About the connector
VirusTotal provides a service that analyzes suspicious files and URLs and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware. This connector facilitates automated operations such as scanning and analyzing suspicious files and URLs and retrieving reports from VirusTotal for files, IP addresses, and domains.
This document provides information about the VirusTotal connector, which facilitates automated interactions with a VirusTotal server using FortiSOAR™ playbooks. Add the VirusTotal connector as a step in FortiSOAR™ playbooks and perform automated operations, such as scanning and analyzing suspicious files and URLs and retrieving reports from VirusTotal for files, IP addresses, and domains.
Field mappings are added to pluggable enrichment playbooks for IP addresses, file hashes, files, URLs, and domains that automatically enrich data when you install and configure the VirusTotal connector. For more information, see the Pluggable Enrichment topic.
Version information
Connector Version: 3.1.2
FortiSOAR™ Version Tested on: 7.4.1-3167
VirusTotal Version Tested on: 3.0
Authored By: Fortinet
Certified: Yes
Release Notes for version 3.1.2
The following enhancements have been made to the VirusTotal Connector in version 3.1.2:
- Enhanced the enrichment playbooks to better manage responses from VirusTotal.
Installing the connector
Use the Content Hub to install the connector. For the detailed procedure to install a connector, click here.
You can also use the following yum command as a root user to install connectors from an SSH session:
yum install cyops-connector-virustotal
Prerequisites to configuring the connector
- You must have the URL of the VirusTotal server and the API key used to access the VirusTotal endpoint to which you will connect and perform the automated operations.
- The FortiSOAR™ server should have outbound connectivity to port 443 on VirusTotal.
- If you are running the Submit File action on an FSR agent, then ensure that you have given the agent appliance
Read permissions on the Attachments and Files modules. The agent appliance requires these permissions to be able to use the Attachment ID input in the Submit File action. For more information on FSR agents, see the FortiSOAR Product Documentation.
Minimum Permissions Required
Configuring the connector
For the procedure to configure a connector, click here.
Configuration parameters
In FortiSOAR™, on the Content Hub (or Connector Store) page, click the Manage tab, and then click the VirusTotal connector card. On the connector popup, click the Configurations tab to enter the required configuration details:
| Parameter |
Description |
| Server URL |
URL of the VirusTotal endpoint server to which you will connect and perform the automated operations. |
| API Key |
API key to access the VirusTotal endpoint to which you will connect and perform the automated operations. |
| Verify SSL |
Specifies whether the SSL certificate for the server is to be verified. |
Actions supported by the connector
The following automated operations can be included in playbooks, and you can also use the annotations to access operations from FortiSOAR™:
| Function |
Description |
Annotation and Category |
| Get Widget Rendering URL |
Retrieves a URL from VirusTotal that renders a widget within an iframe and is valid for three days. |
get_widget_rendering_url
Investigation |
| Get Widget HTML Content |
Retrieves the actual HTML content of the widget report for a given observable. |
get_widget_html_content
Investigation |
| Submit File |
Scans and analyzes files submitted to VirusTotal from FortiSOAR™ to determine if it is suspicious based on the Attachment ID or File IRI you have specified. |
submit_sample Investigation |
| Submit URL for scanning |
Scans and analyzes the URL submitted to VirusTotal to determine if it is suspicious based on the URL you have specified. |
submit_url Investigation |
| Get File Reputation |
Retrieves a report from VirusTotal for the file that you have submitted to determine if it is suspicious based on the file hash value you have specified. |
file_reputation Investigation |
| Get IP Reputation |
Retrieves a report from VirusTotal for the IP address submitted to determine if it is suspicious based on the IP address you have specified. |
ip_reputation Investigation |
| Get Domain Reputation |
Retrieves a report from VirusTotal for the domain submitted to determine if it is suspicious based on the domain name you have specified. |
domain_reputation Investigation |
| Get URL Reputation |
Retrieves a report from VirusTotal for the URL submitted to determine if it is suspicious based on the URL you have specified. |
url_reputation Investigation |
| Get Analysis Details |
Retrieves details of a File or URL analysis from VirusTotal for the File or URL that you had submitted for scanning and analysis to VirusTotal using the "Submit File" or "Submit URL for scanning" action. |
analysis_file Investigation |
| Custom API Endpoint |
Allows querying a custom API endpoint in VirusTotal based on the endpoint and request you have specified. |
custom_endpoint Query |
operation: Get Widget Rendering URL
Input parameters
| Parameter |
Description |
| Indicator |
Specify the indicator value based on which you want to retrieve the widget rendering URL from VirusTotal. |
| Foreground Color |
Specify the primary foreground color in hex notation |
| Primary Background Color |
Specify the primary background color in hex notation |
| Secondary Background Color |
Specify the secondary background color in hex notation |
| Border Color |
Specify the border color in hex notation |
Output
The output contains the following populated JSON schema:
{
"data": {
"url": "",
"found": "",
"detection_ratio": {
"detections": "",
"total": ""
},
"type": "",
"id": ""
}
}
operation: Get Widget HTML Content
Input parameters
| Parameter |
Description |
| Token |
Specify the token provided by the Get Widget Rendering URL operation response. |
Output
The output contains a non-dictionary value.
operation: Submit File
Input parameters
Note: Using this operation, you submit files available in the FortiSOAR™'s Attachments module to VirusTotal.
| Parameter |
Description |
| Type |
Specify the type of file that you want to submit to VirusTotal for analysis. The type can be an Attachment ID or a File IRI. |
| Reference ID |
Specify the reference ID that is used to access the attachment metadata from the FortiSOAR™ Attachments module. In the playbook, this defaults to the{{vars.attachment_id}} value or the {{vars.file_iri}} value. |
Output
The JSON output contains the scan_id of the file. You can use this scan_id in the future to query and retrieve scan reports from VirusTotal for this file.
The output contains the following populated JSON schema:
{
"id": "",
"type": ""
}
operation: Submit URL for scanning
Input parameters
| Parameter |
Description |
| Scan URL |
Specify the URL that you want to submit to VirusTotal for scanning. |
Output
The JSON output contains the scan_id of the URL. You can use this scan_id in the future to query and retrieve scan reports from VirusTotal for this URL.
The output contains the following populated JSON schema:
{
"type": "",
"id": ""
}
operation: Get File Reputation
Input parameters
| Parameter |
Description |
| File Hash |
Specify the File Hash of the file for which you want to retrieve a VirusTotal report. |
| Relationships to Include |
(Optional) Select the relationships such as Comments, Graphs, etc. that you want to include in the output of this operation. |
Output
The JSON contains the report from VirusTotal for a sample based on the specified file hash. You can use this report to determine if the submitted files are suspicious.
The output contains the following populated JSON schema (dynamic output schema):
{
"relationships": {
"meta": {
"cursor": ""
},
"data": [
{
"type": "",
"id": ""
}
],
"links": {
"self": "",
"related": "",
"next": ""
}
},
"attributes": {
"type_description": "",
"bytehero_info": "",
"vhash": "",
"trid": [],
"creation_date": "",
"names": [],
"last_modification_date": "",
"type_tag": "",
"times_submitted": "",
"total_votes": {
"harmless": "",
"malicious": ""
},
"size": "",
"popular_threat_classification": {
"suggested_threat_label": "",
"popular_threat_category": [],
"popular_threat_name": []
},
"authentihash": "",
"last_submission_date": "",
"reputation": "",
"sha256": "",
"type_extension": "",
"tags": [],
"last_analysis_date": "",
"unique_sources": "",
"first_submission_date": "",
"sha1": "",
"ssdeep": "",
"md5": "",
"pe_info": {
"timestamp": "",
"overlay": {
"entropy": "",
"offset": "",
"chi2": "",
"filetype": "",
"size": "",
"md5": ""
},
"entry_point": "",
"machine_type": "",
"imphash": "",
"sections": [
{
"name": "",
"chi2": "",
"virtual_address": "",
"entropy": "",
"raw_size": "",
"flags": "",
"virtual_size": "",
"md5": ""
}
],
"import_list": []
},
"magic": "",
"last_analysis_stats": {
"harmless": "",
"type-unsupported": "",
"suspicious": "",
"confirmed-timeout": "",
"timeout": "",
"failure": "",
"malicious": "",
"undetected": ""
},
"last_analysis_results": {}
},
"type": "",
"id": "",
"links": {
"self": ""
}
}
operation: Get IP Reputation
Input parameters
| Parameter |
Description |
| IP Address |
Specify the IP address for which you want to retrieve a VirusTotal report. |
| Relationships to Include |
(Optional) Select the relationships such as Comments, Graphs, etc. that you want to include in the output of this operation. |
Output
The JSON contains the report from VirusTotal for a sample based on the specified IP address. You can use this report to determine if the submitted IP address is suspicious.
The output contains the following populated JSON schema:
{
"attributes": {
"regional_internet_registry": "",
"jarm": "",
"network": "",
"last_https_certificate_date": "",
"tags": [],
"country": "",
"as_owner": "",
"last_analysis_stats": {
"harmless": "",
"malicious": "",
"suspicious": "",
"undetected": "",
"timeout": ""
},
"asn": "",
"whois_date": "",
"last_analysis_results": {},
"reputation": "",
"last_modification_date": "",
"total_votes": {
"harmless": "",
"malicious": ""
},
"last_https_certificate": {},
"continent": "",
"whois": {
"raw": [],
"data": ""
}
},
"type": "",
"id": "",
"links": {
"self": ""
}
}
operation: Get Domain Reputation
Input parameters
| Parameter |
Description |
| Domain |
Specify the domain name for which you want to retrieve a VirusTotal report. |
| Relationships to Include |
(Optional) Select the relationships such as Comments, Graphs, etc. that you want to include in the output of this operation. |
Output
The JSON contains the report from VirusTotal for a sample based on the specified domain name. You can use this report to determine if the submitted domain is suspicious.
The output contains the following populated JSON schema:
{
"attributes": {
"last_dns_records": [],
"jarm": "",
"whois": {
"raw": [],
"data": ""
},
"last_https_certificate_date": "",
"tags": [],
"popularity_ranks": {},
"last_dns_records_date": "",
"last_analysis_stats": {
"harmless": "",
"malicious": "",
"suspicious": "",
"undetected": "",
"timeout": ""
},
"whois_date": "",
"reputation": "",
"last_analysis_results": {},
"last_modification_date": "",
"last_https_certificate": {
"public_key": {
"rsa": {
"key_size": "",
"modulus": "",
"exponent": ""
},
"algorithm": ""
},
"thumbprint_sha256": "",
"tags": [],
"signature_algorithm": "",
"subject": {
"CN": ""
},
"validity": {
"not_after": "",
"not_before": ""
},
"version": "",
"extensions": {
"certificate_policies": [],
"extended_key_usage": [],
"tags": [],
"subject_alternative_name": [],
"authority_key_identifier": {
"keyid": ""
},
"ca_information_access": {
"CA Issuers": "",
"OCSP": ""
},
"subject_key_identifier": "",
"key_usage": [],
"1.3.6.1.4.1.11129.2.4.2": "",
"CA": ""
},
"cert_signature": {
"signature_algorithm": "",
"signature": ""
},
"serial_number": "",
"thumbprint": "",
"issuer": {
"C": "",
"CN": "",
"O": ""
},
"size": ""
},
"categories": {},
"total_votes": {
"harmless": "",
"malicious": ""
}
},
"type": "",
"id": "",
"links": {
"self": ""
}
}
operation: Get URL Reputation
Input parameters
| Parameter |
Description |
| URL |
Specify the URL for which you want to retrieve a VirusTotal report. |
| Relationships to Include |
(Optional) Select the relationships such as Comments, Graphs, etc. that you want to include in the output of this operation. |
Output
The JSON contains the report from VirusTotal for a sample based on the specified URL. You can use this report to determine if the submitted URL is suspicious.
The output contains the following populated JSON schema (dynamic output schema):
{
"relationships": {
"meta": {
"cursor": ""
},
"data": [
{
"type": "",
"id": ""
}
],
"links": {
"self": "",
"related": "",
"next": ""
}
},
"attributes": {
"last_modification_date": "",
"times_submitted": "",
"total_votes": {
"harmless": "",
"malicious": ""
},
"threat_names": [],
"redirection_chain": [],
"last_submission_date": "",
"last_http_response_content_length": "",
"last_http_response_headers": {},
"reputation": "",
"tags": [],
"last_analysis_date": "",
"first_submission_date": "",
"categories": {},
"last_http_response_content_sha256": "",
"last_http_response_code": "",
"last_final_url": "",
"trackers": {},
"url": "",
"title": "",
"last_analysis_stats": {
"harmless": "",
"malicious": "",
"suspicious": "",
"undetected": "",
"timeout": ""
},
"last_analysis_results": {},
"html_meta": {
"description": [],
"viewport": []
},
"outgoing_links": []
},
"type": "",
"id": "",
"links": {
"self": ""
}
}
operation: Get Analysis Details
Input parameters
| Parameter |
Description |
| Type |
Select the type, either File or URL, whose analysis details you want to retrieve from VirusTotal. |
| Analysis ID |
Specify the ID of the File or URL analysis whose details you want to retrieve from VirusTotal. Note: To retrieve the analysis ID, you can use the "Submit File" or "Submit URL for scanning" operation. |
Output
The output contains the following populated JSON schema:
Output schema when you choose Type as File:
{
"meta": {
"file_info": {
"size": "",
"sha1": "",
"sha256": "",
"md5": ""
}
},
"data": {
"attributes": {
"date": "",
"status": "",
"stats": {
"harmless": "",
"type-unsupported": "",
"suspicious": "",
"confirmed-timeout": "",
"timeout": "",
"failure": "",
"malicious": "",
"undetected": ""
},
"results": {}
},
"type": "",
"id": "",
"links": {
"item": "",
"self": ""
}
}
}
Output schema when you choose Type as URL:
{
"meta": {
"url_info": {
"url": "",
"id": ""
}
},
"data": {
"attributes": {
"date": "",
"status": "",
"stats": {
"harmless": "",
"malicious": "",
"suspicious": "",
"undetected": "",
"timeout": ""
},
"results": {}
},
"type": "",
"id": "",
"links": {
"item": "",
"self": ""
}
}
}
operation: Custom API Endpoint
Input parameters
| Parameter |
Description |
| API Endpoint |
Specify the API Endpoint for VirusTotal that can start with /api/v3/ or https://virustotal.com/api/v3/, to make the API call. |
| HTTP method |
Select the HTTP method to use for the API call. You can choose between GET or POST. |
| Request Body |
(Optional) Specify the GET or POST request body to send with the API call request. |
Output
The output contains a non-dictionary value.
Included playbooks
The Sample - VirusTotal - 3.1.2 playbook collection comes bundled with the VirusTotal connector. These playbooks contain steps using which you can perform all supported actions. You can see the bundled playbooks in the Automation > Playbooks section in FortiSOAR™ after importing the VirusTotal connector.
- Custom API Endpoint
- Domain > VirusTotal > Enrichment
- File > VirusTotal > Enrichment
- File Hash > VirusTotal > Enrichment
- Get Analysis Details
- Get Domain Reputation
- Get File Reputation
- Get IP Reputation
- Get URL Reputation
- Get Widget HTML Content
- Get Widget Rendering URL
- IP Address > VirusTotal > Enrichment
- Submit File
- Submit URL for scanning
- URL > VirusTotal > Enrichment
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection since the sample playbook collection gets deleted during the connector upgrade and delete.
Pluggable Enrichment
The Sample - VirusTotal - 3.1.2 playbook collection contains pluggable enrichment playbooks that are used to provide verdicts for indicator types IP Address, File Hash, URL, Domain, and File. The pluggable enrichment playbooks are in the format: indicatorType > VirusTotal > Enrichment. For example, IP > VirusTotal > Enrichment.
The Configuration step in all the pluggable enrichment playbooks contains variables that have default values for calculating the Verdict for various indicator types.
NOTE: Create a global variable virus_total_upload_file to manage the upload file operation performed by the File > VirusTotal > Enrichment playbook. The value true uploads the file to VirusTotal; false skips the upload.
Default variables for all supported indicator types
The VirusTotal integration API response returns the verdict, cti_score, and enrichment_summary and other variables as listed in the following table:
| Variable Name |
Description |
Return Value |
verdict |
This connector returns a high-reliability value called verdict. Use this verdict to find the reputation of the various types of indicators. |
if the value in last_analysis_stats.malicious > 0 then the verdict returned is Malicious
if the value in last_analysis_stats.suspicious > 0 then the verdict returned is Suspicious
if the value in last_analysis_stats.harmless > 0 then the verdict returned is Good
For any other value, return the verdict as No Reputation Available
|
cti_name |
The name of the connector is called the CTI (Cyber Threat Intelligence) name |
VirusTotal |
cti_score |
The verdict value returned by the integration API. |
Returns the value contained in last_analysis_stats.malicious
Returns the value in last_analysis_stats.suspicious if last_analysis_stats.malicious is empty
Returns 0 if both are empty.
|
source_data |
The source_data response returned by the integration API. |
A JSON response object containing the source data of the threat intelligence integration. |
field_mapping |
The mapping of the FortiSOAR Indicator module fields with the VirusTotal Intelligence response fields. |
A JSON response object containing the field mapping of the threat intelligence integration. |
enrichment_summary |
The contents that are added, in the HTML format, in the Description field of the specified FortiSOAR indicator record. |
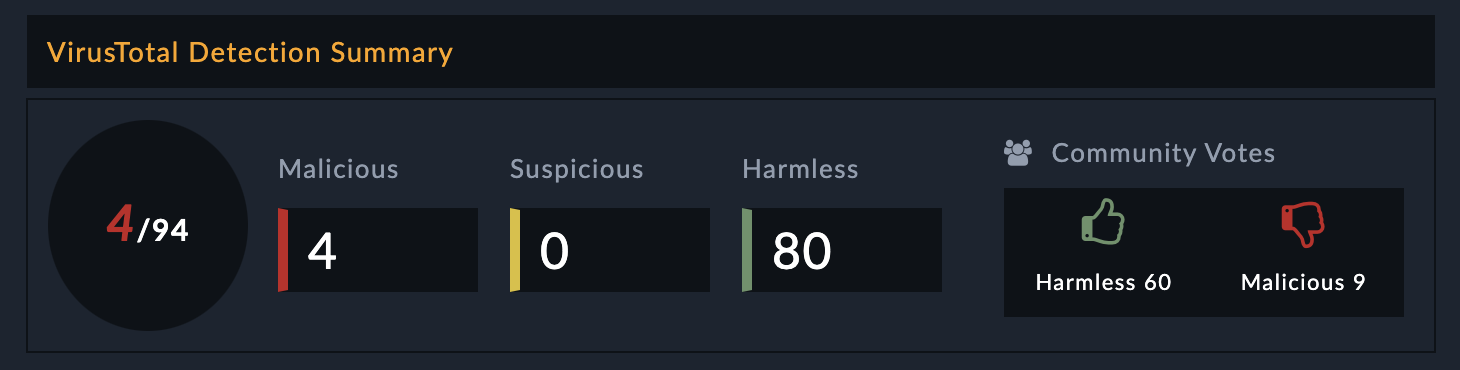
The following values are returned in the HTML format:
- Malicious
- Suspicious
- Harmless
- Community Votes
The following image displays a sample of the populated Description field in a FortiSOAR indicator record:
 |






