Endpoints
Domain name
List the domains to protect. The protection policy configured for this application applies to all the domains.
- You can add up to 10 domains. They should belong to the same root domain, such as www.example.com and mail.example.com.
- Wildcard is supported except the first entry in the list. Make sure that the domain name entries do not overlap, for example, “www.example.com” can't be added together with “*.example.com” . The wildcard only matches with the string within the same domain level, for example, "a.example.com" matches with “*.example.com”, while "a.a.example.com" doesn't.
- Once the application is onboarded, you are not allowed to change the first domain. Highly recommend to use root domain for the first domain, e.g. example.com or www.example.com.
Traffic Type
Select HTTP, HTTPS, HTTP/2
| HTTP |
|
| HTTPS |
If HTTPS is allowed, you will be required to configure the Local Certificate and SSL/TLS settings. Notes:
|
FortiWeb Cloud uses the following ports for HTTP and HTTPS services. These ports are open on FortiWeb Cloud scrubbing center clusters. There won't be security concerns because if the port is not set as the service port for your application, any request to this port for the application will be rejected.
-
HTTP: 80, 81, 3881, 3883, 8000, 8014, 8080, 8087, 8888, 9003, 9013, 9080, 9091, 9092, and 9219
-
HTTPS: 443, 444, 2087, 4333, 4334, 4430, 4466, 4993, 5001, 5454, 7003, 7443, 7741, 8012, 8076, 8078, 8081, 8086, 8088, 8090, 8092, 8093, 8094, 8095, 8096, 8097, 8098, 8099, 8181, 8282, 8443, 8585, 8723, 8787, 8866, 9052, 9090, 9093, 9440, and 52233
If the HTTP and HTTPS port number you want to use is not in the list, please contact Fortinet Support or your sales engineer to customize the port number. Notice not all non-standard ports can be used, and HTTP and HTTPS services must use different ports.
SSL Certificate
The SSL certificate is used to encrypt the HTTPS connections between users and FortiWeb Cloud. Without a valid certificate, users will see a certificate invalid warning when they visit your application.
By default, FortiWeb Cloud automatically retrieves SSL certificates from the Certificate Authority Let's Encrypt. If it fails, or if you would like to use your own certificate, you can manually upload it to FortiWeb Cloud.
|
|
FortiWeb Cloud will not apply automatic certificate if your application uses AWS CloudFront service. |
Automatic Certificate
Before configuring Automatic Certificate, make sure:
- You must have changed your DNS record to the CNAME or A record shown in the last step of the ADD APPLICATION wizard.
- You must have enabled HTTP service and uses port 80 for it on the endpoint if you use HTTP Challenge, because the Certificate Authority sends HTTP requests to FortiWeb Cloud to validate the DNS CNAME record.
- You must add "letsencrypt.org" in the CAA value if you have configured a CAA record at your DNS service. For more information, search CAA in FAQs.
- You should not block requests from United States in IP Protection > Geo IP Block, otherwise FortiWeb Cloud can't retrieve certificates from Let's Encrypt.
- The server health check status should be OK. If not, you should first disable health check so that it won't interrupt certificate retrieval. After the certificate is successfully retrieved, you can go ahead enable health check and troubleshoot the server connection issue.
Selecting the Challenge Type:
Let's Encrypt sends challenges to validate that you control the domain names you have listed while onboarding the application.
You can select HTTP Challenge or DNS Challenge. Please note that DNS challenge will be used for the wildcard domains regardless which challenge type you have chosen.
- HTTP Challenge
To pass the challenge, you must change all the DNS entries for the domains you listed.
-
DNS Challenge
To pass the challenge, you need to create a new CNAME record for automatic certificate as well as change the DNS entries for the domains you listed. To avoid users encounter the "certificate invalid" error, you can first create the CNAME record (beginning with "_acme-challenge") to get the automatic certificate. After DNS status turns to OK, which means the certificate is successfully installed, you can then change the DNS records for your application's domains to direct the traffic to FortiWeb Cloud.
The challenge is handled automatically, but if you need to make some more complex configuration decisions, it’s useful to know more about them. See Challenge Types posted by Let's Encrypt.
Several minutes after the challenge is successful, FortiWeb Cloud obtains an SSL certificate on your behalf from Let’s Encrypt and installs it on your application. It will be used in HTTPS connections to encrypt or decrypt the traffic. If FortiWeb Cloud fails to retrieve the certificate, it will try again every 12 minutes on the 1st day, then once an hour on the 2nd and 3rd days. After that, it downgrades the frequency to once a day, until the certificate is successfully retrieved.
To retrieve the certificate immediately, click the Retrieve button beside Automatic Certificate to restore the interval count to the 1st day. FortiWeb Cloud will then retrieves certificate every 12 minutes, and so on.
Thirty days before your certificate expires, FortiWeb Cloud verifies again that your DNS
Custom Certificate
FortiWeb Cloud may fail to retrieve the certificate for some reasons, for example, the HTTP traffic is not allowed on the endpoints. An exclamation mark will appear beside the Automatic Certificate option indicating the certificate fails to be retrieved. 
In this case, or in case you would like to use your own certificate, you can import SNI certificates or intermediate certificates (optional).
- Select Custom Certificate on the Endpoints page.
- For SNI Certificate, click Import and copy the Private Key and Certificate values provided by your Certificate Authority.
FortiWeb Cloud automatically parses information of the SNI certificates including issuance, expiration, status, and certificate chain, and changes them to recognizable formats.
For status, when FortiWeb Cloud verifies the private key and certificate values are consistent, the status is OK; when FortiWeb Cloud verifies the certificate has expired, the status is Expired; when FortiWeb Cloud verifies the certificate is valid, while the certificate chain verification fails, the status is Invalid Chain.
FortiWeb Cloud requires you to import the private key and certificate in separate fields. If you use a PKCS#12 certificate, refer to this article to extract the key and certificate: https://www.ssl.com/how-to/export-certificates-private-key-from-pkcs12-file-with-openssl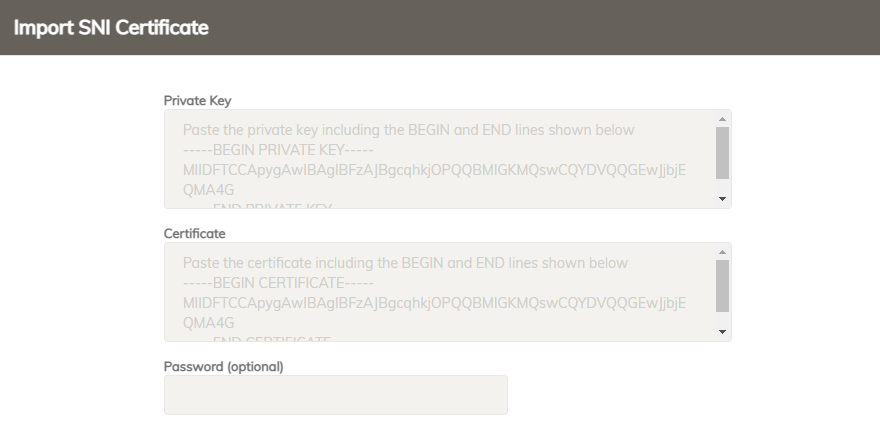
- For Intermediate Certificate (optional), click Import and copy the certificate value provided by your intermediate Certificate Authority.
FortiWeb Cloud automatically parses information of the intermediate certificates including issuance, and expiration, and changes them to recognizable formats. Also, FortiWeb Cloud verifies the status and certificate chain.
When an indeterminate certificate is successfully imported or deleted, FortiWeb Cloud reverifies the expiration and certificate chain.
You can import at most 32 SNI certificates and intermediate certificates respectively. Contact support team if you want to extend the limits.
SSL/TLS
SSL/TLS Versions: Select which versions of SSL or TLS protocols are allowed for the HTTPS connections between FortiWeb Cloud and the clients.
SSL/TLS Encryption Level: The HTTPS traffic is encrypted or decrypted with ciphers.
The SSL/TLS Encryption Level controls how many ciphers are supported and the settings provides the following options:
- Mozilla-Modern: For services with clients that support TLS 1.3 and don't need backward compatibility, Mozilla-Modern is the recommended configuration as it provides an extremely high level of security.
-
Mozilla-Intermediate: For services that don't need compatibility with legacy clients such as Windows XP or old versions of OpenSSL, Mozilla-Intermediate is the recommended configuration as it is highly secure and in the meanwhile compatible with nearly every client released in the last five (or more) years.
-
Mozilla-Old: For services accessed by very old clients or libraries, such as Internet Explorer 8 (Windows XP), Java 6, or OpenSSL 0.9.8. Mozilla-old is the recommended configuration as it is compatible with most of the clients.
-
Customized – Supports a customizable list of all ciphers.
For a complete list of the ciphers of each Encryption Level, see Supported cipher suites & protocol versions.
|
|
When HTTP/2 is enabled, only certain TLS 1.3 and TLS 1.2 ciphers will be supported for all SSL/TLS encryption levels. |
Redirect all HTTP traffic to HTTPS: Select to automatically redirect all HTTP requests to the HTTPS service with the same URL and parameters. Do not enable this option if you have only one origin server and want FortiWeb Cloud to communicate with the origin server over both HTTP and HTTPS protocols.
If you want to provide different content over HTTP and HTTPS protocols, Please refer to Network settings for applications serving different content over HTTP and HTTPS
HTTP Strict Transport Security (HSTS): Enable to combat MITM attacks on HTTP by injecting the RFC 6797 (http://tools.ietf.org/html/rfc6797) strict transport security header into the reply, such as: Strict-Transport-Security: max-age=31536000.
This header forces clients to use HTTPS for subsequent visits to this domain. If the certificate is invalid, the client’s web browser receives a fatal connection error and does not display a dialog that allows the user to override the certificate mismatch error and continue.
HSTS Max-age: Specify the time to live in seconds for the HSTS header. The HSTS enforcement will be lifted after the specified max-age. Subsequent visits will not be required to use HTTPS.
Secure flag for internal Cookie: Enable to add the secure flag to cookies, which forces browsers to return the cookie only when the request is for an HTTPS page. When enabled, only the HTTPS request contains cookie, while the HTTP is cookieless.
HTTP Only flag for internal Cookie: Enable to add the "HTTP Only" flag to internal cookies, which prevents client-side scripts from accessing the cookie.
Advanced Settings
Configure the following settings:
| HTTP/2 | Enable to accept HTTP/2 traffic. |
|
Client Certificate Authentication |
Enable it so that FortiWeb Cloud requires a client to provide a client certificate during the SSL handshake. When enabled, if a client doesn't provide a client certificate during the SSL handshake, FortiWeb Cloud won't accept the request.
|
| IPv6 | If IPv6 is enabled, both IPv4 and IPv6 are allowed to your application. If disabled, only IPv4 traffic is allowed. |
| Custom Block Page |
Select the block page that FortiWeb Cloud displays to your users. It contains the following messages:
The custom block page is configured in Global > System Settings > Custom Block Pages. |

