About the connector
The CrowdStrike Falcon® platform is pioneering cloud-delivered endpoint protection. It both delivers and unifies IT Hygiene, next-generation antivirus, endpoint detection and response (EDR), managed threat hunting, and threat intelligence — all delivered via a single lightweight agent.
This document provides information about the CrowdStrike Falcon connector, which facilitates automated interactions with CrowdStrike Falcon using FortiSOAR™ playbooks. Add the CrowdStrike Falcon connector as a step in FortiSOAR™ playbooks and perform automated investigative operations on endpoints and manage IOC for CrowdStrike Falcon, operations include creating an IOC on CrowdStrike Falcon and hunting a file or domain on CrowdStrike Falcon using a specified filehash or a specific domain.
You can use FortiSOAR™'s Data Ingestion Wizard to easily ingest data into FortiSOAR™ by pulling detections from CrowdStrike Falcon. For more information, see the Data Ingestion Support section.
Version information
Connector Version: 2.3.0
Authored By: Fortinet
Certified: No
Release Notes for version 2.3.0
Following enhancements have been made to the CrowdStrike Falcon Connector in version 2.3.0:
- The API endpoints, parameters and output schema for following actions are updated:
- Create IOC
- Get IOC Details
- Update IOC
- Delete IOC
- Get IOCs
- The following actions now support pagination parameters:
- Hunt File
- Hunt Domain
- Detection Search
NOTE: If the previous version of the CrowdStrike Falcon connector had data ingestion configured, it is possible that the data ingestion playbooks may fail. Perform one of the following actions to fix this issue:
- Edit the playbook > CrowdStrike Falcon > Fetch.
- Edit the connector step Fetch Detections from CrowdStrike Falcon.
- Specify a value in the Number of Records to Return parameter.
OR
- Reconfigure Data Ingestion after upgrading the connector.
Installing the connector
Use the Content Hub to install the connector. For the detailed procedure to install a connector, click here.
You can also use the following yum command as a root user to install connectors from an SSH session:
yum install cyops-connector-crowd-strike-falcon
Prerequisites to configuring the connector
- You must have the URL of a CrowdStrike Falcon server to which you will connect and perform automated operations and the Client ID and Secret used to access the CrowdStrike Falcon APIs and perform automated operations.
- The FortiSOAR™ server should have outbound connectivity to port 443 on the CrowdStrike Falcon server.
Minimum Permissions Required
Configuring the connector
For the procedure to configure a connector, click here.
Configuration parameters
In FortiSOAR™, on the Content Hub (or Connector Store) page, click the Manage tab, and then click the CrowdStrike Falcon connector card. On the connector popup, click the Configurations tab to enter the required configuration details:
| Parameter |
Description |
| Server URL |
The URL of the CrowdStrike Falcon server to which you will connect and perform the automated operations. |
| Client ID |
The Client ID used to access the CrowdStrike Falcon APIs and perform automated operations. |
| Client Secret |
The Client Secret used to access the CrowdStrike Falcon APIs and perform the automated operations. |
| Verify SSL |
Specifies whether the SSL certificate for the server is to be verified or not.
By default, this option is set as True. |
Actions supported by the connector
The following automated operations can be included in playbooks, and you can also use the annotations to access operations from FortiSOAR™:
| Function |
Description |
Annotation and Category |
| Create IOC |
Creates an indicator on CrowdStrike Falcon based on the IOC type, value, and other input parameters you have specified. |
create_ioc
Investigation |
| Get IOCs |
Retrieves a list of all IOCs or specific IOCs based on the input parameters you have specified. |
get_iocs
Investigation |
| Get IOC Details |
Retrieves details of a specific IOC from CrowdStrike Falcon based on the IOC ID you have specified. |
get_ioc
Investigation |
| Update IOC |
Updates an indicator on CrowdStrike Falcon based on the input parameters you have specified. |
update_ioc
Investigation |
| Delete IOC |
Deletes an indicator on CrowdStrike Falcon based on the IOC IDs you have specified. |
delete_ioc
Remediation |
| Hunt File |
Hunts a file on CrowdStrike Falcon using the filehash type and value you have specified. |
hunt_file
Investigation |
| Hunt Domain |
Hunts a domain on CrowdStrike Falcon using the domain value you have specified. This operation retrieves a list of device IDs from CrowdStrike Falcon on which the domain was observed. |
hunt_domain
Investigation |
| Get Processes Related to IOC |
Retrieves a list of processes from CrowdStrike Falcon which are associated with the specified IOC on a given device based on the IOC type and value, device ID, and other input parameters you have specified. |
get_processes
Investigation |
| Get Process Details |
Retrieves details of a specific process from CrowdStrike Falcon, based on the process ID you have specified. |
search_process
Investigation |
| Get Device Details |
Retrieves details of a specific device from CrowdStrike Falcon, based on the device ID you have specified. |
search_endpoint
Investigation |
| Get Endpoint List |
Retrieves a list of all the endpoints or specific endpoints based on the input parameters you have specified configured on a device on CrowdStrike Falcon. |
get_endpoints
Investigation |
| Get Detection Details |
Retrieves details of a specific detection from CrowdStrike Falcon, based on the detection IDs you have specified. |
get_detection
Investigation |
| Contain the Host |
Prevents a potentially compromised host from communicating across the network that contains the host based on the device IDs you have specified. |
list_endpoint
Investigation |
| Remove Containment |
Removes the containment on a host that has been contained and returns its network communications to normal based on the device IDs you have specified. |
list_endpoint
Investigation |
| Detection Search |
Retrieves a list of all detection IDs or specific detection IDs based on the input parameters you have specified configured on a device on CrowdStrike Falcon. |
get_detection
Investigation |
| Detection Aggregates |
Retrieves a count of detections by a query from CrowdStrike Falcon based on the aggregate query name and type, the field used to compute the aggregation, and other input parameters you have specified. |
detection_aggregates
Investigation |
| Update Detection |
Updates specific detections in CrowdStrike Falcon, based on the detection IDs and other input parameters you have specified. |
set_state
Investigation |
| Search Incidents |
Searches for incidents in CrowdStrike Falcon based on the FQL filter, sorting, and pagination details you have specified. |
incidents_query
Investigation |
| Get Incident Details |
Retrieves details for incidents from CrowdStrike Falcon based on the incident IDs you have specified. |
incidents_get_details
Investigation |
| Get Incidents Crowdstrike Score |
Returns entity (incident) data by querying the complete CrowdStrike Score environment based on the timestamp and CrowdStrike score you have specified. |
get_crowdstrikescore_incident
Investigation |
| Update Incidents Status |
Updates specific incidents in CrowdStrike Falcon, based on the incidents IDs and status you have specified. |
update_incidents
Investigation |
| Run Admin Command |
Executes admin commands on a specific device in CrowdStrike Falcon based on the device ID, commands, and optionally command parameters you have specified. |
run_cmd
Investigation |
| Get Admin Command Result |
Retrieves the result of the status of the admin command executed on a specific device from CrowdStrike Falcon Real-Time Response (RTR) based on the cloud request ID and sequence ID you have specified. |
get_result
Investigation |
| Download Session File List |
Retrieves the list of the session files available for download using CrowdStrike Falcon RTR based on the device ID you have specified. |
list_files
Investigation |
| Download Session File |
Downloads a specific session file using CrowdStrike Falcon RTR based on the device ID, the file's SHA256 values, and other input parameters you have specified. |
download_file
Investigation |
| Get Scripts List |
Retrieves a list of PowerShell scripts available for the "runscript" command from CrowdStrike Falcon. These scripts can then be run on devices using CrowdStrike Falcon RTR. |
list_files
Investigation |
| Get Scripts Details by IDs |
Retrieves the PowerShell scripts available for the "runscript" command from CrowdStrike Falcon based on the script ID you have specified. These scripts can then be run on devices using CrowdStrike Falcon RTR. |
get_file
Investigation |
| Get Executable List |
Retrieves a list of Executable available for the "runscript" command from CrowdStrike Falcon. These executables can then be run on devices using CrowdStrike Falcon RTR. |
list_executable
Investigation |
| Get Executables Details by IDs |
Retrieves the executables available for the "runscript" command from CrowdStrike Falcon based on the executable file ID you have specified. These executables can then be run on devices using CrowdStrike Falcon RTR. |
get_file
Investigation |
| Get User ID |
Retrieves the user ID from CrowdStrike Falcon based on the username you have specified. |
get_uid
Investigation |
| Get User Details |
Retrieves the details of a specific user from CrowdStrike Falcon based on the user ID you have specified. |
get_user_details
Investigation |
| Get Usernames List |
Retrieves a list of usernames (usually an email address) for all users in your customer account from CrowdStrike Falcon. |
get_username_list
Investigation |
| Get User IDs List |
Retrieves a list of all user IDs in your customer account from CrowdStrike Falcon. |
get_user_id_list
Investigation |
operation: Create IOC
Input parameters
| Parameter |
Description |
| Retro Detects |
Select this option, i.e. set it to true, to submit retro detects on CrowdStrike Falcon. |
| Ignore Warnings |
Select this option, i.e. set it to true, to ignore warnings and add all IOCs. By default, this is set as true. |
| Comment |
Specify a comment to be associated with the indicator. |
| Number Of Indicators To Create |
Select from the following options whether to submit a single IOC or multiple IOCs to create on CrowdStrike Falcon.
- Create Single Indicator: Specify the following fields when submitting a single indicator to CrowdStrike Falcon:
- Action: Specify the action to be associated with the indicator.
- Apply Globally: Specify whether it should be applied globally or not, by default this is set as true
- Indicator Description: (Optional) Description of the indicator that you want to create on CrowdStrike Falcon.
- Expiration: Specify the expiration of the indicator.
- Host Groups: Specify the host groups. You can specify multiple host groups as comma-separated values.
- Metadata: Specify the file name which you want to associate with the indicator.
- Mobile Action: Specify the mobile action which you want to associate with the indicator.
- Platforms: Specify the platforms.You can specify multiple platforms as comma-separated values.
- Severity: Specify the severity to be associated with indicator.
- Indicator Source: (Optional) Source of origination of the indicator that you want to create on CrowdStrike Falcon. This can be used for tracking where this indicator was defined.
- Tags: Specify the tags.You can specify multiple tags as comma-separated values.
- IOC Type: Specify the type of indicator that you want to create on CrowdStrike Falcon.Valid types include: IPv4, IPv6, Domain, MD5, SHA1, and SHA256.
- IOC Value: String representation of the indicator that you want to create on CrowdStrike Falcon.The value that you specify will be based on the IOC Type you have chosen.
- Create Multiple Indicator
- Indicators: Specify the list of indicators, as comma-separated values, to create on CrowdStrike Falcon.
|
Output
The output contains the following populated JSON schema:
{
"meta": {
"query_time": "",
"pagination": {
"limit": "",
"total": ""
},
"powered_by": "",
"trace_id": ""
},
"errors": "",
"resources": [
{
"id": "",
"type": "",
"value": "",
"action": "",
"mobile_action": "",
"severity": "",
"description": "",
"metadata": {
"filename": ""
},
"platforms": [],
"tags": [],
"expiration": "",
"expired": "",
"deleted": "",
"applied_globally": "",
"from_parent": "",
"created_on": "",
"created_by": "",
"modified_on": "",
"modified_by": ""
}
]
}
operation: Get IOCs
Input parameters
| Parameter |
Description |
| Query String |
Specify the filter expression to use to filter the results. |
| Number of Records to Return |
Select whether you want this operation to Fetch Limited Records or Fetch All Records.
- Fetch Limited Records: Specify the following additional parameters:
- Limit: Specify the maximum number of results that this operation should return.
- Offset: Specify a
0-based index of the page that this operation should return.
- Fetch All Records: Select this option to fetch all records.
|
| Sort Expression |
Specify the sort expression to sort the results. |
| From Parent |
Select whether to return only indicators for the request customer or its MSSP parents |
Output
The output contains the following populated JSON schema:
{
"ioc_count": "",
"ioc_ids": ""
}
operation: Get IOC Details
Input parameters
| Parameter |
Description |
| IOC ID |
Specify a comma-separated list of IOC IDs whose details you want to retrieve from CrowdStrike Falcon. |
Output
The output contains the following populated JSON schema:
{
"ioc_details": {
"meta": {
"query_time": "",
"pagination": {
"limit": "",
"total": ""
},
"powered_by": "",
"trace_id": ""
},
"errors": "",
"resources": [
{
"id": "",
"type": "",
"value": "",
"source": "",
"action": "",
"mobile_action": "",
"severity": "",
"description": "",
"platforms": [],
"expired": "",
"deleted": "",
"applied_globally": "",
"from_parent": "",
"created_on": "",
"created_by": "",
"modified_on": "",
"modified_by": ""
}
]
}
}
operation: Update IOC
Input parameters
| Parameter |
Description |
| Retro Detects |
Select this option, i.e. set it to true, to submit retro detects on CrowdStrike Falcon. |
| Ignore Warnings |
Select this options, i.e. set it to true to ignore warnings and add all IOCs. By default this is set as true. |
| Comment |
Specify the comment to be associated with the indicator. |
| Number Of Indicators To Update |
Select from the following options whether to update a single IOC or update IOCs in Bulk on CrowdStrike Falcon.
- Update Single Indicator: Specify the following fields when submitting a single indicator to CrowdStrike Falcon:
- Action: Specify the action to be associated with the indicator.
- Apply Globally: Specify whether it should be applied globally or not, by default this is set as true
- Indicator Description: (Optional) Description of the indicator that you want to update on CrowdStrike Falcon.
- Expiration: Specify the expiration of the indicator.
- Host Groups: Specify the host groups. You can specify multiple host groups as comma-separated values.
- Metadata: Specify the file name which you want to associate with the indicator.
- Indicator ID: Specify the ID of the indicator to update on CrowdStrike Falcon.
- Mobile Action: Specify the mobile action which you want to associate with the indicator.
- Platforms: Specify the platforms.You can specify multiple platforms as comma-separated values.
- Severity: Specify the severity to be associated with indicator.
- Indicator Source: (Optional) Source of origination of the indicator that you want to update on CrowdStrike Falcon. This can be used for tracking where this indicator was defined.
- Tags: Specify the tags.You can specify multiple tags as comma-separated values.
- Create Multiple Indicator
- Indicators: Specify the list of indicators, as comma-separated values, to update on CrowdStrike Falcon.
- Bulk Update: Specify the following fields when submitting indicators in bulk to CrowdStrike Falcon:
- Action: Specify the action to be associated with the indicator.
- Applied Globally: Specify whether it should be applied globally or not. By default this is set as true
- Indicator Description: Specify the description of the indicator.
- Expiration: Specify the expiration of the indicator.
- Query String: Specify the filter expression that should be used to limit the results.
- From Parent: Specify whether to return only indicators for the request customer or its MSSP parents
- Host Groups: Specify the host groups. You can specify multiple host groups as comma-separated values.
- Metadata: Specify the file name which you want to associate with the indicator.
- Mobile Action: Specify the mobile action which you want to associate with the indicator.
- Platforms: Specify the platforms.You can specify multiple platforms as comma-separated values.
- Severity: Specify the severity to be associated with indicator.
- Indicator Source: Specify the source to be associated with indicator.
- Tags: Specify the tags.You can specify multiple tags as comma-separated values.
|
Output
The output contains the following populated JSON schema:
{
"status": "",
"result": ""
}
operation: Delete IOC
Input parameters
| Parameter |
Description |
| Search IOC By |
Select the method using which to search IOCs on CrowdStrike Falcon. You can choose from the following options:
- Filter Query: Specify the FQL expression, to delete Indicators in bulk, in the Query String field.
- IDs: Specify comma-separated list of IOC IDs, to delete from CrowdStrike Falcon, in the IOC ID field.
|
| Comment |
Specify a reason for deleting these indicators from CrowdStrike Falcon. |
| From Parent |
Specify whether to return only indicators for the request customer or its MSSP parents |
Output
The output contains the following populated JSON schema:
{
"status": "",
"result": {
"meta": {
"query_time": "",
"powered_by": "",
"trace_id": ""
},
"errors": "null",
"resources": []
}
}
operation: Hunt File
Input parameters
| Parameter |
Description |
| Filehash Type |
Specify the type of filehash that you want to hunt for on CrowdStrike Falcon. |
| Filehash Value |
Specify the Value of filehash that you want to hunt for on CrowdStrike Falcon. |
| Get Device Count Only |
Select this parameter, i.e., set it to True, to get the response containing only the number of devices found for that Filehash and value on CrowdStrike Falcon. For example,
"device_count": 13
Clear this parameter, i.e., set it to False, to get the response containing the list of device IDs found for that Filehash and value. For example, "resources": [
"1081290fbf104a1465cc0c91ca4ebe36",
"739e412d9ff341a549a75e5c8107b0f3"]
By default, this parameter is cleared, i.e., set as False. |
| Number of Records to Return |
Select whether you want this operation to Fetch Limited Records or Fetch All Records.
- Fetch Limited Records: Specify the following additional parameters:
- Number Of Hosts To Fetch: (Optional) Specify the maximum number of hosts that this operation should return.
- Offset: Specify a
0-based index of the page that this operation should return.
- Fetch All Records: Select this option to fetch all records.
|
Output
The output contains the following populated JSON schema:
{
"device_count": ""
}
operation: Hunt Domain
Input parameters
| Parameter |
Description |
| Domain |
Specify the value of the domain that you want to hunt for on CrowdStrike Falcon. |
| Get Device Count Only |
Select this parameter, i.e., set it to True, then the response will contain only the number of devices found for that domain on CrowdStrike Falcon.
If you clear this parameter, i.e., set it to False, then the response contains the list of device IDs found for that domain on CrowdStrike Falcon.
By default, this parameter is cleared, i.e., set as False. |
| Number of Records to Return |
Select whether you want this operation to Fetch Limited Records or Fetch All Records.
- Fetch Limited Records: Specify the following additional parameters:
- Number Of Hosts To Fetch: (Optional) Specify the maximum number of hosts that this operation should return.
- Offset: Specify a
0-based index of the page that this operation should return.
- Fetch All Records: Select this option to fetch all records.
|
Output
The output contains the following populated JSON schema:
{
"device_count": ""
}
operation: Get Processes Related to IOC
Input parameters
| Parameter |
Description |
| IOC Type |
Specify the type of indicator whose associated processes you want to retrieve from CrowdStrike Falcon.
Valid types include: IPv4, IPv6, Domain, MD5, SHA1, and SHA256. |
| IOC Value |
Specify the value of the indicator whose associated processes you want to retrieve from CrowdStrike Falcon.
The value that you specify is based on the IOC Type you have chosen. |
| Device ID |
Specify the ID of the device against which you want to check for IOCs and associated processes on CrowdStrike Falcon. |
| Record Count |
(Optional) Specify the number of items to be returned in a single request.
NOTE: You can specify the minimum number as 1 and the maximum number as 500. |
| Offset |
(Optional) Specify the index of the first item that this operation should return.
This allows you to use a pagination token returned by the API to paginate a set of results and allows you to resume pagination without retrieving the already encountered items. |
Output
The output contains the following populated JSON schema:
{
"process_ids": [],
"process_count": ""
}
operation: Get Process Details
Input parameters
| Parameter |
Description |
| Process ID |
Specify the ID of the process whose details you want to retrieve from CrowdStrike Falcon.
This parameter allows you to send multiple IDs to the endpoint to allow for more efficient multi-get type operations. |
Output
The output contains the following populated JSON schema:
{
"process_details": {
"meta": {
"query_time": "",
"trace_id": ""
},
"errors": [],
"resources": [
{
"device_id": "",
"stop_timestamp": "",
"process_id_local": "",
"file_name": "",
"process_id": "",
"start_timestamp_raw": "",
"command_line": "",
"start_timestamp": "",
"stop_timestamp_raw": ""
}
]
}
}
operation: Get Device Details
Input parameters
| Parameter |
Description |
| Device ID |
Specify the ID of the device whose details you want to retrieve from CrowdStrike Falcon. |
Output
The output contains the following populated JSON schema:
{
"system_info": {
"meta": {
"trace_id": "",
"powered_by": "",
"query_time": ""
},
"resources": [
{
"agent_local_time": "",
"cid": "",
"device_id": "",
"config_id_platform": "",
"system_manufacturer": "",
"config_id_base": "",
"system_product_name": "",
"agent_load_flags": "",
"product_type": "",
"external_ip": "",
"os_version": "",
"platform_name": "",
"bios_manufacturer": "",
"bios_version": "",
"first_seen": "",
"policies": [
{
"applied_date": "",
"assigned_date": "",
"applied": "",
"policy_type": "",
"policy_id": "",
"settings_hash": ""
}
],
"platform_id": "",
"device_policies": {
"prevention": {
"applied_date": "",
"assigned_date": "",
"applied": "",
"policy_type": "",
"policy_id": "",
"settings_hash": ""
},
"sensor_update": {
"applied_date": "",
"assigned_date": "",
"applied": "",
"policy_type": "",
"policy_id": "",
"settings_hash": ""
}
},
"last_seen": "",
"product_type_desc": "",
"machine_domain": "",
"meta": {
"version": ""
},
"config_id_build": "",
"modified_timestamp": "",
"mac_address": "",
"agent_version": "",
"major_version": "",
"local_ip": "",
"hostname": "",
"status": "",
"site_name": "",
"minor_version": ""
}
],
"errors": []
}
}
operation: Get Endpoint List
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| Query String |
Specify the filter conditions based on which you want to filter the list of endpoints retrieved from CrowdStrike Falcon.
All parameters listed under Detection Search API > Parameters can be used as filters. |
| Offset |
Specify the index of the first item that this operation should return.
This allows you to use a pagination token returned by the API to paginate a set of results and allows you to resume pagination without retrieving the already encountered items. |
| Record Count |
Specify the number of items to be returned in a single request.
NOTE: You can specify the minimum number as 1 and the maximum number as 500. |
Output
The output contains the following populated JSON schema:
{
"list_of_endpoints": [],
"endpoint_count": ""
}
operation: Contain the Host
Input parameters
| Parameter |
Description |
| Device ID |
Specify the comma-separated device IDs that need to be quarantined from the network, i.e., the devices cannot communicate across the network. |
Output
The output contains the following populated JSON schema:
{
"resources": [
{
"path": "",
"id": ""
}
],
"errors": [],
"meta": {
"trace_id": "",
"query_time": "",
"powered_by": ""
}
}
operation: Remove Containment
Input parameters
| Parameter |
Description |
| Device ID |
Specify the comma-separated device IDs that need to be unquarantined from the network, i.e., the devices cannot communicate across the network. |
Output
The output contains the following populated JSON schema:
{
"resources": [
{
"path": "",
"id": ""
}
],
"errors": [],
"meta": {
"trace_id": "",
"query_time": "",
"powered_by": ""
}
}
operation: Get Detection Details
Input parameters
| Parameter |
Description |
| Detection ID |
Specify the comma-separated detection IDs or a list of detection IDs whose details you want to retrieve from CrowdStrike Falcon. |
Output
The output contains the following populated JSON schema:
{
"errors": [],
"meta": {
"powered_by": "",
"query_time": "",
"trace_id": ""
},
"resources": []
}
operation: Detection Search
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| Severity |
Specify the name used in the UI to determine the severity of the detection that you want to search on CrowdStrike Falcon. You can select from following options.
|
| Tactic |
Specify the tactic for detection filtration on CrowdStrike Falcon. |
| Technique |
Specify the technique for detection filtration on CrowdStrike Falcon. |
| Time |
Specify the time based on which you want to search for detections on CrowdStrike Falcon.
You can choose from the following values:
- Last Hour
- Last Day
- Last Week
- Last 30 days
- Last 90 days
|
| Status |
Specify the current status of the detection that you want to search on CrowdStrike Falcon. You can select from the following options.
- New
- In Progress
- True Positive
- False Positive
- Ignored
|
| Detection ID |
Specify the ID of the detection that you want to search on CrowdStrike Falcon.
This ID can be used in conjunction with other APIs, such as the Detection Details API, or the Resolve Detection API. |
| Confidence |
Specify the highest confidence value to capture when a detection has more than one associated behavior with varying confidence levels.
You can specify any integer between 1-100 in this parameter. |
| Sort By |
Specify the parameter to sort detection records by any of the following options:
- Date Updated
- Last Behavior Descending
- Last Behavior Ascending
/td> |
| Triggering File |
Specify the name of the file that has triggered the process. |
| Assigned to |
Specify the human-readable name of the user to whom the detection is currently assigned. |
| General Search |
Specify the full-text to search for detections across all metadata fields on CrowdStrike Falcon. |
| Query String |
Specify the filter conditions based on which you want to filter the list of detections retrieved from CrowdStrike Falcon.
All parameters listed under Detection Search API > Parameters can be used as filters. |
| Number of Records to Return |
Select whether you want this operation to Fetch Limited Records or Fetch All Records.
- Fetch Limited Records: Specify the following additional parameters:
- Record Count: Specify the maximum number of results that this operation should return.
NOTE: You can specify the minimum number as 1 and the maximum number as 500.
- Offset: Specify a
0-based index of the page that this operation should return.
- Fetch All Records: Select this option to fetch all records.
|
Output
The output contains the following populated JSON schema:
{
"errors": [],
"meta": {
"pagination": {
"total": "",
"limit": "",
"offset": ""
},
"powered_by": "",
"query_time": "",
"trace_id": ""
},
"resources": []
}
operation: Detection Aggregates
Input parameters
| Parameter |
Description |
| Name |
Specify the name of the aggregate query specified by the user.
The name parameter is used to identify the results returned to you. |
| Aggregate Type |
Specify the type of aggregation whose count you want to retrieve from CrowdStrike Falcon.
Valid values include: Date Histogram, Date Range, Terms, Cardinality, Max, and Min. |
| Field |
Specify the field on which you want to compute the aggregation of detections.
All parameters listed under Detection Search API > Parameters can be used as fields for computing aggregations. |
| Time Interval |
Specify the time interval for date histogram aggregations.
Valid values include: Year, Month, Week, Day, Hour, and Minute. |
| Query Filter String |
Specify the filter conditions based on which you want to filter the list of detections retrieved from CrowdStrike Falcon.
All parameters listed under Detection Search API > Parameters can be used as filters. |
| General Search |
Specify the full-text search for detections across all metadata fields on CrowdStrike Falcon. |
| Ranges |
Specify the ranges values as per the field that you have specified.
For example, if max_severity is used, ranges can look like [{"From": 0,"To": 70},{"From": 70,"To": 100}] |
| Date Ranges |
Specify the date_range aggregations.
For example, [{"from": "2016-05-28T09:00:31Z","to": "2016-05- 30T09:00:31Z"},{"from": "2016-06-01T09:00:31Z","to": "2016-06-10T09:00:31Z"}] |
| Missing |
Specify the value of the aggregation field missing from the object/document. In other words, the missing parameter defines how documents that are missing the value should be treated.
By default, they will be ignored, but it is also possible to treat them as if this parameter is given a value. |
| Min Doc Count |
Specify the value to get term buckets whose values are greater than or equal to the value specified. |
| Record Count |
Specify the number of term buckets to be returned in a single request.
Note: You can specify the minimum number as 1 and the maximum number as 500. |
| Sort By |
Specify the value based on which the sort detection aggregations are returned. |
| Sub Aggregates |
Specify nested aggregation. You can specify a maximum of 3 nested aggregations per request.
For example, "sub_aggregates" :[{"name": "max_first_behavior","type": "max","field": "first_behavior"}]" |
Output
The output contains the following populated JSON schema:
{
"errors": [],
"meta": {
"powered_by": "",
"query_time": "",
"trace_id": ""
},
"resources": []
}
operation: Update Detection
Input parameters
| Parameter |
Description |
| Detection ID |
Specify the IDs of the detections that you want to update in CrowdStrike Falcon.
Note: v2 of the CrowdStrike API, the CrowdStrike detection IDs are in the following format: ldt:[first field]:[second field] e.g. ldt:cf54bb61f92e4d3e75bf4f7c11fc8f74:4295536142 |
| Status |
Specify the status to which you want to transition the specific detections. You can choose from the following values: New, In Progress, True Positive, False Positive, Ignored, or Closed. |
| Assigned To |
Specify the email IDs of users to whom you want to assign the specific detections. For example, user@example.com |
| Comment |
Specify the comment to add detections that you want to update in CrowdStrike Falcon. Comments are displayed with the detection in Falcon and are usually added to provide context or notes. |
| Show in UI |
Select this option, i.e., set it to true to display the detections in the UI. |
Output
The output contains the following populated JSON schema:
{
"status": "",
"result": {
"meta": {
"writes": {
"resources_affected": ""
},
"query_time": "",
"trace_id": ""
}
}
}
operation: Search Incidents
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| Query String |
Specify the filter conditions to filter the list of incidents retrieved from CrowdStrike Falcon. |
| Sort By |
Specify the sort query to perform the sorting operation on the results. In the sort query, specify the property to sort the results, followed by a dot (.), and then followed by the sort direction, either asc or desc. |
| Record Count |
Specify the number of items to be returned in a single request.
Note: You can specify the minimum number as 1 and the maximum number as 500. |
| Offset |
Specify the index of the first item that this operation should return.
This allows you to use a pagination token returned by the API to paginate a set of results and allows you to resume pagination without retrieving the already encountered items. For example, if you specify 10 in this parameter, then the operation will start from the 10th record and return the list. |
Output
The output contains a non-dictionary value.
operation: Get Incident Details
Input parameters
| Parameter |
Description |
| Incident IDs |
Specify the comma-separated incident IDs whose details you want to retrieve from CrowdStrike Falcon. |
Output
The output contains the following populated JSON schema:
{
"resources": [
{
"visibility": "",
"assigned_to_name": "",
"cid": "",
"techniques": [],
"modified_timestamp": "",
"name": "",
"events_histogram": [
{
"timestamp_max": "",
"has_prevented": "",
"has_overwatch": "",
"has_detect": "",
"timestamp_min": "",
"count": ""
}
],
"objectives": [],
"assigned_to": "",
"incident_type": "",
"created": "",
"fine_score": "",
"status": "",
"description": "",
"tactics": [],
"start": "",
"lm_host_ids": [],
"incident_id": "",
"users": [],
"end": "",
"tags": [],
"hosts": [
{
"release_group": "",
"site_name": "",
"config_id_platform": "",
"bios_version": "",
"cid": "",
"external_ip": "",
"last_login_user": "",
"bios_manufacturer": "",
"product_type_desc": "",
"last_login_timestamp": "",
"modified_timestamp": "",
"product_type": "",
"status": "",
"groups": [],
"last_seen": "",
"agent_version": "",
"device_id": "",
"config_id_base": "",
"ou": [],
"local_ip": "",
"first_login_timestamp": "",
"agent_load_flags": "",
"minor_version": "",
"platform_name": "",
"machine_domain": "",
"mac_address": "",
"system_product_name": "",
"notes": [],
"config_id_build": "",
"agent_local_time": "",
"os_version": "",
"platform_id": "",
"hostname": "",
"system_manufacturer": "",
"first_login_user": "",
"first_seen": "",
"major_version": "",
"tags": []
}
],
"host_ids": [],
"state": "",
"lm_hosts_capped": ""
}
],
"errors": [
{
"code": "",
"id": "",
"message": ""
}
],
"meta": {
"trace_id": "",
"writes": {
"resources_affected": ""
},
"pagination": {
"total": "",
"offset": "",
"limit": ""
},
"query_time": "",
"powered_by": ""
}
}
operation: Get Incidents Crowdstrike Score
Input parameters
| Parameter |
Description |
| Timestamp |
Specify the timestamp of the CrowdStrike calculation score to retrieve information about the incidents. |
| CrowdStrike Score |
CrowdStrike value of the CrowdStrike Score to retrieve information about the incidents. |
Output
The output contains a non-dictionary value.
operation: Update Incidents Status
Input parameters
| Parameter |
Description |
| Incident IDs |
Specify the comma-separated incident IDs or list of incident IDs whose status you want to update in CrowdStrike Falcon. |
| Status |
Select the status to which you want to update the specified incidents. Valid status values include: New, In Progress, Ignored, or Closed. |
Output
The output contains the following populated JSON schema:
{
"result": ""
}
operation: Run Admin Command
Input parameters
| Parameter |
Description |
| Device ID |
Specify the ID of the device on which to execute the specified admin command using CrowdStrike Falcon Real-Time Response (RTR). |
| Command |
Specify the valid commands to execute on the specified device. |
| Command Argument |
(Optional) Specify the command arguments to add to the specified commands as additional parameters. |
| Queue Offline |
Select this option, i.e., set to true, if you want to run the command on a host that is offline. By default, this option is cleared, i.e, set to False. |
Output
The output contains a non-dictionary value.
operation: Get Admin Command Result
Input parameters
| Parameter |
Description |
| Cloud Request ID |
Specify the ID of the request that is returned when you run the admin command on a specific device. |
| Sequence ID |
Specify the ID of the sequence that is returned in the result content. |
Output
The output contains a non-dictionary value.
operation: Download Session File List
Input parameters
| Parameter |
Description |
| Device ID |
Specify the ID of the device whose associated session file list you want to download using CrowdStrike Falcon RTR. |
Output
The output contains a non-dictionary value.
operation: Download Session File
Input parameters
| Parameter |
Description |
| Device ID |
Specify the ID of the device whose associated session file you want to download using CrowdStrike Falcon RTR. |
| File's SHA256 Value |
Specify the SHA256 value of the file that you want to download. |
| Download File Name |
Specify the name to be given to the downloaded file. The filename specified here will also be used to upload the file to the FortiSOAR™ Attachments module. |
| Additional Filter Parameters |
(Optional) Specify the additional filter parameters to search for the session file. |
Output
The output contains a non-dictionary value.
operation: Get Scripts List
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
Input parameters
| Parameter |
Description |
| Filter |
Specify the FQL query to filter PowerShell scripts. Based on the filter, this operation retrieves a list of PowerShell scripts from CrowdStrike Falcon. |
| Offset |
Specify the index of the first item that this operation should return.
This allows you to use a pagination token returned by the API to paginate a set of results and allows you to resume pagination without retrieving the already encountered items.
For example, if you specify 10 in this parameter, then the operation will start from the 10th record, then and return the list. |
| Limit |
(Optional) Specify the number of results to be returned in a single request.
|
| Sort By |
Specify the sort query to perform the sorting operation over the results. In the sort query, specify the property to sort the results, followed by a dot (.), and then followed by the sort direction, either asc or desc. |
Output
The output contains a non-dictionary value.
operation: Get Scripts Details by IDs
Input parameters
| Parameter |
Description |
| Script File IDs |
Specify the ID of the script file whose details you want to retrieve from CrowdStrike Falcon and which you want to run using the runscript command from CrowdStrike Falcon RTR. |
Output
The output contains a non-dictionary value.
operation: Get Executable List
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
Input parameters
| Parameter |
Description |
| Filter |
Specify the FQL query to filter Executable scripts. Based on the filter, this operation retrieves a list of Executable scripts from CrowdStrike Falcon. |
| Offset |
Specify the index of the first item that this operation should return.
This allows you to use a pagination token returned by the API to paginate a set of results and allows you to resume pagination without retrieving the already encountered items.
For example, if you specify 10 in this parameter, then the operation will start from the 10th record, then and return the list. |
| Limit |
Specify the number of results to be returned in a single request. |
| Sort By |
Sort query that is used to perform the sorting operation over the result. In the sort query, specify the property to sort the results, followed by a dot (.), and then followed by the sort direction, either asc or desc. |
Output
The output contains a non-dictionary value.
operation: Get Executables Details by IDs
Input parameters
| Parameter |
Description |
| Executable File IDs |
Specify the ID of the executable files whose details you want to retrieve from CrowdStrike Falcon and which you want to run using the runscript command from CrowdStrike Falcon RTR. |
The output contains a non-dictionary value.
operation: Get User ID
Input parameters
| Parameter |
Description |
| Username |
Specify the username whose user ID you want to retrieve from CrowdStrike Falcon. This is usually the user's email address; however, this could vary based on your configuration. For example, test@example.com |
Output
The output contains the following populated JSON schema:
{
"errors": [
{
"code": "",
"id": "",
"message": ""
}
],
"meta": {
"pagination": {
"limit": "",
"offset": "",
"total": ""
},
"powered_by": "",
"query_time": "",
"trace_id": "",
"writes": {
"resources_affected": ""
}
},
"resources": []
}
operation: Get User Details
Input parameters
| Parameter |
Description |
| User ID |
Specify the ID of the user whose details you want to retrieve from CrowdStrike Falcon. |
Output
The output contains the following populated JSON schema:
{
"errors": [
{
"code": "",
"id": "",
"message": ""
}
],
"meta": {
"pagination": {
"limit": "",
"offset": "",
"total": ""
},
"powered_by": "",
"query_time": "",
"trace_id": "",
"writes": {
"resources_affected": ""
}
},
"resources": [
{
"customer": "",
"firstName": "",
"lastName": "",
"uid": "",
"uuid": ""
}
]
}
operation: Get Usernames List
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"errors": [
{
"code": "",
"id": "",
"message": ""
}
],
"meta": {
"pagination": {
"limit": "",
"offset": "",
"total": ""
},
"powered_by": "",
"query_time": "",
"trace_id": "",
"writes": {
"resources_affected": ""
}
},
"resources": []
}
operation: Get User IDs List
Input parameters
None.
Output
The output contains the following populated JSON schema:
{
"errors": [
{
"code": "",
"id": "",
"message": ""
}
],
"meta": {
"pagination": {
"limit": "",
"offset": "",
"total": ""
},
"powered_by": "",
"query_time": "",
"trace_id": "",
"writes": {
"resources_affected": ""
}
},
"resources": []
}
Included playbooks
The Sample - CrowdStrike Falcon - 2.3.0 playbook collection comes bundled with the CrowdStrike Falcon connector. These playbooks contain steps using which you can perform all supported actions. You can see bundled playbooks in the Automation > Playbooks section in FortiSOAR™ after importing the CrowdStrike Falcon connector.
- > Crowdstrike Falcon > Fetch and Create
- Contain the Host
- Create IOC
- CrowdStrike Falcon > Ingest
- Delete IOC
- Detection Aggregates
- Detection Search
- Download Session File
- Download Session File List
- Get Admin Command Result
- Get Detection Details
- Get Device Details
- Get Endpoint List
- Get Executable List
- Get Executables Details by IDs
- Get IOC Details
- Get IOCs
- Get Incident Details
- Get Incidents Crowdstrike Score
- Get Process Details
- Get Processes Related to IOC
- Get Scripts Details by IDs
- Get Scripts List
- Get User Details
- Get User ID
- Get User IDs List
- Get Usernames List
- Hunt Domain
- Hunt File
- Remove Containment
- Run Admin Command
- Search Incidents
- Update Detection
- Update IOC
- Update Incidents Status
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection since the sample playbook collection gets deleted during the connector upgrade and delete.
Data Ingestion Support
Use the Data Ingestion Wizard to easily ingest data into FortiSOAR™ by pulling detections from CrowdStrike Falcon. Currently, "detections" in CrowdStrike Falcon are mapped to "alerts" in FortiSOAR™. For more information on the Data Ingestion Wizard, see the "Connectors Guide" in the FortiSOAR™ product documentation.
Configure Data Ingestion
You can configure data ingestion using the “Data Ingestion Wizard” to seamlessly map the incoming CrowdStrike Falcon "Detections" to FortiSOAR™ "Alerts".
The Data Ingestion Wizard enables you to configure the scheduled pulling of data from CrowdStrike Falcon into FortiSOAR™. It also lets you pull some sample data from CrowdStrike Falcon using which you can define the mapping of data between CrowdStrike Falcon and FortiSOAR™. The mapping of common fields is generally already done by the Data Ingestion Wizard; users are mostly required to only map any custom fields that are added to the CrowdStrike Falcon alert.
- To begin configuring data ingestion, click Configure Data Ingestion on the CrowdStrike Falcon connector’s "Configurations" page.
Click Let’s Start by fetching some data, to open the “Fetch Sample Data” screen.
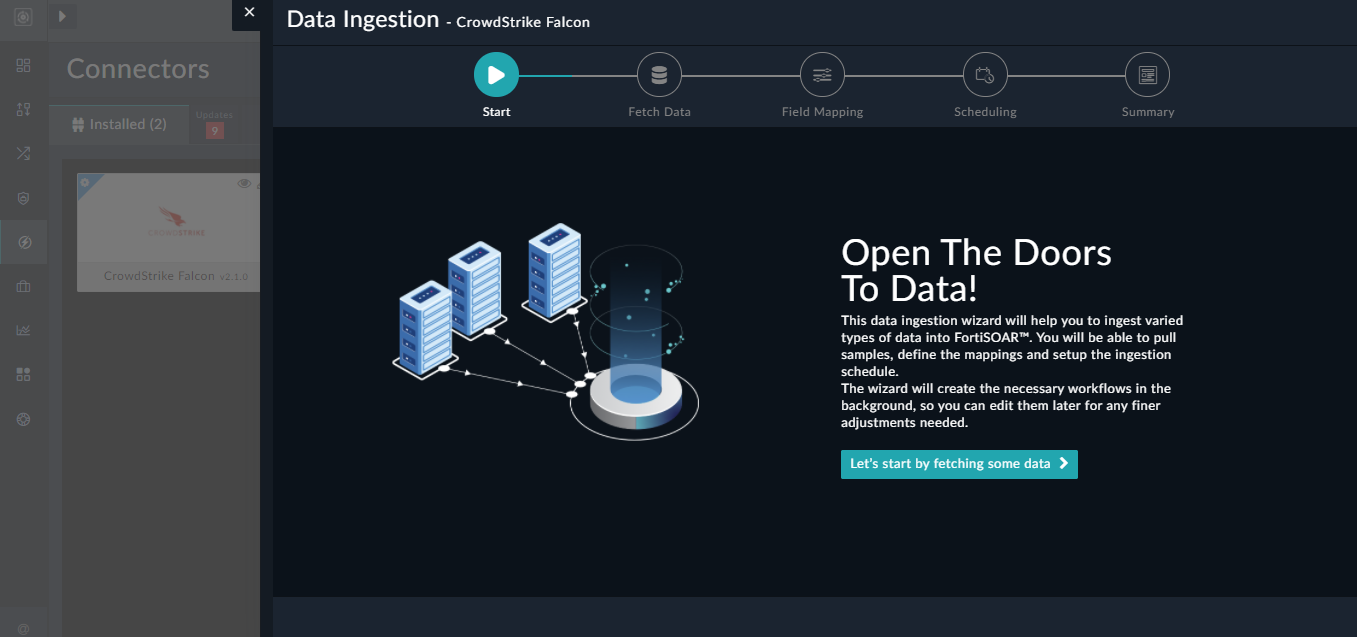
Sample data is required to create a field mapping between CrowdStrike Falcon data and FortiSOAR™. The sample data is pulled from connector actions or ingestion playbooks.
- On the Fetch Data screen, provide the configurations required to fetch CrowdStrike Falcon data.
Users can choose to pull data from CrowdStrike Falcon by specifying the last X minutes based on which they want to pull detections from CrowdStrike Falcon. You can also specify additional parameters such as severity, tactic, technique, status, confidence, etc. to filter detections that are pulled from CrowdStrike Falcon. You can also optionally specify a query based on which detections are fetched from CrowdStrike Falcon and specify the maximum number of records that you want to retrieve from CrowdStrike Falcon. The fetched data is used to create a mapping between the CrowdStrike Falcon detections and FortiSOAR™ alerts.
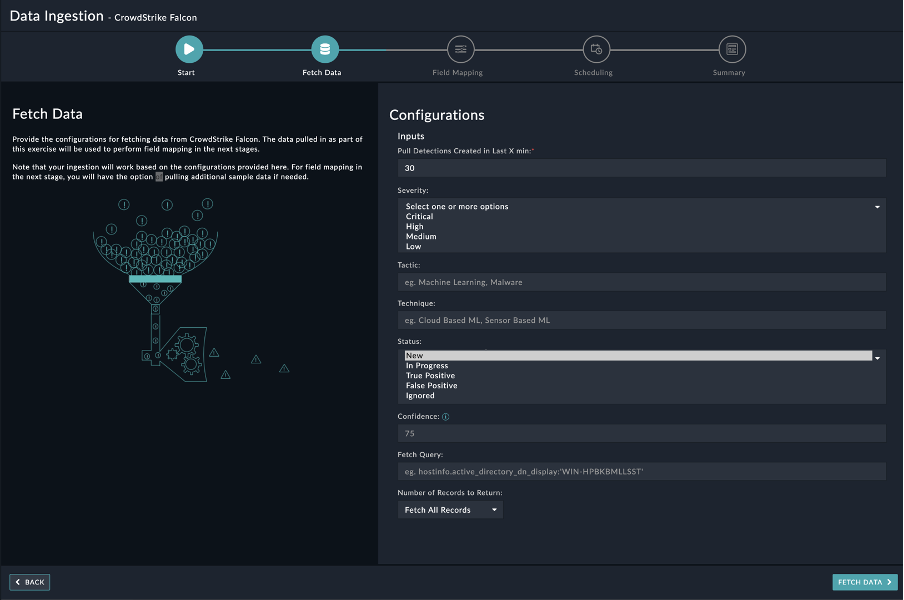
Once you have completed specifying the configurations, click Fetch Data.
-
On the Field Mapping screen, map the fields of a CrowdStrike Falcon detection to the fields of an alert present in FortiSOAR™.
To map a field, click the key in the sample data to add the “jinja” value of the field. For example, to map the max_severity_displayname parameter of a CrowdStrike Falcon detection to the Severity parameter of a FortiSOAR™ alert, click the Severity field and then click the max_severity_displayname field to populate its keys:
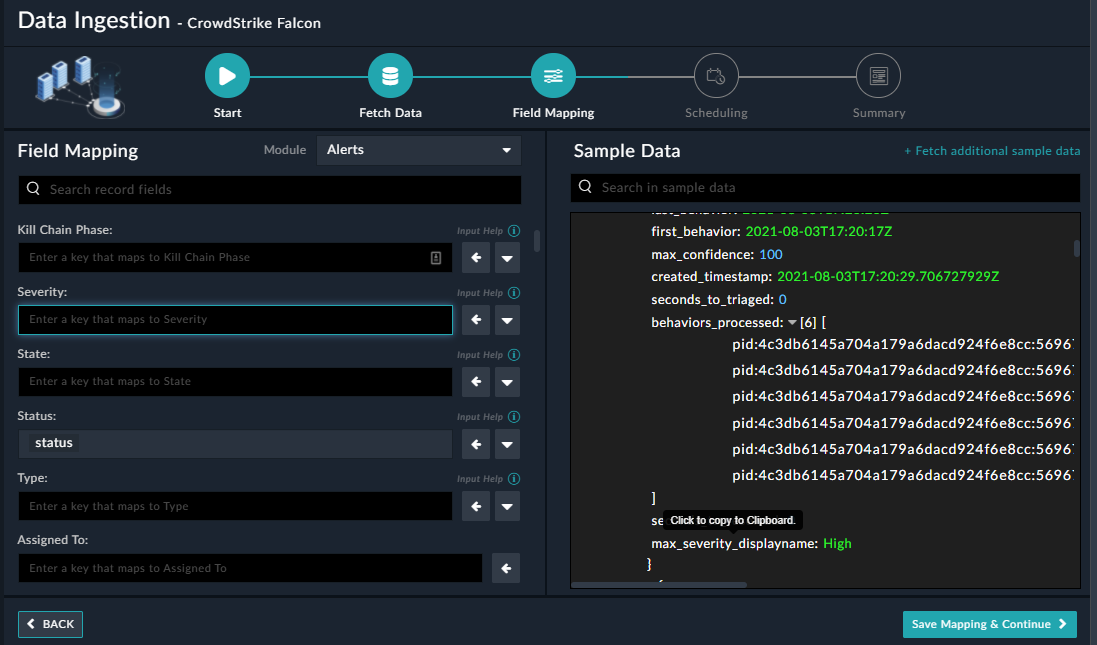
For more information on field mapping, see the Data Ingestion chapter in the "Connectors Guide" in the FortiSOAR™ product documentation. Once you have completed the mapping of fields, click Save Mapping & Continue.
-
(Optional) Use the Scheduling screen to configure schedule-based ingestion, i.e., specify the polling frequency to CrowdStrike Falcon, so that the content gets pulled from the CrowdStrike Falcon integration into FortiSOAR™.
On the Scheduling screen, from the Do you want to schedule the ingestion? drop-down list, select Yes.
In the “Configure Schedule Settings” section, specify the Cron expression for the schedule. For example, if you want to pull data from CrowdStrike Falcon every 5 minutes, click Every X Minute, and in the minute box enter */5. This would mean that based on the configuration you have set up, data, i.e., detections will be pulled from CrowdStrike Falcon every 5 minutes.
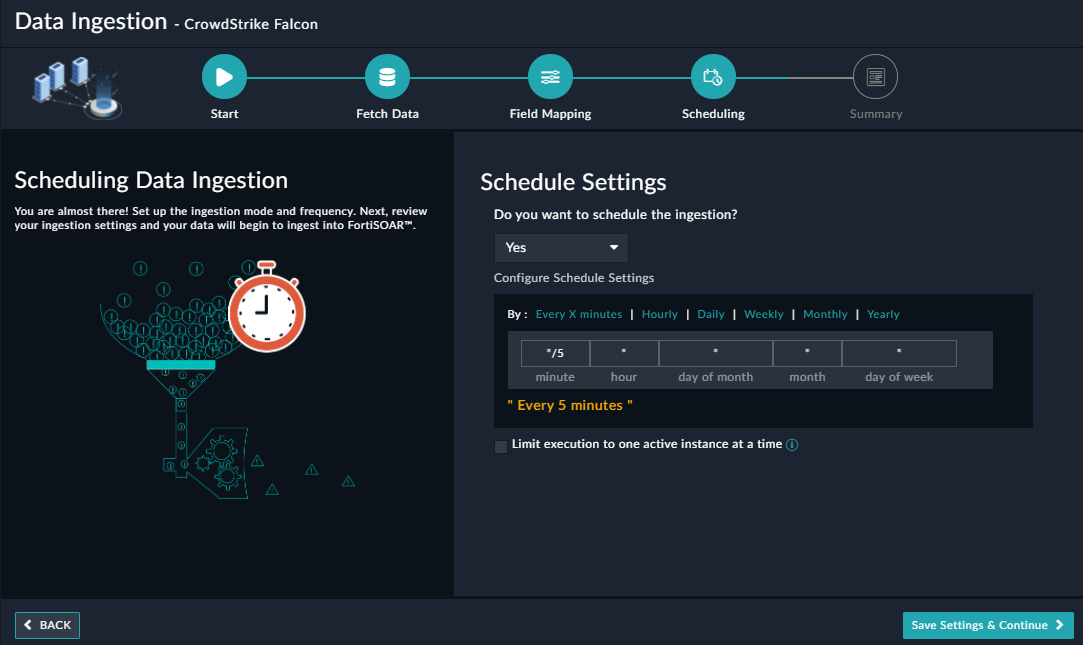
Once you have completed scheduling, click Save Settings & Continue.
-
The Summary screen displays a summary of the mapping done, and it also contains links to the Ingestion playbooks. Click Done to complete the data ingestion and exit the Data Ingestion Wizard.









