the name of the address and other input parameters you have specified |
delete_address
Investigation |
| Create Address Group |
Creates a new address group on Fortinet FortiGate based on the name of the address group, members of the group, and other input parameters you have specified. |
create_address_group
Investigation |
| Get Address Groups |
Retrieves a list of all address groups or specific address groups that are configured on Fortinet FortiGate based on the input parameters you have specified. |
get_address_groups
Investigation |
| Update Address Group |
Updates an existing address group on Fortinet FortiGate based on the name of the address group, members of the group, and other input parameters you have specified. |
update_address_group
Investigation |
| Delete Address Group |
Deletes an address group that is configured on Fortinet FortiGate based on the name of the address group and other input parameters you have specified. |
delete_address_group
Investigation |
| Create Service |
Create a new service on Fortinet FortiGate based on the name of the service and other input parameters you have specified. |
create_firewall_service
Investigation |
| Get Services |
Retrieves a list of all firewalls services or specific services that are configured on Fortinet FortiGate based on the input parameters you have specified |
get_firewall_services
Investigation |
| Update Service |
Creates an existing service on Fortinet FortiGate based on the name of the service and other input parameters you have specified |
update_firewall_service
Investigation |
| Delete Service |
Deletes a firewall service that is configured on Fortinet FortiGate based on the name of the address group and other input parameters you have specified. |
delete_firewall_service
Investigation |
| Create Service Group |
Creates a new service group on Fortinet FortiGate based on the name of the service group, members of the group, and other input parameters you have specified. |
create_service_group
Investigation |
| Get Service Groups |
Retrieves a list of all service groups or specific service groups that are configured on Fortinet FortiGate based on the input parameters you have specified. |
get_service_groups
Investigation |
| Update Service Group |
Updates an existing service group on Fortinet FortiGate based on the name of the service group, members of the group, and other input parameters you have specified. |
update_service_group
Investigation |
| Delete Service Group |
Deletes a service group that is configured on Fortinet FortiGate based on the name of the service group and other input parameters you have specified |
delete_service_group
Investigation |
| Create Policy |
Creates a new firewall policy on Fortinet FortiGate based on the name of the policy, names of the incoming and outgoing interfaces, and other input parameters you have specified. |
create_policy
Investigation |
| Get List of Policies |
Retrieves a list and details for all IPv4 policies or specific IPv4 policies that are configured on Fortinet FortiGate based on the input parameters you have specified |
get_policies
Investigation |
| Update Policy |
Updates an existing firewall policy on Fortinet FortiGate based on the ID of the policy, names of the incoming and outgoing interfaces, and other input parameters you have specified. |
update_policy
Investigation |
| Delete Policy |
Deletes a policy that is configured on Fortinet FortiGate based on the ID of the policy and other input parameters you have specified. |
delete_policy
Investigation |
| Execute Command |
Executes a CLI command on the FortiOS console based on the commands and other input parameters you have specified. |
execute_command
Investigation |
| Create User |
Creates a new user in the Fortinet FortiGate server based on the username, authentication type, and other input parameters you have specified. |
create_user
Investigation |
| Get Users |
Retrieves a list of all users that are configured on Fortinet FortiGate based on the input parameters you have specified. |
get_users
Investigation |
| Update User |
Updates an existing user in the Fortinet FortiGate server based on the username, authentication type, and other input parameters you have specified. |
update_user
Investigation |
| Delete User |
Deletes a user who is configured on Fortinet FortiGate based on the name of the user you have specified. |
delete_user
Investigation |
| Get System Events |
Retrieves system log data from the Fortinet FortiGate server, based on the input parameters you have specified |
get_system_events
Investigation |
| Get User Last Login Details |
Retrieves the last login details for a specified user from the Fortinet FortiGate server, based on the username you have specified. |
get_user_list_login_details
Investigation |
operation: Get Applications Detail
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"status": "",
"http_status": "",
"http_method": "",
"results": [
{
"q_origin_key": "",
"q_name": "",
"protocol": "",
"q_type": "",
"q_path": "",
"id": "",
"category": "",
"q_ref": "",
"q_no_rename": "",
"sub-category": "",
"risk": "",
"metadata": [
{
"id": "",
"q_origin_key": "",
"metaid": "",
"valueid": ""
}
],
"q_static": "",
"technology": "",
"vendor": "",
"weight": "",
"popularity": "",
"q_mkey_type": "",
"q_class": "",
"behavior": "",
"name": "",
"parameter": ""
}
],
"vdom": "",
"build": "",
"serial": "",
"version": "",
"name": "",
"revision": "",
"path": ""
}
operation: Get Blocked IP Addresses
Input parameters
| Parameter |
Description |
| Block Method |
Specify the method to be used for retrieving the list of IP Addresses blocked on Fortinet FortiGate. You can choose from following options:
- Quarantine Based
- Policy Based: Specify values in the following fields:
- Policy Name: Specify the name of the policy specified on Fortinet FortiGate for blocking or unblocking IP addresses and whose associated list of blocked IP addresses to retrieve from Fortinet FortiGate. Based on our example, enter
FortiSOAR_Blocked_Policy in this field. See the Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate section.
- Address Group Name: Specify the name of the IP address group, in CSV(
"1.1.1.1", "2.2.2.2") or list(["1.1.1.1", "2.2.2.2"]) specified on Fortinet FortiGate for blocking or unblocking IP addresses. Based on our example, enter default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate section
- NGFW Mode: Specify the next-generation firewall(NGFW) mode of the VDOM where the specified policy is present on Fortinet FortiGate for blocking or unblocking IP addresses. You can choose from following options:
- Profile Based
- Policy Based
By default it is Profile Based.
|
| VDOM |
(Optional) Specify the VDOMs whose associated list of blocked IP addresses is to be retrieved from Fortinet FortiGate. You can specify VDOMs in CSV("1.1.1.1", "2.2.2.2") or list(["1.1.1.1", "2.2.2.2"]) format.
NOTE: The VDOM value that you specify in this field overwrites the VDOM(s) values that you have specified in the Configuration Parameters while configuring this connector. |
Output
The output contains the following populated JSON schema:
Output schema when you choose Block Method as Quarantine Based:
{
"vdom_not_exist": [],
"result": [
{
"name": "",
"version": "",
"vdom": "",
"serial": "",
"results": [
{
"ipv6": "",
"source": "",
"created": "",
"ip_address": "",
"expires": ""
}
],
"build": "",
"http_method": "",
"status": "",
"path": ""
}
]
}
Output schema when you choose Block Method as Policy Based:
{
"policy_name": "",
"srcaddr": [],
"dstaddr": [],
"addrgrp": [
{
"name": "",
"member": []
}
],
"addrgrp_not_exist": []
}
operation: Get Blocked Applications
Input parameters
| Parameter |
Description |
| VDOM |
(Optional) Specify the VDOM whose associated list of blocked applications are to be retrieved from Fortinet FortiGate. The VDOM mode should be enabled and accepts a single VDOM value in this field. Ensure that the specified VDOM contains a valid Application Control Profile Name to execute the action.
NOTE: The VDOM value that you specify in this field overwrites the VDOM(s) values that you have specified in the Configuration Parameters while configuring this connector. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"name": "",
"risk": "",
"q_ref": "",
"q_name": "",
"q_path": "",
"q_type": "",
"vendor": "",
"weight": "",
"q_class": "",
"behavior": "",
"category": "",
"metadata": [
{
"id": "",
"metaid": "",
"valueid": "",
"q_origin_key": ""
}
],
"protocol": "",
"q_static": true,
"parameter": "",
"popularity": "",
"technology": "",
"q_mkey_type": "",
"q_no_rename": false,
"q_origin_key": "",
"sub-category": "",
"q_global_entry": ""
}
operation: Get Blocked URLs
Input parameters
| Parameter |
Description |
| VDOM |
(Optional) Specify the VDOM whose associated list of blocked URLs are to be retrieved from Fortinet FortiGate. The VDOM mode should be enabled and accepts a single VDOM value in this field. Ensure that the specified VDOM contains a valid Web Filter Profile Name to execute the action.
NOTE: The VDOM value that you specify in this field overwrites the VDOM(s) values that you have specified in the Configuration Parameters while configuring this connector. |
Output
The output contains the following populated JSON schema:
{
"type": "",
"id": "",
"action": "",
"status": "",
"url": "",
"q_origin_key": "",
"exempt": "",
"referrer-host": "",
"web-proxy-profile": "",
"dns-address-family": ""
}
operation: Block IP Address
Input parameters
| Parameter |
Description |
| Block Method |
Method to be used for blocking IP addresses using Fortinet FortiGate. You can choose from following options:
- Quarantine Based: Specify values in the following fields:
- IP Addresses: Specify the IP addresses to block using Fortinet FortiGate in CSV(
"1.1.1.1", "2.2.2.2") or list(["1.1.1.1", "2.2.2.2"]) format.
- Time to Live: Specify the time till when the IP addresses are blocked. You can choose between the following options:
- 1 Hour
- 6 Hour
- 12 Hour
- 1 Day
- 6 Months
- 1 Year
- Custom: Specify a value, in seconds, in the Time to Live field.
- Policy Based: Specify values in the following fields:
- Policy Name: Specify the name of the policy specified on Fortinet FortiGate for blocking or unblocking IP addresses. Based on our example, enter
FortiSOAR_Blocked_Policy in this field. See the Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate section.
- IP Type: Select the type of IP address to block. You can select from the following options:
- Address Group Name: Specify the IP address group name, depending on the IP type selected in IP Type field, specified on Fortinet FortiGate for blocking or unblocking IP addresses. You can specify source or destination address group name. Based on our example, enter
Blocked_IPs in this field. See the Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate section.
- IP Address: Specify IP address, depending on the IP type selected in IP Type field, to block on Fortinet FortiGate.
- NGFW Mode: Specify the next-generation firewall(NGFW) mode of the VDOM where the specified policy is present on Fortinet FortiGate for blocking or unblocking IP addresses. You can choose from following options:
- Profile Based
- Policy Based
By default it is Profile Based.
|
| VDOM |
(Optional) Specify the VDOM to use for blocking IP address on Fortinet FortiGate.
NOTE: The VDOM value that you specify in this field overwrites the VDOM(s) values that you have specified in the Configuration Parameters while configuring this connector. |
Output
The output contains the following populated JSON schema:
Output schema when you choose Block Method as Quarantine Based:
{
"newly_blocked": [],
"vdom_not_exist": [],
"already_blocked": [],
"error_with_block": []
}
Output schema when you choose Block Method as Policy Based:
{
"already_blocked": [],
"newly_blocked": [],
"error_with_block": []
}
operation: Block Application
Input parameters
| Parameter |
Description |
| Application Names |
Specify a list of application names to block on Fortinet FortiGate. To block more than one application, their names must be in the list format. For example, for a list of applications enter ["Application_Name1", "Application_Name2"] in this field. For a single application enter Application_Name.
NOTE: You can retrieve application names using the Get Application Details action |
| VDOM |
(Optional) Specify the VDOM whose associated applications are to be blocked from Fortinet FortiGate. The VDOM mode should be enabled and a a single VDOM value in this field. Ensure that the specified VDOM contains a valid Application Control Profile Name to execute the action.
NOTE: The VDOM value that you specify in this field overwrites the VDOM(s) values that you have specified in the Configuration Parameters while configuring this connector. |
Output
The output contains the following populated JSON schema:
{
"name": "",
"status": "",
"message": ""
}
operation: Block URL
Input parameters
| Parameter |
Description |
| URL |
Specify the List of URLs that to block on Fortinet FortiGate. URLs must be in the list format if to block more than one URL. For example, for a list of URLs, enter: ["URL1", "URL2"] in this field. For a single URL enter: example.com |
| VDOM |
(Optional) Specify the VDOM whose associated list of blocked URLs are to be retrieved from Fortinet FortiGate. The VDOM mode should be enabled and accepts a single VDOM value in this field. Ensure that the specified VDOM contains a valid Web Filter Profile Name to execute the action.
NOTE: The VDOM value that you specify in this field overwrites the VDOM(s) values that you have specified in the Configuration Parameters while configuring this connector. |
Output
The output contains the following populated JSON schema:
{
"already_blocked": [],
"newly_blocked": [],
"not_block": []
}
operation: Unblock IP Address
Input parameters
| Parameter |
Description |
| Unblock Method |
Method to be used for unblocking IP addresses using Fortinet FortiGate. You can choose from following options:
- Quarantine Based: Specify values in the following fields:
- IP Addresses: Specify the IP addresses to unblock using Fortinet FortiGate in CSV(
"1.1.1.1", "2.2.2.2") or list(["1.1.1.1", "2.2.2.2"]) format.
- Policy Based: Specify values in the following fields:
- Policy Name: Specify the name of the policy specified on Fortinet FortiGate for blocking or unblocking IP addresses. Based on our example, enter
FortiSOAR_Blocked_Policy in this field. See the Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate section.
- IP Type: Select the type of IP address to unblock. You can select from the following options:
- Address Group Name: Specify the IP address group name, depending on the IP type selected in IP Type field, specified on Fortinet FortiGate for blocking or unblocking IP addresses. You can specify source or destination address group name. Based on our example, enter
Blocked_IPs in this field. See the Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate section.
- IP Address: Specify IP address, depending on the IP type selected in IP Type field, to unblock on Fortinet FortiGate.
- NGFW Mode: Specify the next-generation firewall(NGFW) mode of the VDOM where the specified policy is present on Fortinet FortiGate for blocking or unblocking IP addresses. You can choose from following options:
- Profile Based
- Policy Based
By default it is Profile Based.
|
| VDOM |
(Optional) Specify the VDOM to use for unblocking IP address on Fortinet FortiGate.
NOTE: The VDOM value that you specify in this field overwrites the VDOM(s) values that you have specified in the Configuration Parameters while configuring this connector. |
Output
The output contains the following populated JSON schema:
Output schema when you choose Unblock Method as Quarantine Based:
{
"newly_unblocked": [],
"ip_not_exist": [],
"vdom_not_exist": [],
"error_with_unblock": []
}
Output schema when you choose Unblock Method as Policy Based:
{
"not_exist": [],
"newly_unblocked": [],
"error_with_unblock": []
}
operation: Unblock Application
Input parameters
| Parameter |
Description |
| Application Names |
Specify a list of application names to unblock on Fortinet FortiGate. To unblock more than one application, their names must be in the list format. For example, for a list of applications enter ["Application_Name1", "Application_Name2"] in this field. For a single application enter Application_Name.
NOTE: You can retrieve application names using the Get Application Details action |
| VDOM |
(Optional) Specify the VDOM whose associated applications are to be unblocked from Fortinet FortiGate. The VDOM mode should be enabled and a a single VDOM value in this field. Ensure that the specified VDOM contains a valid Application Control Profile Name to execute the action.
NOTE: The VDOM value that you specify in this field overwrites the VDOM(s) values that you have specified in the Configuration Parameters while configuring this connector. |
Output
The output contains the following populated JSON schema:
{
"name": "",
"status": "",
"message": ""
}
operation: Unblock URL
Input parameters
| Parameter |
Description |
| URL |
Specify the list of URLs that to unblock on Fortinet FortiGate. URLs must be in the list format if to block more than one URL. For example, for a list of URLs, enter: ["URL1", "URL2"] in this field. For a single URL enter: example.com |
| VDOM |
(Optional) Specify the VDOM whose associated list of unblocked URLs are to be retrieved from Fortinet FortiGate. The VDOM mode should be enabled and accepts a single VDOM value in this field. Ensure that the specified VDOM contains a valid Web Filter Profile Name to execute the action.
NOTE: The VDOM value that you specify in this field overwrites the VDOM(s) values that you have specified in the Configuration Parameters while configuring this connector. |
Output
The output contains the following populated JSON schema:
{
"not_exist": [],
"newly_unblocked": [],
"not_unblock": []
}
operation: Quarantine Host
Input parameters
| Parameter |
Description |
| MAC Address |
Specify the list of MAC addresses that to quarantine on Fortinet FortiGate. MAC addresses must be in a list format if to quarantine more than one MAC address. For example, 00:15:00:e8:27:25 or ['00:15:00:e8:27:25', '00:15:00:e8:27:26']. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"already_quarantine": [],
"newly_quarantine": [],
"not_quarantine": []
}
operation: Unquarantine Host
Input parameters
| Parameter |
Description |
| MAC Address |
Specify the list of MAC addresses that to remove from quarantine on Fortinet FortiGate. MAC addresses must be in a list format if to remove more than one MAC address from quarantine. For example, 00:15:00:e8:27:25 or ['00:15:00:e8:27:25', '00:15:00:e8:27:26']. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"not_exist": [],
"newly_unquarantine": [],
"not_unquarantine": []
}
operation: Get Quarantine Hosts
Input parameters
| Parameter |
Description |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"name": "",
"path": "",
"vdom": "",
"build": "",
"serial": "",
"status": "",
"results": {
"targets": [
{
"macs": [
{
"mac": "",
"drop": "",
"parent": "",
"entry-id": "",
"description": "",
"q_origin_key": ""
}
],
"entry": "",
"description": "",
"q_origin_key": ""
}
],
"quarantine": "",
"traffic-policy": "",
"firewall-groups": ""
},
"version": "",
"revision": "",
"http_method": "",
"http_status": ""
}
operation: Create Address
Input parameters
| Parameter |
Description |
| Address Category |
Select address category to create on Fortinet FortiGate. You can choose from following options:
- IPv4 Address: Specify values in the following fields:
- Address Name: Specify a name of the address to create on Fortinet FortiGate.
- Type: Select the type of address being specified in the subsequent fields:
- Subnet: Specify values in subsequent fields:
- IP/Netmask: Specify an IP address or Netmask name of the address to create on Fortinet FortiGate.
- Static Route Configuration: Select one of the following options:
- Enable: Select to use this address in the static route configuration.
- Disable: Select to disable the use of this address in the static route configuration.
- IP Range: Specify values in subsequent fields:
- Start IP: Specify the first IP address in the range of addresses to be created on Fortinet FortiGate.
- End IP: Specify the last IP address in the range of addresses to be created on Fortinet FortiGate.
- Static Route Configuration: Select one of the following options:
- Enable: Select to use this address in the static route configuration.
- Disable: Select to disable the use of this address in the static route configuration.
- FQDN: Specify values in subsequent fields:
- FQDN: Specify a fully qualified domain name(FQDN) of the address to create on Fortinet FortiGate.
- Static Route Configuration: Select one of the following options:
- Enable: Select to use this address in the static route configuration.
- Disable: Select to disable the use of this address in the static route configuration.
- Geography: Select the country whose associated IP addresses is to be created on Fortinet FortiGate in the Country/Region field.
- Device (MAC Address): Select one of the following options in MAC Address Scope field:
- Single Address: Specify the MAC address to create on Fortinet FortiGate in MAC Address field. For example,
00:15:00:e8:27:25.
- Address Range: Specify values in subsequent fields:
- Starting MAC: Specify the first MAC address in the range of MAC addresses to create on Fortinet FortiGate.
- Ending MAC: Specify the last MAC address in the range of MAC addresses to create on Fortinet FortiGate.
- IPv6 Address: : Specify values in subsequent fields:
- Address Name: Specify a name of the address to create on Fortinet FortiGate.
- Type: Select the type of address being specified in the subsequent fields:
- IPv6 Subnet: Specify an IPv6 address or Netmask name of the address to create on Fortinet FortiGate in IPv6 Address field.
- IPv6 Range: Specify values in subsequent fields:
- Start IP: Specify the first IPv6 address in the range of addresses to be created on Fortinet FortiGate.
- End IP: Specify the last IPv6 address in the range of addresses to be created on Fortinet FortiGate.
- IPv6 FQDN: Specify a fully qualified domain name(FQDN) of the IPv6 address to create on Fortinet FortiGate in FQDN field.
- IPv6 Geography: Select the country whose associated IPv6 addresses is to be created on Fortinet FortiGate in the Country/Region field.
- IPv6 Fabric Connector Address: Specify an SDN connector name in the SDN Connector field.
- IPv6 Template: Specify values in subsequent fields:
- IPv6 Address Template: Specify the IPv6 address template to use.
- Host Type: Select Specific to enter a particular IPv6 host in the Host field.
- Device (MAC Address): Select one of the following options in MAC Address Scope field:
- Single Address: Specify the MAC address to create on Fortinet FortiGate in MAC Address field. For example,
00:15:00:e8:27:25.
- Address Range: Specify values in subsequent fields:
- Starting MAC: Specify the first MAC address in the range of MAC addresses to create on Fortinet FortiGate.
- Ending MAC: Specify the last MAC address in the range of MAC addresses to create on Fortinet FortiGate.
|
| Comments |
(Optional) Comment to be added to the address to be created on Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"mkey": "",
"name": "",
"path": "",
"vdom": "",
"build": "",
"serial": "",
"status": "",
"version": "",
"revision": "",
"http_method": "",
"http_status": "",
"old_revision": "",
"revision_changed": ""
}
operation: Get Addresses
Input parameters
| Parameter |
Description |
| Address Category |
Select the address type to retrieve its details from Fortinet FortiGate. You can select from following options:
- IPv4 Address
- IPv6 Address
|
| Address Name |
Specify the name of the address to retrieve its details from Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"results": [
{
"name": "",
"q_origin_key": "",
"uuid": "",
"subnet": "",
"type": "",
"sub-type": "",
"clearpass-spt": "",
"start-mac": "",
"end-mac": "",
"country": "",
"cache-ttl": "",
"sdn": "",
"fsso-group": [],
"interface": "",
"obj-type": "",
"comment": "",
"associated-interface": "",
"color": "",
"filter": "",
"sdn-addr-type": "",
"obj-id": "",
"list": [],
"tagging": [],
"allow-routing": "",
"fabric-object": ""
}
],
"vdom": "",
"path": "",
"name": "",
"mkey": "",
"status": "",
"http_status": "",
"serial": "",
"version": "",
"build": ""
}
operation: Update Address
Input parameters
| Parameter |
Description |
| Address Category |
Select address category to update on Fortinet FortiGate. You can choose from following options:
- IPv4 Address: Specify values in the following fields:
- Address Name: Specify the name of the address to update on Fortinet FortiGate.
- Type: Select the type of address being specified in the subsequent fields:
- Subnet: Specify values in subsequent fields:
- IP/Netmask: Specify an IP address or Netmask name of the address to update on Fortinet FortiGate.
- Static Route Configuration: Select one of the following options:
- Enable: Select to use this address in the static route configuration.
- Disable: Select to disable the use of this address in the static route configuration.
- IP Range: Specify values in subsequent fields:
- Start IP: Specify the first IP address in the range of addresses to be updated on Fortinet FortiGate.
- End IP: Specify the last IP address in the range of addresses to be updated on Fortinet FortiGate.
- Static Route Configuration: Select one of the following options:
- Enable: Select to use this address in the static route configuration.
- Disable: Select to disable the use of this address in the static route configuration.
- FQDN: Specify values in subsequent fields:
- FQDN: Specify a fully qualified domain name(FQDN) of the address to update on Fortinet FortiGate.
- Static Route Configuration: Select one of the following options:
- Enable: Select to use this address in the static route configuration.
- Disable: Select to disable the use of this address in the static route configuration.
- Geography: Select the country whose associated IP addresses is to be updated on Fortinet FortiGate in the Country/Region field.
- Device (MAC Address): Select one of the following options in MAC Address Scope field:
- Single Address: Specify the MAC address to update on Fortinet FortiGate in MAC Address field. For example,
00:15:00:e8:27:25.
- Address Range: Specify values in subsequent fields:
- Starting MAC: Specify the first MAC address in the range of MAC addresses to update on Fortinet FortiGate.
- Ending MAC: Specify the last MAC address in the range of MAC addresses to update on Fortinet FortiGate.
- IPv6 Address: : Specify values in subsequent fields:
- Address Name: Specify a name of the address to update on Fortinet FortiGate.
- Type: Select the type of address being specified in the subsequent fields:
- IPv6 Subnet: Specify an IPv6 address or Netmask name of the address to update on Fortinet FortiGate in IPv6 Address field.
- IPv6 Range: Specify values in subsequent fields:
- Start IP: Specify the first IPv6 address in the range of addresses to be updated on Fortinet FortiGate.
- End IP: Specify the last IPv6 address in the range of addresses to be updated on Fortinet FortiGate.
- IPv6 FQDN: Specify a fully qualified domain name(FQDN) of the IPv6 address to update on Fortinet FortiGate in FQDN field.
- IPv6 Geography: Select the country whose associated IPv6 addresses is to be updated on Fortinet FortiGate in the Country/Region field.
- IPv6 Fabric Connector Address: Specify an SDN connector name in the SDN Connector field.
- IPv6 Template: Specify values in subsequent fields:
- IPv6 Address Template: Specify the IPv6 address template to use.
- Host Type: Select Specific to enter a particular IPv6 host in the Host field.
- Device (MAC Address): Select one of the following options in MAC Address Scope field:
- Single Address: Specify the MAC address to update on Fortinet FortiGate in MAC Address field. For example,
00:15:00:e8:27:25.
- Address Range: Specify values in subsequent fields:
- Starting MAC: Specify the first MAC address in the range of MAC addresses to update on Fortinet FortiGate.
- Ending MAC: Specify the last MAC address in the range of MAC addresses to update on Fortinet FortiGate.
|
| New Address Name |
(Optional) Specify a new name for the address to update on Fortinet FortiGate. To skip renaming the address, leave this field blank. |
| Comments |
(Optional) Comment to be added to the address to update on Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"mkey": "",
"name": "",
"path": "",
"vdom": "",
"build": "",
"serial": "",
"status": "",
"version": "",
"revision": "",
"http_method": "",
"http_status": "",
"old_revision": "",
"revision_changed": ""
}
operation: Delete Address
Input parameters
| Parameter |
Description |
| Address Category |
Select the address type to delete from Fortinet FortiGate. You can select from following options:
- IPv4 Address
- IPv6 Address
|
| Address Name |
Specify the name of the address to delete from Fortinet FortiGate. |
| VDOM |
(Optional) Specify the VDOM on which to perform automated operations.
NOTE: You can specify VDOMs as a Configuration parameter or here, as an input parameter. You can specify VDOMs in CSV("1.1.1.1", "2.2.2.2") or list(["1.1.1.1", "2.2.2.2"]) format, if the VDOM mode is enabled.
By default, VDOM is set to root. |
Output
The output contains the following populated JSON schema:
{
"mkey": "",
"name": "",
"path": "",
"vdom": "",
"build": "",
"serial": "",
"status": "",
"version": "",
"revision": "",
"http_method": "",
"http_status": "",
"old_revision": "",
"revision_changed": ""
}
operation: Create Address Group
Input parameters
| Parameter |
Description |
| Address Group Category |
Select address group category to create group. You can select from following options:
- IPv4 Group: Specify values in subsequent fields:
- Group Name: Specify the name of address group to create on Fortinet FortiGate.
- Members: Specify the list of IP address names to add to the address group being created on Fortinet FortiGate.
- Type: Specify the type of address group to create on Fortinet FortiGate. You can choose from following options:
- Group: Select this option if the addresses within may belong to multiple groups. This is the default address group type.
- Folder: Select this option if the members cannot belong to any other group.
- Exclude: Select this checkbox, i.e., set it to
True, to enable address exclusion. Once selected, specify the list of IP address names or URL names to add into exclusion list.
- Static Route Configuration: Select one of the following options:
- Enable: Select to use this address in the static route configuration.
- Disable: Select to disable the use of this address in the static route configuration.
- IPv6 Group
- Group Name: Specify the name of address group to be created on Fortinet FortiGate
- Members: Specify the list of IP address names to add to the address group to create on Fortinet FortiGate.
|
| Comments |
(Optional) Specify the comment to be added to the address group to be created on Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Get Address Groups
Input parameters
| Parameter |
Description |
| Address Group Category |
Select the address group type to retrieve its details from Fortinet FortiGate. You can select from following options:
|
| Address Group Name |
Specify the name of the address group to retrieve its details from Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"results": [
{
"name": "",
"q_origin_key": "",
"type": "",
"uuid": "",
"member": [
{
"name": "",
"q_origin_key": ""
},
{
"name": "",
"q_origin_key": ""
},
{
"name": "",
"q_origin_key": ""
}
],
"comment": "",
"exclude": "",
"exclude-member": [],
"color": "",
"tagging": [],
"allow-routing": "",
"fabric-object": ""
}
],
"vdom": "",
"path": "",
"name": "",
"mkey": "",
"status": "",
"http_status": "",
"serial": "",
"version": "",
"build": ""
}
operation: Update Address Group
Input parameters
| Parameter |
Description |
| Address Group Category |
Select address group category to update group. You can select from following options:
- IPv4 Group: Specify values in subsequent fields:
- Group Name: Specify the name of address group to update on Fortinet FortiGate.
- New Group Name: (Optional) Specify a new name for the address group to update its name on Fortinet FortiGate
- Add Members: Specify the list of IP address names to add to the address group being updated on Fortinet FortiGate.
- Remove Members: Specify the list of IP address names to remove from the address group being updated on Fortinet FortiGate.
- Exclude: Select this checkbox, i.e., set it to
True, to enable address exclusion. Once selected, specify the list of IP address names or URL names to add into exclusion list.
- Static Route Configuration: Select one of the following options:
- Enable: Select to use this address in the static route configuration.
- Disable: Select to disable the use of this address in the static route configuration.
- IPv6 Group: Specify values in subsequent fields:
- Group Name: Specify the name of address group to be updated on Fortinet FortiGate
- New Group Name: (Optional) Specify a new name for the address group to update its name on Fortinet FortiGate
- Add Members: Specify the list of IP address names to add to the address group being updated on Fortinet FortiGate.
- Remove Members: Specify the list of IP address names to remove from the address group being updated on Fortinet FortiGate.
|
| Comments |
(Optional) Specify the comment to be added to the address group to be created on Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Delete Address Group
Input parameters
| Parameter |
Description |
| Address Group Category |
Select the address group type to delete from Fortinet FortiGate. You can select from following options:
- IPv4 Address
- IPv6 Address
|
| Address Name |
Specify the name of the address group to delete from Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Create Service
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the service to be created on Fortinet FortiGate. |
| Category |
Specify the category of the service to be created on Fortinet FortiGate. For example, Email, Authentication, General, Remote Access, etc. |
| Protocol |
Select the protocol type based on IANA numbers. You can select from following options:
- TCP/UDP/SCTP: Specify values in following fields:
- Address: Specify the type of address to associate with the service to be created on Fortinet FortiGate. You can select from following options:
- IP Range: Specify the starting and ending IP addresses that constitute the IP range associated with the service, in the IP Range field. For example,
192.0.2.0-192.0.2.24
- FQDN: Specify the Fully qualified domain name associated with the service, in the FQDN field
- TCP Port Range: Specify multiple TCP port ranges associated with the service. For example,
0-22:55-75 55-77:88-100 in the format of TCP Port Low-TCP Port High:Source Port Low-Source Port High.
- UDP Port Range: Specify multiple UDP port ranges associated with the service. For example,
0-22:55-75 55-77:88-100 in the format of UDP Port Low-UDP Port High:Source Port Low-Source Port High.
- SCTP Port Range: Specify multiple SCTP port ranges associated with the service. For example,
0-22:55-75 55-77:88-100 in the format of SCTP Port Low-SCTP Port High:Source Port Low-Source Port High.
- ICMP: Specify values in following fields:
- Type: Specify the type of ICMP to associate with the service to be created on Fortinet FortiGate.
- Code: Specify the ICMP code to associate with the service to be created on Fortinet FortiGate. Maximum:
255 Minimum: 0.
- ICMP6: Specify values in following fields:
- Type: Specify the type of ICMP6 to associate with the service to be created on Fortinet FortiGate.
- Code: Specify the ICMP6 code to associate with the service to be created on Fortinet FortiGate. Maximum:
255 Minimum: 0.
- IP: Specify the protocol number of the IP, in the Protocol Number field, to associate with the service to be created on Fortinet FortiGate. Maximum:
254 Minimum: 0.
- HTTP
- FTP
- CONNECT
- SOCKS-TCP
- SOCKS-UDP
- ALL
|
| Comments |
(Optional) Specify the comment to be added to the service to be created on Fortinet FortiGate. |
| Show in Service List |
Select one of the following options:
- Enable: Select this option to show the created service on the graphical user interface(GUI).
- Disable: Select this option to hide the created service on the graphical user interface(GUI).
|
| VDOM |
(Optional) Specify the VDOM on which to perform automated operations.
NOTE: You can specify VDOMs as a Configuration parameter or here, as an input parameter. You can specify VDOMs in CSV("1.1.1.1", "2.2.2.2") or list(["1.1.1.1", "2.2.2.2"]) format, if the VDOM mode is enabled.
By default, VDOM is set to root. |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Get Services
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the service to retrieve its details from Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"results": [
{
"name": "",
"q_origin_key": "",
"proxy": "",
"category": "",
"protocol": "",
"helper": "",
"iprange": "",
"fqdn": "",
"tcp-portrange": "",
"udp-portrange": "",
"sctp-portrange": "",
"tcp-halfclose-timer": "",
"tcp-halfopen-timer": "",
"tcp-timewait-timer": "",
"udp-idle-timer": "",
"session-ttl": "",
"check-reset-range": "",
"comment": "",
"color": "",
"visibility": "",
"app-service-type": "",
"app-category": [],
"application": [],
"fabric-object": ""
}
],
"vdom": "",
"path": "",
"name": "",
"mkey": "",
"status": "",
"http_status": "",
"serial": "",
"version": "",
"build": ""
}
operation: Update Service
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the service to be updated on Fortinet FortiGate. |
| New Name |
(Optional) Specify a new name for the service to be updated on Fortinet FortiGate. |
| Category |
Specify the category of the service to be updated on Fortinet FortiGate. For example, Email, Authentication, General, Remote Access, etc. |
| Protocol |
Select the protocol type based on IANA numbers. You can select from following options:
- TCP/UDP/SCTP: Specify values in following fields:
- Address: Specify the type of address to associate with the service to be updated on Fortinet FortiGate. You can select from following options:
- IP Range: Specify the starting and ending IP addresses that constitute the IP range associated with the service, in the IP Range field. For example,
192.0.2.0-192.0.2.24
- FQDN: Specify the Fully qualified domain name associated with the service, in the FQDN field
- TCP Port Range: Specify multiple TCP port ranges associated with the service. For example,
0-22:55-75 55-77:88-100 in the format of TCP Port Low-TCP Port High:Source Port Low-Source Port High.
- UDP Port Range: Specify multiple UDP port ranges associated with the service. For example,
0-22:55-75 55-77:88-100 in the format of UDP Port Low-UDP Port High:Source Port Low-Source Port High.
- SCTP Port Range: Specify multiple SCTP port ranges associated with the service. For example,
0-22:55-75 55-77:88-100 in the format of SCTP Port Low-SCTP Port High:Source Port Low-Source Port High.
- ICMP: Specify values in following fields:
- Type: Specify the type of ICMP to associate with the service to be updated on Fortinet FortiGate.
- Code: Specify the ICMP code to associate with the service to be updated on Fortinet FortiGate. Maximum:
255 Minimum: 0.
- ICMP6: Specify values in following fields:
- Type: Specify the type of ICMP6 to associate with the service to be updated on Fortinet FortiGate.
- Code: Specify the ICMP6 code to associate with the service to be updated on Fortinet FortiGate. Maximum:
255 Minimum: 0.
- IP: Specify the protocol number of the IP, in the Protocol Number field, to associate with the service to be updated on Fortinet FortiGate. Maximum:
254 Minimum: 0.
- HTTP
- FTP
- CONNECT
- SOCKS-TCP
- SOCKS-UDP
- ALL
|
| Comments |
(Optional) Specify the comment to be added to the service to be updated on Fortinet FortiGate. |
| Show in Service List |
Select one of the following options:
- Enable: Select this option to show the updated service on the graphical user interface(GUI).
- Disable: Select this option to hide the updated service on the graphical user interface(GUI).
|
| VDOM |
(Optional) Specify the VDOM on which to perform automated operations.
NOTE: You can specify VDOMs as a Configuration parameter or here, as an input parameter. You can specify VDOMs in CSV("1.1.1.1", "2.2.2.2") or list(["1.1.1.1", "2.2.2.2"]) format, if the VDOM mode is enabled.
By default, VDOM is set to root. |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Delete Service
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the service to be deleted from Fortinet FortiGate |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Create Service Group
Input parameters
| Parameter |
Description |
| Name |
Specify the name of service group to be created on Fortinet FortiGate. |
| Members |
Specify the list of members to add to the service group being created on Fortinet FortiGate. |
| Comments |
(Optional) Specify the comment to be added to the service group being created on Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Get Service Groups
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the service group to retrieve its details from Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"results": [
{
"name": "",
"q_origin_key": "",
"proxy": "",
"member": [
{
"name": "",
"q_origin_key": ""
}
],
"comment": "",
"color": "",
"fabric-object": ""
}
],
"vdom": "",
"path": "",
"name": "",
"status": "",
"http_status": "",
"serial": "",
"version": "",
"build": ""
}
operation: Update Service Group
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the service group to be updated on Fortinet FortiGate. |
| New Name |
(Optional) Specify a new name for the service group to be updated on Fortinet FortiGate. |
| Add Members |
Specify the list of members to add to the service group to update on Fortinet FortiGate. |
| Remove Members |
Specify the list of members to remove from the service group to update on Fortinet FortiGate. |
| Comments |
(Optional) Specify the comment on the service group to be updated on Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Delete Service Group
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the service group to be deleted from Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Create Policy
Input parameters
| Parameter |
Description |
| Policy Name |
Specify the name of policy to be created on Fortinet FortiGate |
| Incoming Interface |
Specify names of incoming interface associated with the policy to be created on Fortinet FortiGate. For example port1. |
| Outgoing Interface |
Specify names of outgoing interface associated with the policy to be created on Fortinet FortiGate. For example port2. |
| Source |
Specify the source IPv4 address and address group names associated with the policy to be created on Fortinet FortiGate. |
| Destination |
Specify the destination IPv4 address and address group names associated with the policy to be created on Fortinet FortiGate. |
| Service |
Specify the service and service group names associated with the policy to be created on Fortinet FortiGate. |
| Schedule |
Specify the name of the schedule associated with the policy to be created on Fortinet FortiGate. |
| Status |
Select from the following options:
- Enable: Select to enable to this policy on Fortinet FortiGate.
- Disable: Select to disable to this policy on Fortinet FortiGate.
|
| Action |
Select the policy action from following available options:
- Accept: Select this action to allow sessions that match this firewall policy.
- Inspection Mode: Select the appropriate inspection mode for the policy. You can choose from the following options:
- Flow Based(default)
- Proxy Based
- NAT: Select to enable NAT and specify following information:
- IP Pool Configuration: Select from the following options:
- Use Outgoing Interface Address
- Use Dynamic IP Pool: Specify pool names in CSV or list format in the Pool Name field.
- Preserve Source Port: Enable to prevent source NAT from changing a session's source port
- Protocol Options: Specify the name of an existing protocol options profile.
- Security Profiles: Select security profiles to enable. You can select multiple values from following options:
- AntiVirus: Specify the name of an existing antivirus profile in the Antivirus Profile field.
- Web Filter: Specify the name of an existing web filter profile in the Web Filter Profile field.
- DNS Filter: Specify the name of an existing DNS filter profile in the DNS Filter Profile field.
- Application Control: Specify the name of an existing application list in the Application Control field.
- IPS: Specify the name of an existing IPS sensor in the IPS Sensor field.
- File Filter: Specify the name of an existing file-filter profile in the File Filter Profile field.
- SSL Inspection: Specify the name of an existing SSL inspection profile in the SSL Inspection Profile field.
- Log Traffic: Select the logging levels for this policy.Enable or disable logging.
- All: Select this option to log all sessions accepted or denied by this policy.
- UTM: Select this option to log traffic that has a security profile applied to it.
- Disable: Select this option to disable all logging for this policy.
- Deny: Select this action to block sessions that match this firewall policy.
|
| Comments |
(Optional) Specify the comment to be added to the policy on Fortinet FortiGate |
| Additional Policy Arguments |
(Optional) Specify policy arguments in JSON format to be added to the policy on Fortinet FortiGate. You can enter arguments in the following format:
{
"field1": value1,
"field2": value2
}
|
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Get List of Policies
Input parameters
| Parameter |
Description |
| Policy ID |
Specify the policy ID to get its details |
| VDOM |
(Optional) Specify the VDOM on which to perform automated operations.
NOTE: You can specify VDOMs as a Configuration parameter or here, as an input parameter. You can specify VDOMs in CSV("1.1.1.1", "2.2.2.2") or list(["1.1.1.1", "2.2.2.2"]) format, if the VDOM mode is enabled.
By default, VDOM is set to root. |
Output
The output contains the following populated JSON schema:
{
"result": [
{
"status": "",
"path": "",
"revision": "",
"name": "",
"http_method": "",
"vdom": "",
"http_status": "",
"version": "",
"build": "",
"serial": "",
"results": [
{
"logtraffic": "",
"srcaddr": [
{
"q_origin_key": "",
"name": ""
}
],
"dstintf": [
{
"q_origin_key": "",
"name": ""
}
],
"label": "",
"scan-botnet-connections": "",
"action": "",
"capture-packet": "",
"ips-sensor": "",
"tcp-session-without-syn": "",
"av-profile": "",
"policyid": "",
"diffserv-reverse": "",
"dnsfilter-profile": "",
"send-deny-packet": "",
"profile-protocol-options": "",
"app-category": [],
"vlan-cos-fwd": "",
"diffserv-forward": "",
"wanopt-passive-opt": "",
"tags": [],
"custom-log-fields": [],
"voip-profile": "",
"users": [],
"srcintf": [
{
"q_origin_key": "",
"name": ""
}
],
"learning-mode": "",
"timeout-send-rst": "",
"wsso": "",
"fsso": "",
"spamfilter-profile": "",
"traffic-shaper-reverse": "",
"url-category": [],
"block-notification": "",
"rsso": "",
"internet-service": "",
"internet-service-custom": [],
"webfilter-profile": "",
"dsri": "",
"auth-cert": "",
"ssl-mirror": "",
"groups": [],
"diffservcode-forward": "",
"internet-service-id": [],
"firewall-session-dirty": "",
"tcp-mss-sender": "",
"dstaddr-negate": "",
"outbound": "",
"rtp-nat": "",
"dscp-value": "",
"profile-type": "",
"wccp": "",
"inbound": "",
"ssl-mirror-intf": [],
"service": [
{
"q_origin_key": "",
"name": ""
}
],
"webcache": "",
"service-negate": "",
"wanopt": "",
"dscp-negate": "",
"profile-group": "",
"status": "",
"q_origin_key": "",
"tcp-mss-receiver": "",
"rtp-addr": [],
"nat": "",
"utm-status": "",
"poolname": [],
"fsso-agent-for-ntlm": "",
"delay-tcp-npu-session": "",
"ntlm": "",
"permit-stun-host": "",
"vpntunnel": "",
"devices": [],
"schedule": "",
"permit-any-host": "",
"global-label": "",
"icap-profile": "",
"dlp-sensor": "",
"identity-based-route": "",
"logtraffic-start": "",
"redirect-url": "",
"session-ttl": "",
"diffservcode-rev": "",
"auth-path": "",
"disclaimer": "",
"application": [],
"name": "",
"wanopt-profile": "",
"schedule-timeout": "",
"internet-service-negate": "",
"traffic-shaper": "",
"ippool": "",
"wanopt-detection": "",
"natoutbound": "",
"webcache-https": "",
"fixedport": "",
"application-list": "",
"waf-profile": "",
"dstaddr": [
{
"q_origin_key": "",
"name": ""
}
],
"comments": "",
"srcaddr-negate": "",
"replacemsg-override-group": "",
"uuid": "",
"vlan-cos-rev": "",
"radius-mac-auth-bypass": "",
"wanopt-peer": "",
"natip": "",
"per-ip-shaper": "",
"dscp-match": "",
"ntlm-enabled-browsers": [],
"ntlm-guest": "",
"natinbound": "",
"captive-portal-exempt": "",
"match-vip": "",
"ssl-ssh-profile": "",
"auth-redirect-addr": ""
}
]
}
],
"vdom_not_exist": []
}
operation: Update Policy
Input parameters
| Parameter |
Description |
| Policy ID |
Specify the ID of policy to be updated on Fortinet FortiGate. |
| Policy Name |
Specify the name of policy to be updated on Fortinet FortiGate. |
| Incoming Interface |
Specify names of incoming interface associated with the policy to be updated on Fortinet FortiGate. For example port1. |
| Outgoing Interface |
Specify names of outgoing interface associated with the policy to be updated on Fortinet FortiGate. For example port2. |
| Source |
Specify the source IPv4 address and address group names associated with the policy to be updated on Fortinet FortiGate. |
| Destination |
Specify the destination IPv4 address and address group names associated with the policy to be updated on Fortinet FortiGate. |
| Service |
Specify the service and service group names associated with the policy to be updated on Fortinet FortiGate. |
| Schedule |
Specify the name of the schedule associated with the policy to be updated on Fortinet FortiGate. |
| Status |
Select from the following options:
- Enable: Select to enable to this policy on Fortinet FortiGate.
- Disable: Select to disable to this policy on Fortinet FortiGate.
|
| Action |
Select the policy action from following available options:
- Accept: Select this action to allow sessions that match this firewall policy.
- Inspection Mode: Select the appropriate inspection mode for the policy. You can choose from the following options:
- Flow Based(default)
- Proxy Based
- NAT: Select to enable NAT and specify following information:
- IP Pool Configuration: Select from the following options:
- Use Outgoing Interface Address
- Use Dynamic IP Pool: Specify pool names in CSV or list format in the Pool Name field.
- Preserve Source Port: Enable to prevent source NAT from changing a session's source port
- Protocol Options: Specify the name of an existing protocol options profile.
- Security Profiles: Select security profiles to enable. You can select multiple values from following options:
- AntiVirus: Specify the name of an existing antivirus profile in the Antivirus Profile field.
- Web Filter: Specify the name of an existing web filter profile in the Web Filter Profile field.
- DNS Filter: Specify the name of an existing DNS filter profile in the DNS Filter Profile field.
- Application Control: Specify the name of an existing application list in the Application Control field.
- IPS: Specify the name of an existing IPS sensor in the IPS Sensor field.
- File Filter: Specify the name of an existing file-filter profile in the File Filter Profile field.
- SSL Inspection: Specify the name of an existing SSL inspection profile in the SSL Inspection Profile field.
- Log Traffic: Select the logging levels for this policy.Enable or disable logging.
- All: Select this option to log all sessions accepted or denied by this policy.
- UTM: Select this option to log traffic that has a security profile applied to it.
- Disable: Select this option to disable all logging for this policy.
- Deny: Select this action to block sessions that match this firewall policy.
|
| Comments |
(Optional) Comment to be added to the policy to be updated on Fortinet FortiGate |
| Additional Policy Arguments |
(Optional) Specify policy arguments in JSON format to be updated on Fortinet FortiGate. You can enter arguments in the following format:
{
"field1": value1,
"field2": value2
}
|
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"revision": "",
"revision_changed": "",
"old_revision": "",
"mkey": "",
"status": "",
"http_status": "",
"vdom": "",
"path": "",
"name": "",
"serial": "",
"version": "",
"build": ""
}
operation: Delete Policy
Input parameters
| Parameter |
Description |
| Policy ID |
Specify the ID of policy to be deleted from Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"mkey": "",
"name": "",
"path": "",
"vdom": "",
"build": "",
"serial": "",
"status": "",
"version": "",
"revision": "",
"http_method": "",
"http_status": "",
"old_revision": "",
"revision_changed": ""
}
operation: Execute Command
Input parameters
| Parameter |
Description |
| Commands |
Specify the command that to execute on the FortiOS console. You can provide commands in the .csv or the list format. |
| Username |
Specify the username to access the FortiOS endpoint server to connect and execute the specified command. |
| Password |
Specify the password to access the FortiOS endpoint server to connect and execute the specified command. |
| Private Key |
Specify the private key to perform SSH authentication on the FortiOS server. |
| Port |
Specify the port number to use for connecting to the FortiOS server via SSH. By default, this is set to 22. |
| Timeout |
Specify the time, in seconds, after which the execution of the remote command times out. |
Output
The output contains the following populated JSON schema:
{
"command": "",
"output": []
}
operation: Create User
Input parameters
| Parameter |
Description |
| User Type |
Select user type based on which to create a new user. You can choose from following options:
- Local User: Specify values in following fields:
- Username: Specify the username for the user to be created in the Fortinet FortiGate server
- Password: Specify the password for the user to be created in the Fortinet FortiGate server
- Remote Radius User: Specify values in following fields:
- Username: Specify the username for the user to be created in the Fortinet FortiGate server
- Radius Server: Specify the name of the RADIUS server using which the user gets authenticated
- Remote TACACS+ User: Specify values in following fields:
- Username: Specify the username for the user to be created in the Fortinet FortiGate server
- TACACS+ Server: Specify the name of the TACACS+ server using which the user gets authenticated.
|
| Two Factor Authentication |
Select one of the following options for the two-factor authentication:
- Enable: Select to enable the two-factor authentication. Specify values in the following fields:
- Authentication Type: Select the type of two-factor authentication for the user you are creating on Fortinet FortiGate. You can choose from following options:
- FortiToken: Select this option to use FortiToken as the authentication type. Specify values in the following fields:
- Token: Enter the token name used to authenticate the user
- Send Activation Code: Select one of the following options:
- Enable: Select the method of sending the activation code from the Activation Method field. You can choose from following options:
- Disable: Select this option to disable sending of an activation code for two-factor authentication.
- FortiToken Cloud: Select this option to use FortiToken Cloud as the authentication type.
- Email Address: Enter email address of the user being created on Fortinet FortiGate.
- SMS: Select from the following options:
- Enable: Select to enable SMS-based two-factor authentication for the user being created on Fortinet FortiGate. Specify values in the following fields:
- Country Dial Code: Specify the dial-code of the country where the user being created, works.
- Phone Number: Specify the mobile phone number of the user for two-factor authentication.
- Disable: Select to disable SMS-based two-factor authentication for the user being created on Fortinet FortiGate.
- Disable: Select to disable the two-factor authentication.
|
| User Account Status |
Select the account status of the user being created on Fortinet FortiGate. You can choose from following options:
|
| User Group |
Select the group to assign to the user being created on Fortinet FortiGate. You can choose from following options:
- Enable: Select to assign the user to the group specified in the User Group Names field. You can specify multiple user groups in a CSV or a list format.
- Disable: Select to disable assigning the user to a group.
|
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"mkey": "",
"name": "",
"path": "",
"vdom": "",
"build": "",
"serial": "",
"status": "",
"version": "",
"revision": "",
"http_method": "",
"http_status": "",
"old_revision": "",
"revision_changed": ""
}
operation: Get Users
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the user for whom to retrieve data from the Fortinet FortiGate server |
| Start |
Specify the starting entry index from where to retrieve users from the Fortinet FortiGate server. |
| Count |
Specify the maximum number of users to return. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"name": "",
"path": "",
"vdom": "",
"build": "",
"serial": "",
"status": "",
"results": [
{
"id": "",
"name": "",
"type": "",
"q_ref": "",
"passwd": "",
"q_name": "",
"q_path": "",
"q_type": "",
"status": "",
"q_class": "",
"email-to": "",
"q_static": "",
"css-class": "",
"q_no_edit": "",
"sms-phone": "",
"fortitoken": {
"datasource": "",
"q_origin_key": "",
"serial-number": ""
},
"ppk-secret": "",
"sms-server": "",
"two-factor": "",
"authtimeout": "",
"ldap-server": "",
"passwd-time": "",
"q_mkey_type": "",
"q_no_rename": "",
"workstation": "",
"ppk-identity": "",
"q_origin_key": "",
"passwd-policy": "",
"radius-server": "",
"q_global_entry": "",
"tacacs+-server": {
"name": "",
"datasource": "",
"q_origin_key": ""
},
"sms-custom-server": "",
"auth-concurrent-value": "",
"two-factor-notification": "",
"auth-concurrent-override": "",
"two-factor-authentication": "",
"username-case-sensitivity": ""
}
],
"version": "",
"revision": "",
"http_method": "",
"http_status": ""
}
operation: Update User
Input parameters
| Parameter |
Description |
| User Type |
Select user type based on which to update a user. You can choose from following options:
- Local User: Specify values in following fields:
- Username: Specify the existing username of the user to be updated in the Fortinet FortiGate server
- New Username: (Optional) Specify the new username of the existing user to be updated in the Fortinet FortiGate server
- Password: (Optional) Specify a new password for the user to be updated in the Fortinet FortiGate server
- Remote Radius User: Specify values in following fields:
- Username: Specify the existing username of the user to be updated in the Fortinet FortiGate server
- New Username: (Optional) Specify the new username of the existing user to be updated in the Fortinet FortiGate server
- Radius Server: Specify the name of the RADIUS server using which the user gets authenticated
- Remote TACACS+ User: Specify values in following fields:
- Username: Specify the existing username of the user to be updated in the Fortinet FortiGate server
- New Username: (Optional) Specify the new username of the existing user to be updated in the Fortinet FortiGate server
- TACACS+ Server: Specify the name of the TACACS+ server using which the user gets authenticated.
|
| Two Factor Authentication |
Select one of the following options for the two-factor authentication:
- Enable: Select to enable the two-factor authentication.
- Disable: Select to disable the two-factor authentication.
|
| Authentication Type |
Select the type of two-factor authentication for the user you are creating on Fortinet FortiGate. You can choose from following options:
- FortiToken: Select this option to use FortiToken as the authentication type.
- FortiToken Cloud: Select this option to use FortiToken Cloud as the authentication type.
|
| Token |
Specify the token name used to authenticate the user. |
| Send Activation Code |
Select one of the following options
- Enable: Select the method of sending the activation code from the Activation Method field. You can choose from following options:
- Disable: Select this option to disable sending of an activation code for two-factor authentication.
|
| Email Address |
Specify the email address of the user being updated on Fortinet FortiGate. |
| SMS |
Select from the following options:
- Enable: Select to enable SMS-based two-factor authentication for the user being created on Fortinet FortiGate. Specify values in the following fields:
- Country Dial Code: Specify the dial-code of the country where the user being created, works.
- Phone Number: Specify the mobile phone number of the user for two-factor authentication.
- Disable: Select to disable SMS-based two-factor authentication for the user being created on Fortinet FortiGate.
|
| User Account Status |
Select the account status of the user being created on Fortinet FortiGate. You can choose from following options:
|
| User Group Names To Add |
Specify the user group names, in CSV or list format, in which to add the user you are updating on Fortinet FortiGate. |
| User Group Names To Remove |
Enter the user group names, in the CSV or list format, from which to remove the user you are updating on Fortinet FortiGate. |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"mkey": "",
"name": "",
"path": "",
"vdom": "",
"build": "",
"serial": "",
"status": "",
"version": "",
"revision": "",
"http_method": "",
"http_status": "",
"revision_changed": ""
}
operation: Delete User
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the user to be deleted from Fortinet FortiGate |
| VDOM |
(Optional) Specify the Virtual Domain(VDOM) from which results are returned or on which to apply these changes.
NOTE: You can specify the VDOM here as a configuration parameter, in the CSV or List format, or you can specify VDOMs as a function parameter, i.e., in the Configuration parameters while configuring this connector. If both are specified, the one that is specified in this operation overwrites the one specified in the configuration parameters. If this parameter is not provided, the management VDOM is used. If the admin does not have access to the VDOM, a permission error will be returned. You must specify the parameter from one of the following: vdom=root (Single VDOM), vdom=vdom1,vdom2 (Multiple VDOMs), vdom=* (All VDOMs). |
Output
The output contains the following populated JSON schema:
{
"mkey": "",
"name": "",
"path": "",
"vdom": "",
"build": "",
"serial": "",
"status": "",
"version": "",
"revision": "",
"http_method": "",
"http_status": "",
"old_revision": "",
"revision_changed": ""
}
operation: Get System Events
Input parameters
| Parameter |
Description |
| Filter Query |
Specify the query using which to filter system events being retrieved from the Fortinet FortiGate server. For example, user=*"admin", level=*"emergency" |
| Start |
Specify the starting entry index from where to retrieve data from the Fortinet FortiGate server. |
| Rows |
Specify the maximum number of items to return. |
Output
The output contains the following populated JSON schema:
{
"http_method": "",
"results": [
{
"date": "",
"time": "",
"eventtime": "",
"tz": "",
"logid": "",
"type": "",
"subtype": "",
"level": "",
"vd": "",
"logdesc": "",
"user": "",
"action": "",
"msg": "",
"_metadata": {
"#": "",
"logid": "",
"timestamp": "",
"roll": ""
}
}
],
"vdom": "",
"device": "",
"category": "",
"subcategory": "",
"start": "",
"rows": "",
"session_id": "",
"completed": "",
"total_lines": "",
"now": "",
"status": "",
"serial": "",
"version": "",
"build": ""
}
operation: Get User Last Login Details
Input parameters
| Parameter |
Description |
| Username |
Specify the username to retrieve their last login details from the Fortinet FortiGate server. |
Output
The output contains the following populated JSON schema:
{
"date": "",
"time": "",
"eventtime": "",
"tz": "",
"logid": "",
"type": "",
"subtype": "",
"level": "",
"vd": "",
"logdesc": "",
"sn": "",
"user": "",
"ui": "",
"method": "",
"srcip": "",
"dstip": "",
"action": "",
"status": "",
"reason": "",
"profile": "",
"msg": "",
"_metadata": {
"#": "",
"logid": "",
"timestamp": "",
"roll": ""
}
}
Included playbooks
The Sample - Fortinet FortiGate - 5.2.3 playbook collection comes bundled with the Fortinet FortiGate connector. These playbooks contain steps using which you can perform all supported actions. You can see bundled playbooks in the Automation > Playbooks section in FortiSOARTM after importing the Fortinet FortiGate connector.
- Address Group: Create Address Group
- Address Group: Delete Address Group
- Address Group: Get Address Groups
- Address Group: Update Address Group
- Address: Block IP Address
- Address: Create Address
- Address: Delete Address
- Address: Get Addresses
- Address: Get Blocked IP Addresses
- Address: Unblock IP Address
- Address: Update Address
- Application: Block Application
- Application: Get Applications Detail
- Application: Get Blocked Applications
- Application: Unblock Application
- Execute Command
- Get System Events
- Host: Get Quarantine Hosts
- Host: Quarantine Host
- Host: Unquarantine Host
- Policy: Create Policy
- Policy: Delete Policy
- Policy: Get List of Policies
- Policy: Update Policy
- Service Group: Create Service Group
- Service Group: Delete Service Group
- Service Group: Get Service Groups
- Service Group: Update Service Group
- Service: Create Service
- Service: Delete Service
- Service: Get Services
- Service: Update Service
- URL: Block URL
- URL: Get Blocked URLs
- URL: Unblock URL
- User: Create User
- User: Delete User
- User: Get User Last Login Details
- User: Update User
- Users: Get Users
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection, since the sample playbook collection gets deleted during connector upgrade and delete.
Blocking or Unblocking IP addresses, URLs, or applications on Fortinet FortiGate
- Log on to the Fortinet FortiGate server with the necessary credentials.
- To block or unblock an IP address, you must create a policy for IP addresses on the Fortinet FortiGate server. The following steps define the process of adding a policy:
- In
Policy & Objects, click Addresses to create an address group with the following conditions:
- Category = IPv4 Group
- Group Name = Blocked_IPs
- Type = Group
- Member = none
- NOTE: You can create different address groups for source and destination.
For more information on creating address groups and address group exclusions, see the FortiOS 7.2.3 Address Group Exclusion.
NOTE: For IPv6 addresses, you can specify the Category as IPv6 Group.
- In
Policy & Objects, click Firewall Policy to create a policy for IPv4 with the following conditions:
- Name = FortiSOAR_Blocked_Policy
- Source = Blocked_IPs
- Destination = Blocked_IPs
- Schedule = always
- Service = ALL
- Action = DENY
- Enable this policy = Enable
- In
Policy & Objects, click Firewall Policy and enter the firewall policy name as the Action parameter. For our example, we have named this as FortiSOAR_Blocked_Policy. When you are configuring your Fortinet FortiGate connector in FortiSOAR™, you must use the policy name that you have specified in this step as your Policy Name action parameter.
For more information on the firewall policy, see Firewall Policy in the FortiOS documentation.
NOTE: If your VDOM's NGFW Mode is Policy Based then click on Security Policy in Policy & Object to create policy.
- To block or unblock a URL, you must create a profile for blocking or unblocking static URLs on the Fortinet FortiGate server. For information on creating web filters, see Web Filter in the FortiOS 7.2.3 Administration Guide.
- The following steps define the process of adding a policy:
- In
Security Profiles, click Web Filter to create a new profile for blocking or unblocking static URLs or use the default profile.
NOTE: Ensure that the URL Filter is enabled.
- Enter the Web Filter Profile name on the configuration page. For our example, we have named this URL Block Policy. When you are configuring your Fortinet FortiGate connector in FortiSOAR™, you must use the Web Filter Profile name that you have specified in this step as your
Web Filter Profile Name configuration parameter.
- To block or unblock an application, you must create a profile for blocking or unblocking applications on the Fortinet FortiGate server. The following steps define the process of adding a policy:
- In
Security Profiles, click Application Control to create a new profile for blocking or unblocking applications or use the default profile.
- Enter the policy name on the configuration page. For our example, we have named this App Block Policy. When you are configuring your Fortinet FortiGate connector in FortiSOAR™, you must use the Application Control Profile name that you have specified in this step as your
Application Control Profile Name configuration parameter.
For information on adding application controls, see Application Control FortiOS 7.2.3 Administration Guide.







