Introduction
This document provides reference architectures for configuring networks for small campuses, large campuses, small software-defined (SD) branches, medium SD-branches, and large SD-branches.
-
“Campus” covers a wide range of networks and locations, from multiple floors in an office tower to a university campus of a couple hundred acres. However, the Fortinet recommended architecture remains the same for this wide range. Generally speaking, a single location with 100 to 100,000 devices will fit this campus model.
-
An effective SD-branch design should consolidate WAN and LAN capabilities to simplify remote office infrastructure and optimize operations without introducing new risks.
The nature of a campus deployment is not just the large physical size of the network, but the greater complexity of who and what is using that network. As the network grows in size, security needs become more complex with more categories of end devices. Fortinet calls this network configuration the local area network (LAN) edge.
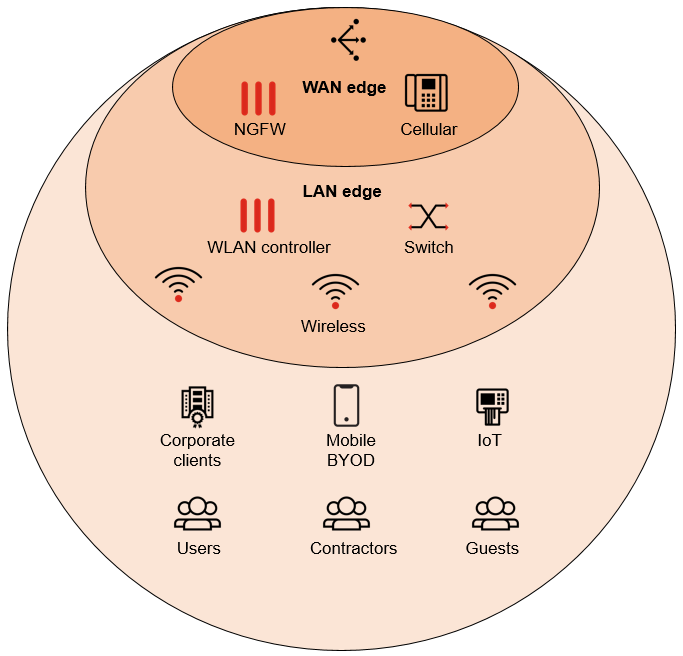
Physically, the LAN edge is just the access layer, but securing the access layer now has to account for a bewildering mix of devices: enterprise owned, end-user owned, guest users, known users, Internet of things (IoT) devices with no associated users, and so on. Unlike other vendors, Fortinet takes a security-first approach to wired LANs with the FortiSwitch line and wireless LANs (WLANs) for security-driven networking.
Fortinetʼs security-driven networking strategy tightly integrates an organizationʼs network infrastructure and security architecture, enabling the network to scale and change without compromising security. This next-generation approach is essential for effectively defending todayʼs highly dynamic environments—not only by providing consistent enforcement across todayʼs highly flexible perimeters, but by also weaving security deep into the network itself in a Security Fabric.
Intended audience
This guide is intended for network and security architects and engineers who are interested in deploying Fortinet’s FortiSwitch units in a new environment or in replacing their equipment in an existing environment. Readers are expected to have a firm understanding of networking and security concepts.
About this guide
This guide provides reference architectures for secure campuses and SD-branch network topologies. These reference architectures offer examples of the best way to configure your network for each use case. The Fortinet solutions in this guide make it easier to configure these challenging topologies.
This document is not intended to be a step-by-step configuration guide. Instead, it is meant to be the starting point in your network design, where you begin to draw out the architecture that will be used to meet your specific needs. For more information and documentation about the topics covered in this document, refer to the Fortinet Document Library at https://docs.fortinet.com.

