About the connector
Fortinet FortiSandbox utilizes advanced detection, dynamic antivirus scanning, and threat scanning technology to detect viruses and APTs. Fortinet FortiSandbox executes suspicious files in the VM host module to determine if the file is High, Medium, or Low Risk, based on the behavior observed in the VM sandbox module.
This document provides information about the Fortinet FortiSandbox connector, which facilitates automated interaction with your Fortinet FortiSandbox server using FortiSOAR™ playbooks. Add the Fortinet FortiSandbox connector, as a step in FortiSOAR™ playbooks and perform automated operations such as submitting files to Fortinet FortiSandbox from the FortiSOAR™ Attachments module and retrieving the status of the system and scan stats from Fortinet FortiSandbox.
Version information
Connector Version: 2.1.0
FortiSOAR™ Version Tested on: 7.5.0-4015
Fortinet FortiSandbox Version Tested on: v4.2.3-build4244 (GA)
Contributor: Mahdi Naili
Publisher: Fortinet
Certified: Yes
Release Notes for version 2.1.0
Following enhancements have been made to the Fortinet FortiSandbox connector in version 2.1.0:
Installing the connector
Use the Content Hub to install the connector. For the detailed procedure to install a connector, click here.
You can also use the yum command as a root user to install the connector:
yum install cyops-connector-fortinet-fortisandbox
Prerequisites to configuring the connector
- You must have the URL of the Fortinet FortiSandbox server to which you will connect and perform automated operations and credentials to access that server.
- The FortiSOAR™ server should have outbound connectivity to port 443 on the Fortinet FortiSandbox server.
- To configure the connector, you must add the following roles to users in Fortinet Sandbox, including an account that can access the JSON API:
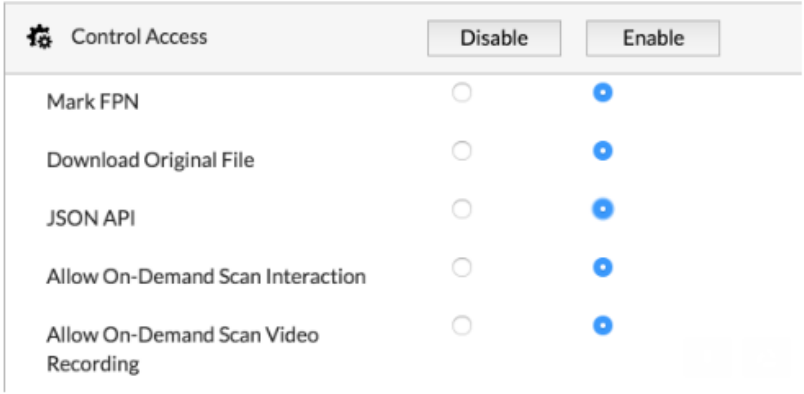
Minimum Permissions Required
Configuring the connector
For the procedure to configure a connector, click here.
Configuration parameters
In FortiSOAR™, on the Content Hub (or Connector Store) page, click the Manage tab, and then click the Fortinet FortiSandbox connector card. On the connector popup, click the Configurations tab to enter the required configuration details:
| Parameter |
Description |
| Server URL |
URL of the Fortinet FortiSandbox server to which you will connect and perform automated operations. |
| Instance Type |
Select the instance type from the following options:
- OnPremise: Select this option if Fortinet FortiSandbox is deployed on an on-premises server. Specify values in the following fields:
- Username: Username of the Fortinet FortiSandbox server to which you will connect and perform automated operations.
- Password: Password to access the Fortinet FortiSandbox server to which you will connect and perform the automated operations.
- Cloud: Select this option if the Fortinet FortiSandbox server is deployed on cloud. Specify values in the following fields:
- API Authentication Token: FortiSandbox Cloud Token for API authenticate. You can generate a token with the command: login-token -g on FortiSandbox Cloud.
|
| Version |
(Optional) Specify the FortiSandBox version to which you will connect and perform automated operations. |
| Verify SSL |
Specifies whether the SSL certificate for the server is to be verified or not.
By default, this option is set to True. |
Actions supported by the connector
The following automated operations can be included in playbooks, and you can also use the annotations to access operations:
| Function |
Description |
Annotation and Category |
| Submit File |
Submits a file to Fortinet FortiSandbox based on the attachment ID or indicator IRI you have specified. |
submit_file
Investigation |
| Submit URL |
Submits a URL(s) to Fortinet FortiSandbox. |
submit_url
Investigation |
| Get System Status |
Retrieves the status of the system from Fortinet FortiSandbox. |
get_system_status
Investigation |
| Get Scan Stats |
Retrieves the scan stats for the last 7 days from Fortinet FortiSandbox. |
get_scan_stats
Investigation |
| Get Submission Job List |
Retrieves all job IDs associated with the submission ID you have specified from Fortinet FortiSandbox. |
get_job_list
Investigation |
| Get Job Verdict Detail |
Retrieves job verdict detail for job ID you have specified from Fortinet FortiSandbox. |
get_job_detail
Investigation |
| Get File Rating |
Retrieves file rating for the file type and filehash you have specified from Fortinet FortiSandbox. |
get_file_rating
Investigation |
| Get URL Rating |
Get rating details for the URL you have specified from Fortinet FortiSandbox. |
get_url_rating
Investigation |
| Get File Verdict |
Retrieves the file verdict details for the file type and filehash you have specified from Fortinet FortiSandbox. |
get_file_verdict
Investigation |
| Get Job Behavior |
Retrieves job behavior details associated with the file type and filehash you have specified from Fortinet FortiSandbox. |
get_job_details
Investigation |
| Update White or Black List |
(Deprecated) Updates an existing whitelist or an existing blacklist in Fortinet FortiSandbox, based on the input parameter such as indicator type and value, and action you have specified.
NOTE: This action is now deprecated for FortiSandBox version 4.0 and later. Use the action Update Allow or Block List instead.
|
update_white_black_list
Miscellaneous |
| Update Allow or Block List |
Updates an existing allow list or an existing blocked list in Fortinet FortiSandbox, based on the input parameter such as indicator type and value, and action you have specified.
NOTE: This action replaces the deprecated action Update White or Black List in FortiSandBox version 4.0 and later.
|
update_allow_block_list
Miscellaneous |
| Toggle FPN State |
Marks specified sample based on the Job ID you have specified as false negative or false positive in Fortinet FortiSandbox. |
toggle_fpn_state
Miscellaneous |
| Get AV-Rescan Result |
Retrieves AV-Rescan results for the time duration you have specified from Fortinet FortiSandbox. |
get_scan_result
Investigation |
| Get All Installed VM |
Retrieves the names and the clone numbers of all installed VMs on Fortinet FortiSandbox. |
get_installed_vm
Investigation |
| Get PDF Report |
Retrieves a PDF report from Fortinet FortiSandbox based on the query type and value parameter you have specified and creates an attachment in the FortiSOAR™ Attachment module if the report is found. |
get_report
Investigation |
| List Filehash or URL From Malware Package or URL Package |
Retrieves a list of file hashes or URLs based on the type you have specified from the Malware Package or URL Package in Fortinet FortiSandbox. |
list_filehash_url
Investigation |
operation: Submit File
Input parameters
Note: To execute this action on a remote agent using the Indicator IRI, you must ensure that the Indicator module has appropriate permissions for the FortiSOAR Agent to access indicator files on the agent.
| Parameter |
Description |
| Indicator IRI/Attachment ID |
Select whether you want to submit an Indicator IRI or an Attachment ID to Fortinet FortiSandbox. Select from the following options:
- Indicator IRI: Specify the IRI of the indicator that you want to submit to Fortinet FortiSandbox, in the Indicator IRI field.
- Attachment ID: Specify the ID of the attachment that you want to submit to Fortinet FortiSandbox, in the Attachment ID field. Attachment IRIs are used to access the file directly from the FortiSOAR™ Attachments module.
NOTE: Following file types are supported:
- 32bit and 64bit executable files including all the Portable Executables (PE) files
- text-based file such as, HTML, VBA, VBS, JS, office documents, PDF, BAT, SH, PHP, XML
- PowerShell scripts
- archive formats like
.tar, .gz, .tar.gz, .tgz, .zip, .bz2, and .rar
|
| VM Name |
(Optional) Specify a VM name to scan the specified URL file.
NOTE: If you do not specify a VM Name, then the VM Name defaults to the one being used.
|
| Unzip File |
Select to unzip the file and submit extracted files to Fortinet FortiSandbox. Once selected, specify values in the following field:
Password: Specify the password to open the protected file.
|
Output
The output contains the following populated JSON schema:
Output schema when you choose Unzip File as false:
{
"ver": "",
"id": "",
"result": {
"url": "",
"status": {
"message": "",
"code": ""
},
"data": {
"msg": "",
"sid": "",
"error": ""
}
}
}
Output schema when you choose Unzip File as true:
{
"id": "",
"ver": "",
"results": [
{
"url": "",
"data": {
"msg": "",
"sid": "",
"error": ""
},
"status": {
"code": "",
"message": ""
}
}
]
}
operation: Submit URL
Input parameters
| Parameter |
Description |
| URL |
URL that you want to submit to Fortinet FortiSandbox.
Note: You can submit a single URL or multiple URLs in a list format. |
| VM Name |
(Optional) Name of the VM that will scan the specified URL.
If you do not specify a VM Name, then the VM Name will default to the one that will be used. |
| Timeout |
(Optional) Time after which the scan will timeout, i.e., the time in seconds of the length of the scan.
By default, the timeout value is set to 60 seconds. |
| Depth |
(Optional) This option specifies the depth of web links this operation should scan. Select this option, i.e., set to True, to crawl into the links of the specified URL for scanning purposes. Deselect this option, i.e., set to False, to scan only the specified URL and not any links within the URL. |
Output
The output contains the following populated JSON schema:
{
"ver": "",
"id": "",
"result": {
"url": "",
"status": {
"message": "",
"code": ""
},
"data": {
"msg": "",
"sid": "",
"error": ""
}
}
}
operation: Get System Status
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"result": {
"url": "",
"data": {
"Build": "",
"Major": "",
"Minor": "",
"Patch": "",
"Version": "",
"Hostname": "",
"Time Zone": "",
"Disk Usage": "",
"Inode Usage": "",
"System time": "",
"Branch Point": "",
"FIPS-CC mode": "",
"Platform Type": "",
"Serial-Number": "",
"Disk Available": "",
"License Status": "",
"Inode Available": "",
"vm_network_access": "",
"win_lic_activated": "",
"Platform Full Name": "",
"64-bit Applications": "",
"wf_server_accessible": "",
"fdn_server_accessible": "",
"cloud_server_accessible": "",
"Admin Domain Configuration": "",
"Release Version Information": ""
},
"status": {
"code": "",
"message": ""
}
},
"ver": "",
"id": ""
}
operation: Get Scan Stats
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"result": {
"url": "",
"data": {
"processing": "",
"suspicious_medium": "",
"suspicious_high": "",
"suspicious_low": "",
"malicious": "",
"pending": ""
},
"status": {
"message": "",
"code": ""
}
},
"ver": "",
"id": ""
}
operation: Get Submission Job List
Input parameters
| Parameter |
Description |
| Submission ID |
The ID of the submission whose associated Job IDs you want to retrieve from Fortinet FortiSandbox. |
Output
The output contains the following populated JSON schema:
{
"result": {
"url": "",
"data": {
"total_jids": "",
"jids": []
},
"status": {
"message": "",
"code": ""
}
},
"ver": "",
"id": ""
}
operation: Get Job Verdict Detail
Input parameters
| Parameter |
Description |
| Job ID |
The ID of the job whose job verdict details you want to retrieve from Fortinet FortiSandbox. |
Output
The output contains the following populated JSON schema:
{
"ver": "",
"id": "",
"result": {
"url": "",
"status": {
"message": "",
"code": ""
},
"data": {
"jid": "",
"ftype": "",
"file_name": "",
"category": "",
"rating": "",
"sha256": "",
"detection_os": "",
"vid": "",
"untrusted": "",
"start_ts": "",
"download_url": "",
"sha1": "",
"infected_os": "",
"score": "",
"finish_ts": "",
"detail_url": "",
"false_positive_negative": "",
"now": "",
"rating_source": "",
"malware_name": ""
}
}
}
operation: Get File Rating
Input parameters
| Parameter |
Description |
| Hash Type |
Type of the filehash based on which you want to retrieve the file rating from Fortinet FortiSandbox.
You can choose from the following values: MD5, SHA1, or SHA256. |
| Filehash |
Value of the filehash (considering the filehash type you have chosen from the Hash Type drop-down list) based on which you want to retrieve the file rating from Fortinet FortiSandbox. |
Output
The output contains the following populated JSON schema:
{
"ver": "",
"id": "",
"result": {
"url": "",
"status": {
"message": "",
"code": 0
},
"data": {
"rating": [],
"untrusted": "",
"start_ts": "",
"score": "",
"finish_ts": "",
"now": ""
}
}
}
operation: Get URL Rating
Input parameters
| Parameter |
Description |
| URL |
URL for which you want to retrieve the rating details from Fortinet FortiSandbox. |
Output
The output contains the following populated JSON schema:
{
"ver": "",
"id": "",
"result": {
"url": "",
"status": {
"code": "",
"message": ""
},
"data": [
{
"url": "",
"rating": [],
"start_ts": "",
"finish_ts": "",
"untrusted": "",
"now": "",
"behavior_info": ""
}
]
}
}
operation: Get File Verdict
Input parameters
| Parameter |
Description |
| Hash Type |
Type of the filehash based on which you want to retrieve the file verdict details from Fortinet FortiSandbox.
You can choose from the following values: MD5, SHA1, or SHA256. |
| Filehash |
Value of the filehash (considering the filehash type you have chosen from the Hash Type drop-down list) based on which you want to retrieve the file verdict details from Fortinet FortiSandbox. |
Output
The output contains the following populated JSON schema:
{
"result": {
"status": {
"message": "",
"code": ""
},
"data": [
{
"job_list": [
{
"finish_ts": "",
"malware_name": "",
"start_ts": "",
"untrusted": "",
"rating": "",
"jid": "",
"vid": "",
"false_positive_negative": "",
"score": "",
"rsrcid": "",
"behavior_info": ""
}
],
"kidsum": "",
"now": "",
"sid": "",
"checksum": ""
}
],
"url": ""
},
"id": "",
"ver": ""
}
operation: Get Job Behavior
Input parameters
| Parameter |
Description |
| Hash Type |
Type of the filehash whose associated job behavior details you want to retrieve from Fortinet FortiSandbox.
You can choose from the following values: MD5, SHA1, or SHA256. |
| Filehash |
Value of the filehash (considering the filehash type you have chosen from the Hash Type drop-down list) whose associated job behavior details you want to retrieve from Fortinet FortiSandbox. |
| Decode Behavior File String |
(Optional) Specify whether you want to retrieve job behavior details in decoded format. By default it retrieves in a gzip format. |
Output
The output contains the following populated JSON schema:
The output contains the following populated JSON schema:
Output schema when you choose Decode Behavior File String as false:
{
"id": "",
"result": {
"status": {
"message": "",
"code": ""
},
"data": {
"ver": "",
"rtype": "",
"behavior_files": ""
},
"url": ""
},
"ver": ""
}
Output schema when you choose Decode Behavior File String as true:
{
"id": "",
"result": {
"status": {
"message": "",
"code": ""
},
"data": {
"ver": "",
"rtype": "",
"behavior_files": {
"scan_md5": "",
"scan_submit": {
"7019748908627266956": {
"Static Scan Engine": {
"Rating": "",
"Static": {
"MD5": "",
"SHA1": "",
"Size": "",
"Type": "",
"score": "",
"SHA256": "",
"FileName": "",
"score_ai": "",
"fmw_extension": ""
},
"Version": "",
"Category": "",
"Revision": ""
}
}
}
}
},
"url": ""
},
"ver": ""
}
operation: Update White or Black List
Input parameters
| Parameter |
Description |
| List Type |
Type of list on Fortinet FortiSandbox in which you want to add the indicator.
You can select from the following list types: White or Black. |
| Indicator Type |
Type of indicator that you want to add to the whitelist or blacklist in Fortinet FortiSandbox.
You can choose from the following values: MD5, SHA1, SHA256, Domain, URL, or URL Regex. |
| Indicator Value |
Value of the indicator (considering the Indicator type you have chosen from the Indicator Type drop-down list) that you want to add to the whitelist or blacklist in Fortinet FortiSandbox. |
| Action |
Action that you want to apply on the whitelist or blacklist in Fortinet FortiSandbox, i.e., you can choose to append the specified indicator to the whitelist or blacklist in Fortinet FortiSandbox, or you can choose to delete the specified indicator from the whitelist or blacklist in Fortinet FortiSandbox.
You can choose from the following actions: Append, Replace, Clear, Download, or Delete. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"ver": "",
"result": {
"data": {
"msg": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
}
operation: Toggle FPN State
Input parameters
| Parameter |
Description |
| Job ID |
Job ID that you want to mark as false negative or false positive in Fortinet FortiSandbox. |
| Comments |
Comments that you want to provide for marking the specified job as false negative or false positive. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"ver": "",
"result": {
"data": {
"msg": "",
"error": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
}
operation: Get AV-Rescan Result
Input parameters
| Parameter |
Description |
| From |
Start DateTime from when you want to retrieve the AV-Rescan results from Fortinet FortiSandbox. |
| To |
End DateTime till when you want to retrieve the AV-Rescan results from Fortinet FortiSandbox. |
| Need AV Version |
(Optional) Select this option, i.e., set it to True, if you want this operation to return only the AV version.
By default, this is deselected, i.e., set as False. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"result": {
"url": "",
"status": {
"message": "",
"code": ""
},
"data": {
"rescan_list": [],
"avadb_ver": ""
}
},
"ver": ""
}
operation: Get All Installed VM
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"result": {
"data": {
"vm-list": [
{
"version": "",
"clonenum": "",
"status": "",
"name": "",
"id": ""
}
]
},
"status": {
"code": "",
"message": ""
},
"url": ""
},
"ver": "",
"id": ""
}
operation: Get PDF Report
Input parameters
| Parameter |
Description |
| Query Type |
Type of query to be used to retrieve the PDF report from Fortinet FortiSandbox.
Note: Query type only supports SHA256 filehash. |
| Query Value |
Value of the SHA256 filehash based on which you want to retrieve the PDF report from Fortinet FortiSandbox. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"@id": "",
"file": {
"id": "",
"@id": "",
"size": "",
"uuid": "",
"@type": "",
"assignee": "",
"filename": "",
"metadata": [],
"mimeType": "",
"thumbnail": "",
"uploadDate": ""
},
"cVEs": [],
"workspaces": [],
"vulnerabilities": [],
"name": "",
"type": "",
"uuid": "",
"@type": "",
"tasks": [],
"alerts": [],
"assets": [],
"owners": [],
"people": [],
"@context": "",
"assignee": "",
"comments": [],
"warrooms": [],
"incidents": [],
"createDate": "",
"createUser": {
"id": "",
"@id": "",
"name": "",
"uuid": "",
"@type": "",
"avatar": "",
"userId": "",
"userType": "",
"createDate": "",
"createUser": "",
"modifyDate": "",
"modifyUser": ""
},
"indicators": [],
"modifyDate": "",
"modifyUser": {
"id": "",
"@id": "",
"name": "",
"uuid": "",
"@type": "",
"avatar": "",
"userId": "",
"userType": "",
"createDate": "",
"createUser": "",
"modifyDate": "",
"modifyUser": ""
},
"recordTags": [],
"userOwners": [],
"description": ""
}
operation: List Filehash or URL From Malware Package or URL Package
Input parameters
| Parameter |
Description |
| Type |
Type, based on which you want to retrieve a list of file hashes or URLs from the Malware Package or URL Package in Fortinet FortiSandbox.
You can choose from the following values: MD5, SHA1, SHA256, or URL. |
| Lazy |
Use this parameter to specify the major and minor numbers of the Malware Package or the URL Package.
If you clear this option, i.e., set it to False, then the list of file hashes or URLs is retrieved from the Malware Package or URL Package of the specified major and minor number.
If you select this option, i.e., set it to True, then the latest version of the Malware Package or URL Package is used to retrieve the list of file hashes or URLs.
If this parameter is set as False, then you must specify the following:
- Major: Major number of the Malware Package or the URL Package to be used to retrieve the list of file hashes or URLs.
- Minor: Minor number of the Malware Package or the URL Package to be used to retrieve the list of file hashes or URLs.
|
Output
The output contains the following populated JSON schema:
{
"result": {
"status": {
"code": "",
"message": ""
},
"url": "",
"data": {
"md5sum": "",
"major": "",
"download_file": "",
"minor": ""
}
},
"id": "",
"ver": ""
}
operation: Update Allow or Block List
Input parameters
| Parameter |
Description |
| List Type |
Select the list type on Fortinet FortiSandbox based on which to add the indicator. You can select from the following options:
|
| Indicator Type |
Select the indicator type to add to the allow or block list in Fortinet FortiSandbox. You can select from the following options:
- MD5
- SHA1
- SHA256
- Domain
- URL
- URL Regex
|
| Action |
Select the action to apply on the allow or blocklist in Fortinet FortiSandbox. You can select from the following options:
- APPEND: Select this option to append the selected List Type. Specify values in the following fields:
- REPLACE: Select this option to replace the selected List Type. Specify values in the following fields:
- CLEAR: Select this option to clear the selected List Type.
- DOWNLOAD: Select this option to download the selected List Type as an attachment in the FortiSOAR™'s Attachments module.
- DELETE: Select this option to delete a comma-separated list of indicators from the selected List Type. Specify the indicator values to delete in the Indicator Value field.
|
Output
The output contains the following populated JSON schema:
Output schema when you choose Action as DOWNLOAD:
{
"id": "",
"@id": "",
"file": {
"id": "",
"@id": "",
"size": "",
"uuid": "",
"@type": "",
"assignee": "",
"filename": "",
"metadata": [],
"mimeType": "",
"thumbnail": "",
"uploadDate": ""
},
"name": "",
"type": "",
"uuid": "",
"@type": "",
"tasks": [],
"alerts": [],
"assets": [],
"owners": [],
"people": [],
"@context": "",
"assignee": "",
"comments": [],
"warrooms": [],
"incidents": [],
"createDate": "",
"createUser": {
"id": "",
"@id": "",
"name": "",
"uuid": "",
"@type": "",
"avatar": "",
"userId": "",
"userType": "",
"createDate": "",
"createUser": "",
"modifyDate": "",
"modifyUser": ""
},
"indicators": [],
"modifyDate": "",
"modifyUser": {
"id": "",
"@id": "",
"name": "",
"uuid": "",
"@type": "",
"avatar": "",
"userId": "",
"userType": "",
"createDate": "",
"createUser": "",
"modifyDate": "",
"modifyUser": ""
},
"recordTags": [],
"userOwners": [],
"description": ""
}
Output schema when Action is NOT DOWNLOAD:
{
"id": "",
"ver": "",
"result": {
"data": {
"msg": ""
},
"status": {
"code": "",
"message": ""
},
"url": ""
}
}
Included playbooks
The Sample - Fortinet FortiSandbox - 2.1.0 playbook collection comes bundled with the Fortinet FortiSandbox connector. These playbooks contain steps using which you can perform all supported actions. You can see bundled playbooks in the Automation > Playbooks section in FortiSOAR™ after importing the Fortinet FortiSandbox connector.
- File > FortiSandbox > Enrichment
- Get All Installed VM
- Get AV-Rescan Result
- Get File Rating
- Get File Verdict
- Get Job Behavior
- Get Job Verdict Detail
- Get PDF Report
- Get Scan Stats
- Get Submission Job List
- Get System Status
- Get URL Rating
- List Filehash or URL From Malware Package or URL Package
- Toggle FPN State
- Submit File
- Submit URL
- Update White or Black List
- Update Allow or Block List
- URL > FortiSandbox > Enrichment
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection since the sample playbook collection gets deleted during the connector upgrade and delete.
Pluggable Enrichment
The Sample - Fortinet FortiSandbox - 2.1.0 playbook collection contains pluggable enrichment playbooks that are used to provide verdicts for File Hash and URL indicator types. The pluggable enrichment playbooks are in the format: indicatorType > Fortinet FortiSandbox > Enrichment. For example, URL > Fortinet FortiSandbox > Enrichment.
The Configuration step in all the pluggable enrichment playbooks contains variables that have default values for calculating the Verdict for various indicator types.
NOTE: Create a global variable fortisandbox_upload_file to manage the upload file operation performed by the File > FortiSandbox > Enrichment playbook. The value true uploads the file to Fortinet FortiSandbox servers; false skips the upload.
The following table lists the variable names and their default values:
| Variable Name |
Default value (score) |
good_score |
0 |
suspicious_score |
3 or 4 |
malicious_score |
1 or 2 |
Based on the above default values, the Fortinet FortiSandbox integration API response returns the verdict, cti_score, and other variables.
| Variable Name |
Description |
Return Value |
verdict |
This connector returns a high-reliability value called verdict. Use this verdict to find the reputation of the various types of indicators. |
If the score value returned is between the value specified in the malicious_score variable, then return the verdict as Malicious.
If the score value returned is between the value specified in the suspicious_score variable, then return the verdict as Suspicious.
If the score value returned is between the value specified in the good_score variable, then return the verdict as Good.
For any other value, return the verdict as No Reputation Available
|
cti_name |
The name of the connector is called the CTI (Cyber Threat Intelligence) name |
FortiSandbox |
cti_score |
The verdict value returned by the integration API. |
score |
source_data |
The source_data response returned by the integration API. |
A JSON response object containing the source data of the threat intelligence integration. |
field_mapping |
The mapping of the FortiSOAR Indicator module fields with the FortiSandbox response fields. |
A JSON response object containing the field mapping of the threat intelligence integration. |
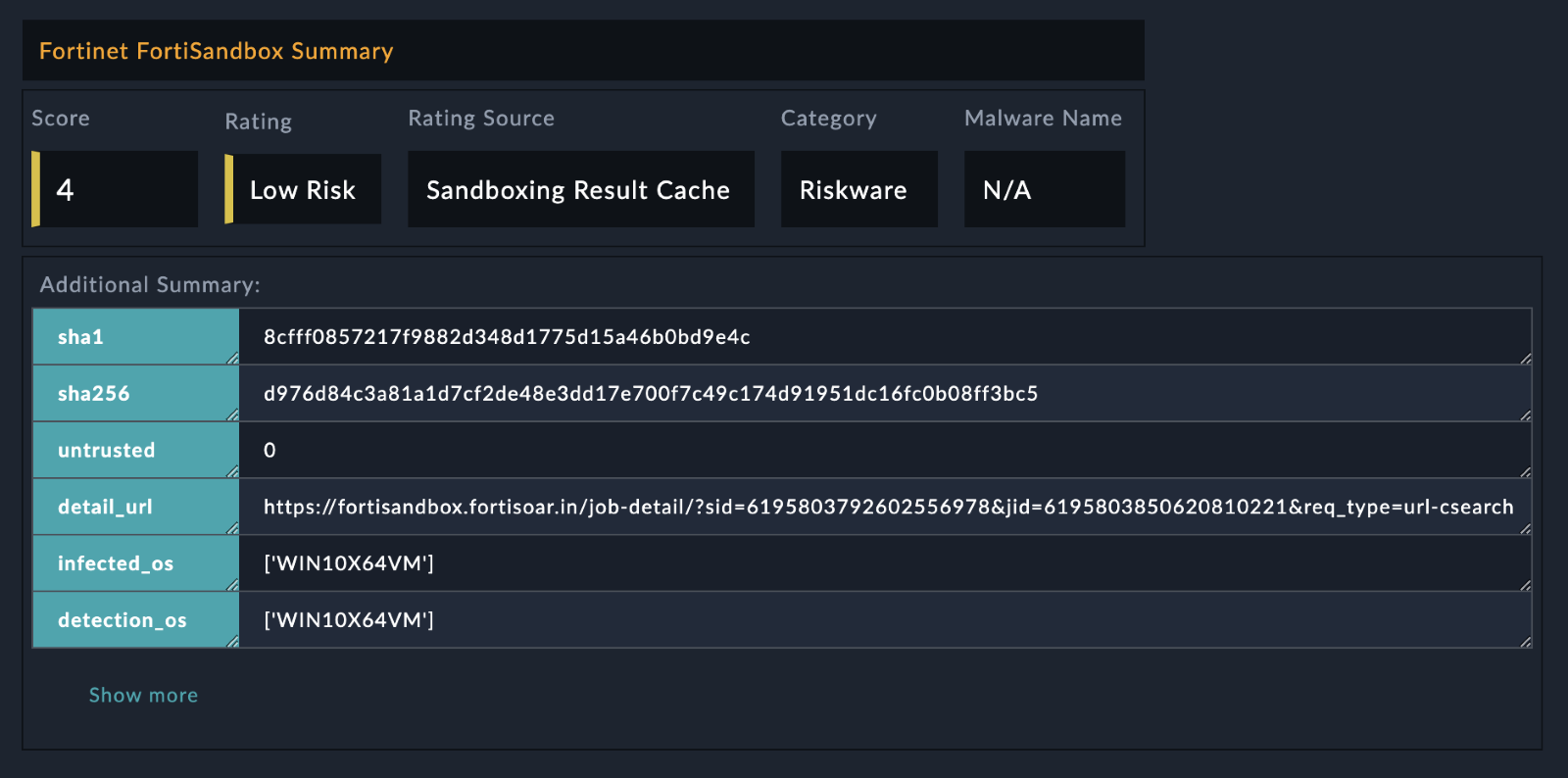
enrichment_summary |
The contents that are added, in the HTML format, in the Description field of the specified FortiSOAR indicator record. |
The following values are returned in the HTML format:
- Score
- Rating
- Rating Source
- Category
- Malware Name
The following image displays a sample of the populated Description field in a FortiSOAR indicator record:
 |







