About the connector
The RSA NetWitness Platform is an evolved SIEM and threat detection and response solution that allows security teams to rapidly detect and respond to any threat, anywhere.
This document provides information about the RSA NetWitness SIEM connector, which facilitates automated interactions, with a RSA NetWitness SIEM server using FortiSOAR™ playbooks. Add the RSA NetWitness SIEM connector as a step in FortiSOAR™ playbooks and perform automated operations, such as retrieving incidents from RSA NetWitness SIEM and retrieving alerts associated with incidents from RSA NetWitness SIEM.
Version information
Connector Version: 1.1.0
Authored By: Fortinet
Certified: No
Release Notes for version 1.1.0
Following enhancements have been made to the RSA NetWitness SIEM Connector in version 1.1.0:
- The connector now supports data ingestion using the Data Ingestion Wizard.
Installing the connector
Use the Content Hub to install the connector. For the detailed procedure to install a connector, click here.
You can also use the yum command as a root user to install the connector:
yum install cyops-connector-rsa-netwitness-siem
Prerequisites to configuring the connector
- You must have the URL of RSA NetWitness SIEM server to connect and perform automated operations and credentials (username-password pair) to access that server.
- The FortiSOAR™ server should have outbound connectivity to port 443 on the RSA NetWitness SIEM server.
Minimum Permissions Required
Configuring the connector
For the procedure to configure a connector, click here
Configuration parameters
In FortiSOAR™, on the Connectors page, click the RSA NetWitness SIEM connector row (if you are in the Grid view on the Connectors page) and in the Configurations tab enter the required configuration details:
| Parameter |
Description |
| Server URL |
URL of the RSA NetWitness SIEM server to connect and perform the automated operations. |
| Username |
Username of the RSA NetWitness SIEM server to connect and perform the automated operations. |
| Password |
Password of the RSA NetWitness SIEM server to connect and perform the automated operations. |
| Verify SSL |
Specifies whether the SSL certificate for the server is to be verified or not.
By default, this option is set to True. |
Actions supported by the connector
The following automated operations can be included in playbooks, and you can also use the annotations to access operations from FortiSOAR™ release 4.10.0 and onwards:
| Function |
Description |
Annotation and Category |
| Get Incident |
Retrieves a single incident from RSA NetWitness SIEM based on the incident's unique identifier. |
get_incident
Investigation |
| Get Incidents by Date Range |
Retrieves all incidents from RSA NetWitness SIEM based on the date and time they were created in RSA NetWitness SIEM. |
get_incident_by_date_range
Investigation |
| Get Incident Related Alerts |
Retrieves all alerts that are associated with an incident from RSA NetWitness SIEM based on the incident’s unique identifier. |
get_incidents_alerts
Investigation |
operation: Get Incident
Input parameters
| Parameter |
Description |
| Incident ID |
Specify the unique identifier of the incident based on which you want to retrieve the incident from RSA NetWitness SIEM. |
Output
The output contains the following populated JSON schema:
{
"id": "",
"title": "",
"summary": "",
"priority": "",
"riskScore": "",
"status": "",
"alertCount": "",
"averageAlertRiskScore": "",
"sealed": "",
"totalRemediationTaskCount": "",
"openRemediationTaskCount": "",
"created": "",
"lastUpdated": "",
"lastUpdatedBy": "",
"assignee": "",
"sources": [],
"ruleId": "",
"firstAlertTime": "",
"categories": [
{
"id": "",
"parent": "",
"name": ""
}
],
"journalEntries": [
{
"id": "",
"author": "",
"notes": "",
"created": "",
"lastUpdated": "",
"milestone": ""
}
],
"createdBy": "",
"deletedAlertCount": "",
"eventCount": "",
"alertMeta": {
"SourceIp": [],
"DestinationIp": []
}
}
operation: Get Incidents by Date Range
Input parameters
| Parameter |
Description |
| Start Time |
Specify the timestamp based on which to retrieve incidents from RSA NetWitness SIEM. Incidents that were created on or after this timestamp are retrieved from RSA NetWitness SIEM. |
| End Time |
Specify the timestamp based on which to retrieve incidents from RSA NetWitness SIEM. Incidents that were created on or before this timestamp are retrieved from RSA NetWitness SIEM. |
| Page Number |
(Optional) Specify the page number from which to request for data. |
| Page Size |
(Optional) Specify the maximum number of records that you want to return in a single page. |
Output
The output contains the following populated JSON schema:
{
"items": [
{
"id": "",
"title": "",
"summary": "",
"priority": "",
"riskScore": "",
"status": "",
"alertCount": "",
"averageAlertRiskScore": "",
"sealed": "",
"totalRemediationTaskCount": "",
"openRemediationTaskCount": "",
"created": "",
"lastUpdated": "",
"lastUpdatedBy": "",
"assignee": "",
"sources": [],
"ruleId": "",
"firstAlertTime": "",
"categories": [
{
"id": "",
"parent": "",
"name": ""
}
],
"journalEntries": [
{
"id": "",
"author": "",
"notes": "",
"created": "",
"lastUpdated": "",
"milestone": ""
}
],
"createdBy": "",
"deletedAlertCount": "",
"eventCount": "",
"alertMeta": {
"SourceIp": [],
"DestinationIp": []
}
}
],
"pageNumber": "",
"pageSize": "",
"totalPages": "",
"totalItems": "",
"hasNext": "",
"hasPrevious": ""
}
operation: Get Incident Related Alerts
Input parameters
| Parameter |
Description |
| Incident ID |
Specify the unique identifier of the incident whose associated alerts you want to retrieve from RSA NetWitness SIEM. |
| Page Number |
(Optional) Specify the page number from which you want to request for data. |
| Page Size |
(Optional) Specify the maximum number of records that you want to return in a single page. |
Output
The output contains the following populated JSON schema:
{
"items": [
{
"id": "",
"title": "",
"detail": "",
"created": "",
"source": "",
"riskScore": "",
"type": "",
"events": [
{
"source": {
"device": {
"ipAddress": "",
"port": "",
"macAddress": "",
"dnsHostname": "",
"dnsDomain": ""
},
"user": {
"username": "",
"emailAddress": "",
"adUsername": "",
"adDomain": ""
}
},
"destination": {
"device": {
"ipAddress": "",
"port": "",
"macAddress": "",
"dnsHostname": "",
"dnsDomain": ""
},
"user": {
"username": "",
"emailAddress": "",
"adUsername": "",
"adDomain": ""
}
},
"domain": "",
"eventSource": "",
"eventSourceId": ""
}
]
}
],
"pageNumber": "",
"pageSize": "",
"totalPages": "",
"totalItems": "",
"hasNext": "",
"hasPrevious": ""
}
Included playbooks
The Sample - RSA NetWitness SIEM - 1.1.0 playbook collection comes bundled with the RSA NetWitness SIEM connector. These playbooks contain steps using which you can perform all supported actions. You can see bundled playbooks in the Automation > Playbooks section in CyOPsTM after importing the RSA NetWitness SIEM connector.
- Get Incident
- Get Incident Related Alerts
- Get Incidents by Date Range
- > RSA NetWitness SIEM > Fetch
- >> RSA NetWitness SIEM > Fetch Associated events for Incident
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection since the sample playbook collection gets deleted during connector upgrade and delete.
Data Ingestion Support
Use the Data Ingestion Wizard to easily ingest data into FortiSOAR™ by pulling Incidents from RSA NetWitness SIEM. Currently, Incidents ingested from RSA NetWitness SIEM is mapped to Alerts in FortiSOAR™. For more information on the Data Ingestion Wizard, see the Connectors Guide in the FortiSOAR™ product documentation.
Configure Data Ingestion
You can configure data ingestion using the Data Ingestion Wizard to seamlessly map the incoming RSA NetWitness SIEM Incidents to FortiSOAR™'s Alerts.
The Data Ingestion Wizard helps you to configure the scheduled pulling of data from RSA NetWitness SIEM into FortiSOAR™. It also lets you pull some sample data from RSA NetWitness SIEM using which you can define the mapping of data between RSA NetWitness SIEM and FortiSOAR™. The mapping of common fields is generally already done by the Data Ingestion Wizard; users are mostly required to only map any custom fields that are added to the RSA NetWitness SIEM Incidents.
-
To begin configuring data ingestion, click Configure Data Ingestion on the RSA NetWitness SIEM connector's Configurations page.
Click Let's Start by fetching some data, to open the Fetch Sample Data screen.
Sample data is required to create a field mapping between RSA NetWitness SIEM data and FortiSOAR™. The sample data is pulled from connector actions or ingestion playbooks.
-
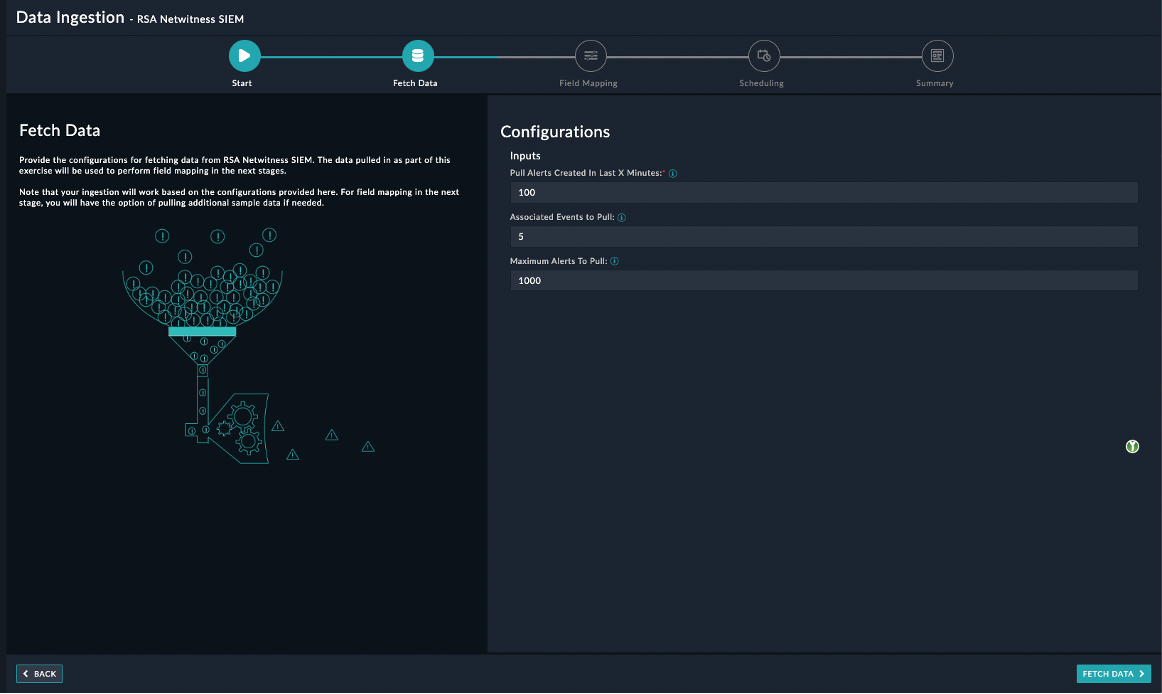
On the Fetch Data screen, provide the configurations required to fetch Incidents from RSA NetWitness SIEM.
You can specify Pull Alerts Created in Last X Minutes, Associated Events to Pull, and Maximum Alerts to Pull. The fetched data is used to create a mapping between the RSA NetWitness SIEM Incidents and FortiSOAR™ Alerts.
The fetched data is used to create a mapping between the Incidents from RSA NetWitness SIEM and FortiSOAR Alerts. Once you have completed specifying the configurations, click Fetch Data.
-
On the Field Mapping screen, map the fields of the ingested Incidents RSA NetWitness SIEM to the fields of an Alert present in FortiSOAR™.
To map a field, click the key in the sample data to add the Jinja value of the field. For example, to map the Severity parameter of an ingested Incident from RSA NetWitness SIEM to the Alert Severity parameter of a FortiSOAR™ Alert, click the Severity field and then click the Alert Severity field to populate its keys:
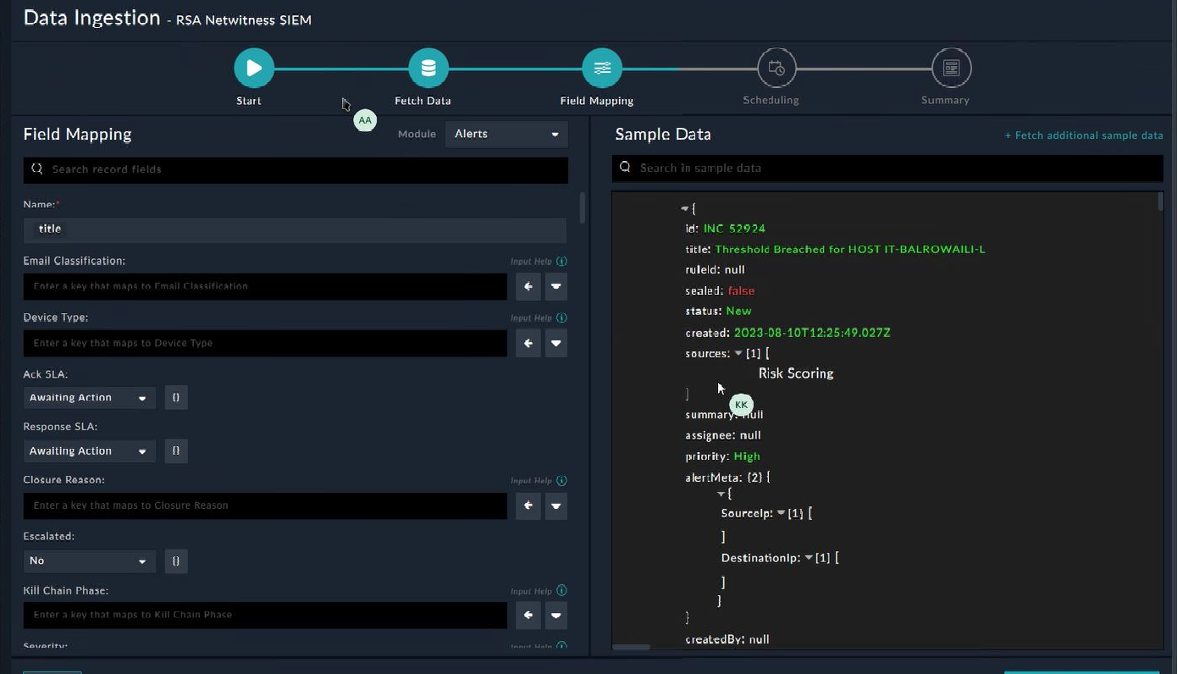
For more information on field mapping, see the Data Ingestion chapter in the Connectors Guide in the FortiSOAR™ product documentation. Once you have completed the mapping of fields, click Save Mapping & Continue.
-
(Optional) Use the Scheduling screen to configure schedule-based ingestion, i.e., specify the polling frequency to RSA NetWitness SIEM, so that the content gets pulled from the RSA NetWitness SIEM integration into FortiSOAR™
On the Scheduling screen, from the Do you want to schedule the ingestion? drop-down list, select Yes.
In the Configure Schedule Settings section, specify the Cron expression for the schedule. For example, if you want to pull data from Sophos Central every 5 minutes, click Every X Minute, and in the minute box enter */5. This means that the alerts will be pulled from Sophos Central every 5 minutes:
In the Configure Schedule Settings section, specify the Cron expression for the schedule. For example, if you want to pull data from RSA NetWitness SIEM every 10 minutes, click Every X Minute, and in the minute box enter */10. This means that the Incidents will be pulled from RSA NetWitness SIEM every 10 minutes:
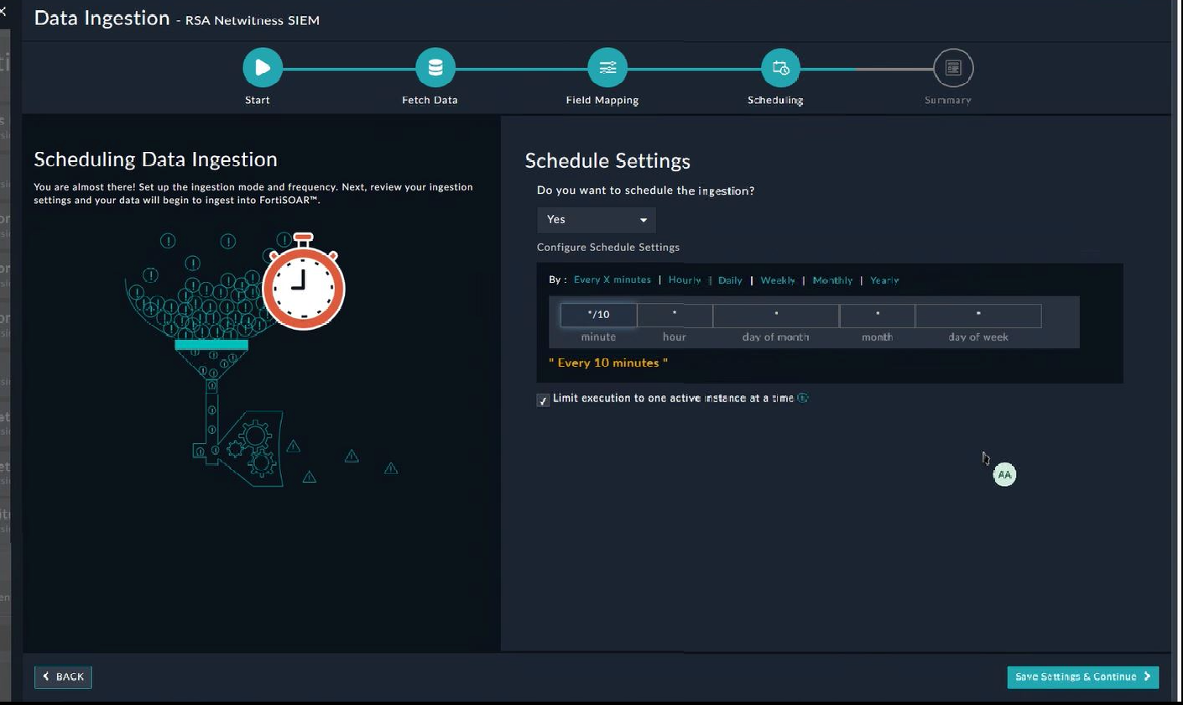
Once you have completed scheduling, click Save Settings & Continue.
-
The Summary screen displays a summary of the mapping done, and it also contains links to the Ingestion playbooks. Click Done to complete the data ingestion and exit the Data Ingestion Wizard.









