About the connector
Fortinet FortiManager provides easy centralized configuration, policy-based provisioning, update management, and end-to-end network monitoring for your Fortinet installed environment.
This document provides information about the Fortinet FortiManager Connector, which facilitates automated interactions with your Fortinet FortiManager server using FortiSOAR™ playbooks. Add the Fortinet FortiManager connector, as a step in FortiSOAR™ playbooks and perform automated operations such as retrieving a list of all devices configured on the Fortinet FortiManager server, creating and updating incidents on the Fortinet FortiManager server, and retrieving a list of all incidents from the Fortinet FortiManager server.
You can use FortiSOAR™'s Data Ingestion Wizard to easily ingest data into FortiSOAR™ by pulling incidents from Fortinet FortiManager. For more information, see the Data Ingestion Support section.
Version information
Connector Version: 3.0.0
FortiSOAR™ Version Tested on: 7.0.2-664
Fortinet FortiManager Version Tested on: FortiManager VM64-KVM v7.0.1 Interim build4653
Authored By: Fortinet
Certified: Yes
Release Notes for version 3.0.0
Following changes have been made to the Fortinet FortiManager Connector in version 3.0.0:
- Added the following new operations and playbooks:
- Get Device Groups List
- Create Address
- Get Addresses List
- Update Address
- Delete Address
- Create Address Group
- Get Address Groups List
- Update Address Group
- Delete Address Group
- Get Service Categories List
- Create Service Group
- Get Service Groups List
- Update Service Group
- Delete Service Group
- Create Custom Service
- Get Custom Services List
- Update Custom Service
- Delete Custom Service
- Create Policy Package
- Update Policy Package
- Delete Policy Package
- Create Firewall Policy
- Update Firewall Policy
- Delete Firewall Policy
- Move Firewall Policy
- Get Dynamic Interface List
- Install Policy
- Get Installation Policy Package Status
- Create LDAP Server
- Get LDAP Server List
- Update LDAP Server
- Delete LDAP Server
- Create User Group
- Get User Groups List
- Update User Group
- Delete User Group
- Get SSL VPN Settings
- Update SSL VPN Settings
- Get Web Filter List
- Get Blocked URLs
- Block URL
- Unblock URL
- Get Applications Detail
- Get Applications Control List
- Get Blocked Applications
- Block Application
- Unblock Application
- Updated the names of the following operations and playbooks:
- List ADOM IPv4 Policy updated to List ADOM Firewall Policies
- List Global IPv4 Policy updated to List Global Firewall Policies
- Renamed the 'IPv4' configuration parameter to 'Firewall' across all the operations.
Installing the connector
Use the Connector Store to install the connector. For the detailed procedure to install a connector, click here.
You can also use the following yum command as a root user to install connectors from an SSH session:
yum install cyops-connector-fortinet-fortimanager
Prerequisites to configuring the connector
- You must have the IP address or hostname of the Fortinet FortiManager server to which you will connect and perform automated operations and credentials (username-password pair) to access that server.
- You must enable "FortiAnalyzer Features" in FortiManager to perform the following operations:
- Create Incident
- List Incident
- Get Events Related to Incident
- Get Events
- Get Events Details
- Update Incident
- You must enable "Administrative Domain" features in FortiManager.
- The FortiSOAR™ server should have outbound connectivity to port 443 on the Fortinet FortiManager server.
- You must add the configurations required to block or unblock IP addresses, URLs, or applications in Fortinet FortiManager. For more information, see the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager
-
Log on to the Fortinet FortiManager server with the necessary credentials.
-
To block or unblock an IP address, you must create a policy for IP addresses on the Fortinet FortiManager server. The following steps define the process of adding a policy:
- In
Policy & Objects > Policy Packages, click IPv4 Policy or Firewall Policy to create a policy for IPv4 with the following conditions.
IPv4 Source Address = Blocked_IPs
IPv4 Destination Address = Blocked_IPs
Schedule = always
Service = ALL
Action = DENY
Note: You can create an IPv6 policy in a similar manner.
For more information on address group exclusions, see the Create a new object topic in the FortiManager 6.2.2 Administration Guide.
- In
Policy & Objects > Object Configuration, click Address Group to create an address group with the following conditions.
Group Name = Blocked_IPs
Member = none
Show in address list = enable
For more information on creating address groups and address group exclusions, see the IP policies topic in the FortiManager 6.2.2 Administration Guide.
- To block or unblock a URL, you must create a profile for blocking or unblocking static URLs on the Fortinet FortiManager server. For information on creating web filters, see 'Web Filter' topic in the https://docs.fortinet.com/document/fortimanager/6.2.2/administration-guide/795923/web-filter document. The following steps define the process of adding a policy:
- In Security Profiles, click Web Filter to create a new profile for blocking or unblocking static URLs or use the default profile.
Note: Ensure that the "URL Filter" is enabled.
- Enter the Web Filter Profile name on the action page. For our example, we have named this 'URL Block Policy'.
- To block or unblock an application, you must create a profile for blocking or unblocking applications on the Fortinet FortiManager server. The following steps define the process of adding a policy:
- In Security Profiles, click Application Control to create a new profile for blocking or unblocking applications or use the default profile.
- Enter the policy name on the configuration page. For our example, we have named this?'App Block Policy'. When you are configuring your Fortinet FortiManager connector in FortiSOAR™, you must use the Application Control Profile name that you have specified in this step as your 'Application Control Profile Name' action parameter.
For information on adding application controls, see the 'Application Control' topic in the https://docs.fortinet.com/document/fortimanager/6.2.2/administration-guide/966512/application-control document.
- Users who are configuring Fortinet FortiManager for the first time have to perform the following steps for the 'Install' Policy:
- Add devices to the “Installation Targets” where the user wants to install the IPv4/Firewall policy.
- Navigate to the Device Manager select the Device that is specified in the installation target and click Install.
- Click Install Policy Package & Device Settings and select the policy package where the IPv4 Policy or Firewall Policy is created.
- Run the 'Install Wizard' completely.
- Users who are configuring Fortinet FortiManager for the first time have to perform the following steps for the 'Assign Global Policy Package':
- Add ADOM to the “Assignment” where the user wants to assign the Global Policy Package. For more information see the Assign a global policy package section in the FortiManager document
- Select the ADOM that you have specified in the assignment.
- Run the 'Assign Wizard' completely.
Minimum Permissions Required
The minimum privileges that require to be assigned to users who are going to use this connector and run actions on Fortinet FortiManager are:
Configuring the connector
For the procedure to configure a connector, click here.
Configuration parameters
In FortiSOAR™, on the Connectors page, click the Fortinet FortiManager connector row (if you are in the Grid view on the Connectors page), and in the Configurations tab enter the required configuration details.
| Parameter |
Description |
| Hostname |
IP address or Hostname of the Fortinet FortiManager endpoint server to which you will connect and perform the automated operations. |
| Username |
Username to access the Fortinet FortiManager server to which you will connect and perform the automated operations. |
| Password |
Password to access the Fortinet FortiManager server to which you will connect and perform the automated operations. |
| ADOM |
Administrative domain names (ADOMs) of the Fortinet FortiManager server to which you will connect and perform the automated operations. Enter the ADOMs, in the CSV or List format. |
| Port |
Port number used to access the Fortinet FortiManager server to which you will connect and perform the automated operations. By default, this is set to 443. |
| Verify SSL |
Specifies whether the SSL certificate for the server is to be verified or not.
By default, this option is set as True. |
Actions supported by the connector
The following automated operations can be included in playbooks, and you can also use the annotations to access operations:
| Function |
Description |
Annotation and Category |
| Create Incident |
Creates an incident in Fortinet FortiManager based on the reporter name, endpoint name, and other input parameters you have specified. |
create_incident
Investigation |
| List Incident |
Retrieves a list of all incidents or specific incidents from Fortinet FortiManager based on the search parameters you have specified. |
get_incidents
Investigation |
| Get Events Related to Incident |
Retrieves details of events associated with a Fortinet FortiManager incident, based on the incident ID and other input parameters you have specified. |
get_incident_events
Investigation |
| Get Device List |
Retrieves a list of all devices or specific devices from Fortinet FortiManager based on the search parameters you have specified.
Note: If a parameter is left blank or null, then this operation will return devices matching all values. |
get_devices
Investigation |
| Get Events |
Retrieves a list of all events or specific events from Fortinet FortiManager based on the search parameters you have specified.
Note: If a parameter is left blank or null, then this operation will return events matching all values. |
get_alert_event
Investigation |
| Get Event Details |
Retrieves a list of event details (logs) from Fortinet FortiManager based on the alert IDs and other search parameters you have specified. |
get_alert_logs
Investigation |
| Update Incident |
Update an incident in Fortinet FortiManager based on the incident ID and other input parameters you have specified. |
create_incident
Investigation |
| List ADOM Policy Package |
Retrieves a list of all ADOM policy packages or specific ADOM policy packages from Fortinet FortiManager based on the search parameters you have specified. |
get_adom_policy_package
Investigation |
| List ADOM Firewall Policies |
Retrieves a list of all ADOM firewall policies or specific ADOM firewall policies from Fortinet FortiManager based on the search parameters you have specified. |
get_adom_policy
Investigation |
| ADOM Level Get Blocked IP Addresses |
Retrieves a list of ADOM level IP Addresses that are blocked on Fortinet FortiGate through Fortinet FortiManager based on the firewall policy, address group name, and other input parameters you have specified. |
get_blocked_ip
Investigation |
| ADOM Level Block IP Address |
Blocks IP addresses at the ADOM level on Fortinet FortiGate based on the Firewall policy, address group name, and other input parameters you have specified. |
block_ip
Containment |
| ADOM Level Unblock IP Address |
Unlocks IP addresses at the ADOM level on Fortinet FortiGate based on the Firewall policy, address group name, and other input parameters you have specified. |
unblock_ip
Remediation |
| Re-install Policy |
Reinstalls a Firewall Policy in Fortinet FortiManager based on the ADOM Name and policy package name you have specified. |
reinstall_policy
Investigation |
| List Global Policy Package |
Retrieves a list of all policy packages or specific policy packages from Fortinet FortiManager based on the search parameters you have specified. |
get_global_policy_package
Investigation |
| List Global Firewall Policies |
Retrieves a list of all global firewall policies or specific firewall policies from Fortinet FortiManager based on the search parameters you have specified. |
get_global_policy
Investigation |
| Global Level Get Blocked IP Addresses |
Retrieves a list of Global (header/footer policy) level IP Addresses that are blocked on Fortinet FortiGate through Fortinet FortiManager based on the firewall policy, address group name, and other input parameters you have specified. |
get_blocked_ip
Investigation |
| Global Level Block IP Address |
Blocks IP addresses at the global level on Fortinet FortiGate based on the firewall header/footer policy, address group name, and other input parameters you have specified. |
block_ip
Containment |
| Global Level Unblock IP Address |
Unblocks IP addresses at the global level on Fortinet FortiGate based on the firewall header/footer policy, address group name, and other input parameters you have specified. |
unblock_ip
Remediation |
| Assign Global Policy Package |
Assigns a global policy package to ADOM packages in Fortinet FortiManager based on the policy package name, ADOM devices, and other input parameters you have specified. |
global_assign_policy
Investigation |
| Get Device Groups List |
Retrieves a list of all device groups or specific device groups from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_device_groups
Investigation |
| Create Address |
Creates an address in Fortinet FortiManager based on the address name, level type, and other input parameters you have specified. |
create_address
Investigation |
| Get Addresses List |
Retrieves a list of addresses or specific addresses from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_addresses
Investigation |
| Update Address |
Updates an address in Fortinet FortiManager based on the address name, level type, and other input parameters you have specified. |
update_address
Investigation |
| Delete Address |
Deletes an address from Fortinet FortiManager based on the level type you have specified. |
delete_address
Investigation |
| Create Address Group |
Creates an address group in Fortinet FortiManager based on the address name, level type, and other input parameters you have specified. |
create_address_group
Investigation |
| Get Address Groups List |
Retrieves a list of address groups or specific address groups from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_address_groups
Investigation |
| Update Address Group |
Updates an existing address group in Fortinet FortiManager based on the level type, method, and other input parameters you have specified. |
update_address_group
Investigation |
| Delete Address Group |
Deletes an address group from Fortinet FortiManager based on the level type you have specified. |
delete_address_group
Investigation |
| Get Service Categories List |
Retrieves a list of service categories or specific service categories from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_service_categories
Investigation |
| Create Service Group |
Creates a service group in Fortinet FortiManagerin Fortinet FortiManager based on the level type, members, and other input parameters you have specified. |
create_service_group
Investigation |
| Get Service Groups List |
Retrieves a list of address groups or specific address groups from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_service_group
Investigation |
| Update Service Group |
Updates an existing service group in Fortinet FortiManager based on the level type, method, and other input parameters you have specified. |
update_service_group
Investigation |
| Delete Service Group |
Deletes a service group from Fortinet FortiManager based on the level type you have specified. |
delete_service_group
Investigation |
| Create Custom Service |
Creates a custom service in Fortinet FortiManager based on the level type and other input parameters you have specified. |
create_custom_service
Investigation |
| Get Custom Services List |
Retrieves a list of custom services or specific custom services from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_custom_service
Investigation |
| Update Custom Service |
Updates an existing custom service in Fortinet FortiManager based on the level type and other input parameters you have specified. |
update_custom_service
Investigation |
| Delete Custom Service |
Deletes a custom service from Fortinet FortiManager based on the level type you have specified. |
delete_custom_service
Investigation |
| Create Policy Package |
Creates a policy package in Fortinet FortiManager based on the level type, package type, and other input parameters you have specified. |
create_policy_package
Investigation |
| Update Policy Package |
Updates a policy package in Fortinet FortiManager based on the level type and other input parameters you have specified. |
update_policy_package
Investigation |
| Delete Policy Package |
Deletes a policy package from Fortinet FortiManager based on the level type and other input parameters you have specified. |
delete_policy_package
Investigation |
| Create Firewall Policy |
Creates a firewall policy in Fortinet FortiManager based on the level type, package type, policy package name, and other input parameters you have specified. |
create_policy
Investigation |
| Update Firewall Policy |
Updates a firewall policy in Fortinet FortiManager based on the level type, package type, policy package name, and other input parameters you have specified. |
update_policy
Investigation |
| Delete Firewall Policy |
Deletes a firewall policy in Fortinet FortiManager based on the level type, policy ID, policy package name, and other input parameters you have specified. |
delete_policy
Investigation |
| Move Firewall Policy |
Moves a firewall policy in Fortinet FortiManager based on the level type, policy ID, policy package name, target, and other input parameters you have specified. |
move_policy
Investigation |
| Get Dynamic Interface List |
Retrieves a list of all dynamic interfaces or specific dynamic interfaces from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_dynamic_interface
Investigation |
| Install Policy |
Installs a policy package on Fortinet FortiManager based on the ADOM, policy package name, and other input parameters you have specified. |
install_policy
Investigation |
| Get Installation Policy Package Status |
Retrieves the status of installation for a specific policy package from Fortinet FortiManager based on the task ID you have specified. |
install_policy_status
Investigation |
| Create LDAP Server |
Creates an LDAP server in Fortinet FortiManager based on the level type, LDAP server name, username, password, and other input parameters you have specified. |
create_ldap_server
Investigation |
| Get LDAP Server List |
Retrieves a list of LDAP servers or specific LDAP servers from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_ldap_server
Investigation |
| Update LDAP Server |
Updates an LDAP server in Fortinet FortiManager based on the level type, LDAP server name, and other input parameters you have specified. |
update_ldap_server
Investigation |
| Delete LDAP Server |
Deletes an LDAP server from Fortinet FortiManager based on the level type, LDAP server name, and other input parameters you have specified. |
delete_ldap_server
Investigation |
| Create User Group |
Creates a user group in Fortinet FortiManager based on the level type, group name, members list, and other input parameters you have specified. |
create_user_group
Investigation |
| Get User Groups List |
Retrieves a list of all user groups or specific user groups from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_user_group
Investigation |
| Update User Group |
Updates a user group in Fortinet FortiManager based on the level type, group name, change in the members' list, and other input parameters you have specified. |
update_user_group
Investigation |
| Delete User Group |
Deletes a user group from Fortinet FortiManager based on the level type, group name, and other input parameters you have specified. |
delete_user_group
Investigation |
| Get SSL VPN Settings |
Retrieves SSL VPN settings from Fortinet FortiManager based on the device name, VDOM, and other search parameters you have specified. |
get_ssl_vpn
Investigation |
| Update SSL VPN Settings |
Updates an SSL VPN settings in Fortinet FortiManager based on the device name, VDOM, and input search parameters you have specified. |
update_ssl_vpn
Investigation |
| Get Web Filter List |
Retrieves a list all of web filters or specific web filters from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_web_filter
Investigation |
| Get Blocked URLs |
Retrieves a list of URLs that are blocked on Fortinet FortiManager based on the specified web filter profile name, level type, and other search parameters you have specified. |
get_blocked_urls
Investigation |
| Block URL |
Blocks URLs on Fortinet FortiManager using the Web Filter Profile Name you have specified. |
block_url
Containment |
| Unblock URL |
Unblocks URLs on Fortinet FortiManager using the Web Filter Profile Name you have specified. |
unblock_url
Containment |
| Get Applications Detail |
Retrieves a list of all application names and associated details from the Fortinet FortiManager server. |
get_app_details
Investigation |
| Get Applications Control List |
Retrieves a list all of application control profiles or specific application control profiles from Fortinet FortiManager based on the level type and other search parameters you have specified. |
get_application_control_list
Investigation |
| Get Blocked Applications |
Retrieves a list of application names that are blocked on Fortinet FortiManager based on the specified application control name, level type, and other search parameters you have specified. |
get_blocked_app
Investigation |
| Block Application |
Blocks applications on Fortinet FortiManager using the Application Control Profile Name you have specified. |
block_application
Containment |
| Unblock Application |
Unblocks applications on Fortinet FortiManager using the Application Control Profile Name you have specified. |
unblock_applications
Containment |
operation: Create Incident
Input parameters
| Parameter |
Description |
| ADOM |
(Optional) The administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Reporter |
Name of the reporter of the incident that you want to create in Fortinet FortiManager. For example, admin. |
| Endpoint Name |
Details of the endpoint affected by the incident that you want to create in Fortinet FortiAnalyzer. For example, 11.XXX.YY.Z/32 (11.XXX.YY.Z) or 11.XXX.YY.Z/32 (Emp1 Laptop). |
| Endpoint ID |
(Optional) Endpoint ID that you want to assign to the incident you want to create in Fortinet FortiManager. |
| End User ID |
(Optional) End-user ID that you want to assign to the incident you want to create in Fortinet FortiManager. |
| Category |
(Optional) The category you want to assign to the incident you want to create in Fortinet FortiManager. You can choose from the following options: Unauthorized access, Denial of Service, Malicious Code, Improper Usage, Scans/Probes/Attempted Access, or Uncategorized. |
| Severity |
(Optional) The severity level you want to assign to the incident you want to create in Fortinet FortiManager. You can choose from the following options: High, Medium, or Low. |
| Status |
(Optional) The status you want to assign to the incident you want to create in Fortinet FortiManager. You can choose from the following options: New, Analysis, Response, Closed: Remediated, or Closed: False Positive. |
| Description |
(Optional) Description of the new incident that you want to create in Fortinet FortiManager. |
Output
The output contains the following populated JSON schema:
{
"jsonrpc": "",
"id": "",
"result": {
"incid": ""
}
}
operation: List Incident
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| ADOM |
The administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Incident ID |
The ID of incidents in CSV or list format that you want to retrieve from Fortinet FortiManager. |
| Detail Level |
Level of detail of the incidents that you want to retrieve from Fortinet FortiManager. By default, this is set to "Standard". |
| Filter |
Query in the format of field_name="field_value" using which you want to filter incidents to be retrieved from Fortinet FortiManager
For example category="CAT2" and severity="medium" |
| Sort By |
Sorts the incidents by the specified field and order the results.
If you choose "Field", then you can specify the following parameters:
- In the Field field specify the name of the field on which you want to sort the result. For example, severity, category, etc.
- (Optional) In the Order field choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
| Limit |
The maximum number of records that this operation should return. Values supported are: Default "50", Minimum "1" and Maximum "2000". |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
Output
The output contains the following populated JSON schema:
Output schema when you choose “Detail Level” as 'Basic':
{
"jsonrpc": "",
"id": "",
"result": {
"status": {
"code": "",
"message": ""
},
"detail-level": "",
"data": [
{
"attach_revision": "",
"attach_lastupdate": "",
"lastupdate": "",
"revision": "",
"incid": ""
}
]
}
}
Output schema when you choose “Detail Level” as 'Extended':
{
"result": {
"data": [
{
"endpoint": "",
"euname": "",
"epip": "",
"status": "",
"incid": "",
"attachments": [
{
"lastupdate": "",
"attachid": "",
"revision": ""
}
],
"lastupdate": "",
"osversion": "",
"attach_lastupdate": "",
"euid": "",
"category": "",
"epid": "",
"epname": "",
"revision": "",
"reporter": "",
"createtime": "",
"description": "",
"osname": "",
"mac": "",
"lastuser": "",
"severity": "",
"attach_revision": "",
"refinfo": ""
}
],
"detail-level": "",
"status": {
"message": "",
"code": ""
}
},
"id": "",
"jsonrpc": ""
}
Output schema when you choose “Detail Level” as 'Standard' or you do not select any detail level:
{
"result": {
"data": [
{
"endpoint": "",
"reporter": "",
"createtime": "",
"description": "",
"status": "",
"incid": "",
"severity": "",
"lastuser": "",
"attach_lastupdate": "",
"lastupdate": "",
"euid": "",
"attach_revision": "",
"category": "",
"refinfo": "",
"epid": "",
"revision": ""
}
],
"detail-level": "",
"status": {
"message": "",
"code": ""
}
},
"id": "",
"jsonrpc": ""
}
operation: Get Events Related to Incident
Input parameters
| Parameter |
Description |
| ADOM |
(Optional) The administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Incident ID |
The ID of the incident whose associated events you want to retrieve from Fortinet FortiManager. |
| Attachment Type |
Types of attachment that you want to search for in Fortinet FortiManager. Valid types include: Alert Event, Log, Comment, Log Search Filter, Upload File, or Report. |
| Limit |
The maximum number of records that this operation should return. Values supported are: Default "50", Minimum "1" and Maximum "2000". |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
Output
The output contains the following populated JSON schema:
{
"result": {
"data": [
{
"attachtype": "",
"lastupdate": "",
"incid": "",
"attachid": "",
"createtime": "",
"data": "",
"lastuser": "",
"revision": ""
}
],
"status": {
"message": "",
"code": ""
}
},
"id": "",
"jsonrpc": ""
}
operation: Get Device List
Input parameters
| Parameter |
Description |
| ADOM |
(Optional) The administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Device Name |
Valid device name based on which you want to retrieve details of devices from Fortinet FortiManager.
Note: If a parameter is left blank or null, then this operation will return devices matching all values. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
},
"data": [
{
"os_ver": "",
"build": "",
"ips_ext": "",
"foslic_inst_time": "",
"mgmt.__data[5]": "",
"lic_region": "",
"latitude": "",
"foslic_ram": "",
"faz.perm": "",
"branch_pt": "",
"ips_ver": "",
"foslic_utm": "",
"source": "",
"foslic_cpu": "",
"mgmt.__data[3]": "",
"mgmt.__data[2]": "",
"ha_mode": "",
"opts": "",
"last_resync": "",
"foslic_last_sync": "",
"conn_status": "",
"mgmt.__data[7]": "",
"patch": "",
"hw_rev_minor": "",
"mgmt.__data[1]": "",
"psk": "",
"checksum": "",
"faz.quota": "",
"ha_group_id": "",
"adm_usr": "",
"ha_group_name": "",
"faz.used": "",
"tunnel_cookie": "",
"conf_status": "",
"mgmt.__data[6]": "",
"last_checked": "",
"version": "",
"mgmt.__data[0]": "",
"ha_slave": "",
"name": "",
"longitude": "",
"platform_str": "",
"foslic_dr_site": "",
"tunnel_ip": "",
"oid": "",
"foslic_type": "",
"prefer_img_ver": "",
"location_from": "",
"vm_cpu_limit": "",
"mgmt_if": "",
"faz.full_act": "",
"av_ver": "",
"fex_cnt": "",
"fsw_cnt": "",
"mgmt.__data[4]": "",
"vm_mem": "",
"sn": "",
"logdisk_size": "",
"lic_flags": "",
"hostname": "",
"vm_mem_limit": "",
"vdom": [
{
"tab_status": "",
"opmode": "",
"name": "",
"devid": "",
"rtm_prof_id": "",
"status": "",
"comments": "",
"oid": "",
"ext_flags": "",
"node_flags": "",
"vpn_id": "",
"flags": ""
}
],
"tab_status": "",
"adm_pass": [],
"mgmt_id": "",
"beta": "",
"dev_status": "",
"os_type": "",
"vm_lic_expire": "",
"mgmt_mode": "",
"hdisk_size": "",
"ip": "",
"vm_status": "",
"db_status": "",
"mr": "",
"module_sn": "",
"hw_rev_major": "",
"flags": "",
"desc": "",
"app_ver": "",
"maxvdom": "",
"vm_cpu": "",
"conn_mode": "",
"node_flags": "",
"fap_cnt": "",
"mgt_vdom": ""
}
]
}
]
}
operation: Get Events
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| ADOM |
The administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Filter |
Filter expression using which you want to retrieve events from Fortinet FortiManager.
'event_value', 'severity', 'triggername', 'count', 'comment' and 'flags' are supported.
For example, triggername='Local Device Event' and severity>=3 or subject='desc:User login from SSH failed' |
| Time Range |
Select this checkbox to specify the time range for which you want to retrieve events from Fortinet FortiManager.
If you select this checkbox, then you must specify the following parameters:
- Start Time: Starting DateTime from when you want to retrieve events from Fortinet FortiManager.
Consider the timezone as Fortinet FortiAnalyzer's timezone, if the timezone info is not specified.
Format: 'yyyy-MM-dd'T'HH:mm:ssZ' (RFC 3339) e.g. '2016-10-17T20:45:37-07:00 or 'yyyy-MM-dd HH:mm:ss' e.g. '2016-10-17 20:45:37'
- End Time: Ending DateTime till when you want to retrieve events from Fortinet FortiManager.
Consider the timezone as Fortinet FortiAnalyzer's timezone, if the timezone info is not specified.
Format: 'yyyy-MM-dd'T'HH:mm:ssZ' (RFC 3339) e.g. '2016-10-17T20:45:37-07:00 or 'yyyy-MM-dd HH:mm:ss' e.g. '2016-10-17 20:45:37'
|
| Limit |
The maximum number of records that this operation should return. Values supported are: Default "50", Minimum "1" and Maximum "2000". |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
Output
The output contains the following populated JSON schema:
{
"jsonrpc": "",
"result": {
"data": [
{
"alerttime": "",
"triggername": "",
"devname": "",
"vdom": "",
"filterid": "",
"filterkey": "",
"devtype": "",
"eventtype": "",
"groupby1": "",
"euid": "1",
"subject": "",
"devid": "",
"alertid": "",
"extrainfo": "",
"euname": "",
"epname": "",
"ackflag": "",
"logcount": "",
"filtercksum": "",
"tag": "",
"updatetime": "",
"epid": "1",
"severity": "",
"readflag": "",
"lastlogtime": "",
"firstlogtime": ""
}
]
},
"id": ""
}
operation: Get Event Details
Input parameters
| Parameter |
Description |
| ADOM |
(Optional) The administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Alert ID |
The ID of alerts in CSV or list format whose event details (logs) you want to retrieve from Fortinet FortiManager.
Note: You can find the "Alert IDs" using the "Get Events" action. |
| Time Order |
Select the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Descending. |
| Limit |
The maximum number of records that this operation should return. Values supported are: Default "50", Minimum "1" and Maximum "2000". |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": {
"data": [
{
"log_id": "",
"devname": "",
"userfrom": "",
"time": "",
"dstepid": "",
"desc": "",
"user": "",
"dtime": "",
"msg": "",
"type": "",
"devid": "",
"dsteuid": "",
"euid": "",
"date": "",
"idseq": "",
"itime_t": "",
"epid": "",
"subtype": "",
"level": "",
"itime": ""
}
]
},
"jsonrpc": ""
}
operation: Update Incident
Input parameters
| Parameter |
Description |
| ADOM |
(Optional) The administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Incident ID |
The ID of the incident that you want to update in FortiManager. |
| Endpoint Name |
Details of the endpoint affected by the incident that you want to update in Fortinet FortiAnalyzer. For example, 11.XXX.YY.Z/32 (11.XXX.YY.Z) or 11.XXX.YY.Z/32 (Emp1 Laptop). |
| Endpoint ID |
(Optional) Endpoint ID that you want to assign to the incident you want to update in Fortinet FortiManager.
|
| End User ID |
(Optional) End-user ID that you want to assign to the incident you want to update in Fortinet FortiManager. |
| Category |
(Optional) The category you want to assign to the incident you want to update in Fortinet FortiManager. You can choose from the following options: Unauthorized access, Denial of Service, Malicious Code, Improper Usage, Scans/Probes/Attempted Access, or Uncategorized. |
| Severity |
(Optional) The severity level you want to assign to the incident you want to update in Fortinet FortiManager. You can choose from the following options: High, Medium, or Low. |
| Status |
(Optional) The status you want to assign to the incident you want to update in Fortinet FortiManager. You can choose from the following options: New, Analysis, Response, Closed: Remediated, or Closed: False Positive. |
| Description |
(Optional) Description of the incident that you want to update in Fortinet FortiManager. |
| Last Revision |
(Optional) Last version of the incident that you want to update in Fortinet FortiManager. |
| Last User |
(Optional) Last user of the incident that you want to update in Fortinet FortiManager. |
Output
The output contains the following populated JSON schema:
{
"jsonrpc": "",
"id": "",
"result": {
"status": {
"code": "",
"message": ""
}
}
}
operation: List ADOM Policy Package
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| ADOM Name |
Specify the ADOM name whose policy package you want to retrieve from Fortinet FortiManager. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Policy Package Name |
Select the policy package name whose details you want to retrieve from Fortinet FortiManager This parameter makes an API call named "list_adom_policy_package" to dynamically populate its dropdown selection. |
| Policy Package/Folder Path |
Specify the policy package or folder path of the ADOM policy package whose details you want to retrieve from Fortinet FortiManager. |
Output
The output contains the following populated JSON schema:
Output schema when the 'Policy Package Name' is empty
{
"result": [
{
"data": [
{
"type": "",
"package settings": {
"consolidated-firewall-mode": "",
"fwpolicy6-implicit-log": "",
"fwpolicy-implicit-log": "",
"ngfw-mode": "",
"central-nat": ""
},
"oid": "",
"name": "",
"scope member": [
{
"vdom": "",
"name": ""
}
],
"obj ver": ""
}
],
"url": "",
"status": {
"code": "",
"message": ""
}
}
],
"id": ""
}
Default Output schema
{
"id": "",
"result": [
{
"status": {
"code": "",
"message": ""
},
"data": {
"obj ver": "",
"name": "",
"type": "",
"scope member": [
{
"name": "",
"vdom": ""
}
],
"oid": "",
"package settings": {
"ngfw-mode": "",
"consolidated-firewall-mode": "",
"fwpolicy6-implicit-log": "",
"fwpolicy-implicit-log": "",
"central-nat": ""
}
},
"url": ""
}
]
}
operation: List ADOM Firewall Policies
Input parameters
| Parameter |
Description |
| ADOM Name |
(Optional) Specify the ADOM name whose ADOM firewall policy you want to retrieve from Fortinet FortiManager. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Policy Package Name |
Select the policy package name whose firewall policy details you want to retrieve from Fortinet FortiManager. This parameter makes an API call named "list_adom_policy_package" to dynamically populate its dropdown selection. |
| Policy Package/Folder Path |
(Optional) Specify the policy package or folder path of the ADOM firewall policy whose details you want to retrieve from Fortinet FortiManager. |
| Firewall Policy Name |
(Optional) Specify the firewall policy name whose details you want to retrieve from Fortinet FortiManager. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": [
{
"_last_hit": "",
"_byte": "",
"custom-log-fields": [],
"_pkts": "",
"anti-replay": "",
"_first_hit": "",
"webproxy-profile": [],
"delay-tcp-npu-session": "",
"dstaddr-negate": "",
"tcp-mss-receiver": "",
"internet-service": "",
"srcaddr": [],
"traffic-shaper": [],
"vpn_dst_node": "",
"match-vip-only": "",
"_hitcount": "",
"schedule": [],
"fsso-agent-for-ntlm": [],
"permit-any-host": "",
"schedule-timeout": "",
"radius-mac-auth-bypass": "",
"email-collect": "",
"name": "",
"ssl-mirror-intf": [],
"status": "",
"policyid": "",
"vlan-cos-fwd": "",
"vpn_src_node": "",
"nat": "",
"block-notification": "",
"logtraffic-start": "",
"per-ip-shaper": [],
"tos-negate": "",
"traffic-shaper-reverse": [],
"logtraffic": "",
"np-acceleration": "",
"session-ttl": "",
"uuid": "",
"service-negate": "",
"srcaddr-negate": "",
"wccp": "",
"_policy_block": "",
"action": "",
"groups": [],
"fsso": "",
"tos": "",
"internet-service-src": "",
"utm-status": "",
"natip": [],
"capture-packet": "",
"dstaddr": [],
"tcp-mss-sender": "",
"_first_session": "",
"_sesscount": "",
"_global-vpn-tgt": "",
"srcintf": [],
"tcp-session-without-syn": "",
"timeout-send-rst": "",
"ssl-ssh-profile": [],
"fsso-groups": [],
"service": [],
"vlan-cos-rev": "",
"captive-portal-exempt": "",
"users": [],
"app-group": [],
"webcache-https": "",
"geoip-anycast": "",
"diffserv-forward": "",
"profile-type": "",
"rtp-nat": "",
"reputation-direction": "",
"disclaimer": "",
"webproxy-forward-server": [],
"inspection-mode": "",
"obj seq": "",
"auto-asic-offload": "",
"_global-vpn": [],
"ssl-mirror": "",
"dstintf": [],
"_last_session": "",
"match-vip": "",
"diffserv-reverse": "",
"dsri": "",
"tos-mask": "",
"reputation-minimum": "",
"profile-protocol-options": [],
"replacemsg-override-group": []
}
],
"status": {
"message": "",
"code": ""
},
"url": ""
}
]
}
operation: ADOM Level Get Blocked IP Addresses
Input parameters
| Parameter |
Description |
| ADOM |
(Optional) Specify the ADOM name whose associated list of blocked IP addresses you want to retrieve from Fortinet FortiManager. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Policy Package Name |
Select the policy package name whose associated blocked IP addresses you want to retrieve from Fortinet FortiManager. This parameter makes an API call named "list_adom_policy_package" to dynamically populate its dropdown selection. |
| Policy Package/Folder Path |
(Optional) Specify the policy package or folder path of the ADOM Firewall policy whose associated blocked IP addresses you want to retrieve from Fortinet FortiManager. |
| Firewall Policy Name |
Specify the Firewall policy name associated with the blocked IP addresses you want to retrieve from Fortinet FortiManager. |
| Address Group Name |
Name of the IP address group name, in the "CSV" or "list" format, that you have specified in Fortinet FortiManager for blocking or unblocking IP addresses. For more information, see the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section. |
Output
The output contains the following populated JSON schema:
{
"policy_name": "",
"dstaddr": [],
"srcaddr": [],
"addrgrp": [
{
"name": "",
"member": []
}
],
"addrgrp_not_exist": []
}
operation: ADOM Level Block IP Address
Input parameters
| Parameter |
Description |
| ADOM Name |
(Optional) Specify the ADOM name whose associated IP addresses you want to block in the firewall policy of Fortinet FortiManager. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Policy Package Name |
Select the policy package name whose associated IP addresses you want to block in the firewall policy of Fortinet FortiManager. This parameter makes an API call named "list_adom_policy_package" to dynamically populate its dropdown selection. |
| Policy Package/Folder Path |
(Optional) Specify the policy package or folder path of the ADOM firewall policy whose associated IP addresses you want to block in Fortinet FortiManager. |
| Firewall Policy Name |
Name of the firewall policy that you have specified in Fortinet FortiManager for blocking or unblocking IP addresses. |
| Address Group Name |
Name of the IP address group name that you have specified in Fortinet FortiManager for blocking or unblocking IP addresses. For more information, see the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section. |
| IP Address |
Specify the IP addresses that you want to block using Fortinet FortiManager in the "CSV" or "list" format. For example, ["1.1.1.1", "2.2.2.2"] or "1.1.1.1", "2.2.2.2". |
Output
The output contains the following populated JSON schema:
{
"already_blocked": [],
"newly_blocked": [],
"error_with_block": []
}
operation: ADOM Level Unblock IP Address
Input parameters
| Parameter |
Description |
| ADOM Name |
(Optional) Specify the ADOM name whose associated IP addresses you want to unblock in the firewall policy of Fortinet FortiManager. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Policy Package Name |
Select the policy package name whose associated IP addresses you want to unblock in the firewall policy of Fortinet FortiManager. This parameter makes an API call named "list_adom_policy_package" to dynamically populate its dropdown selection. |
| Policy Package/Folder Path |
(Optional) Specify the policy package or folder path of the ADOM firewall policy whose associated IP addresses you want to unblock in Fortinet FortiManager. |
| Firewall Policy Name |
Name of the firewall Policy that you have specified in Fortinet FortiManager for blocking or unblocking IP addresses. |
| Address Group Name |
Name of the IP address group name, that you have specified in Fortinet FortiManager for blocking or unblocking IP addresses. For more information, see the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section. |
| IP Address |
Specify the IP addresses that you want to unblock using Fortinet FortiManager in the "CSV" or "list" format. For example, ["1.1.1.1", "2.2.2.2"] or "1.1.1.1", "2.2.2.2". |
Output
The output contains the following populated JSON schema:
{
"not_exist": [],
"newly_unblocked": [],
"error_with_unblock": []
}
operation: Re-install Policy
Input parameters
| Parameter |
Description |
| ADOM Name |
(Optional) Specify the ADOM name to which you want to apply the firewall policy in Fortinet FortiManager. The ADOM that you specify here will overwrite the ADOM that you have specified in the 'Connector Configuration' as a configuration parameter. |
| Policy Package Name |
Select the policy package name to which you want to apply the firewall policy in Fortinet FortiManager. This parameter makes an API call named "list_adom_policy_package" to dynamically populate its dropdown selection. |
| Policy Package/Folder Path |
(Optional) Specify the policy package or folder path to apply the firewall policy in Fortinet FortiManager. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": {
"task": ""
},
"status": {
"message": "",
"code": ""
},
"url": ""
}
]
}
operation: List Global Policy Package
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| Package Name |
Specify the name of the global policy package name from which you want to retrieve package details. |
| Policy Package/Folder Path |
Specify the policy package or folder path from which you want to retrieve package details. |
Output
The output contains the following populated JSON schema:
Output schema when the 'Policy Package Name' is empty
{
"result": [
{
"url": "",
"data": [
{
"type": "",
"package settings": {
"ngfw-mode": "",
"central-nat": "",
"consolidated-firewall-mode": "",
"fwpolicy-implicit-log": "",
"fwpolicy6-implicit-log": ""
},
"scope member": [
{
"name": ""
}
],
"obj ver": "",
"name": "",
"oid": ""
}
],
"status": {
"message": "",
"code": ""
}
}
],
"id": ""
}
Default Output schema
{
"result": [
{
"url": "",
"data": {
"type": "",
"package settings": {
"ngfw-mode": "",
"central-nat": "",
"consolidated-firewall-mode": "",
"fwpolicy-implicit-log": "",
"fwpolicy6-implicit-log": ""
},
"scope member": [
{
"name": ""
}
],
"obj ver": "",
"name": "",
"oid": ""
},
"status": {
"message": "",
"code": ""
}
}
],
"id": ""
}
operation: List Global Firewall Policies
Input parameters
| Parameter |
Description |
| Policy Package Name |
Specify the name of the global firewall policy package from which you want to retrieve package details. This parameter makes an API call named "list_global_policy_pck" to dynamically populate its dropdown selections. |
| Policy Package/Folder Path |
(Optional) Specify the policy package or folder path from which you want to retrieve package details. |
| Policy Type |
Select the policy type from which you want to retrieve firewall policy details. |
| Policy Name |
(Optional) Specify the name of the global firewall policy whose details you want to retrieve from Fortinet FortiManager. |
Output
The output contains the following populated JSON schema:
{
"result": [
{
"url": "",
"data": [
{
"ssl-ssh-profile": [],
"_pkts": "",
"disclaimer": "",
"diffserv-reverse": "",
"replacemsg-override-group": [],
"dstaddr": [],
"per-ip-shaper": [],
"vlan-cos-rev": "",
"schedule": [],
"wccp": "",
"_byte": "",
"status": "",
"groups": [],
"block-notification": "",
"_global-vpn": [],
"webcache-https": "",
"obj seq": "",
"utm-status": "",
"webproxy-profile": [],
"tcp-mss-receiver": "",
"tos-negate": "",
"profile-type": "",
"reputation-minimum": "",
"timeout-send-rst": "",
"policyid": "",
"dstaddr-negate": "",
"traffic-shaper": [],
"profile-protocol-options": [],
"internet-service": "",
"reputation-direction": "",
"natip": [],
"session-ttl": "",
"vlan-cos-fwd": "",
"delay-tcp-npu-session": "",
"webproxy-forward-server": [],
"email-collect": "",
"np-acceleration": "",
"fsso-agent-for-ntlm": [],
"identity-based-policy": "",
"name": "",
"tos": "",
"_first_session": "",
"uuid": "",
"_sesscount": "",
"match-vip": "",
"logtraffic": "",
"schedule-timeout": "",
"traffic-shaper-reverse": [],
"tos-mask": "",
"permit-any-host": "",
"anti-replay": "",
"capture-packet": "",
"ssl-mirror-intf": [],
"srcaddr": [],
"service": [],
"internet-service-src": "",
"dstintf": [],
"_last_hit": "",
"_hitcount": "",
"_first_hit": "",
"gtp-profile": [],
"radius-mac-auth-bypass": "",
"diffserv-forward": "",
"geoip-anycast": "",
"tcp-mss-sender": "",
"app-group": [],
"rtp-nat": "",
"inspection-mode": "",
"tcp-session-without-syn": "",
"logtraffic-start": "",
"auto-asic-offload": "",
"action": "",
"fsso-groups": [],
"fsso": "",
"_global-vpn-tgt": "",
"captive-portal-exempt": "",
"users": [],
"custom-log-fields": [],
"dsri": "",
"srcintf": [],
"nat": "",
"service-negate": "",
"match-vip-only": "",
"ssl-mirror": "",
"_last_session": "",
"srcaddr-negate": ""
}
],
"status": {
"message": "",
"code": ""
}
}
],
"id": ""
}
operation: Global Level Get Blocked IP Addresses
Input parameters
| Parameter |
Description |
| Policy Package Name |
Specify the name of the global firewall policy whose associated blocked IP addresses you want to retrieve from Fortinet FortiManager. This parameter makes an API call named "list_global_policy_pck" to dynamically populate its dropdown selections. |
| Policy Package/Folder Path |
(Optional) Specify the policy package or folder path of the global firewall policy whose associated blocked IP addresses you want to retrieve from Fortinet FortiManager. |
| Policy Type |
Select policy type based on which you want to retrieve blocked IP addresses from Fortinet FortiManager. |
| Firewall Policy Name |
Specify the firewall policy name associated with the blocked IP addresses you want to retrieve from Fortinet FortiManager. |
| Address Group Name |
Name of the IP address group name, in the "CSV" or "list" format, that you have specified in Fortinet FortiManager for blocking or unblocking IP addresses. For more information, see the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section. |
Output
The output contains the following populated JSON schema:
{
"policy_name": "",
"dstaddr": [],
"srcaddr": [],
"addrgrp": [
{
"name": "",
"member": []
}
],
"addrgrp_not_exist": []
}
operation: Global Level Block IP Address
Input parameters
| Parameter |
Description |
| Policy Package Name |
Select the policy package whose associated IP addresses you want to block in the global firewall policy of Fortinet FortiManager. This parameter makes an API call named "list_global_policy_pck" to dynamically populate its dropdown selections. |
| Policy Package/Folder Path |
(Optional) Specify the policy package or folder path of the global firewall policy whose associated IP addresses you want to block in Fortinet FortiManager. |
| Policy Type |
Select policy type whose IP addresses you want to block in Fortinet FortiManager. |
| Firewall Policy Name |
Name of the firewall Policy that you have specified in Fortinet FortiManager for blocking or blocking IP addresses. |
| Address Group Name |
Name of the IP address group name, that you have specified in Fortinet FortiManager for blocking or unblocking IP addresses. For more information, see the Blocking or Unblocking IP addresses, URLs or applications in Fortinet FortiManager section. |
| IP Address |
IP addresses that you want to block using Fortinet FortiManager in the "CSV" or "list" format.For example, ["1.1.1.1", "2.2.2.2"] or "1.1.1.1", "2.2.2.2". |
Output
The output contains the following populated JSON schema:
{
"already_blocked": [],
"newly_blocked": [],
"error_with_block": []
}
operation: Global Level Unblock IP Address
Input parameters
| Parameter |
Description |
| Policy Package Name |
Select the policy package whose associated IP addresses you want to unblock in the global firewall policy of Fortinet FortiManager. This parameter makes an API call named "list_global_policy_pck" to dynamically populate its dropdown selections. |
| Policy Package/Folder Path |
(Optional) Specify the policy package or folder path of the global firewall policy whose associated IP addresses you want to unblock in Fortinet FortiManager. |
| Policy Type |
Select policy type whose IP addresses you want to unblock in Fortinet FortiManager. |
| Firewall Policy Name |
Name of the firewall Policy that you have specified in Fortinet FortiManager for blocking or blocking IP addresses. |
| Address Group Name |
Name of the IP address group name, that you have specified in Fortinet FortiManager for blocking or unblocking IP addresses. For more information, see the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section. |
| IP Address |
IP addresses that you want to unblock using Fortinet FortiManager in the "CSV" or "list" format.For example, ["1.1.1.1", "2.2.2.2"] or "1.1.1.1", "2.2.2.2". |
Output
The output contains the following populated JSON schema:
{
"not_exist": [],
"newly_unblocked": [],
"error_with_unblock": []
}
operation: Assign Global Policy Package
Input parameters
| Parameter |
Description |
| Policy Package Name |
Select the policy package that you want to assign to ADOM devices in the global firewall policy of Fortinet FortiManager. This parameter makes an API call named "list_global_policy_pck" to dynamically populate its dropdown selections. |
| Policy Package/Folder Path |
Specify the policy package or folder path of the global policy package that you want to assign to ADOM devices in Fortinet FortiManager. |
| ADOM Devices |
Specify one or more destination ADOMs to which you want to assign the selected global policy package. This parameter makes an API call named "list_global_adom" to dynamically populate its dropdown selections. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": {
"task": ""
},
"status": {
"message": "",
"code": ""
},
"url": ""
}
]
}
operation: Get Device Groups List
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to retrieve the device group details. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Device Group: Valid device group name based on which you want to retrieve details of device group from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return devices matching all values.
If you choose 'Global', then you can specify the following parameters:
- Device Group: Valid device group name based on which you want to retrieve details of device group from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return devices matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, [ "desc", "name", "os_type", "type"]. If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying one of the attributes. Attributes are desc, name, os_type, type. For example, [["name", "==", "All_FortiADC"],[ "os_type", "==", 9]] |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the device groups by the specified field and order the results. You can choose to either sort the results by fields, or can order the results, or both.
If you choose 'Field', then you must specify the following parameters:
- Field: Specify the name of the field on which you want to sort the result. For example, severity, category, etc.
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": {
"oid": "",
"desc": "",
"name": "",
"type": "",
"os_type": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Create Address
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to create the address. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Address Name: Valid address name that you want to create in Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Address Name: Valid address name that you want to create in Fortinet FortiManager.
|
| Address Type |
Choose the type of address you want to create in Fortinet FortiManager. You can select between Subnet, IP Range, FQDN, Wildcard, Geography, or MAC Address.
If you choose 'Subnet', then you can specify the following parameters:
- Subnet: Specify the IP address and subnet mask of the address that you want to create.
- Subnet Name: Specify the Subnet name of the address that you want to create.
If you choose 'IP Range', then you can specify the following parameters:
- Start IP: Specify the starting (First) IP address (inclusive) in the IP address range to be assigned to the address you want to create.
- End IP: Specify the ending (Final) IP address (inclusive) in the IP address range to be assigned to the address you want to create.
If you choose 'FQDN', then you can specify the following parameters:
- FQDN: Specify the Fully Qualified Domain Name of the address that you want to create.
If you choose 'Wildcard', then you can specify the following parameters:
- Wildcard: Specify the IP address and wildcard netmask of the address that you want to create.
If you choose 'Geography', then you can specify the following parameters:
- Country: Specify the country whose IP addresses you want to associate with the address you want to create.
If you choose 'MAC Address', then you can specify the following parameters:
- MAC Address Scope: Select the MAC Address Scope to be associated with the address that you want to create. You can choose between Single Address, Range, or MAC List.
- If you choose 'Single Address', then you can specify the following parameters
- MAC Address: The single MAC address to be added to the address you want to create. For example,
00:15:00:e8:27:25
- If you choose 'Range', then you can specify the following parameters:
- MAC Address Start: Starting (First) MAC address in the range for the address to be added to the address you want to create. For example,
00:15:00:e8:27:25
- MAC Address End: Ending (Final) MAC address in the range for the address to be added to the address you want to create. For example,
00:15:00:e8:27:27
- If you choose 'MAC List', then you can specify the following parameters:
- MAC Address: Specify a CSV or list of MAC addresses to be added to the address you want to create. For example,
["00:15:00:e8:27:25","00:15:00:e8:27:26",]
|
| Policy Group Name |
(Optional) Specify the name of the policy group to be added to the address that you want to create. |
| Comment |
(Optional) Comment to be added to the address that you want to create. |
| Additional Address Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the address. You can enter the arguments in the following format: {"field1":value1, "field2":value2} |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Get Addresses List
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to retrieve the address details. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Address Name: Valid address name based on which you want to retrieve address details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return addresses matching all values.
If you choose 'Global', then you can specify the following parameters:
- Address Name: Valid address name based on which you want to retrieve address details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return addresses matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, [ "_image-base64", "allow-routing", "associated-interface", "cache-ttl", "clearpass-spt", "color", "comment", "country", "end-ip", "epg-name", "fabric-object", "filter", "fqdn", "fsso-group", "interface", "macaddr", "name", "node-ip-only", "obj-id", "obj-tag", "obj-type", "organization", "policy-group", "sdn", "sdn-addr-type", "sdn-tag", "start-ip", "sub-type", "subnet", "subnet-name", "tenant", "type", "uuid", "wildcard", "wildcard-fqdn"]
Note: If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying attributes. |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the addresses by the specified field and order the results. You can choose to either sort the results by fields, or can order the results, or both.
If you choose 'Field', then you must specify the following parameters:
- Field: Specify the name of the field on which you want to sort the result. For example,
_image-base64, allow-routing, associated-interface, cache-ttl, clearpass-spt, color, comment, country, end-ip, epg-name, fabric-object, filter, fqdn, fsso-group, interface, macaddr, name, node-ip-only, obj-id, obj-tag, obj-type, organization, policy-group, sdn, sdn-addr-type, sdn-tag, start-ip, sub-type, subnet, subnet-name, tenant, type, uuid, wildcard, wildcard-fqdn, etc.
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
},
"data": [
{
"list": "",
"name": "",
"type": "",
"uuid": "",
"color": "",
"subnet": [],
"comment": "",
"macaddr": [],
"tagging": "",
"obj-type": "",
"node-ip-only": "",
"allow-routing": "",
"clearpass-spt": "",
"fabric-object": "",
"sdn-addr-type": "",
"dynamic_mapping": "",
"associated-interface": []
}
]
}
]
}
operation: Update Address
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to update the address. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Address Name: Valid address name that you want to update in Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Address Name: Valid address name that you want to update in Fortinet FortiManager.
|
| Address Type |
Choose the type of address you want to update in Fortinet FortiManager. You can select between Subnet, IP Range, FQDN, Wildcard, Geography, or MAC Address.
If you choose 'Subnet', then you can specify the following parameters:
- Subnet: Specify the IP address and subnet mask of the address that you want to update.
- Subnet Name: Specify the Subnet name of the address that you want to update.
If you choose 'IP Range', then you can specify the following parameters:
- Start IP: Specify the starting (First) IP address (inclusive) in the IP address range to be assigned to the address you want to update.
- End IP: Specify the ending (Final) IP address (inclusive) in the IP address range to be assigned to the address you want to update.
If you choose 'FQDN', then you can specify the following parameters:
- FQDN: Specify the Fully Qualified Domain Name of the address that you want to update.
If you choose 'Wildcard', then you can specify the following parameters:
- Wildcard: Specify the IP address and wildcard netmask of the address that you want to update.
If you choose 'Geography', then you can specify the following parameters:
- Country: Specify the country whose IP addresses you want to associate with the address you want to update.
If you choose 'MAC Address', then you can specify the following parameters:
- MAC Address Scope: Select the MAC Address Scope to be associated with the address that you want to update. You can choose between Single Address, Range, or MAC List.
- If you choose 'Single Address', then you can specify the following parameters
- MAC Address: The single MAC address to be added to the address you want to update. For example,
00:15:00:e8:27:25
- If you choose 'Range', then you can specify the following parameters:
- MAC Address Start: Starting (First) MAC address in the range for the address to be added to the address you want to update. For example,
00:15:00:e8:27:25
- MAC Address End: Ending (Final) MAC address in the range for the address to be added to the address you want to update. For example,
00:15:00:e8:27:27
- If you choose 'MAC List', then you can specify the following parameters:
- MAC Address: Specify a CSV or list of MAC addresses to be added to the address you want to update. For example,
["00:15:00:e8:27:25","00:15:00:e8:27:26",]
|
| Policy Group Name |
(Optional) Specify the name of the policy group to be added to the address that you want to update. |
| Comment |
(Optional) Comment to be added to the address that you want to update. |
| Additional Address Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the updation of the address. You can enter the arguments in the following format: {"field1":value1, "field2":value2}. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Delete Address
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to delete the address. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Address Name: Valid address name that you want to delete from Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Address Name: Valid address name that you want to delete from Fortinet FortiManager.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Create Address Group
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to create the address group. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Address Group Name: Valid address group name that you want to create in Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Address Group Name: Valid address group name that you want to create in Fortinet FortiManager.
|
| Type |
Choose the type of address group you want to create in Fortinet FortiManager. You can select between Group (default) or Folder.
- Group, is the Default address group type; in this case, members can belong to multiple groups
- Folder, address folder group; in this case, members cannot belong to any other group.
|
| Member |
Specify a CSV list or a list of address objects or address groups that you want to add to the address group that you want to create in Fortinet FortiManager. |
| Exclude |
Select this option, i.e., set it to true to enable address exclusion and if this option is selected, then in the Exclude Member field specify a CSV list or a list of address objects or address groups that you want to add to the exclusion member list. |
| Comment |
(Optional) Comment to be added to the address group that you want to create. |
| Additional Address Group Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the address group. You can enter the arguments in the following format: {"field1":value1, "field2":value2} |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Get Address Groups List
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to retrieve the address group details. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Address Group Name: Valid address group name based on which you want to retrieve address group details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return address groups matching all values.
If you choose 'Global', then you can specify the following parameters:
- Address Group Name: Valid address group name based on which you want to retrieve address group details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return address groups matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, [ "_image-base64", "allow-routing", "associated-interface", "cache-ttl", "clearpass-spt", "color", "comment", "country", "end-ip", "epg-name", "fabric-object", "filter", "fqdn", "fsso-group", "interface", "macaddr", "name", "node-ip-only", "obj-id", "obj-tag", "obj-type", "organization", "policy-group", "sdn", "sdn-addr-type", "sdn-tag", "start-ip", "sub-type", "subnet", "subnet-name", "tenant", "type", "uuid", "wildcard", "wildcard-fqdn"]
Note: If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying attributes. |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the address groups by the specified field and order the results. You can choose to either sort the results by fields, or can order the results, or both.
If you choose 'Field', then you must specify the following parameters:
- Field: Specify the name of the field on which you want to sort the result. For example,
_image-base64, allow-routing, category, color, comment, exclude, exclude-member, fabric-object, member, name, type, uuid etc.
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [
{
"name": "",
"type": "",
"uuid": "",
"color": "",
"member": [],
"exclude": "",
"tagging": "",
"category": "",
"allow-routing": "",
"fabric-object": "",
"exclude-member": [],
"dynamic_mapping": ""
}
],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Update Address Group
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to update the address group. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Address Group: Valid address group that you want to update in Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Address Group: Valid address group that you want to update in Fortinet FortiManager.
|
| Method |
Select the action that you want to perform on members of the address group. You can choose between Add or Remove.
- If you choose 'Add', then in the Add Member field, specify a CSV list or a list of address group objects that you want to add to the address group that you want to update in Fortinet FortiManager.
- If you choose 'Remove', then in the Remove Member field, specify a CSV list or a list of address group objects that you want to remove from the address group that you want to update in Fortinet FortiManager.
|
| Exclude |
Select this option, i.e., set it to true to enable address exclusion and if this option is selected, then specify the following:
- In the Add Exclude Member field specify a CSV list or a list of address objects or address groups that you want to add to the exclusion member list.
- In the Remove Exclude Member field specify a CSV list or a list of address objects or address groups that you want to remove from the exclusion member list.
|
| Comment |
(Optional) Comment to be added to the address group that you want to update. |
| Additional Address Group Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the updation of the address group. You can enter the arguments in the following format: {"field1":value1, "field2":value2} |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Delete Address Group
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to delete the address group. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Address Group Name: Valid address group name that you want to delete from Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Address Group Name: Valid address group name that you want to delete from Fortinet FortiManager.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Get Service Categories List
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to retrieve the service categories details. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Service Category Name: Valid service category name based on which you want to retrieve address group details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return service categories matching all values.
If you choose 'Global', then you can specify the following parameters:
- Service Category Name: Valid address name based on which you want to retrieve address group details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return service categories matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, ["comment", "fabric-object", "name"]
Note: If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying attributes. |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the service categories by the specified field and order the results. You can choose to either sort the results by fields, or can order the results, or both.
If you choose 'Field', then you must specify the following parameters:
- Field: Specify the name of the field on which you want to sort the result. For example,
comment, fabric-object, name etc.
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [
{
"name": "",
"comment": "",
"obj seq": "",
"fabric-object": ""
}
],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Create Service Group
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to create the service group. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Service Group: Valid service group to create in Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Sevice Group: Valid service group to create in Fortinet FortiManager.
|
| Member |
Specify a CSV list or a list of service objects that you want to add to the service group that you want to create in Fortinet FortiManager. |
| Proxy |
Select Enable to enable the web proxy service group or Disable to disable the web proxy service group. |
| Comment |
(Optional) Comment to be added to the service group that you want to create. |
| Additional Service Group Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the service group. You can enter the arguments in the following format: {"field1":value1, "field2":value2} |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Get Service Groups List
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to retrieve the service group details. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Service Group: Valid service group based on which you want to retrieve service group details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return service groups matching all values.
If you choose 'Global', then you can specify the following parameters:
- Service Category Name: Valid service group based on which you want to retrieve service group details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return service groups matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, ["color", "comment", "fabric-objec"t, "member", "name", "proxy"]
Note: If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying attributes. |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the service groups by the specified field and order the results. You can choose to either sort the results by fields, or can order the results, or both.
If you choose 'Field', then you must specify the following parameters:
- Field: Specify the name of the field on which you want to sort the result. For example, color, comment, fabric-object, member, name, proxy etc.
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [
{
"oid": "",
"name": "",
"member": []
}
],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Update Service Group
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to update the service group. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Service Group: Valid service group that you want to update in Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Service Group: Valid service group that you want to update in Fortinet FortiManager.
|
| Method |
Select the action that you want to perform on members of the service group. You can choose between Add or Remove.
- If you choose 'Add', then in the Add Member field, specify a CSV list or a list of service group objects that you want to add to the service group that you want to update in Fortinet FortiManager.
- If you choose 'Remove', then in the Remove Member field, specify a CSV list or a list of service group objects that you want to remove from the service group that you want to update in Fortinet FortiManager.
|
| Proxy |
Select Enable to enable the web proxy service group or Disable to disable the web proxy service group. |
| Comment |
(Optional) Comment to be added to the service group that you want to update. |
| Additional Service Group Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the updation of the address group. You can enter the arguments in the following format: {"field1":value1, "field2":value2} |
Output
The output contains a non-dictionary value.
operation: Delete Service Group
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to delete the service group. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Service Group: Valid service group that you want to delete from Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Service Group: Valid service group that you want to delete from Fortinet FortiManager.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Create Custom Service
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to create the custom service. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Custom Service Name: Valid custom service name that you want to create in Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Custom Service Name: Valid custom service name that you want to create in Fortinet FortiManager.
|
| Service Category |
(Optional) Specify the ID of the category of the custom service that you want to create in Fortinet FortiManager. |
| Proxy |
Select Enable to enable the web proxy service or Disable to disable the web proxy service.
If you choose Enable, then you can specify the following parameters:
- Protocol: (Optional) Select the protocol type based on IANA numbers for the custom service that you want to create in Fortinet FortiManager. You can choose between the following protocols: 'ALL', 'CONNECT', 'FTP', 'HTTP', 'SOCKS-TCP', or 'SOCKS-UDP'.
- If you choose 'ALL', 'CONNECT', 'FTP', 'HTTP', or 'SOCKS-TCP', then in the TCP Port Range field, specify multiple TCP port ranges for the custom service that you want to create in Fortinet FortiManager. For example,
0-64535:0-65535
- If you choose 'SOCKS-UDP', then in the UDP Port Range field, specify multiple UDP port ranges for the custom service that you want to create in Fortinet FortiManager.
If you choose Disable, then you can specify the following parameters:
- Protocol: (Optional) Select the protocol type based on IANA numbers for the custom service that you want to create in Fortinet FortiManager. You can choose between the following protocols: 'TCP/UDP/SCTP', 'ICMP', 'ICMP6', 'FQDN', or 'IP'.
- If you choose 'TCP/UDP/SCTP', then from the Protocol list, select the protocol that you want to apply to the custom service that you want to create in Fortinet FortiManager. Choose between TCP, UDP, or SCTP.
- If you choose 'TCP', then in the TCP Port Range field, specify multiple TCP port ranges for the custom service that you want to create in Fortinet FortiManager. For example,
0-64535:0-65535
- If you choose 'UDP', then in the UDP Port Range field, specify multiple UDP port ranges for the custom service that you want to create in Fortinet FortiManager.
- If you choose 'SCTP', then in the SCTP Port Range field, specify multiple SCTP port ranges for the custom service that you want to create in Fortinet FortiManager.
- Whether you choose TCP, UDP, or SCTP, in the IP/FQDN field, you must specify the fully qualified domain name for the custom service that you want to create in Fortinet FortiManager.
- If you choose 'ICMP' or 'ICMP6', then specify the following parameters:
- In the ICMP Code field, specify the ICMP code for the custom service that you want to create in Fortinet FortiManager.
- In the ICMP Type field, specify the ICMP type for the custom service that you want to create in Fortinet FortiManager.
- If you choose 'IP', then specify the following parameters:
- In the Protocol Number field, specify the IP protocol number for the custom service that you want to create in Fortinet FortiManager.
- In the ICMP Type field, specify the ICMP type for the custom service that you want to create in Fortinet FortiManager.
|
| App Category |
(Optional) Specify the ID of the application category for the custom service that you want to create in Fortinet FortiManager. |
| App Service Type |
Select the type of application service type for the custom service that you want to create in Fortinet FortiManager. You can choose between Disable (default), App ID, or App Category. |
| Application ID |
(Optional) Specify the ID of the application for the custom service that you want to create in Fortinet FortiManager. |
| ICMP Error Message |
Configure the type of ICMP error message verification for the custom service that you want to create in Fortinet FortiManager. You can choose between Disable, Default, or Strict. |
| Helper Name |
(Optional) Specify the helper name for the custom service that you want to create in Fortinet FortiManager. You can specify the following values: disable, auto, ftp, tftp, ras, h323, tns, mms, sip, pptp, rtsp, dns-udp, dns-tcp, pmap, rsh, dcerpc, mgcp, gtp-c, gtp-u, gtp-b, pfcp |
| Session TTL |
(Optional) Specify the TTL for the session (300 - 2764800, 0 = default) associated with the custom service that you want to create in Fortinet FortiManager. |
| TCP Halfclose Timer |
(Optional) Specify the wait time to close a TCP session waiting for an unanswered FIN packet (1 - 86400 sec, 0 = default) for the custom service that you want to create in Fortinet FortiManager. |
| TCP Halfopen Timer |
(Optional) Specify the wait time to open a TCP session waiting for an unanswered open session packet (1 - 86400 sec, 0 = default) for the custom service that you want to create in Fortinet FortiManager. |
| TCP Rst Timer |
(Optional) Set the length of the TCP CLOSE state in seconds (5 - 300 sec, 0 = default) for the custom service that you want to create in Fortinet FortiManager. |
| TCP Time-Wait Timer |
(Optional) Set the length of the TCP TIME-WAIT state in seconds (1 - 300 sec, 0 = default). for the custom service that you want to create in Fortinet FortiManager. |
| UDP Idle Timer |
(Optional) Specify UDP half-close timeout (0 - 86400 sec, 0 = default) for the custom service that you want to create in Fortinet FortiManager. |
| Comment |
(Optional) Comment to be added to the custom service that you want to create. |
| Additional Custom Service Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the custom service. You can enter the arguments in the following format: {"field1":value1, "field2":value2} |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Get Custom Services List
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to retrieve the custom service details. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Custom Service Name: Valid custom service name based on which you want to retrieve custom service details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return service categories matching all values.
If you choose 'Global', then you can specify the following parameters:
- Custom Service Name: Valid custom service name based on which you want to retrieve custom service details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return service categories matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, ["app-category", "app-service-type", "application", "category", "check-reset-range", "color", "comment", "fabric-object", "fqdn", "helper", "icmpcode", "icmptype", "iprange", "name", "protocol", "protocol-number", "proxy", "sctp-portrange", "session-ttl", "tcp-halfclose-timer", "tcp-halfopen-timer", "tcp-portrange", "tcp-rst-timer", "tcp-timewait-timer", "udp-idle-timer", "udp-portrange", "visibility"]
Note: If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying attributes. |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the device groups by the specified field and order the results. You can choose to either sort the results by fields, or can order the results, or both.
If you choose 'Field', then you must specify the following parameters:
- Field: Specify the name of the field on which you want to sort the result. For example,
color, comment, fabric-object, member, name, proxy, etc.
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [
{
"name": "",
"color": "",
"proxy": "",
"helper": "",
"iprange": "",
"obj seq": "",
"category": [],
"protocol": "",
"visibility": "",
"application": [],
"app-category": [],
"fabric-object": "",
"tcp-rst-timer": "",
"udp-portrange": [],
"protocol-number": "",
"app-service-type": ""
}
],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Update Custom Service
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to update the custom service. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Custom Service Name: Valid custom service name that you want to update in Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Custom Service Name: Valid custom service name that you want to update in Fortinet FortiManager.
|
| Service Category |
(Optional) Specify the ID of the category of the custom service that you want to update in Fortinet FortiManager. |
| Proxy |
Select Enable to enable the web proxy service or Disable to disable the web proxy service.
If you choose Enable, then you can specify the following parameters:
- Protocol: (Optional) Select the protocol type based on IANA numbers for the custom service that you want to update in Fortinet FortiManager. You can choose between the following protocols: 'ALL', 'CONNECT', 'FTP', 'HTTP', 'SOCKS-TCP', or 'SOCKS-UDP'.
- If you choose 'ALL', 'CONNECT', 'FTP', 'HTTP', or 'SOCKS-TCP', then in the TCP Port Range field, specify multiple TCP port ranges for the custom service that you want to update in Fortinet FortiManager. For example,
0-64535:0-65535
- If you choose 'SOCKS-UDP', then in the UDP Port Range field, specify multiple UDP port ranges for the custom service that you want to update in Fortinet FortiManager.
If you choose Disable, then you can specify the following parameters:
- Protocol: (Optional) Select the protocol type based on IANA numbers for the custom service that you want to update in Fortinet FortiManager. You can choose between the following protocols: 'TCP/UDP/SCTP', 'ICMP', 'ICMP6', 'FQDN', or 'IP'.
- If you choose 'TCP/UDP/SCTP', then from the Protocol list, select the protocol that you want to apply to the custom service that you want to update in Fortinet FortiManager. Choose between TCP, UDP, or SCTP.
- If you choose 'TCP', then in the TCP Port Range field, specify multiple TCP port ranges for the custom service that you want to update in Fortinet FortiManager. For example,
0-64535:0-65535
- If you choose 'UDP', then in the UDP Port Range field, specify multiple UDP port ranges for the custom service that you want to update in Fortinet FortiManager.
- If you choose 'SCTP', then in the SCTP Port Range field, specify multiple SCTP port ranges for the custom service that you want to update in Fortinet FortiManager.
- Whether you choose TCP, UDP, or SCTP, in the IP/FQDN field, you must specify the fully qualified domain name for the custom service that you want to update in Fortinet FortiManager.
- If you choose 'ICMP' or 'ICMP6', then specify the following parameters:
- In the ICMP Code field, specify the ICMP code for the custom service that you want to update in Fortinet FortiManager.
- In the ICMP Type field, specify the ICMP type for the custom service that you want to update in Fortinet FortiManager.
- If you choose 'IP', then specify the following parameters:
- In the Protocol Number field, specify the IP protocol number for the custom service that you want to update in Fortinet FortiManager.
- In the ICMP Type field, specify the ICMP type for the custom service that you want to update in Fortinet FortiManager.
|
| App Category |
(Optional) Specify the ID of the application category for the custom service that you want to update in Fortinet FortiManager. |
| App Service Type |
Select the type of application service type for the custom service that you want to update in Fortinet FortiManager. You can choose between Disable (default), App ID, or App Category. |
| Application ID |
(Optional) Specify the ID of the application for the custom service that you want to update in Fortinet FortiManager. |
| ICMP Error Message |
Configure the type of ICMP error message verification for the custom service that you want to update in Fortinet FortiManager. You can choose between Disable, Default, or Strict. |
| Helper Name |
(Optional) Specify the helper name for the custom service that you want to update in Fortinet FortiManager. You can specify the following values: disable, auto, ftp, tftp, ras, h323, tns, mms, sip, pptp, rtsp, dns-udp, dns-tcp, pmap, rsh, dcerpc, mgcp, gtp-c, gtp-u, gtp-b, pfcp |
| Session TTL |
(Optional) Specify the TTL for the session (300 - 2764800, 0 = default) associated with the custom service that you want to update in Fortinet FortiManager. |
| TCP Halfclose Timer |
(Optional) Specify the wait time to close a TCP session waiting for an unanswered FIN packet (1 - 86400 sec, 0 = default) for the custom service that you want to update in Fortinet FortiManager. |
| TCP Halfopen Timer |
(Optional) Specify the wait time to open a TCP session waiting for an unanswered open session packet (1 - 86400 sec, 0 = default) for the custom service that you want to update in Fortinet FortiManager. |
| TCP Rst Timer |
(Optional) Set the length of the TCP CLOSE state in seconds (5 - 300 sec, 0 = default) for the custom service that you want to update in Fortinet FortiManager. |
| TCP Time-Wait Timer |
(Optional) Set the length of the TCP TIME-WAIT state in seconds (1 - 300 sec, 0 = default). for the custom service that you want to update in Fortinet FortiManager. |
| UDP Idle Timer |
(Optional) Specify UDP half-close timeout (0 - 86400 sec, 0 = default) for the custom service that you want to update in Fortinet FortiManager. |
| Comment |
(Optional) Comment to be added to the custom service that you want to update. |
| Additional Custom Service Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the custom service. You can enter the arguments in the following format: {"field1":value1, "field2":value2} |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Delete Custom Service
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to delete the custom service. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Custom Service Name: Valid custom service name that you want to delete from Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Custom Service Name: Valid custom service name that you want to delete from Fortinet FortiManager.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Create Policy Package
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to create the policy package. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Policy Package Name: Valid policy package name that you want to create in Fortinet FortiManager.
|
| Package Type |
Select the type of package, either Package or Folder, for the policy package that you want to create in Fortinet FortiManager.
If you choose 'Package', then you can specify the following parameters:
- Policy Package Name: Specify the valid policy package name that you want to create in Fortinet FortiManager.
- NGFW Mode: Select the NGFW mode for the policy package that you want to create in Fortinet FortiManager. You can choose between Profile-based or Policy-based.
- If you choose 'Profile-based', then from the Central NAT field, select Enable if you want to enable the central NAT for the policy package that you want to create in Fortinet FortiManager, else select Disable.
If you choose 'Policy-based',the Central NAT field is disabled.
- Policy Offload Level: Select the policy offload level at which you want to create the policy package on Fortinet FortiManager. You can choose between Disable, Default, DoS Offload, or Full Offload.
- Consolidated Firewall Mode: Select Enable if you want to enable the consolidated firewall mode for the policy package that you want to create in Fortinet FortiManager, else select Disable.
- Firewall Policy Implicit Log: Select Enable if you want to enable the firewall policy implicit log for the policy package that you want to create in Fortinet FortiManager, else select Disable.
- Firewall Policy6 Implicit Log: Select Enable if you want to enable the firewall policy6 implicit log for the policy package that you want to create in Fortinet FortiManager, else select Disable.
- Inspection Mode: Select the Inspection mode for the policy package that you want to create in Fortinet FortiManager. You can choose between proxy or flow.
- SSL SSH Profile: Specify the SSL SSH Profile for the policy package that you want to create in Fortinet FortiManager.
If you choose 'Folder', then in the Policy Package Folder Name field, specify the valid policy package folder name that you want to create in Fortinet FortiManager.
|
| Additional Policy Package Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the policy package. You can enter the arguments in the following format: {"field1":value1, "field2":value2} |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Update Policy Package
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to update the policy package. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Policy Package Name: Valid policy package name that you want to update in Fortinet FortiManager.
|
| Package Type |
Select the type of package, either Package or Folder, for the policy package that you want to update in Fortinet FortiManager.
If you choose 'Package', then you can specify the following parameters:
- Policy Package Name: Specify the valid policy package name that you want to update in Fortinet FortiManager.
- NGFW Mode: Select the NGFW mode for the policy package that you want to update in Fortinet FortiManager. You can choose between Profile-based or Policy-based.
- If you choose 'Profile-based', then from the Central NAT field, select Enable if you want to enable the central NAT for the policy package that you want to update in Fortinet FortiManager, else select Disable.
If you choose 'Policy-based',the Central NAT field is disabled.
- Policy Offload Level: Select the policy offload level at which you want to update the policy package on Fortinet FortiManager. You can choose between Disable, Default, DoS Offload, or Full Offload.
- Consolidated Firewall Mode: Select Enable if you want to enable the consolidated firewall mode for the policy package that you want to update in Fortinet FortiManager, else select Disable.
- Firewall Policy Implicit Log: Select Enable if you want to enable the firewall policy implicit log for the policy package that you want to update in Fortinet FortiManager, else select Disable.
- Firewall Policy6 Implicit Log: Select Enable if you want to enable the firewall policy6 implicit log for the policy package that you want to update in Fortinet FortiManager, else select Disable.
- Inspection Mode: Select the Inspection mode for the policy package that you want to update in Fortinet FortiManager. You can choose between proxy or flow.
- SSL SSH Profile: Specify the SSL SSH Profile for the policy package that you want to update in Fortinet FortiManager.
If you choose 'Folder', then in the Policy Package Folder Name field, specify the valid policy package folder name that you want to update in Fortinet FortiManager.
|
| Additional Policy Package Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the policy package. You can enter the arguments in the following format: {"field1":value1, "field2":value2} |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Delete Policy Package
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to delete the policy package. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Policy Package Name: Valid policy package name that you want to delete from Fortinet FortiManager.
If you choose 'Global', then you can specify the following parameters:
- Policy Package Name: Valid policy package name that you want to delete from Fortinet FortiManager.
|
| Policy Package Path |
(Optional) Specify a valid path for the policy package you want to delete from Fortinet FortiManager. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Create Firewall Policy
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to create the firewall policy. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
If you choose 'Global', then you can specify the following parameters:
- Policy Type: Select the type of firewall policy you want to create in Fortinet FortiManager.
|
| Policy Package Name |
Specify a valid policy package name for the firewall policy you want to create in Fortinet FortiManager. |
| Policy Name |
Valid name of the policy name that you want to create in Fortinet FortiManager. |
| Source Interface |
Specify the Incoming (ingress) interface for the firewall policy you want to create in Fortinet FortiManager. |
| Destination Interface |
Specify the Outgoing (egress) interface for the firewall policy you want to create in Fortinet FortiManager. |
| Service |
Specify service and service group names for the firewall policy you want to create in Fortinet FortiManager. |
| Source IPv4 Address |
Specify source IPv4 address and address group names for the firewall policy you want to create in Fortinet FortiManager. |
| Source IPv6 Address |
Specify source IPv6 address and address group names for the firewall policy you want to create in Fortinet FortiManager. |
| Destination IPv4 Address |
Specify destination IPv4 address and address group names for the firewall policy you want to create in Fortinet FortiManager. |
| Destination IPv6 Address |
Specify destination IPv6 address and address group names for the firewall policy you want to create in Fortinet FortiManager. |
| Policy Action |
Select the policy action for the firewall policy you want to create in Fortinet FortiManager. You can choose from the following options:
- Accept: Allows sessions that match the firewall policy.
- Deny: Blocks sessions that match the firewall policy.
- IPSec: Firewall policy becomes a policy-based IPsec VPN policy.
|
| Status |
Select Enable to enable this firewall policy on Fortinet FortiManager. |
| Inspection Mode |
Select the Inspection mode for the firewall policy that you want to create in Fortinet FortiManager. You can choose between proxy or flow (default). |
| Schedule |
Specify the name for the schedule to be associated with the firewall policy that you want to create in Fortinet FortiManager. For example, always, none, etc. |
| Schedule Timeout |
Select Enable to enable forceful ending of current sessions when the schedule object times out. Select Disable to allow them to end from inactivity. |
| Comment |
(Optional) Comment to be added to the firewall policy that you want to create. |
| Log Traffic |
Select the method of logging traffic, i.e, logging of all sessions or security profile sessions. You can choose from the following:
- All: Logs all sessions accepted or denied by this policy.
- UTM: Logs traffic that has an applied security profile applied.
- Disable: Disables all logging for this policy.
|
| Additional Policy Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the firewall policy. You can enter the arguments in the following format: {"field1":value1, "field2":value2}.
For example, {"logtraffic-start": "disable", "radius-mac-auth-bypass": "disable", "profile-type": "single" } |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": {
"policyid": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
]
}
operation: Update Firewall Policy
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to update the firewall policy. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
If you choose 'Global', then you can specify the following parameters:
- Policy Type: Select the type of firewall policy you want to update in Fortinet FortiManager.
|
| Policy Package Name |
Specify a valid policy package name for the firewall policy you want to update in Fortinet FortiManager. |
| Policy Name |
Valid name of the policy name that you want to update in Fortinet FortiManager. |
| Method |
Select the action that you want to perform for updating the firewall policy in Fortinet FortiManager. You can choose between Add or Remove.
If you choose 'Add', then you can specify the following parameters:
- Add Source Interface: Specify the Incoming (ingress) interface that you want to add to the firewall policy you want to update in Fortinet FortiManager.
- Add Destination Interface: Specify the Outgoing (egress) interface that you want to add to the firewall policy you want to update in Fortinet FortiManager.
- Add Service: Specify service and service group names that you want to add to the firewall policy you want to update in Fortinet FortiManager.
- Add Source IPv4 Address: Specify source IPv4 address and address group names that you want to add to the firewall policy you want to update in Fortinet FortiManager.
- Add Source IPv6 Address: Specify source IPv6 address and address group names that you want to add to the firewall policy you want to update in Fortinet FortiManager.
- Add Destination IPv4 Address: Specify destination IPv4 address and address group names that you want to add to the firewall policy you want to update in Fortinet FortiManager.
- Add Destination IPv6 Address: Specify destination IPv6 address and address group names that you want to add to the firewall policy you want to update in Fortinet FortiManager.
If you choose 'Remove', then you can specify the following parameters:
- Add Source Interface: Specify the Incoming (ingress) interface that you want to remove from the firewall policy you want to update in Fortinet FortiManager.
- Add Destination Interface: Specify the Outgoing (egress) interface that you want to remove from the firewall policy you want to update in Fortinet FortiManager.
- Add Service: Specify service and service group names that you want to remove from the firewall policy you want to update in Fortinet FortiManager.
- Add Source IPv4 Address: Specify the source IPv4 address and address group names that you want to remove from the firewall policy you want to update in Fortinet FortiManager.
- Add Source IPv6 Address: Specify the source IPv6 address and address group names that you want to remove from the firewall policy you want to update in Fortinet FortiManager.
- Add Destination IPv4 Address: Specify the destination IPv4 address and address group names that you want to remove from the firewall policy you want to update in Fortinet FortiManager.
- Add Destination IPv6 Address: Specify the destination IPv6 address and address group names that you want to remove from the firewall policy you want to update in Fortinet FortiManager.
|
| Policy Action |
Select the policy action for the firewall policy you want to update in Fortinet FortiManager. You can choose from the following options:
- Accept: Allows sessions that match the firewall policy.
- Deny: Blocks sessions that match the firewall policy.
- IPSec: Firewall policy becomes a policy-based IPsec VPN policy.
|
| Status |
Select Enable to enable this firewall policy on Fortinet FortiManager. |
| Inspection Mode |
Select the Inspection mode for the firewall policy that you want to create in Fortinet FortiManager. You can choose between proxy or flow (default). |
| Schedule |
Specify the name for the schedule to be associated with the firewall policy that you want to create in Fortinet FortiManager. For example, always, none,etc. |
| Schedule Timeout |
Select Enable to enable forceful ending of current sessions when the schedule object times out. Select Disable to allow them to end from inactivity. |
| Comment |
(Optional) Comment to be added to the firewall policy that you want to create. |
| Additional Policy Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the updation of the firewall policy. You can enter the arguments in the following format: {"field1":value1, "field2":value2}. For example, {"radius-mac-auth-bypass": "disable", "profile-type": "single" } |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": {
"policyid": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
]
}
operation: Delete Firewall Policy
Input parameters
| Parameter |
Description |
| Type |
Choose the level type at which you want to delete the firewall policy. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
If you choose 'Global', then you can specify the following parameters:
- Policy Type: Select the type of firewall policy you want to delete from Fortinet FortiManager.
|
| Policy Package Name |
Specify a valid policy package name for the firewall policy you want to delete from Fortinet FortiManager. |
| Policy ID |
Specify the ID of the firewall policy that you want to delete from Fortinet FortiManager. You can get the policy ID from "List Global Firewall Policies" or "List ADOM Firewall Policies" actions. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Move Firewall Policy
Input parameters
| Parameter |
Description |
| Level |
Choose the level type at which you want to move the firewall policy. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
If you choose 'Global', then you can specify the following parameters:
- Policy Type: Select the type of firewall policy you want to move in Fortinet FortiManager.
|
| Policy Package Name |
Specify a valid policy package name for the firewall policy you want to move in Fortinet FortiManager. |
| Policy ID |
Specify the ID of the firewall policy that you want to move in Fortinet FortiManager. You can get the policy ID from "List Global Firewall Policies" or "List ADOM Firewall Policies" actions. |
| Target |
Specify the Key to the target entry, i.e., the ID of the target policy. |
| Option |
Select whether you want to move the firewall policy Before or After the target policy in Fortinet FortiManager. |
Output
The output contains a non-dictionary value.
operation: Get Dynamic Interface List
Input parameters
| Parameter |
Description |
| Level |
Choose the level type from which you want to retrieve the dynamic interface details. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Interface Name: Valid dynamic interface name based on which you want to retrieve dynamic interface details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return all dynamic interfaces matching all values.
If you choose 'Global', then you can specify the following parameters:
- Interface Name: Valid dynamic interface name based on which you want to retrieve dynamic interface details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return all dynamic interfaces matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, ["color", "default-mapping", "defmap-intf", "defmap-intrazone-deny", "defmap-zonemember", "description", "egress-shaping-profile", "name", "single-intf", "wildcard", "wildcard-intf"]
Note: If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying attributes. |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the dynamic interfaces by the specified field and order the results. You can choose to either sort the results by fields, or can order the results, or both.
If you choose 'Field', then you must specify the following parameters:
- Field: Field: Specify the name of the field on which you want to sort the result. For example,
color, default-mapping, defmap-intf, defmap-intrazone-deny, defmap-zonemember, description, egress-shaping-profile, name, single-intf, wildcard, wildcard-intf, etc.
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [
{
"name": "",
"color": "",
"wildcard": "",
"single-intf": "",
"default-mapping": "",
"dynamic_mapping": "",
"platform_mapping": [
{
"name": "",
"intf-zone": "",
"intrazone-deny": ""
}
],
"defmap-zonemember": [],
"defmap-intrazone-deny": ""
}
],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Install Policy
Input parameters
| Parameter |
Description |
| ADOM Name |
Specify the ADOM name of the policy that you want to install in Fortinet FortiManager. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter. |
| Policy Package Name |
Select the name of the policy package that you want to install in Fortinet FortiManager. This parameter will make an API call named "list_adom_policy_package" to dynamically populate its dropdown selections. |
| ADOM Revision Comment |
Specify the ADOM revision comment of the policy that you want to install in Fortinet FortiManager |
| ADOM Revision Name |
Specify the ADOM revision name of the policy that you want to install in Fortinet FortiManager |
| Device Configuration Revision |
Comments that you want to for the device configuration revision that will be generated during the installation. |
| Device Name |
Specify the device name or device group name on which you want to install the policy package. |
| VDOM |
Specify the VDOM on which you want to install the policy package. |
Output
The output contains a non-dictionary value.
operation: Get Installation Policy Package Status
Input parameters
| Parameter |
Description |
| Task ID |
Specify the ID of the task whose policy package installation status you want to retrieve from Fortinet FortiManager. You get the task ID using the "Install Policy" action. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": {
"adom": "",
"end_tm": "",
"flags": "",
"id": "",
"line": [
{
"detail": "",
"end_tm": "",
"err": "",
"history": [
{
"detail": "",
"name": "",
"percent": "",
"vdom": ""
}
],
"ip": "",
"name": "",
"oid": "",
"percent": "",
"start_tm": "",
"state": "",
"vdom": ""
}
],
"num_done": "",
"num_err": "",
"num_lines": "",
"num_warn": "",
"percent": "",
"pid": "",
"src": "",
"start_tm": "",
"state": "",
"title": "",
"tot_percent": "",
"user": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
]
}
operation: Create LDAP Server
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to create the LDAP server. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
|
| LDAP Server Name |
Specify the entry name of the LDAP server used to create the LDAP server that you want to create on Fortinet FortiManager. |
| Username |
Specify the Username (full DN) used for initial binding at the time of the creation of the LDAP server on Fortinet FortiManager. |
| Password |
Specify the Password used for initial binding at the time of the creation of the LDAP server on Fortinet FortiManager. |
| Distinguished Name |
Specify the Distinguished Name used to look up entries on the LDAP server at the time of the creation of the LDAP server on Fortinet FortiManager. |
| Server |
Specify LDAP server CN domain name or IP to be used at the time of the creation of the LDAP server on Fortinet FortiManager. |
| Account Key Processing |
Select the type of Account Key processing operation, either Same (keep) or Strip (strip domain string of UPN in the token) to be used at the time of the creation of the LDAP server on Fortinet FortiManager. |
| AntiPhishing |
Select Enable to enable AntiPhishing credential backend when the LDAP server is being created on Fortinet FortiManager. |
| Group Member Check |
Select the type of group member checking methods to be used at the time of the creation of the LDAP server on Fortinet FortiManager. You can choose between User Attribute, Group Object, or Posix Group Object. |
| Interface Select Method |
Select the type of outgoing interface selection method used to reach the server at the time of the creation of the LDAP server on Fortinet FortiManager. You can choose between Auto, SD-WAN, or Specify. |
| Obtain User Info |
Select Enable to enable obtaining of user information when the LDAP server is being created on Fortinet FortiManager. |
| Source IP |
(Optional) Specify the IP address of FortiGate to be used for communication with the LDAP server when the LDAP server is being created on Fortinet FortiManager. |
| Source Port |
(Optional) Specify the source port to be used for communication with the LDAP server when the LDAP server is being created on Fortinet FortiManager. |
| Additional LDAP Server Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the LDAP server. You can enter the arguments in the following format: {"field1":value1, "field2":value2}. For example, {"account-key-filter": "string", "group-filter": "string", "ssl-min-proto-version": "default" } |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
]
}
operation: Get LDAP Server List
Input parameters
| Parameter |
Description |
| Level |
Choose the level type from which you want to retrieve the details for the LDAP servers. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- LDAP Server Name: Valid LDAP server name based on which you want to retrieve LDAP servers details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return all LDAP servers matching all values.
If you choose 'Global', then you can specify the following parameters:
- LDAP Server Name: Valid LDAP server name based on which you want to retrieve LDAP server details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return all LDAP servers matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, [ "account-key-filter", "account-key-processing", "antiphish", "ca-cert", "cnid", "dn", "group-filter", "group-member-check", "group-object-filter", "group-search-base", "interface", "interface-select-method", "member-attr", "name", "obtain-user-info", "password", "password-attr", "password-expiry-warning", "password-renewal", "port", "search-type", "secondary-server", "secure", "server", "server-identity-check", "source-ip", "source-port", "ssl-min-proto-version", "tertiary-server", "two-factor", "two-factor-authentication", "two-factor-notification", "type", "user-info-exchange-server", "username" ]
Note: If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying attributes. |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the LDAP servers by the specified field and order the results. You can choose to either sort the results by fields, or can order the results, or both.
If you choose 'Field', then you must specify the following parameters:
- Field: Specify the name of the field on which you want to sort the result. For example,
account-key-filter, account-key-processing, antiphish, ca-cert, cnid, dn, group-filter, group-member-check, group-object-filter, group-search-base, interface, interface-select-method, member-attr, name, obtain-user-info, password, password-attr, password-expiry-warning, password-renewal, port, search-type, secondary-server, secure, server, server-identity-check, source-ip, source-port, ssl-min-proto-version, tertiary-server, two-factor, two-factor-authentication, two-factor-notification, type, user-info-exchange-server, username
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Update LDAP Server
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to update the LDAP server. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
|
| LDAP Server Name |
Specify the entry name of the LDAP server used to update the LDAP server that you want to update on Fortinet FortiManager. |
| Username |
(Optional) Specify the Username (full DN) used for initial binding at the time of the updation of the LDAP server on Fortinet FortiManager. |
| Password |
(Optional) Specify the Password used for initial binding at the time of the updation of the LDAP server on Fortinet FortiManager. |
| Distinguished Name |
(Optional) Specify the Distinguished Name used to look up entries on the LDAP server at the time of the updation of the LDAP server on Fortinet FortiManager. |
| Server |
(Optional) Specify LDAP server CN domain name or IP to be used at the time of the updation of the LDAP server on Fortinet FortiManager. |
| Account Key Processing |
Select the type of Account Key processing operation, either Same (keep) or Strip (strip domain string of UPN in the token) to be used at the time of the updation of the LDAP server on Fortinet FortiManager. |
| AntiPhishing |
Select Enable to enable AntiPhishing credential backend when the LDAP server is being updated on Fortinet FortiManager. |
| Group Member Check |
Select the type of group member checking methods to be used at the time of the updation of the LDAP server on Fortinet FortiManager. You can choose between User Attribute, Group Object, or Posix Group Object. |
| Interface Select Method |
Select the type of outgoing interface selection method used to reach the server at the time of the updation of the LDAP server on Fortinet FortiManager. You can choose between Auto, SD-WAN, or Specify. |
| Obtain User Info |
Select Enable to enable obtaining of user information when the LDAP server is being updated on Fortinet FortiManager. |
| Source IP |
(Optional) Specify the IP address of FortiGate to be used for communication with the LDAP server when the LDAP server is being updated on Fortinet FortiManager. |
| Source Port |
(Optional) Specify the source port to be used for communication with the LDAP server when the LDAP server is being updated on Fortinet FortiManager. |
| Additional LDAP Server Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the updation of the LDAP server. You can enter the arguments in the following format: {"field1":value1, "field2":value2}. For example, {"account-key-filter": "string", "group-filter": "string", "ssl-min-proto-version": "default" } |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
]
}
operation: Delete LDAP Server
Input parameters
| Parameter |
Description |
| Type |
Choose the level type at which you want to delete the LDAP server. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
|
| LDAP Server Name |
Specify the entry name of the LDAP server that you want to delete from Fortinet FortiManager. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Create User Group
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to create the user group. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
|
| Group Name |
Specify the name of the user group name you want to create in Fortinet FortiManager. |
| Member |
Specify a CSV list or list of names of users, peers, LDAP servers, or RADIUS servers that you want to add to the user group, which you want to create in Fortinet FortiManager. |
| Additional User Group Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the creation of the user group. You can enter the arguments in the following format: {"field1":value1, "field2":value2}. For example, {"account-key-filter": "string", "group-filter": "string", "ssl-min-proto-version": "default" } |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
]
}
operation: Get User Groups List
Input parameters
| Parameter |
Description |
| Level |
Choose the level type from which you want to retrieve the details for the user groups. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- User Group Name: Valid user group name based on which you want to retrieve user group details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return all user groups matching all values.
If you choose 'Global', then you can specify the following parameters:
- User Group Name: Valid user group name based on which you want to retrieve user group details from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return all user groups matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, ["auth-concurrent-override","auth-concurrent-value","authtimeout","company","email","expire","expire-type","group-type","http-digest-realm","id","max-accounts","member","mobile-phone","multiple-guest-add","name","password","sms-custom-server","sms-server","sponsor","sso-attribute-value","user-id","user-name"]
Note: If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying attributes. |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the user groups by the specified field and order the results. You can choose to either sort the results by fields, or can order the results, or both.
If you choose 'Field', then you must specify the following parameters:
- Field: Specify the name of the field on which you want to sort the result. For example,
auth-concurrent-override, auth-concurrent-value, authtimeout, company, email, expire, expire-type, group-type, http-digest-realm, id, max-accounts, member, mobile-phone, multiple-guest-add, name, password, sms-custom-server, sms-server, sponsor, sso-attribute-value, user-id, user-name
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Update User Group
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to update the user group. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
|
| Group Name |
Specify the name of the user group name you want to update in Fortinet FortiManager. |
| Method |
Select the action that you want to perform on members of the user group. You can choose between Add or Remove.
- If you choose 'Add', then in the Add Member field, specify a CSV list or list of names of users, peers, LDAP servers, or RADIUS servers that you want to add to the user group, which you want to update in Fortinet FortiManager.
- If you choose 'Remove', then in the Remove Member field, specify a CSV list or list of names of users, peers, LDAP servers, or RADIUS servers that you want to remove from the user group, which you want to update in Fortinet FortiManager.
|
| Additional User Group Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the updation of the user group. You can enter the arguments in the following format: {"field1":value1, "field2":value2}. For example, {"sponsor": "optional", "sms-server": "string", "ssl-min-proto-version": "default" } |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"data": {
"name": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
]
}
operation: Delete User Group
Input parameters
| Parameter |
Description |
| Type |
Choose the level type at which you want to delete the user group. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
|
| Group Name |
Name of the group from which you want to delete the user group on Fortinet FortiManager. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Get SSL VPN Settings
Input parameters
| Parameter |
Description |
| Device |
Specify the device name whose SSL VPN settings you want to retrieve from Fortinet FortiManager. |
| VDOM |
Specify the VDOM name using which you want to retrieve the SSL VPN settings from Fortinet FortiManager. For example, root |
| Option |
Select the Fetch option to be set for the request. If you do not select any option then by default all the attributes of the object are returned. You can choose from the following:
- Object - Returns a list of object members along with other attributes.
- Check Sum - Returns the check-sum value instead of attributes.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": {
"algorithm": "",
"auth-session-check-source-ip": "",
"auth-timeout": "",
"authentication-rule": [
{
"auth": "",
"cipher": "",
"client-cert": "",
"groups": [],
"id": "",
"obj seq": "",
"portal": [],
"realm": [],
"source-address": [],
"source-address-negate": "",
"source-address6": [],
"source-address6-negate": "",
"source-interface": [],
"users": []
}
],
"auto-tunnel-static-route": "",
"banned-cipher": "",
"check-referer": "",
"ciphersuite": "",
"client-sigalgs": "",
"default-portal": [],
"deflate-compression-level": "",
"deflate-min-data-size": "",
"dns-server1": "",
"dns-server2": "",
"dns-suffix": "",
"dtls-hello-timeout": "",
"dtls-max-proto-ver": "",
"dtls-min-proto-ver": "",
"dtls-tunnel": "",
"dual-stack-mode": "",
"encode-2f-sequence": "",
"encrypt-and-store-password": "",
"force-two-factor-auth": "",
"header-x-forwarded-for": "",
"hsts-include-subdomains": "",
"http-compression": "",
"http-only-cookie": "",
"http-request-body-timeout": "",
"http-request-header-timeout": "",
"https-redirect": "",
"idle-timeout": "",
"ipv6-dns-server1": "",
"ipv6-dns-server2": "",
"ipv6-wins-server1": "",
"ipv6-wins-server2": "",
"login-attempt-limit": "",
"login-block-time": "",
"login-timeout": "",
"port": "",
"port-precedence": "",
"reqclientcert": "",
"saml-redirect-port": "",
"servercert": [],
"source-address": [],
"source-address-negate": "",
"source-address6": [],
"source-address6-negate": "",
"source-interface": [],
"ssl-client-renegotiation": "",
"ssl-insert-empty-fragment": "",
"ssl-max-proto-ver": "",
"ssl-min-proto-ver": "",
"status": "",
"transform-backward-slashes": "",
"tunnel-addr-assigned-method": "",
"tunnel-connect-without-reauth": "",
"tunnel-ip-pools": [],
"tunnel-ipv6-pools": [],
"tunnel-user-session-timeout": "",
"unsafe-legacy-renegotiation": "",
"url-obscuration": "",
"wins-server1": "",
"wins-server2": "",
"x-content-type-options": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Update SSL VPN Settings
Input parameters
| Parameter |
Description |
| Device |
Specify the device name whose SSL VPN settings you want to update in Fortinet FortiManager. |
| VDOM |
Specify the VDOM name using which you want to update the SSL VPN settings in Fortinet FortiManager. For example, root |
| Default SSL VPN Portal |
Specify the default SSL VPN portal to be used to update the SSL VPN settings in Fortinet FortiManager. |
| Source Interface |
Specify the SSL VPN source interface of incoming traffic to be used to update the SSL VPN settings in Fortinet FortiManager. |
| Port |
Specify the SSL VPN access port (1 - 65535) to be used to update the SSL VPN settings in Fortinet FortiManager. |
| Server Certificate |
Specify the name of the server certificate to be used for SSL VPNs when the SSL VPN settings are updated in Fortinet FortiManager. For example, self-sign |
| Authentication/Portal Mapping |
By default, all users see the same Authentication/Portal portal and this parameter is unchecked (cleared). The Authentication/Portal Mapping allows you to assign different portals to different users and groups in Fortinet FortiManager.
Note: To update the default Authentication/Portal Mapping, you must select this parameter and then specify at least one of the following Authentication/Portal Mapping parameters:
- Authentication/Portal ID: Specify the Authentication/Portal mapping ID to be updated in the SSL VPN settings in Fortinet FortiManager.
- Authentication/Portal User Names: Specify the CSV list or list of user names to be updated in the SSL VPN settings in Fortinet FortiManager.
- Authentication/Portal User Groups: Specify the CSV list or list of user groups to be updated in the SSL VPN settings in Fortinet FortiManager.
- Authentication/Portal Realm: Specify the SSL VPN Realm to be used to update the SSL VPN settings in Fortinet FortiManager
- Authentication/Portal Portal: Specify the SSL VPN portal to be used to update the SSL VPN settings in Fortinet FortiManager. For example,
web-access, full-access, tunnel-access, etc.
- Authentication/Portal Authentication: Select the SSL VPN authentication method restriction to be used to update the SSL VPN settings in Fortinet FortiManager. You can choose between Any, Local, LDAP, RADIUS, or TACACS+.
- Authentication/Portal Cipher: Specify the SSL VPN cipher strength to be used to update the SSL VPN settings in Fortinet FortiManager. You can choose between Any, High, or Medium.
- Authentication/Portal Client Certificate: Select Enable to enable SSL VPN client certificate restriction when the SSL VPN settings are updated in Fortinet FortiManager.
- Authentication/Portal Source Interface: Specify the CSV or the list of SSL VPN source interfaces of incoming traffic to be used to update the SSL VPN settings in Fortinet FortiManager.
- Authentication/Portal Source Address: Specify the CSV or the list of source addresses of incoming traffic to be updated in the SSL VPN settings in Fortinet FortiManager.
- Authentication/Portal Source Address Negate: Select Enable to enable negated source address match when the SSL VPN settings are updated in Fortinet FortiManager.
- Authentication/Portal Source Address6: Specify the CSV or the list of IPv6 source addresses of incoming traffic to be updated in the SSL VPN settings in Fortinet FortiManager.
- Authentication/Portal Source Address6 Negate: Select Enable to enable negated source address match when the SSL VPN settings are updated in Fortinet FortiManager.
- Authentication/Portal User Peer: Specify the name of the user peer to be used to update the SSL VPN settings in Fortinet FortiManager.
|
| Source Address |
Specify the CSV or the list of source addresses of incoming traffic to be updated in the SSL VPN settings in Fortinet FortiManager. |
| Source Address6 |
Specify the CSV or the list of IPv6 source addresses of incoming traffic to be updated in the SSL VPN settings in Fortinet FortiManager. |
| Source Address Negate |
Select Enable to enable negated source address match when the SSL VPN settings are updated in Fortinet FortiManager. |
| User Peer |
Specify the name of the user peer to be used to update the SSL VPN settings in Fortinet FortiManager. |
| Additional SSL VPN Settings Arguments |
(Optional) Specify additional arguments, in JSON format, to be added during the updating of the SSL VPN settings. You can enter the arguments in the following format: {"field1":value1, "field2":value2}. For example, {"tunnel-ip-pools": "SSLVPN_TUNNEL_ADDR1", "sms-server": "string", "ssl-min-proto-version": "default" } |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Get Web Filter List
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to retrieve the web filter details. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Web Filter Profile Name: Valid web filter profile name based on which you want to retrieve details web filters from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return web filters matching all values.
If you choose 'Global', then you can specify the following parameters:
- Web Filter Profile Name: Valid web filter profile name based on which you want to retrieve details web filters from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return web filters matching all values.
|
| Attributes in Result |
(Optional) You can choose to limit the output by returning only those attributes that are specified in the string array. For example, ["comment", "extended-log", "feature-set", "https-replacemsg", "log-all-url", "name", "options", "ovrd-perm", "post-action", "replacemsg-group", "web-antiphishing-log", "web-content-log", "web-extended-all-action-log", "web-filter-activex-log", "web-filter-applet-log", "web-filter-command-block-log", "web-filter-cookie-log", "web-filter-cookie-removal-log", "web-filter-js-log", "web-filter-jscript-log", "web-filter-referer-log", "web-filter-unknown-log", "web-filter-vbs-log", "web-ftgd-err-log", "web-ftgd-quota-usage", "web-invalid-domain-log", "web-url-log", "wisp", "wisp-algorithm", "wisp-servers"]. If attributes are not specified, then all attributes will be returned. |
| Filter By |
(Optional) You can filter the result according to a set of criteria by specifying attributes in the format [["", "==", ""]] |
| Limit |
(Optional) The maximum number of results that this operation should return. |
| Offset |
(Optional) The offset value retrieves a subset of records that starts from the offset value. The offset works with the 'Limit' parameter, which determines how many records to retrieve starting from the offset. Values supported are: Default "0" and Minimum "0". |
| Sort By |
Sort the web filters by a field and order the results. You can choose to either sort the results by fields, or can order the results, or both.If you choose "Field", then in the Field field specify the name of the field on which you want to sort the result. For example, default-mapping, defmap-intf, defmap-intrazone-deny, etc.
If you choose 'Field'
- Field: Specify the name of the field on which you want to sort the result. Fields based on which you can sort are
account-key-filter, account-key-processing, antiphish, ca-cert, cnid, dn, group-filter, group-member-check, group-object-filter, group-search-base, interface, interface-select-method, member-attr, name, obtain-user-info, password, password-attr, password-expiry-warning, password-renewal, port, search-type, secondary-server, secure, server, server-identity-check, source-ip, source-port, ssl-min-proto-version, tertiary-server, two-factor, two-factor-authentication, two-factor-notification, type, user-info-exchange-server, username.
- Order: Choose the order in which you want to sort the result. You can choose between Ascending or Descending. By default, this is set to Ascending.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [
{
"antiphish": {
"authentication": "",
"check-basic-auth": "",
"check-uri": "",
"check-username-only": "",
"custom-patterns": "",
"default-action": "",
"domain-controller": [],
"inspection-entries": "",
"ldap": [],
"max-body-len": "",
"status": ""
},
"ftgd-wf": {
"exempt-quota": [],
"filters": [
{
"action": "",
"category": [],
"id": "",
"log": "",
"warn-duration": "",
"warning-prompt": ""
}
],
"max-quota-timeout": "",
"options": "",
"ovrd": [],
"quota": "",
"rate-crl-urls": "",
"rate-css-urls": "",
"rate-javascript-urls": ""
},
"override": {
"ovrd-cookie": "",
"ovrd-dur": "",
"ovrd-dur-mode": "",
"ovrd-scope": "",
"ovrd-user-group": [],
"profile": [],
"profile-attribute": "",
"profile-type": ""
},
"url-extraction": "",
"web": {
"allowlist": "",
"blocklist": "",
"bword-table": [],
"bword-threshold": "",
"content-header-list": [],
"urlfilter-table": [],
"vimeo-restrict": "",
"youtube-restrict": ""
},
"name": "",
"web-content-log": "",
"web-filter-cookie-log": "",
"web-url-log": "",
"web-invalid-domain-log": "",
"web-ftgd-err-log": "",
"options": "",
"ovrd-perm": "",
"post-action": "",
"replacemsg-group": [],
"https-replacemsg": "",
"log-all-url": "",
"web-filter-command-block-log": "",
"wisp": "",
"wisp-algorithm": "",
"extended-log": "",
"web-extended-all-action-log": "",
"feature-set": ""
}
],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Get Blocked URLs
Input parameters
| Parameter |
Description |
| Level |
Choose the level type from which you want to retrieve the details of blocked URLs associated with the specified web filter profile. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Web Filter Profile Name: Valid web filter profile name that you have specified in Fortinet FortiManager for blocking or unblocking URLs. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
If you choose 'Global', then you can specify the following parameters:
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [
{
"action": "",
"antiphish-action": "",
"dns-address-family": "",
"id": "",
"obj seq": "",
"status": "",
"type": "",
"url": "",
"web-proxy-profile": []
}
],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Block URL
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to block the URLs specific to the web filter profile. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Web Filter Profile Name: Valid web filter profile name that you have specified in Fortinet FortiManager for blocking or unblocking URLs. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
- URL: List of URLs that you want to block on Fortinet FortiManager. Specify the URLs in the list format, if you want to block more than one URL. For example, for a list of URLs, enter:
["URL1", "URL2"] in this field. For a single URL enter: "example.com"
If you choose 'Global', then you can specify the following parameters:
- Web Filter Profile Name: Valid web filter profile name that you have specified in Fortinet FortiManager for blocking or unblocking URLs. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
- URL: List of URLs that you want to block on Fortinet FortiManager. Specify the URLs in the list format, if you want to block more than one URL. For example, for a list of URLs, enter:
["URL1", "URL2"] in this field. For a single URL enter: "example.com"
|
Output
The output contains the following populated JSON schema:
{
"already_blocked": [],
"newly_blocked": []
}
operation: Unblock URL
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type at which you want to unblock the URLs specific to the web filter profile. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Web Filter Profile Name: Valid web filter profile name that you have specified in Fortinet FortiManager for blocking or unblocking URLs. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
- URL: List of URLs that you want to unblock on Fortinet FortiManager. Specify the URLs in the list format, if you want to unblock more than one URL. For example, for a list of URLs, enter:
["URL1", "URL2"] in this field. For a single URL enter: "example.com"
If you choose 'Global', then you can specify the following parameters:
- Web Filter Profile Name: Valid web filter profile name that you have specified in Fortinet FortiManager for blocking or unblocking URLs. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
- URL: List of URLs that you want to unblock on Fortinet FortiManager. Specify the URLs in the list format, if you want to unblock more than one URL. For example, for a list of URLs, enter:
["URL1", "URL2"] in this field. For a single URL enter: "example.com"
|
Output
The output contains the following populated JSON schema:
{
"not_exist": [],
"newly_unblocked": []
}
operation: Get Applications Detail
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [
{
"behavior": "",
"casi": "",
"cat-id": "",
"category": "",
"database": "",
"id": "",
"language": "",
"name": "",
"parameter": "",
"popularity": "",
"protocol": "",
"require_ssl_di": "",
"risk": "",
"shaping": "",
"technology": "",
"vendor": "",
"weight": ""
}
],
"status": {
"code": "",
"message": ""
},
"version": ""
}
]
}
operation: Get Applications Control List
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to retrieve the list of applications control profiles. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Appplication Control Profile Name: Valid application control profile name based on which you want to retrieve details of the application control profile from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return web filters matching all values.
If you choose 'Global', then you can specify the following parameters:
- Appplication Control Profile Name: Valid application control profile name based on which you want to retrieve details of the application control profile from Fortinet FortiManager.
Note: If this parameter is left blank or null, then this operation will return web filters matching all values.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": [
{
"url": "",
"data": [
{
"default-network-services": "",
"entries": [
{
"action": "",
"application": [],
"behavior": [],
"category": [],
"exclusion": [],
"id": "",
"log": "",
"log-packet": "",
"obj seq": "",
"parameters": "",
"per-ip-shaper": [],
"popularity": "",
"protocols": [],
"quarantine": "",
"quarantine-expiry": "",
"quarantine-log": "",
"rate-count": "",
"rate-duration": "",
"rate-mode": "",
"rate-track": "",
"risk": [],
"session-ttl": "",
"shaper": [],
"shaper-reverse": [],
"technology": [],
"vendor": []
}
],
"name": "",
"other-application-action": "",
"other-application-log": "",
"unknown-application-action": "",
"unknown-application-log": "",
"replacemsg-group": [],
"options": "",
"app-replacemsg": "",
"deep-app-inspection": "",
"extended-log": "",
"enforce-default-app-port": "",
"control-default-network-services": "",
"force-inclusion-ssl-di-sigs": "",
"p2p-block-list": ""
}
],
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Get Blocked Applications
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to retrieve details of blocked applications associated with the specified application control profile. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Application Control Profile Name: Valid application control profile name that you have specified in Fortinet FortiManager for blocking or unblocking applications. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
If you choose 'Global', then you can specify the following parameters:
|
Output
The output contains the following populated JSON schema:
{
"behavior": "",
"casi": "",
"cat-id": "",
"category": "",
"database": "",
"id": "",
"language": "",
"name": "",
"parameter": "",
"popularity": "",
"protocol": "",
"require_ssl_di": "",
"risk": "",
"shaping": "",
"technology": "",
"vendor": "",
"weight": ""
}
operation: Block Application
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to block the applications associated with the specified application control profile. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Application Control Profile Name: Valid application control profile name that you have specified in Fortinet FortiManager for blocking or unblocking applications. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
- Application Names: List of application names that you want to block on Fortinet FortiManager. Specify the application names in the list format, if you want to block more than one application. For example, for a list of applications, enter:
["Application_Name1", "Application_Name2"] in this field. For a single URL enter: Application_Name
If you choose 'Global', then you can specify the following parameters:
- Application Control Profile Name: Valid application control profile name that you have specified in Fortinet FortiManager for blocking or unblocking applications. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
- Application Names: List of application names that you want to block on Fortinet FortiManager. Specify the application names in the list format, if you want to block more than one application. For example, for a list of applications, enter:
["Application_Name1", "Application_Name2"] in this field. For a single URL enter: Application_Name
|
Output
The output contains the following populated JSON schema:
{
"name": "",
"message": "",
"status": ""
}
operation: Unblock Application
Input parameters
| Parameter |
Description |
| Level Type |
Choose the level type from which you want to unblock the applications associated with the specified application control profile. You can choose between ADOM or Global Type.
If you choose 'ADOM', then you can specify the following parameters:
- ADOM: Administrative domain name (ADOM) of the Fortinet FortiManager server to which you will connect and perform the automated operations. The ADOM that you specify here will overwrite the ADOM that you have specified as a configuration parameter.
- Application Control Profile Name: Valid application control profile name that you have specified in Fortinet FortiManager for blocking or unblocking applications. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
- Application Names: List of application names that you want to unblock on Fortinet FortiManager. Specify the application names in the list format, if you want to unblock more than one application. For example, for a list of applications, enter:
["Application_Name1", "Application_Name2"] in this field. For a single URL enter: Application_Name
If you choose 'Global', then you can specify the following parameters:
- Application Control Profile Name: Valid application control profile name that you have specified in Fortinet FortiManager for blocking or unblocking applications. Based on our example, enter
default in this field. See the Blocking or Unblocking IP addresses, URLs, or applications in Fortinet FortiManager section.
- Application Names: List of application names that you want to unblock on Fortinet FortiManager. Specify the application names in the list format, if you want to unblock more than one application. For example, for a list of applications, enter:
["Application_Name1", "Application_Name2"] in this field. For a single URL enter: Application_Name
|
Output
The output contains the following populated JSON schema:
{
"name": "",
"message": "",
"status": ""
}
Included playbooks
The Sample - Fortinet Fortimanager - 3.0.0 playbook collection comes bundled with the Fortinet FortiManager connector. These playbooks contain steps using which you can perform all supported actions. You can see bundled playbooks in the Automation > Playbooks section in FortiSOAR™ after importing the Fortinet FortiManager connector.
- ADOM Level Block IP Address
- ADOM Level Get Blocked IP Addresses
- ADOM Level Unblock IP Address
- Assign Global Policy Package
- Block Application
- Block URL
- Create Address
- Create Address Group
- Create Custom Service
- Create Firewall Policy
- Create Incident
- Create LDAP Server
- Create Policy Package
- Create Service Group
- Create User Group
- Delete Address
- Delete Address Group
- Delete Custom Service
- Delete Firewall Policy
- Delete LDAP Server
- Delete Policy Package
- Delete Service Group
- Delete User Group
- > FortiManager > Fetch
- >> FortiManager > Handle Macro
- FortiManager > Ingest
- Get Address Groups List
- Get Addresses List
- Get Applications Control List
- Get Applications Detail
- Get Blocked Applications
- Get Blocked URLs
- Get Custom Services List
- Get Device Groups List
- Get Device List
- Get Dynamic Interface List
- Get Event Details
- Get Events
- Get Events Related to Incident
- Get Installation Policy Package Status
- Get LDAP Server List
- Get SSL VPN Settings
- Get Service Categories List
- Get Service Groups List
- Get User Groups List
- Get Web Filter List
- Global Level Block IP Address
- Global Level Get Blocked IP Addresses
- Global Level Unblock IP Address
- Install Policy
- List ADOM Firewall Policies
- List ADOM Policy Package
- List Global Firewall Policies
- List Global Policy Package
- List Incident
- Move Firewall Policy
- Re-install Policy
- Unblock Application
- Unblock URL
- Update Address
- Update Address Group
- Update Custom Service
- Update Firewall Policy
- Update Incident
- Update LDAP Server
- Update Policy Package
- Update SSL VPN Settings
- Update Service Group
- Update User Group
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection since the sample playbook collection gets deleted during the connector upgrade and delete.
Data Ingestion Support
Use the Data Ingestion Wizard to easily ingest data into FortiSOAR™ by pulling incidents from Fortinet FortiManager. Currently, "incidents" in Fortinet FortiManager are mapped to "alerts" in FortiSOAR™. For more information on the Data Ingestion Wizard, see the "Connectors Guide" in the FortiSOAR™ product documentation.
Configure Data Ingestion
You can configure data ingestion using the “Data Ingestion Wizard” to seamlessly map the incoming Fortinet FortiManager "Incidents" to FortiSOAR™ "Alerts".
The Data Ingestion Wizard enables you to configure scheduled pulling of data from Fortinet FortiManager into FortiSOAR™. It also lets you pull some sample data from Fortinet FortiManager using which you can define the mapping of data between Fortinet FortiManager and FortiSOAR™. The mapping of common fields is generally already done by the Data Ingestion Wizard; users are mostly required to only map any custom fields that are added to the Fortinet FortiManager incident.
- To begin configuring data ingestion, click Configure Data Ingestion on the Fortinet FortiManager connector’s "Configurations" page.
Click Let’s Start by fetching some data, to open the “Fetch Sample Data” screen.
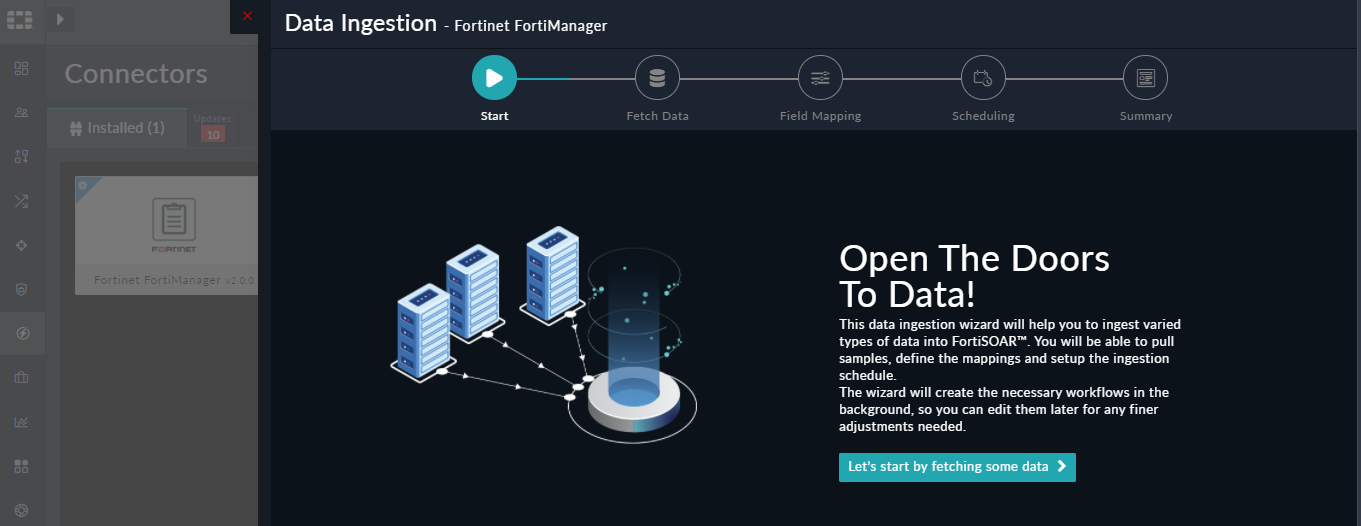
Sample data is required to create a field mapping between Fortinet FortiManager data and FortiSOAR™. The sample data is pulled from connector actions or ingestion playbooks.
- On the Fetch Data screen, provide the configurations required to fetch Fortinet FortiManager data.
Users can choose to pull data from Fortinet FortiManager by specifying the last X minutes in which the incidents have been created or updated in Fortinet FortiManager. You can also specify a query to filter data retrieved from Fortinet FortiManager and can also specify additional parameters such as the category, severity, and status of the incidents to be fetched from Fortinet FortiManager. The fetched data is used to create a mapping between the Fortinet FortiManager data and FortiSOAR™ alerts.
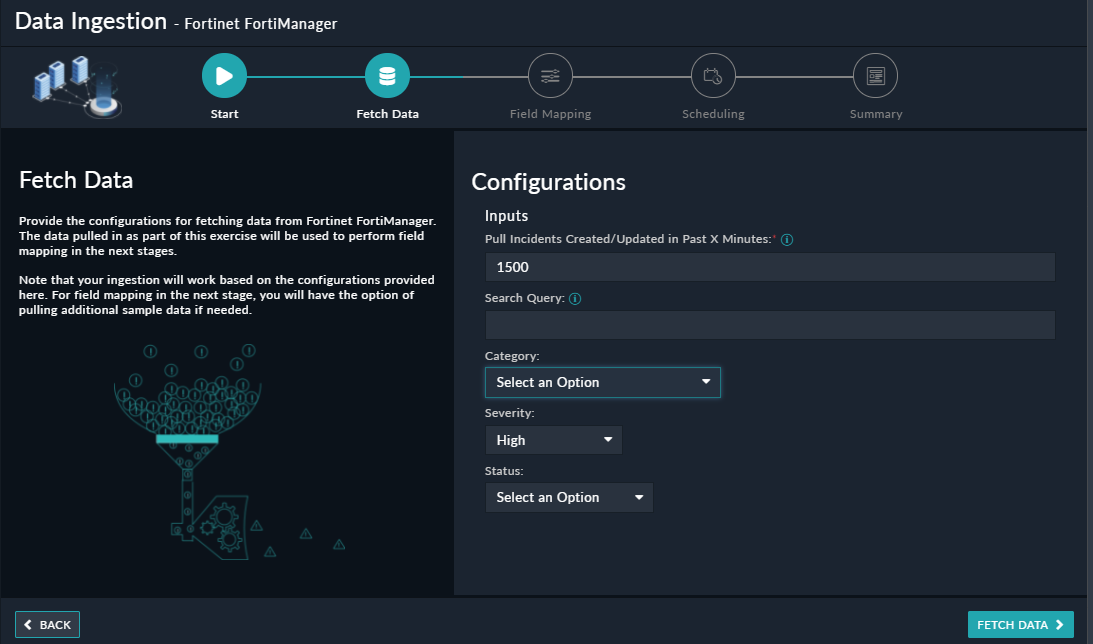
Once you have completed specifying the configurations, click Fetch Data.
-
On the Field Mapping screen, map the fields of a Fortinet FortiManager incident to the fields of an alert present in FortiSOAR™.
To map a field, click the key in the sample data to add the “jinja” value of the field. For example, to map the status parameter of a Fortinet FortiManager incident to the state parameter of a FortiSOAR™ alert, click the State field and then click the status field to populate its keys:

For more information on field mapping, see the Data Ingestion chapter in the "Connectors Guide" in the FortiSOAR™ product documentation. Once you have completed mapping the fields, click Save Mapping & Continue.
-
Use the Scheduling screen to configure schedule-based ingestion, i.e., specify the polling frequency to Fortinet FortiManager, so that the content gets pulled from the Fortinet FortiManager integration into FortiSOAR™.
On the Scheduling screen, from the Do you want to schedule the ingestion? drop-down list, select Yes.
In the “Configure Schedule Settings” section, specify the Cron expression for the schedule. For example, if you want to pull data from Fortinet FortiManager every 5 minutes, click Every X Minute, and in the minute box enter */5. This would mean that based on the configuration you have set up, data, i.e., incidents will be pulled from Fortinet FortiManager every 5 minutes.

Once you have completed scheduling, click Save Settings & Continue.
-
The Summary screen displays a summary of the mapping done, and it also contains links to the Ingestion playbooks. Click Done to complete the data ingestion and exit the Data Ingestion Wizard.









