Testing and monitoring
The basic configuration is complete at this point. Test the connections to the Internet and corporate networks on an endpoint.
To test connection to the Internet on a Windows computer with a RADIUS user:
- From the endpoint, open a browser.
- Browse to a webpage.
- An authentication prompt appears. Enter your username and password.

- Once authenticated, you can browse to any webpage. FortiSASE scans this traffic.
- Browse to a webpage that triggers a Web Filter violation. The browser shows a message that FortiSASE is blocking the webpage.
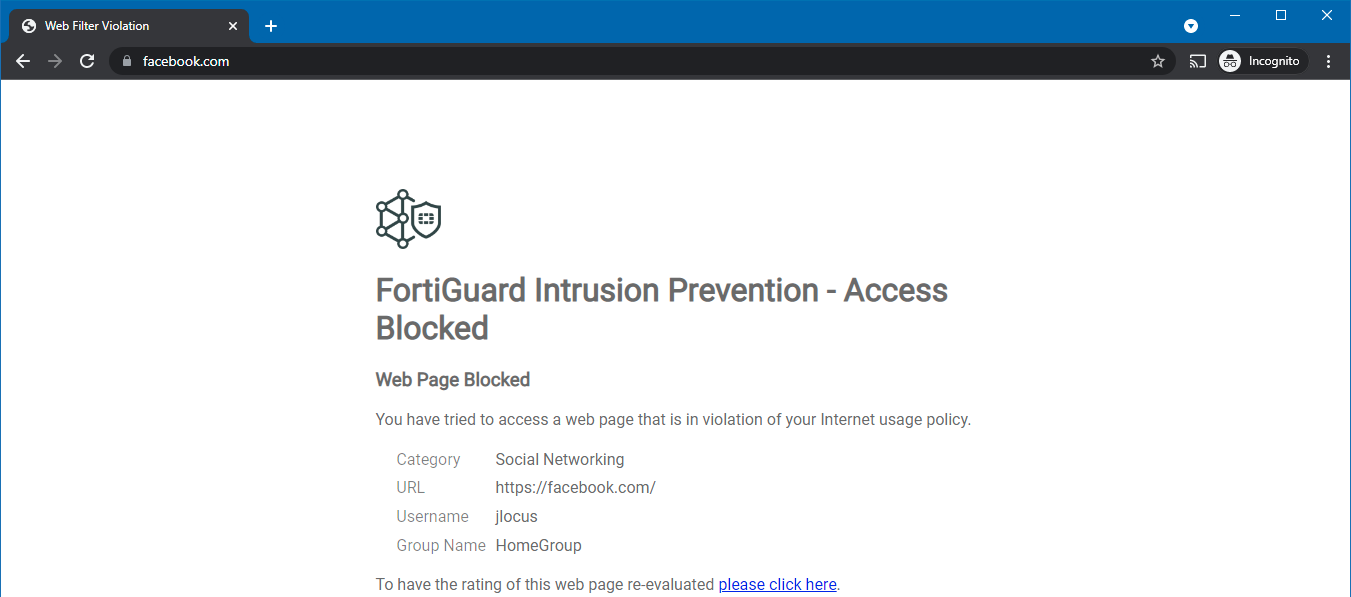
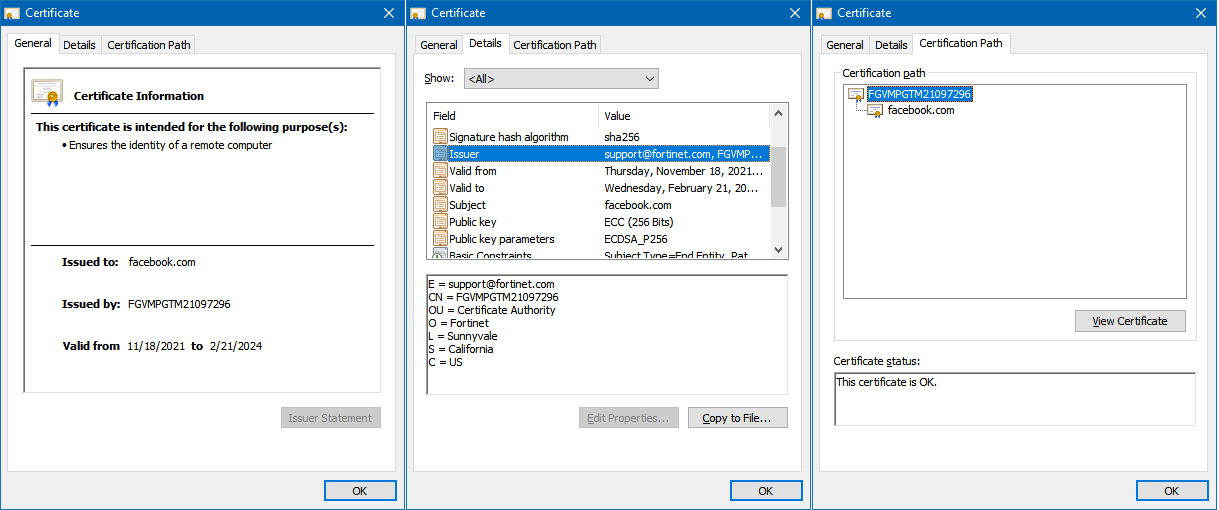
For the blocked webpage message to display without a certificate warning, the FortiSASE root certificate authority certificate must be installed on the endpoint. The following shows a valid certificate chain.
- In FortiSASE, go to Session Monitor to see the logged in user.

To test connection to the Internet on a macOS computer with an Azure Active Directory (AD) user:
- From the endpoint, open a browser.
- Browse to a webpage. The page redirects to a Microsoft login page to perform single sign on.
- Log in using your Azure AD credentials.
- Once authenticated, you can browse to any webpage. FortiSASE scans this traffic.
- To properly browse any HTTPS websites, you must install the FortiSASE root certificate on the endpoint. Double-click the FortiSASE certificate that the administrator provided during onboarding. In the Keychain field, select System, then click Add.
- When you view the certificate, the root certificate appears as not trusted. Expand the Trust section. In the When using this certificate field, select Always Trust.

- Save the configuration and add the certificate to the system keychain.
- You can connect to HTTPS websites without seeing a warning. Browse to an HTTPS website, then go to Session Monitor in FortiSASE to see the logged in user.
To test connection to the corporate network:
- On the endpoint, connect to the SSL VPN gateway using the VPN client (FortiClient). In this scenario, the SSL VPN user and FortiSASE user is from the same source.
- Once VPN connects, verify the routes from Windows Command Prompt:
> route print Active Routes: Network Destination Netmask Gateway Interface Metric 0.0.0.0 0.0.0.0 10.10.10.1 10.10.10.25 60 10.10.10.0 255.255.255.0 On-link 10.10.10.25 316 10.212.134.200 255.255.255.255 On-link 10.212.134.200 257 127.0.0.0 255.0.0.0 On-link 127.0.0.1 331 127.0.0.1 255.255.255.255 On-link 127.0.0.1 331 127.255.255.255 255.255.255.255 On-link 127.0.0.1 331 192.168.20.0 255.255.255.0 10.212.134.201 10.212.134.200 1
The corporate network (192.168.20.0/24) is routed through the SSL VPN interface.
- In FortiOS, go to Firewall > Network Dashboard > SSL-VPN widget to see the logged in VPN user.

- From the endpoint, connect to an internal resource on the corporate network. The connection succeeds.

