Multi-stage load balance
You can use a FortiSwitch unit to configure multi-stage load balancing on a set of FortiGate units. This capability allows you to scale security processing while maintaining a simple basic architecture. This configuration is commonly referred to a “firewall sandwich.”

Because the FortiGate unit provides session-aware analysis, the load distribution algorithm must be symmetric (traffic for a given session, in both directions, must all traverse the same FortiGate unit).
For larger scale deployment, the topology uses multiple layers of load distribution to allow for far larger numbers of FortiGate devices.
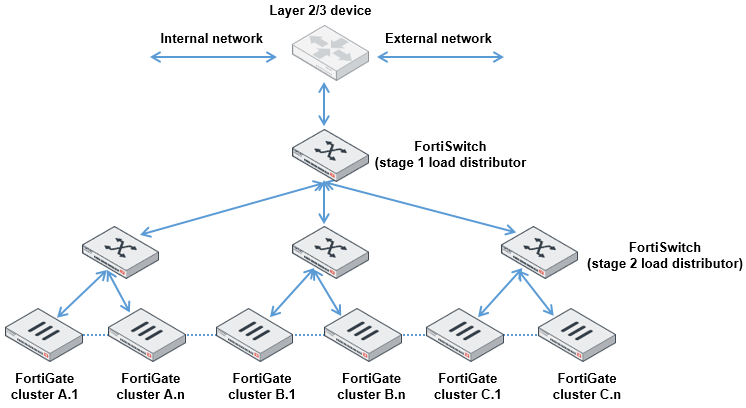
The hash at the first and second stages must be symmetric. The two stages must provide different hashing results.
Configuring the trunk ports
Use the following commands to configure the trunk members and set the port-selection criteria:
config switch trunk
edit <trunk name>
set description <description_string>
set members <ports>
set mode {fortinet-trunk | lacp-active | lacp-passive | static}
set port-selection-criteria src-dst-ip-xor16
end
end
Heartbeats
When in Fortinet-trunk mode, Heartbeat capability is enabled. Heartbeat messages monitor the status of FortiGate units. If one is unavailable, the FortiSwitch unit stops sending traffic to that FortiGate unit until the FortiGate unit becomes available.
If you enable hb-verify, each received heartbeat frame will be validated to match the signature (transmit-port plus switch serial number) and the following configured heartbeat parameters:
- hb-in-vlan
- hb-src-ip
- hb-dst-ip
- hb-src-upd-port
- hb-dst-udp-port
The destination MAC address of the heartbeat frame is set by default to 02:80:c2:00:00:02. You can change the value to any MAC address that is not a broadcast or multicast MAC address.
Configuring heartbeats
Configure the heartbeat fields using trunk configuration commands, as shown in this section. By default, all of the configurable values are set to zero, and hb-verify is disabled.
Set the mode to forti-hb and set the heartbeat loss limit to a value between 3 and 32.
The heartbeat will transmit at 1-second intervals on any link in the trunk that is up. This value is not configurable.
The heartbeat frame has configurable parameters for the layer-3 source and destination addresses and the layer-4 UDP ports. You must also specify the transmit and receive VLANs.
config switch trunk
edit hb-trunk
set mode fortinet-trunk
set members <port> [<port>] ... [<port>]
set hb-loss-limit <3-32>
set hb-out-vlan <int>
set hb-in-vlan <int>
set hb-src-ip <x.x.x.x>
set hb-dst-ip <x.x.x.x>
set hb-src-udp-port <int>
set hb-dst-udp-port <int>
set hb-verify [ enable | disable ]
end
Use the following command to configure the destination MAC address:
config switch global
set forti-trunk-dmac <mac address>
end
Example
The following example creates trunk tr1 with heartbeat capability:
config switch trunk
edit "tr1"
set mode fortinet-trunk
set members "port1" "port2"
set hb-out-vlan 300
set hb-in-vlan 500
set hb-src-ip 10.105.7.200
set hb-dst-ip 10.105.7.199
set hb-src-udp-port 12345
set hb-dst-udp-port 54321
set hb-verify enable
next
end

